Computer Architecture > Final Exam Review > Microsoft Exam SC-100 Microsoft Cybersecurity Architect Version: 3.0 [ Total Questions: 105 ]. All A (All)
Microsoft Exam SC-100 Microsoft Cybersecurity Architect Version: 3.0 [ Total Questions: 105 ]. All Answers Provided_Score 100%
Document Content and Description Below
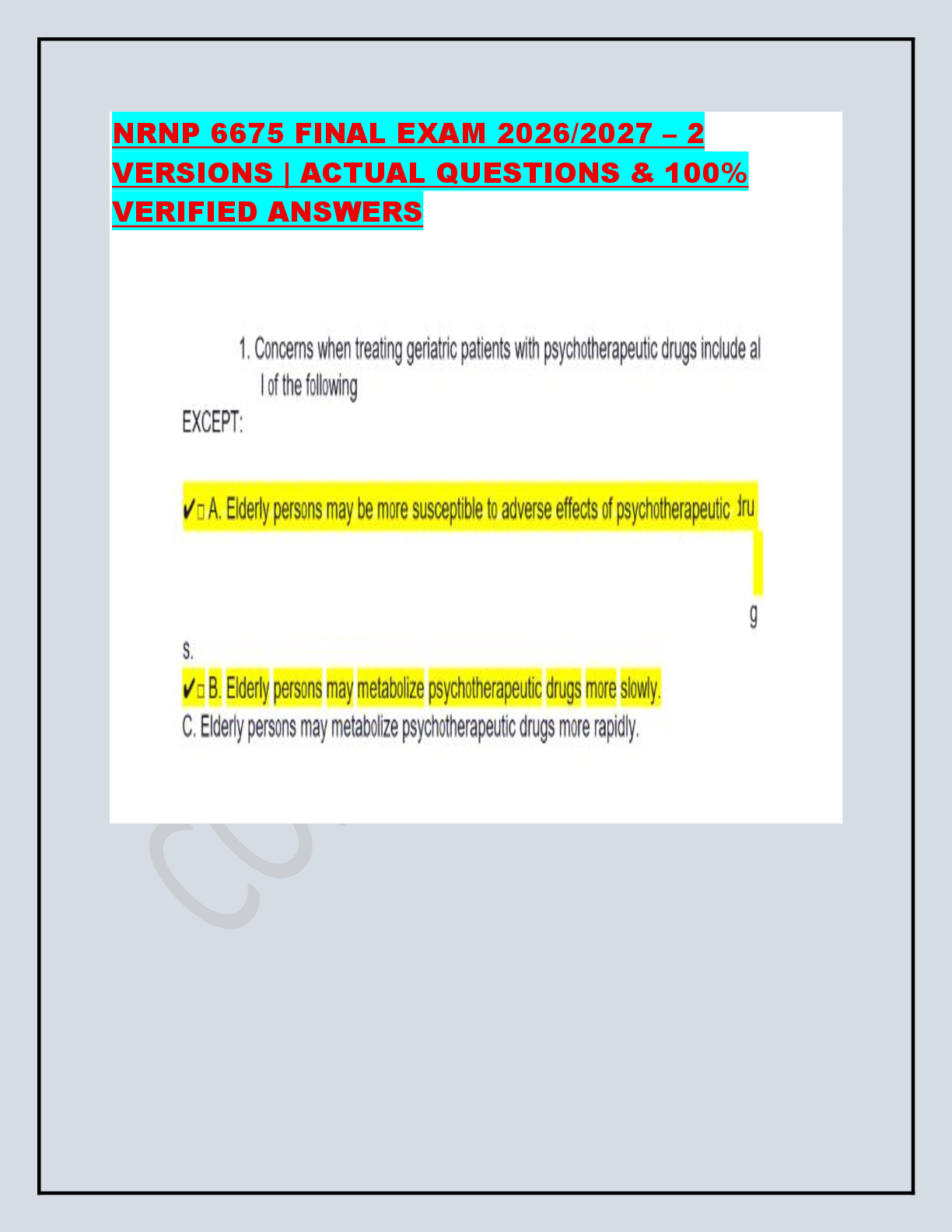
Microsoft Exam SC-100 Microsoft Cybersecurity Architect Version: 3.0 [ Total Questions: 105 ] Topic break down Topic No. of Questions Topic 1: Fabrikam, Inc Case Study 1 10 Topic 2: Litware, in ... c. Case Study 2 8 Topic 3: Mix Questions 87 Microsoft SC-100 2 Topic 1, Fabrikam, Inc Case Study 1 OverView Fabrikam, Inc. is an insurance company that has a main office in New York and a branch office in Paris. On-premises Environment The on-premises network contains a single Active Directory Domain Services (AD DS) domain named corp.fabrikam.com. Azure Environment Fabrikam has the following Azure resources: • An Azure Active Directory (Azure AD) tenant named fabrikam.onmicrosoft.com that syncs with corp.fabnkam.com • A single Azure subscription named Sub1 • A virtual network named Vnetl in the East US Azure region • A virtual network named Vnet2 in the West Europe Azure region • An instance of Azure Front Door named FD1 that has Azure Web Application Firewall (WAR enabled • A Microsoft Sentinel workspace • An Azure SQL database named ClaimsDB that contains a table named ClaimDetails • 20 virtual machines that are configured as application servers and are NOT onboarded to Microsoft Defender for Cloud • A resource group named TestRG that is used for testing purposes only • An Azure Virtual Desktop host pool that contains personal assigned session hosts All the resources in Sub1 are in either the East US or the West Europe region. Partners Fabrikam has contracted a company named Contoso, Ltd. to develop applications. Contoso has the following infrastructure-. • An Azure AD tenant named contoso.onmicrosoft.com • An Amazon Web Services (AWS) implementation named ContosoAWS1 that contains AWS EC2 instances used to host test workloads for the applications of Fabrikam Developers at Contoso will connect to the resources of Fabrikam to test or update applications. The developers will be added to a security Group named Contoso Developers in fabrikam.onmicrosoft.com that will be assigned to roles in Sub1. The ContosoDevelopers group is assigned the db.owner role for the ClaimsDB database. Compliance Event Fabrikam deploys the following compliance environment: • Defender for Cloud is configured to assess all the resources in Sub1 for compliance to the HIPAA HITRUST standard. • Currently, resources that are noncompliant with the HIPAA HITRUST standard are remediated manually. • Qualys is used as the standard vulnerability assessment tool for servers. Problem Statements The secure score in Defender for Cloud shows that all the virtual machines generate the following recommendation-. Machines should have a vulnerability assessment solution. All the virtual machines must be compliant in Defender for Cloud. Microsoft SC-100 3 ClaimApp Deployment Fabrikam plans to implement an internet-accessible application named ClaimsApp that will have the following specification • ClaimsApp will be deployed to Azure App Service instances that connect to Vnetl and Vnet2. • Users will connect to ClaimsApp by using a URL of https://claims.fabrikam.com. • ClaimsApp will access data in ClaimsDB. • ClaimsDB must be accessible only from Azure virtual networks. • The app services permission for ClaimsApp must be assigned to ClaimsDB. Application Development Requirements Fabrikam identifies the following requirements for application development: • Azure DevTest labs will be used by developers for testing. • All the application code must be stored in GitHub Enterprise. • Azure Pipelines will be used to manage application deployments. • All application code changes must be scanned for security vulnerabilities, including application code or configuration files that contain secrets in clear text. Scanning must be done at the time the code is pushed to a repository. Security Requirement Fabrikam identifies the following security requirements: • Internet-accessible applications must prevent connections that originate in North Korea. • Only members of a group named InfraSec must be allowed to configure network security groups (NSGs} and instances of Azure Firewall, VJM. And Front Door in Sub1. • Administrators must connect to a secure host to perform any remote administration of the virtual machines. The secure host must be provisioned from a custom operating system image. AWS Requirements Fabrikam identifies the following security requirements for the data hosted in ContosoAWSV. • Notify security administrators at Fabrikam if any AWS EC2 instances are noncompliant with secure score recommendations. • Ensure that the security administrators can query AWS service logs directly from the Azure environment. Contoso Developer Requirements Fabrikam identifies the following requirements for the Contoso developers; • Every month, the membership of the ContosoDevelopers group must be verified. • The Contoso developers must use their existing contoso.onmicrosoft.com credentials to access the resources in Sub1. • The Comoro developers must be prevented from viewing the data in a column named MedicalHistory in the ClaimDetails table. Compliance Requirement Fabrikam wants to automatically remediate the virtual machines in Sub1 to be compliant with the HIPPA HITRUST standard. The virtual machines in TestRG must be excluded from the compliance assessment. Question No : 1 - (Topic 1) Microsoft SC-100 4 You need to recommend a solution to secure the MedicalHistory data in the ClaimsDetail table. The solution must meet the Contoso developer requirements. What should you include in the recommendation? A. Transparent Data Encryption (TDE) B. Always Encrypted C. row-level security (RLS) D. dynamic data masking E. data classification You need to recommend a solution to meet the AWS requirements. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Answer: Question No : 2 HOTSPOT - (Topic 1) Microsoft SC-100 5 What should you create in Azure AD to meet the Contoso developer requirements? Answer: You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation? A. Onboard the virtual machines to Microsoft Defender for Endpoint. B. Onboard the virtual machines to Azure Arc. C. Create a device compliance policy in Microsoft Endpoint Manager. D. Enable the Qualys scanner in Defender for Cloud. Question No : 3 HOTSPOT - (Topic 1) Question No : 4 - (Topic 1) Question No : 5 HOTSPOT - (Topic 1) Microsoft SC-100 6 You need to recommend a solution to meet the requirements for connections to ClaimsDB. What should you recommend using for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Answer: You need to recommend a solution to meet the security requirements for the InfraSec group. What should you use to delegate the access? A. a subscription B. a custom role-based access control (RBAC) role C. a resource group D. a management group You need to recommend a solution to meet the compliance requirements. Question No : 6 - (Topic 1) Question No : 7 HOTSPOT - (Topic 1) Microsoft SC-100 7 What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Answer: You are evaluating the security of ClaimsApp. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE; Each correct selection is worth one point. Answer: Question No : 8 HOTSPOT - (Topic 1) Microsoft SC-100 8 You need to recommend a solution to meet the security requirements for the virtual machines. What should you include in the recommendation? A. an Azure Bastion host B. a network security group (NSG) C. just-in-time (JIT) VM access D. Azure Virtual Desktop You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation? A. Azure Key Vault B. GitHub Advanced Security C. Application Insights in Azure Monitor D. Azure DevTest Labs Topic 2, Litware, inc. Case Study 2 Overview Litware, inc. is a financial services company that has main offices in New York and San Francisco. litware has 30 branch offices and remote employees across the United States. The remote employees connect to the main offices by using a VPN. Litware has grown significantly during the last two years due to mergers and acquisitions. The acquisitions include several companies based in France. Existing Environment Question No : 9 - (Topic 1) Question No : 10 - (Topic 1) Microsoft SC-100 9 Litware has an Azure Active Directory (Azure AD) tenant that syncs with an Active Directory Domain Services (AD D%) forest named Utvvare.com and is linked to 20 Azure subscriptions. Azure AD Connect is used to implement pass-through authentication. Password hash synchronization is disabled, and password writeback is enabled. All Litware users have Microsoft 365 E5 licenses. The environment also includes several AD DS forests, Azure AD tenants, and hundreds of Azure subscriptions that belong to the subsidiaries of Litware. Planned Changes Litware plans to implement the following changes: • Create a management group hierarchy for each Azure AD tenant. • Design a landing zone strategy to refactor the existing Azure environment of Litware and deploy all future Azure workloads. • Implement Azure AD Application Proxy to provide secure access to internal applications that are currently accessed by using the VPN. Business Requirements Litware identifies the following business requirements: • Minimize any additional on-premises infrastructure. • Minimize the operational costs associated with administrative overhead. Hybrid Requirements Litware identifies the following hybrid cloud requirements: • Enable the management of on-premises resources from Azure, including the following: •Use Azure Policy for enforcement and compliance evaluation. • Provide change tracking and asset inventory. • Implement patch management. • Provide centralized, cross-tenant subscription management without the overhead of maintaining guest accounts. Microsoft Sentinel Requirements Litware plans to leverage the security information and event management (SIEM) and security orchestration automated response (SOAK) capabilities of Microsoft Sentinel. The company wants to centralize Security Operations Center (SOQ by using Microsoft Sentinel. Identity Requirements Litware identifies the following identity requirements: • Detect brute force attacks that directly target AD DS user accounts. • Implement leaked credential detection in the Azure AD tenant of Litware. • Prevent AD DS user accounts from being locked out by brute force attacks that target Azure AD user accounts. • Implement delegated management of users and groups in the Azure AD tenant of Litware, including support for. • The management of group properties, membership, and licensing « The management of user properties, passwords, and licensing • The delegation of user management based on business units. Regulatory Compliance Requirements Litware identifies the following regulatory compliance requirements: • insure data residency compliance when collecting logs, telemetry, and data owned by each United States- and France-based subsidiary. • Leverage built-in Azure Policy definitions to evaluate regulatory compliance across the Microsoft SC-100 10 entire managed environment. • Use the principle of least privilege. Azure Landing Zone Requirements Litware identifies the following landing zone requirements: • Route all internet-bound traffic from landing zones through Azure Firewall in a dedicated Azure subscription. • Provide a secure score scoped to the landing zone. • Ensure that the Azure virtual machines in each landing zone communicate with Azure App Service web apps in the same zone over the Microsoft backbone network, rather than over public endpoints. • Minimize the possibility of data exfiltration. • Maximize network bandwidth. The landing zone architecture will include the dedicated subscription, which will serve as the hub for internet and hybrid connectivity. Each landing zone will have the following characteristics: • Be created in a dedicated subscription. • Use a DNS namespace of litware.com. Application Security Requirements Litware identifies the following application security requirements: • Identify internal applications that will support single sign-on (SSO) by using Azure AD Application Proxy. • Monitor and control access to Microsoft SharePoint Online and Exchange Online data in real time. To meet the application security requirements, which two authentication methods must the applications support? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. Security Assertion Markup Language (SAML) B. NTLMv2 C. certificate-based authentication D. Kerberos ,C You need to recommend a solution for securing the landing zones. The solution must meet the landing zone requirements and the business requirements. Question No : 11 - (Topic 2) Question No : 12 - (Topic 2) Microsoft SC-100 11 What should you configure for each landing zone? A. Azure DDoS Protection Standard B. an Azure Private DNS zone C. Microsoft Defender for Cloud D. an ExpressRoute gateway You need to recommend a multi-tenant and hybrid security solution that meets to the business requirements and the hybrid requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Answer: You need to recommend an identity security solution for the Azure AD tenant of Litware. The solution must meet the identity requirements and the regulatory compliance requirements. What should you recommend? To answer, select the appropriate options in the answer area. Question No : 13 HOTSPOT - (Topic 2) Question No : 14 HOTSPOT - (Topic 2) Microsoft SC-100 12 NOTE: Each correct selection is worth one point. Answer: You need to recommend a strategy for App Service web app connectivity. The solution must meet the landing zone requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE Each correct selection is worth one point. Answer: Question No : 15 HOTSPOT - (Topic 2) Question No : 16 HOTSPOT - (Topic 2) Microsoft SC-100 13 You need to recommend a solution to evaluate regulatory compliance across the entire managed environment. The solution must meet the regulatory compliance requirements and the business requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Answer: You need to recommend a strategy for securing the litware.com forest. The solution must meet the identity requirements. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE; Each correct selection is worth one point. Answer: Question No : 17 HOTSPOT - (Topic 2) Microsoft SC-100 14 You need to recommend a SIEM and SOAR strategy that meets the hybrid requirements, the Microsoft Sentinel requirements, and the regulatory compliance requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Answer: Topic 3, Mix Questions Your company has a Microsoft 365 E5 subscription. The Chief Compliance Officer plans to enhance privacy management in the working environment. You need to recommend a solution to enhance the privacy management. The solution must meet the following requirements: Question No : 18 HOTSPOT - (Topic 2) Question No : 19 - (Topic 3) Microsoft SC-100 15 • Identify unused personal data and empower users to make smart data handling decisions. • Provide users with notifications and guidance when a user sends personal data in Microsoft Teams. • Provide users with recommendations to mitigate privacy risks. What should you include in the recommendation? A. Microsoft Viva Insights B. Advanced eDiscovery C. Privacy Risk Management in Microsoft Priva D. communication compliance in insider risk management Your company is developing an invoicing application that will use Azure Active Directory (Azure AD) B2C. The application will be deployed as an App Service web app. You need to recommend a solution to the application development team to secure the application from identity related attacks. Which two configurations should you recommend? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. A. Azure AD Conditional Access integration with user flows and custom policies B. Azure AD workbooks to monitor risk detections C. custom resource owner password credentials (ROPC) flows in Azure AD B2C D. access packages in Identity Governance E. smart account lockout in Azure AD B2C ,E Your company is developing a new Azure App Service web app. You are providing design assistance to verify the security of the web app. You need to recommend a solution to test the web app for vulnerabilities such as insecure server configurations, cross-site scripting (XSS), and SQL injection. What should you include in the recommendation? A. interactive application security testing (IAST) Question No : 20 - (Topic 3) Question No : 21 - (Topic 3) Microsoft SC-100 16 B. static application security testing (SAST) C. runtime application se/f-protection (RASP) D. dynamic application security testing (DAST) You have a Microsoft 365 E5 subscription and an Azure subscription. You are designing a Microsoft Sentinel deployment. You need to recommend a solution for the security operations team. The solution must include custom views and a dashboard for analyzing security events. What should you recommend using in Microsoft Sentinel? A. playbooks B. workbooks C. notebooks D. threat intelligence You are designing security for an Azure landing zone. Your company identifies the following compliance and privacy requirements: • Encrypt cardholder data by using encryption keys managed by the company. • Encrypt insurance claim files by using encryption keys hosted on-premises. Which two configurations meet the compliance and privacy requirements? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. A. Store the insurance claim data in Azure Blob storage encrypted by using customerprovided keys. B. Store the cardholder data in an Azure SQL database that is encrypted by using keys stored in Azure Key Vault Managed HSM C. Store the insurance claim data in Azure Files encrypted by using Azure Key Vault Managed HSM. D. Store the cardholder data in an Azure SQL database that is encrypted by using Microsoft-managed Keys. Question No : 22 - (Topic 3) Question No : 23 - (Topic 3) Microsoft SC-100 17 ,D A customer has a hybrid cloud infrastructure that contains a Microsoft 365 E5 subscription and an Azure subscription. All the on-premises servers in the perimeter network are prevented from connecting directly to the internet. The customer recently recovered from a ransomware attack. The customer plans to deploy Microsoft Sentinel. You need to recommend configurations to meet the following requirements: • Ensure that the security operations team can access the security logs and the operation logs. • Ensure that the IT operations team can access only the operations logs, including the event logs of the servers in the perimeter network. Which two configurations can you include in the recommendation? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. Configure Azure Active Directory (Azure AD) Conditional Access policies. B. Use the Azure Monitor agent with the multi-homing configuration. C. Implement resource-based role-based access control (RBAC) in Microsoft Sentinel. D. Create a custom collector that uses the Log Analytics agent. Your company has the virtual machine infrastructure shown in the following table. The company plans to use Microsoft Azure Backup Server (MABS) to back up the virtual Question No : 24 - (Topic 3) Question No : 25 - (Topic 3) Microsoft SC-100 18 machines to Azure. You need to provide recommendations to increase the resiliency of the backup strategy to mitigate attacks such as ransomware. What should you include in the recommendation? A. Use geo-redundant storage (GRS). B. Use customer-managed keys (CMKs) for encryption. C. Require PINs to disable backups. D. Implement Azure Site Recovery replication. Your company has an office in Seattle. The company has two Azure virtual machine scale sets hosted on different virtual networks. The company plans to contract developers in India. You need to recommend a solution provide the developers with the ability to connect to the virtual machines over SSL from the Azure portal. The solution must meet the following requirements: • Prevent exposing the public IP addresses of the virtual machines. • Provide the ability to connect without using a VPN. • Minimize costs. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. A. Deploy Azure Bastion to one virtual network. B. Deploy Azure Bastion to each virtual network. C. Enable just-in-time VM access on the virtual machines. D. Create a hub and spoke network by using virtual network peering. E. Create NAT rules and network rules in Azure Firewall. ,E Question No : 26 - (Topic 3) Microsoft SC-100 19 Your company has a Microsoft 365 E5 subscription, an Azure subscription, on-premises applications, and Active Directory Domain Services (AD DSV You need to recommend an identity security strategy that meets the following requirements: • Ensures that customers can use their Facebook credentials to authenticate to an Azure App Service website • Ensures that partner companies can access Microsoft SharePoint Online sites for the project to which they are assigned The solution must minimize the need to deploy additional infrastructure components. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Answer: Your company finalizes the adoption of Azure and is implementing Microsoft Defender for Cloud. You receive the following recommendations in Defender for Cloud Question No : 27 HOTSPOT - (Topic 3) Question No : 28 - (Topic 3) Microsoft SC-100 20 • Access to storage accounts with firewall and virtual network configurations should be restricted, • Storage accounts should restrict network access using virtual network rules. • Storage account should use a private link connection. • Storage account public access should be disallowed. You need to recommend a service to mitigate identified risks that relate to the recommendations. What should you recommend? A. Azure Storage Analytics B. Azure Network Watcher C. Microsoft Sentinel D. Azure Policy You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report. In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls. Solution: You recommend enabling just-in-time (JIT) VM access on all virtual machines. Does this meet the goal? A. Yes B. No Your company uses Microsoft Defender for Cloud and Microsoft Sentinel. The company is designing an application that will have the architecture shown in the following exhibit. Question No : 29 - (Topic 3) Question No : 30 HOTSPOT - (Topic 3) Microsoft SC-100 21 You are designing a logging and auditing solution for the proposed architecture. The solution must meet the following requirements-. • Integrate Azure Web Application Firewall (WAF) logs with Microsoft Sentinel. • Use Defender for Cloud to review alerts from the virtual machines. What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Answer: A customer uses Azure to develop a mobile app that will be consumed by external users as shown in the following exhibit. Question No : 31 - (Topic 3) Microsoft SC-100 22 You need to design an identity strategy for the app. The solution must meet the following requirements: • Enable the usage of external IDs such as Google, Facebook, and Microsoft accounts. • Be managed separately from the identity store of the customer. • Support fully customizable branding for each app. Which service should you recommend to complete the design? A. Azure Active Directory (Azure AD) B2C B. Azure Active Directory (Azure AD) B2B C. Azure AD Connect D. Azure Active Directory Domain Services (Azure AD DS) You are designing security for a runbook in an Azure Automation account. The runbook will copy data to Azure Data Lake Storage Gen2. You need to recommend a solution to secure the components of the copy process. What should you include in the recommendation for each component? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Question No : 32 HOTSPOT - (Topic 3) Microsoft SC-100 23 Answer: Your company is moving all on-premises workloads to Azure and Microsoft 365. Vou need to design a security orchestration, automation, and response (SOAR) strategy in Microsoft Sentinel that meets the following requirements: • Minimizes manual intervention by security operation analysts • Supports Waging alerts within Microsoft Teams channels What should you include in the strategy? A. data connectors B. playbooks C. workbooks D. KQL You are planning the security requirements for Azure Cosmos DB Core (SQL) API accounts. You need to recommend a solution to audit all users that access the data in the Azure Cosmos DB accounts. Which two configurations should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct Question No : 33 - (Topic 3) Question No : 34 - (Topic 3) Microsoft SC-100 24 selection is worth one point. A. Enable Microsoft Defender for Cosmos DB. B. Send the Azure Active Directory (Azure AD) sign-in logs to a Log Analytics workspace. C. Disable local authentication for Azure Cosmos DB. D. Enable Microsoft Defender for Identity. E. Send the Azure Cosmos DB logs to a Log Analytics workspace. ,D Your company has a hybrid cloud infrastructure. The company plans to hire several temporary employees within a brief period. The temporary employees will need to access applications and data on the company' premises network. The company's security policy prevents the use of personal devices for accessing company data and applications. You need to recommend a solution to provide the temporary employee with access to company resources. The solution must be able to scale on demand. What should you include in the recommendation? A. Migrate the on-premises applications to cloud-based applications. B. Redesign the VPN infrastructure by adopting a split tunnel configuration. C. Deploy Microsoft Endpoint Manager and Azure Active Directory (Azure AD) Conditional Access. D. Deploy Azure Virtual Desktop, Azure Active Directory (Azure AD) Conditional Access, and Microsoft Defender for Cloud Apps. Your on-premises network contains an e-commerce web app that was developed in Angular and Nodejs. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone. Question No : 35 - (Topic 3) Question No : 36 - (Topic 3) Microsoft SC-100 25 You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model. Solution: You recommend creating private endpoints for the web app and the database layer. Does this meet the goal? A. Yes B. No You open Microsoft Defender for Cloud as shown in the following exhibit. Use the drop-down menus to select the answer choice that complete each statements based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Question No : 37 HOTSPOT - (Topic 3) Microsoft SC-100 26 Answer: Your company is developing a serverless application in Azure that will have the architecture shown in the following exhibit. You need to recommend a solution to isolate the compute components on an Azure virtual network. What should you include in the recommendation? A. Azure Active Directory (Azure AD) enterprise applications B. an Azure App Service Environment (ASE) C. Azure service endpoints D. an Azure Active Directory (Azure AD) application proxy Question No : 38 - (Topic 3) Microsoft SC-100 27 A customer is deploying Docker images to 10 Azure Kubernetes Service (AKS) resources across four Azure subscriptions. You are evaluating the security posture of the customer. You discover that the AKS resources are excluded from the secure score recommendations. You need to produce accurate recommendations and update the secure score. Which two actions should you recommend in Microsoft Defender for Cloud? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. A. Configure auto provisioning. B. Assign regulatory compliance policies. C. Review the inventory. D. Add a workflow automation. E. Enable Defender plans. ,D You are designing the security standards for containerized applications onboarded to Azure. You are evaluating the use of Microsoft Defender for Containers. In which two environments can you use Defender for Containers to scan for known vulnerabilities? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. Linux containers deployed to Azure Container Registry B. Linux containers deployed to Azure Kubernetes Service (AKS) C. Windows containers deployed to Azure Container Registry D. Windows containers deployed to Azure Kubernetes Service (AKS) E. Linux containers deployed to Azure Container Instances ,E Question No : 39 - (Topic 3) Question No : 40 - (Topic 3) Question No : 41 HOTSPOT - (Topic 3) Microsoft SC-100 28 Your company has a multi-cloud environment that contains a Microsoft 365 subscription, an Azure subscription, and Amazon Web Services (AWS) implementation. You need to recommend a security posture management solution for the following components: • Azure loT Edge devices • AWS EC2 instances Which services should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Answer: You are evaluating an Azure environment for compliance. You need to design an Azure Policy implementation that can be used to evaluate compliance without changing any resources. Which effect should you use in Azure Policy? A. Deny B. Disabled Question No : 42 - (Topic 3) Microsoft SC-100 29 C. Modify D. Append You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance. You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance. Solution: You recommend access restrictions to allow traffic from the backend IP address of the Front Door instance. Does this meet the goal? A. Yes B. No Your company has an on-premises network, an Azure subscription, and a Microsoft 365 E5 subscription. The company uses the following devices: • Computers that run either Windows 10 or Windows 11 • Tablets and phones that run either Android or iOS You need to recommend a solution to classify and encrypt sensitive Microsoft Office 365 data regardless of where the data is stored. What should you include in the recommendation? A. eDiscovery B. retention policies C. Compliance Manager D. Microsoft Information Protection Question No : 43 - (Topic 3) Question No : 44 - (Topic 3) Microsoft SC-100 30 You have an Azure subscription that contains virtual machines, storage accounts, and Azure SQL databases. All resources are backed up multiple times a day by using Azure Backup. You are developing a strategy to protect against ransomware attacks. You need to recommend which controls must be enabled to ensure that Azure Backup can be used to restore the resources in the event of a successtu\ ransonvwaTe attack. Which two controls should you include in the recommendation? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. Use Azure Monitor notifications when backup configurations change. B. Require PINs for critical operations. C. Perform offline backups to Azure Data Box. D. Encrypt backups by using customer-managed keys (CMKs). E. Enable soft delete for backups. You are creating an application lifecycle management process based on the Microsoft Security Development Lifecycle (SDL). You need to recommend a security standard for onboarding applications to Azure. The standard will include recommendations for application design, development, and deployment What should you include during the application design phase? A. static application security testing (SAST) by using SonarQube B. dynamic application security testing (DAST) by using Veracode C. threat modeling by using the Microsoft Threat Modeling Tool D. software decomposition by using Microsoft Visual Studio Enterprise Question No : 45 - (Topic 3) Question No : 46 - (Topic 3) Question No : 47 - (Topic 3) Microsoft SC-100 31 A customer follows the Zero Trust model and explicitly verifies each attempt to access its corporate applications. The customer discovers that several endpoints are infected with malware. The customer suspends access attempts from the infected endpoints. The malware is removed from the end point. Which two conditions must be met before endpoint users can access the corporate applications again? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. A. Microsoft Defender for Endpoint reports the endpoints as compliant. B. Microsoft Intune reports the endpoints as compliant. C. A new Azure Active Directory (Azure AD) Conditional Access policy is enforced. D. The client access tokens are refreshed. ,D Your company has a hybrid cloud infrastructure. Data and applications are moved regularly between cloud environments. The company's on-premises network is managed as shown in the following exhibit. Question No : 48 - (Topic 3) Microsoft SC-100 32 NOTE Each correct selection is worth one point. A. Azure VPN Gateway B. guest configuration in Azure Policy C. on-premises data gateway D. Azure Bastion E. Azure Arc ,E You are designing an auditing solution for Azure landing zones that will contain the following components: • SQL audit logs for Azure SQL databases • Windows Security logs from Azure virtual machines • Azure App Service audit logs from App Service web apps You need to recommend a centralized logging solution for the landing zones. The solution must meet the following requirements: • Log all privileged access. • Retain logs for at least 365 days. • Minimize costs. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Question No : 49 HOTSPOT - (Topic 3) Microsoft SC-100 33 Answer: You have a Microsoft 365 E5 subscription and an Azure subscripts You need to evaluate the existing environment to increase the overall security posture for the following components: • Windows 11 devices managed by Microsoft Intune • Azure Storage accounts • Azure virtual machines What should you use to evaluate the components? To answer, select the appropriate options in the answer area. Answer: Question No : 50 HOTSPOT - (Topic 3) Microsoft SC-100 34 Azure subscription that uses Azure Storage. The company plans to share specific blobs with vendors. You need to recommend a solution to provide the vendors with secure access to specific blobs without exposing the blobs publicly. The access must be t\me-Vim\ted. What should you include in the recommendation? A. Create shared access signatures (SAS). B. Share the connection string of the access key. C. Configure private link connections. D. Configure encryption by using customer-managed keys (CMKs) Your company has a Microsoft 365 E5 subscription. The company plans to deploy 45 mobile self-service kiosks that will run Windows 10. You need to provide recommendations to secure the kiosks. The solution must meet the following requirements: • Ensure that only authorized applications can run on the kiosks. • Regularly harden the kiosks against new threats. Which two actions should you include in the recommendations? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. Question No : 51 - (Topic 3) Question No : 52 - (Topic 3) Microsoft SC-100 35 A. Onboard the kiosks to Azure Monitor. B. Implement Privileged Access Workstation (PAW) for the kiosks. C. Implement Automated Investigation and Remediation (AIR) in Microsoft Defender for Endpoint. D. Implement threat and vulnerability management in Microsoft Defender for Endpoint. E. Onboard the kiosks to Microsoft Intune and Microsoft Defender for Endpoint. ,B You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains a Microsoft Sentinel workspace. Microsoft Sentinel data connectors are configured for Microsoft 365, Microsoft 365 Defender, Defender for Cloud, and Azure. You plan to deploy Azure virtual machines that will run Windows Server. You need to enable extended detection and response (EDR) and security orchestration, automation, and response (SOAR) capabilities for Microsoft Sentinel. How should you recommend enabling each capability? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Answer: Question No : 53 HOTSPOT - (Topic 3) Microsoft SC-100 36 Your company is designing an application architecture for Azure App Service Environment (ASE) web apps as shown in the exhibit. (Click the Exhibit tab.) Communication between the on-premises network and Azure uses an ExpressRoute connection. You need to recommend a solution to ensure that the web apps can communicate with the on-premises application server. The solution must minimize the number of public IP addresses that are allowed to access the on-premises network. What should you include in the recommendation? A. Azure Traffic Manager with priority traffic-routing methods B. Azure Application Gateway v2 with user-defined routes (UDRs). C. Azure Front Door with Azure Web Application Firewall (WAF) D. Azure Firewall with policy rule sets You have an Azure subscription that has Microsoft Defender for Cloud enabled. You need to enforce ISO 2700V2013 standards for the subscription. The solution must ensure that noncompliant resources are remediated automatical What should you use? A. the regulatory compliance dashboard in Defender for Cloud B. Azure Policy Question No : 54 - (Topic 3) Question No : 55 - (Topic 3) Microsoft SC-100 37 C. Azure Blueprints D. Azure role-based access control (Azure RBAC) You have 50 Azure subscriptions. You need to monitor resource in the subscriptions for compliance with the ISO 27001:2013 standards. The solution must minimize the effort required to modify the list of monitored policy definitions for the subscriptions. NOTE: Each correct selection is worth one point. A. Assign an initiative to a management group. B. Assign a blueprint to each subscription. C. Assign a policy to each subscription. D. Assign a blueprint to a management group. E. Assign an initiative to each subscription. F. Assign a policy to a management group. ,D Your company has an on-premise network in Seattle and an Azure subscription. The onpremises network contains a Remote Desktop server. The company contracts a third-party development firm from France to develop and deploy resources to the virtual machines hosted in the Azure subscription. Currently, the firm establishes an RDP connection to the Remote Desktop server. From the Remote Desktop connection, the firm can access the virtual machines hosted in Azure by using custom administrative tools installed on the Remote Desktop server. All the traffic to the Remote Desktop server is captured by a firewall, and the firewall only allows specific connections from France to the server. You need to recommend a modern security solution based on the Zero Trust model. The solution must minimize latency tor developers. Which three actions should you recommend? Each correct answer presents part of the solution. Question No : 56 - (Topic 3) Question No : 57 - (Topic 3) Microsoft SC-100 38 NOTE: Each correct selection is worth one point. A. Configure network security groups (NSGs) to allow access from only specific logical groupings of IP address ranges. B. Implement Azure Firewall to restrict host pool outbound access. C. Configure Azure Active Directory (Azure AD) Conditional Access with multi-factor authentication (MFA) and named locations. D. Migrate from the Remote Desktop server to Azure Virtual Desktop. E. Deploy a Remote Desktop server to an Azure region located in France. ,D,E Your company plans to deploy several Azure App Service web apps. The web apps will be deployed to the West Europe Azure region. The web apps will be accessed only by customers in Europe and the United States. You need to recommend a solution to prevent malicious bots from scanning the web apps for vulnerabilities. The solution must minimize the attach surface. What should you include in the recommendation? A. Azure Firewall Premium B. Azure Application Gateway Web Application Firewall (WAF) C. network security groups (NSGs) D. Azure Traffic Manager and application security groups You need to recommend a strategy for routing internet-bound traffic from the landing zones. The solution must meet the landing zone requirements. What should you recommend as part of the landing zone deployment? A. service chaining B. local network gateways C. forced tunneling D. a VNet-to-VNet connection Question No : 58 - (Topic 3) Question No : 59 - (Topic 3) Microsoft SC-100 39 You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report. In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls. Solution: You recommend onboarding all virtual machines to Microsoft Defender for Endpoint. Does this meet the goal? A. Yes B. No You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements. Which two services should you leverage in the strategy? Each correct answer presents part of the solution. NOTE; Each correct selection is worth one point. A. Azure AD Conditional Access B. Microsoft Defender for Cloud Apps C. Microsoft Defender for Cloud D. Microsoft Defender for Endpoint E. access reviews in Azure AD ,E Your company has a third-party security information and event management (SIEM) Question No : 60 - (Topic 3) Question No : 61 - (Topic 3) Question No : 62 - (Topic 3) Microsoft SC-100 40 solution that uses Splunk and Microsoft Sentinel. You plan to integrate Microsoft Sentinel with Splunk. You need to recommend a solution to send security events from Microsoft Sentinel to Splunk. What should you include in the recommendation? A. Azure Event Hubs B. Azure Data Factor C. a Microsoft Sentinel workbook D. a Microsoft Sentinel data connector You have a hybrid cloud infrastructure. You plan to deploy the Azure applications shown in the following table. What should you use to meet the requirement of each app? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Answer: Question No : 63 HOTSPOT - (Topic 3) Microsoft SC-100 41 You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019. You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application. Which security control should you recommend? A. Azure Active Directory (Azure AD) Conditional Access App Control policies B. OAuth app policies in Microsoft Defender for Cloud Apps C. app protection policies in Microsoft Endpoint Manager D. application control policies in Microsoft Defender for Endpoint Your company has on-premises Microsoft SQL Server databases. The company plans to move the databases to Azure. You need to recommend a secure architecture for the databases that will minimize operational requirements for patching and protect sensitive data by using dynamic data masking. The solution must minimize costs. Question No : 64 - (Topic 3) Question No : 65 - (Topic 3) Microsoft SC-100 42 What should you include in the recommendation? A. Azure SQL Managed Instance B. Azure Synapse Analytics dedicated SQL pools C. Azure SQL Database D. SQL Server on Azure Virtual Machines Your on-premises network contains an e-commerce web app that was developed in Angular and Node.js. The web app uses a MongoDB database You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone. You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model. Solution: You recommend implementing Azure Application Gateway with Azure Web Application Firewall (WAF). Does this meet the goal? A. Yes B. No Your company is moving a big data solution to Azure. The company plans to use the following storage workloads: • Azure Storage blob containers • Azure Data Lake Storage Gen2 • Azure Storage file shares Question No : 66 - (Topic 3) Question No : 67 - (Topic 3) Microsoft SC-100 43 • Azure Disk Storage Which two storage workloads support authentication by using Azure Active Directory (Azure AD)? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. Azure Disk Storage B. Azure Storage blob containers C. Azure Storage file shares D. Azure Data Lake Storage Gen2 ,D You have a Microsoft 365 subscription You need to recommend a security solution to monitor the following activities: • User accounts that were potentially compromised • Users performing bulk file downloads from Microsoft SharePoint Online What should you include in the recommendation for each activity? To answer, drag the appropriate components to the correct activities. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each Correct selection is worth one Point. Answer: Question No : 68 DRAG DROP - (Topic 3) Microsoft SC-100 44 You have an Azure subscription that has Microsoft Defender for Cloud enabled. You have an Amazon Web Services (AWS) implementation. You plan to extend the Azure security strategy to the AWS implementation. The solution will NOT use Azure Arc. Which three services can you use to provide security for the AWS resources? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. Azure Active Directory (Azure AD) Privileged Identity Management (PIM) B. Azure Active Directory (Azure AD) Conditional Access C. Microsoft Defender for servers D. Azure Policy E. Microsoft Defender for Containers ,E You are designing the security standards for a new Azure environment. You need to design a privileged identity strategy based on the Zero Trust model. Which framework should you follow to create the design? A. Enhanced Security Admin Environment (ESAE) B. Microsoft Security Development Lifecycle (SDL) C. Rapid Modernization Plan (RaMP) D. Microsoft Operational Security Assurance (OSA) Your company is preparing for cloud adoption. You are designing security for Azure landing zones. Question No : 69 - (Topic 3) Question No : 70 - (Topic 3) Question No : 71 - (Topic 3) Microsoft SC-100 45 Which two preventative controls can you implement to increase the secure score? Each NOTE: Each correct selection is worth one point. A. Azure Firewall B. Azure Web Application Firewall (WAF) C. Microsoft Defender for Cloud alerts D. Azure Active Directory (Azure AD Privileged Identity Management (PIM) E. Microsoft Sentinel ,D You have Windows 11 devices and Microsoft 365 E5 licenses. You need to recommend a solution to prevent users from accessing websites that contain adult content such as gambling sites. What should you include in the recommendation? A. Microsoft Endpoint Manager B. Compliance Manager C. Microsoft Defender for Cloud Apps D. Microsoft Defender for Endpoint You need to design a solution to provide administrators with secure remote access to the virtual machines. The solution must meet the following requirements: • Prevent the need to enable ports 3389 and 22 from the internet. • Only provide permission to connect the virtual machines when required. • Ensure that administrators use the Azure portal to connect to the virtual machines. Which two actions should you include in the solution? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. A. Enable Azure Active Directory (Azure AD) Privileged Identity Management (PIM) roles as virtual machine contributors. B. Configure Azure VPN Gateway. C. Enable Just Enough Administration (JEA). Question No : 72 - (Topic 3) Question No : 73 - (Topic 3) Microsoft SC-100 46 D. Enable just-in-time (JIT) VM access. E. Configure Azure Bastion. ,E You have an Azure subscription that has Microsoft Defender for Cloud enabled. Suspicious authentication activity alerts have been appearing in the Workload protections dashboard. You need to recommend a solution to evaluate and remediate the alerts by using workflow automation. The solution must minimize development effort. What should you include in the recommendation? A. Azure Monitor webhooks B. Azure Logics Apps C. Azure Event Hubs D. Azure Functions apps You have a customer that has a Microsoft 365 subscription and an Azure subscription. The customer has devices that run either Windows, iOS, Android, or macOS. The Windows devices are deployed on-premises and in Azure. You need to design a security solution to assess whether all the devices meet the customer's compliance rules. What should you include in the solution? A. Microsoft Information Protection B. Microsoft Defender for Endpoint C. Microsoft Sentinel D. Microsoft Endpoint Manager Question No : 74 - (Topic 3) Question No : 75 - (Topic 3) Question No : 76 - (Topic 3) Microsoft SC-100 47 You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance. You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance. Solution: You recommend configuring gateway-required virtual network integration. Does this meet the goal? A. Yes B. No Your company has an Azure App Service plan that is used to deploy containerized web apps. You are designing a secure DevOps strategy for deploying the web apps to the App Service plan. You need to recommend a strategy to integrate code scanning tools into a secure software development lifecycle. The code must be scanned during the following two phases: Uploading the code to repositories Building containers Where should you integrate code scanning for each phase? To answer, select the appropriate options in the answer area. Answer: Question No : 77 HOTSPOT - (Topic 3) Microsoft SC-100 48 You receive a security alert in Microsoft Defender for Cloud as shown in the exhibit. (Click the Exhibit tab.) After remediating the threat which policy definition should you assign to prevent the threat from reoccurring? A. Storage account public access should be disallowed B. Azure Key Vault Managed HSM should have purge protection enabled C. Storage accounts should prevent shared key access D. Storage account keys should not be expired You have an on-premises network that has several legacy applications. The applications perform LDAP queries against an existing directory service. You are migrating the onpremises infrastructure to a cloud-only infrastructure. You need to recommend an identity solution for the infrastructure that supports the legacy applications. The solution must minimize the administrative effort to maintain the infrastructure. Which identity service should you include in the recommendation? Question No : 78 - (Topic 3) Question No : 79 - (Topic 3) Microsoft SC-100 49 A. Azure Active Directory Domain Services (Azure AD DS) B. Azure Active Directory (Azure AD) B2C C. Azure Active Directory (Azure AD) D. Active Directory Domain Services (AD DS) Your on-premises network contains an e-commerce web app that was developed in Angular and Node.js. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone. You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model. Solution: You recommend implementing Azure Front Door with Azure Web Application Firewall (WAF). Does this meet the goal? A. Yes B. No Your company is migrating data to Azure. The data contains Personally Identifiable Information (Pll). The company plans to use Microsoft Information Protection for the Pll data store in Azure. You need to recommend a solution to discover Pll data at risk in the Azure resources. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Question No : 80 - (Topic 3) Question No : 81 HOTSPOT - (Topic 3) Microsoft SC-100 50 Answer: You have an Azure subscription that contains several storage accounts. The storage accounts are accessed by legacy applications that are authenticated by using access keys. You need to recommend a solution to prevent new applications from obtaining the access keys of the storage accounts. The solution must minimize the impact on the legacy applications. What should you include in the recommendation? A. Apply read-only locks on the storage accounts. B. Set the AllowSharcdKeyAccess property to false. C. Set the AllowBlobPublicAcccss property to false. D. Configure automated key rotation. Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud. The company signs a contract with the United States government. You need to review the current subscription for NIST 800-53 compliance. What should you do first? Question No : 82 - (Topic 3) Question No : 83 - (Topic 3) Microsoft SC-100 51 A. From Defender for Cloud, review the Azure security baseline for audit report. B. From Defender for Cloud, add a regulatory compliance standard. C. From Defender for Cloud, enable Defender for Cloud plans. D. From Defender for Cloud, review the secure score recommendations. You have a Microsoft 365 E5 subscription. You need to recommend a solution to add a watermark to email attachments that contain sensitive data. What should you include in the recommendation? A. Microsoft Defender for Cloud Apps B. insider risk management C. Microsoft Information Protection D. Azure Purview You have Microsoft Defender for Cloud assigned to Azure management groups. You have a Microsoft Sentinel deployment. During the triage of alerts, you require additional information about the security events, including suggestions for remediation. Which two components can you use to achieve the goal? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. workload protections in Defender for Cloud B. threat intelligence reports in Defender for Cloud C. Microsoft Sentinel notebooks D. Microsoft Sentinel threat intelligence workbooks Question No : 84 - (Topic 3) Question No : 85 - (Topic 3) Question No : 86 - (Topic 3) Microsoft SC-100 52 You have an Azure subscription that is used as an Azure landing zone for an application. You need to evaluate the security posture of all the workloads in the landing zone. What should you do first? A. Add Microsoft Sentinel data connectors. B. Configure Continuous Integration/Continuous Deployment (CI/CD) vulnerability scanning. C. Enable the Defender plan for all resource types in Microsoft Defender for Cloud. D. Obtain Azure Active Directory Premium Plan 2 licenses. You are creating the security recommendations for an Azure App Service web app named App1. App1 has the following specifications: • Users will request access to App1 through the My Apps portal. A human resources manager will approve the requests. • Users will authenticate by using Azure Active Directory (Azure AD) user accounts. You need to recommend an access security architecture for App1. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Answer: Question No : 87 HOTSPOT - (Topic 3) Microsoft SC-100 53 You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance. You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance. Solution: You recommend access restrictions based on HTTP headers that have the Front Door ID. Does this meet the goal? A. Yes B. No Your company plans to provision blob storage by using an Azure Storage account The blob storage will be accessible from 20 application sewers on the internet. You need to recommend a solution to ensure that only the application servers can access the storage account. What should you recommend using to secure the blob storage? A. service tags in network security groups (NSGs) B. managed rule sets in Azure Web Application Firewall (WAF) policies C. inbound rules in network security groups (NSGs) D. firewall rules for the storage account E. inbound rules in Azure Firewall Your company has devices that run either Windows 10, Windows 11, or Windows Server. You are in the process of improving the security posture of the devices. You plan to use security baselines from the Microsoft Security Compliance Toolkit. What should you recommend using to compare the baselines to the current device configurations? Question No : 88 - (Topic 3) Question No : 89 - (Topic 3) Question No : 90 - (Topic 3) Microsoft SC-100 54 A. Microsoft Intune B. Policy Analyzer C. Local Group Policy Object (LGPO) D. Windows Autopilot You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report as shown in the following exhibit. Question No : 91 - (Topic 3) Microsoft SC-100 55 You need to verify whether Microsoft Defender for servers is installed on all the virtual machines that run Windows. Which compliance control should you evaluate? A. Data Protection B. Incident Response C. Posture and Vulnerability Management D. Asset Management E. Endpoint Security Microsoft SC-100 56 You have a customer that has a Microsoft 365 subscription and uses the Free edition of Azure Active Directory (Azure AD) The customer plans to obtain an Azure subscription and provision several Azure resources. You need to evaluate the customer's security environment. What will necessitate an upgrade from the Azure AD Free edition to the Premium edition? A. role-based authorization B. Azure AD Privileged Identity Management (PIM) C. resource-based authorization D. Azure AD Multi-Factor Authentication You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report. In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls. Solution: You recommend enabling adaptive network hardening. Does this meet the goal? A. Yes B. No Your company has a hybrid cloud infrastructure that contains an on-premises Active Directory Domain Services (AD DS) forest, a Microsoft B65 subscription, and an Azure subscription. The company's on-premises network contains internal web apps that use Kerberos authentication. Currently, the web apps are accessible only from the network. You have remote users who have personal devices that run Windows 11. Question No : 92 - (Topic 3) Question No : 93 - (Topic 3) Question No : 94 - (Topic 3) Microsoft SC-100 57 You need to recommend a solution to provide the remote users with the ability to access the web apps. The solution must meet the following requirements: • Prevent the remote users from accessing any other resources on the network. • Support Azure Active Directory (Azure AD) Conditional Access. • Simplify the end-user experience. What should you include in the recommendation? A. Azure AD Application Proxy B. Azure Virtual WAN C. Microsoft Tunnel D. web content filtering in Microsoft Defender for Endpoint You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance. You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance. Solution: You recommend access restrictions that allow traffic from the Front Door service tags. Does this meet the goal? A. Yes B. No You have a Microsoft 365 E5 subscription. You are designing a solution to protect confidential data in Microsoft SharePoint Online sites that contain more than one million documents. You need to recommend a solution to prevent Personally Identifiable Information (Pll) from Question No : 95 - (Topic 3) Question No : 96 - (Topic 3) Microsoft SC-100 58 being shared. Which two components should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. A. data loss prevention (DLP) policies B. sensitivity label policies C. retention label policies D. eDiscovery cases Your company develops several applications that are accessed as custom enterprise applications in Azure Active Directory (Azure AD). You need to recommend a solution to prevent users on a specific list of countries from connecting to the applications. What should you include in the recommendation? A. activity policies in Microsoft Defender for Cloud Apps B. sign-in risk policies in Azure AD Identity Protection C. device compliance policies in Microsoft Endpoint Manager D. Azure AD Conditional Access policies E. user risk policies in Azure AD Identity Protection Your company plans to move all on-premises virtual machines to Azure. A network engineer proposes the Azure virtual network design shown in the following table. You need to recommend an Azure Bastion deployment to provide secure remote access to Question No : 97 - (Topic 3) Question No : 98 - (Topic 3) Microsoft SC-100 59 all the virtual machines. Based on the virtual network design, how many Azure Bastion subnets are required? A. 1 B. 2 C. 3 D. 4 E. 5 Your company has an on-premises network and an Azure subscription. The company does NOT have a Site-to-Site VPN or an ExpressRoute connection to Azure. You are designing the security standards for Azure App Service web apps. The web apps will access Microsoft SQL Server databases on the network. You need to recommend security standards that will allow the web apps to access the databases. The solution must minimize the number of open internet-accessible endpoints to the on-premises network. What should you include in the recommendation? A. a private endpoint B. hybrid connections C. virtual network NAT gateway integration D. virtual network integration Your company has Microsoft 365 E5 licenses and Azure subscriptions. The company plans to automatically label sensitive data stored in the following locations: • Microsoft SharePoint Online • Microsoft Exchange Online Question No : 99 - (Topic 3) Question No : 100 DRAG DROP - (Topic 3) Microsoft SC-100 60 • Microsoft Teams You need to recommend a strategy to identify and protect sensitive data. Which scope should you recommend for the sensitivity label policies? To answer, drag the appropriate scopes to the correct locations. Each scope may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Answer: Your company is developing a modern application that will run as an Azure App Service web app. You plan to perform threat modeling to identify potential security issues by using the Microsoft Threat Modeling Tool. Which type of diagram should you create? A. dataflow B. system flow C. process flow D. network flow Your company has a Microsoft 365 E5 subscription. The company wants to identify and classify data in Microsoft Teams, SharePoint Online, and Exchange Online. You need to Question No : 101 - (Topic 3) Question No : 102 - (Topic 3) Microsoft SC-100 61 recommend a solution to identify documents that contain sensitive information. What should you include in the recommendation? A. data classification content explorer B. data loss prevention (DLP) C. eDiscovery D. Information Governance Your company has a Microsoft 365 subscription and uses Microsoft Defender for Identity. You are informed about incidents that relate to compromised identities. You need to recommend a solution to expose several accounts for attackers to exploit. When the attackers attempt to exploit the accounts, an alert must be triggered. Which Defender for Identity feature should you include in the recommendation? A. standalone sensors B. honeytoken entity tags C. sensitivity labels D. custom user tags A customer has a Microsoft 365 E5 subscription and an Azure subscription. The customer wants to centrally manage security incidents, analyze log, audit activity, and hunt for potential threats across all deployed services. You need to recommend a solution for the customer. The solution must minimize costs. What should you include in the recommendation? A. Microsoft 365 Defender B. Microsoft Defender for Cloud C. Microsoft Defender for Cloud Apps D. Microsoft Sentinel Question No : 103 - (Topic 3) Question No : 104 - (Topic 3) Microsoft SC-100 62 Your company has a Microsoft 365 E5 subscription. Users use Microsoft Teams, Exchange Online, SharePoint Online, and OneDrive for sharing and collaborating. The company identifies protected health information (PHI) within stored documents and communications. What should you recommend using to prevent the PHI from being shared outside the company? A. insider risk management policies B. data loss prevention (DLP) policies C. sensitivity label policies D. retention policies Question No : 105 - (Topic 3) Microsoft SC-100 63 [Show More]
Last updated: 3 years ago
Preview 1 out of 63 pages
![Preview image of Microsoft Exam SC-100 Microsoft Cybersecurity Architect Version: 3.0 [ Total Questions: 105 ]. All Answers Provided_Score 100% document](https://scholarfriends.com/storage/sc_100__3_.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$14.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 14, 2022
Number of pages
63
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 14, 2022
Downloads
0
Views
90




 JN21.png)







