Computer Science > QUESTIONS & ANSWERS > CompTIA Security+ SY0-601 Study Guide Questions with Complete solutions. Rated A (All)
CompTIA Security+ SY0-601 Study Guide Questions with Complete solutions. Rated A
Document Content and Description Below
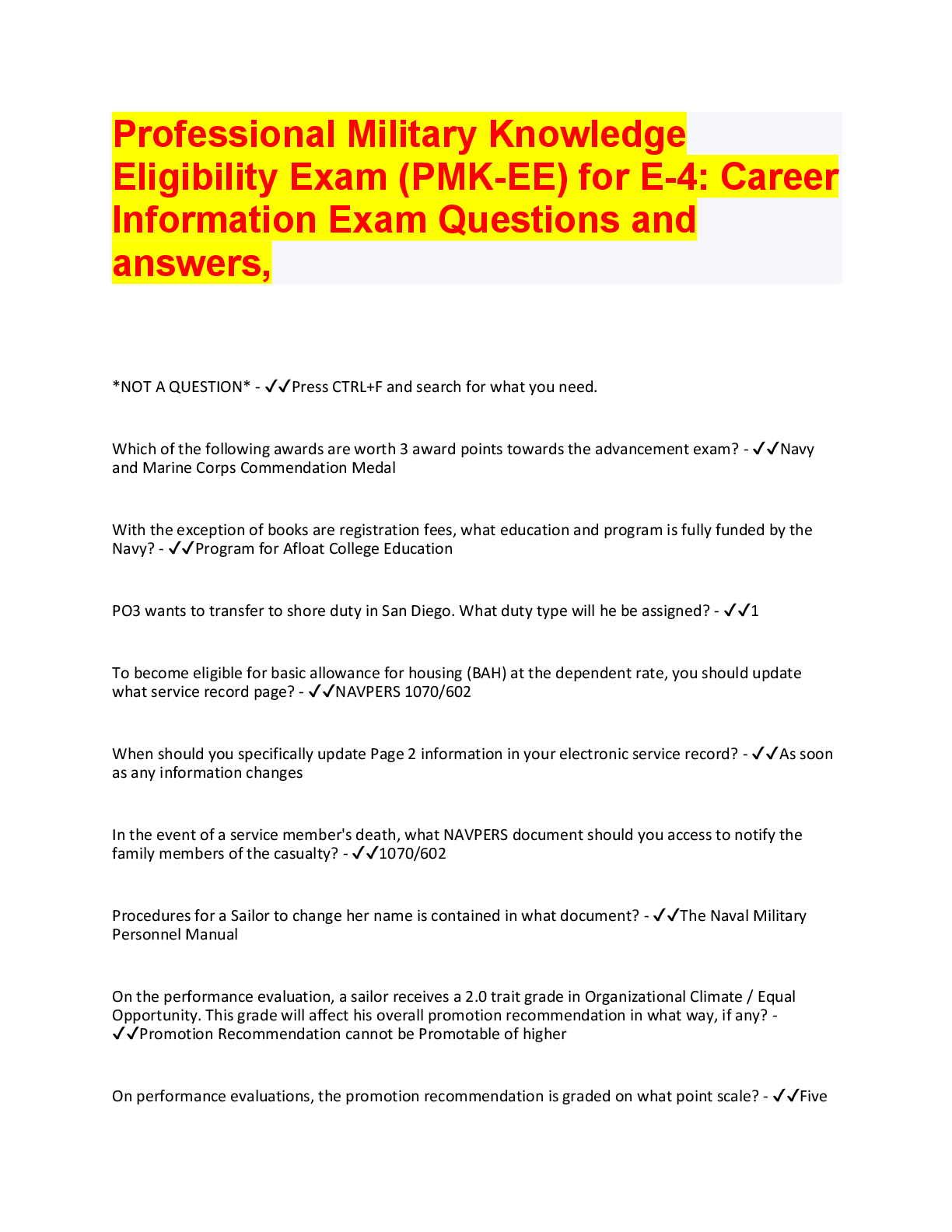
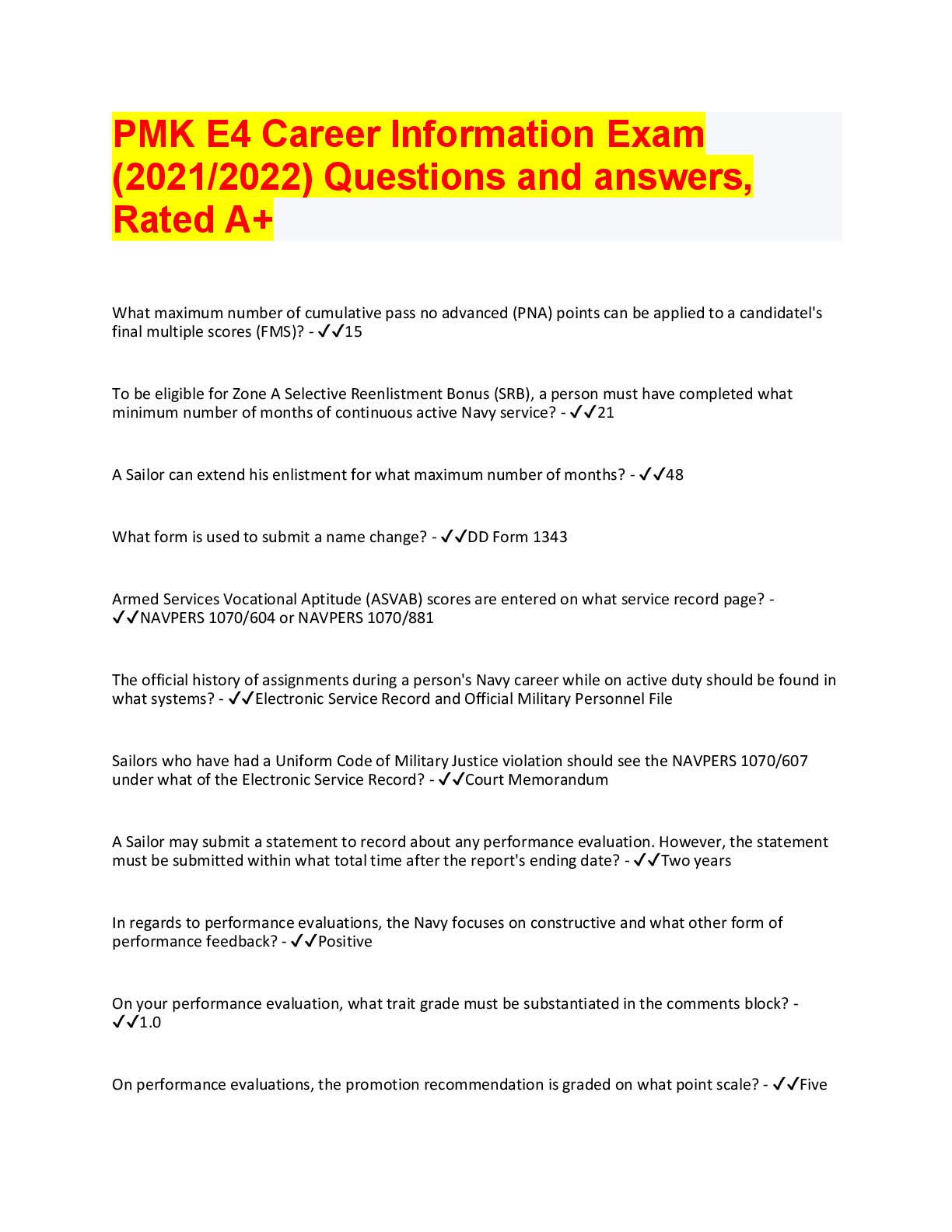
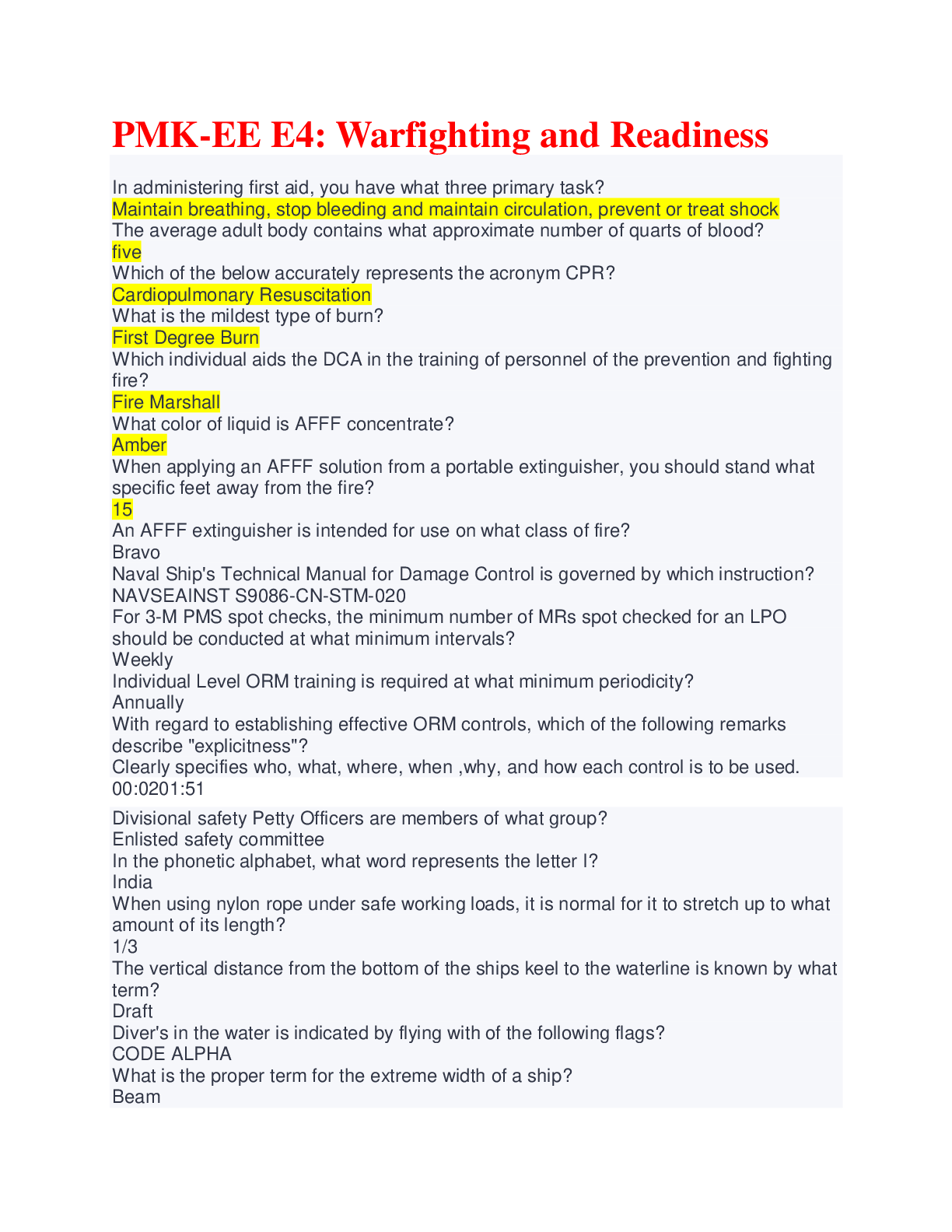
CompTIA Security+ SY0-601 Study Guide Questions with Complete solutions What type of certificate does a CA have? -Answer- Root Certificate; used to sign keys If I am going to use a CA internally, w... hat type of CA should I use? -Answer- Private CA If I want to carry out a B2B activity with third-party companies or sell products on the web, what type of certificate should I use? -Answer- Public CA Why would I make my CA offline when not in use? -Answer- Military, Security, or Banking Organizations; preventing data from being compromised. Who signs X.509 certificates? -Answer- Central Authorities (CA) Who builds the CA or intermediate authorities? -Answer- Architect What can I use to prevent my CA from being compromised and fraudulent certificates being issued? -Answer- Certificate Pinning If two entities what to set up a cross-certification, what must they set up first? -AnswerRoot CAs using a bridge trust model What type of trust model does PGP use? -Answer- Web of Trust How can I tell if my certificate is valid? -Answer- Certificate Revocation List (CRL) If the CRL is going slow, what should I implement? -Answer- Online Certification Status Protocol (OCSP) Explain certificate stapling/OCSP stapling -Answer- Web servers use an OCSP for faster authentication bypassing the CRL What is the process of obtaining a new certificate -Answer- Certificate Signing Request (CSR) What is the purpose of key escrow? -Answer- Holds an provides access to 3rd party keys provided the need. What is the purpose of Hardware Security Model (HSM) -Answer- Used by key escrow to store and manage keys What is the purpose of DRA and what does it require in order to complete its role effectively? -Answer- When a users private key becomes corrupt, the DRA recovers data by obtaining a copy of the private key from the key escrow.How can I identify each certificate -Answer- Object Identifier (OID) or the serial number What format is a private certificate? -Answer- P12 What file extension is a private certificate? -Answer- .pfx extension What format is a public certificate? -Answer- P7B What file extension is a public certificate? -Answer- .cer extension What format is a PEM certificate? -Answer- Base64 What type of certificate can be used on multiple servers in the same domain -AnswerWildcard (denoted by a *) What type of certificate can be used on multiple domains? -Answer- Subject Alternative Name (SAN) What should I do with my software to verify that it is original and not a fake copy (verify integrity)? -Answer- Code Signing What is the purpose of extended validation of an X.509 certificate? -Answer- Provides Financial institutions with a higher level of trust. What is the purpose of DH? -Answer- Creates a secure tunnel; during a VPN connection (on port 500), used during IKE What two things does digitally signing an email provide? -Answer- Integrity and Nonrepudiation What asymmetric encryption algorithm should I use to encrypt data on a smartphone? - Answer- ECC (Elliptic Curve Cryptography) What shall I use to encrypt a military mobile phone? -Answer- AES-256 Name two key stretching algorithms -Answer- Bcrypt & PBKDF2 What is the purpose of key stretching? -Answer- To make weak passwords less volatile to brute-force attacks What happens to Cipher Block Chaining (CBC) if I do not have all the blocks? -AnswerNo decryption is possible If I want to ensure integrity of data, what shall I use? -Answer- MD5 & SHA-1What type of man-in-the-middle (MITM) attack is SSL 3.0 (CBC) vulnerable to? - Answer- POODLE What is the usage of Diffie Hellman Ephemeral (DHE) and Elliptic Curve Diffie Hellman Ephemeral (ECDHE) -Answer- one time keys What is the strongest method of encryption with an L2TP/IPSec VPN Tunnel -AnswerAES What is the weakest method of encryption with an L2TP/IPSec VPN Tunnel -AnswerDES What is the name of the key used to ensure the security of communication between a computer and a server or a computer to another computer? -Answer- Session key What should I do to protect data at rest on a laptop? -Answer- Full Disk Encryption (FDE) What should I do to protect data at rest on a tablet or smartphone? -Answer- Full Device Encryption (FDE) What should I do to protect data at rest on a backend server? -Answer- Ensure database encryption What should I do to protect data at rest on a removable device, such as a USB drive or external hard drive? -Answer- Data Loss Prevention (DLP) or FDE What two protocols protect data in transit? -Answer- Transport Layer Security (TLS) or HTTPS How can I protect data in use? -Answer- Full memory encryption What is the purpose of obfuscation? -Answer- Provided source code is compromised the code will be obscure; using either XOR or ROT13. What is the purpose of perfect forward secrecy? -Answer- There is no link between the server's session key and the private key. What type of attack tries to find two has values that match? -Answer- Collision attack What is the purpose of rainbow tables? -Answer- Maintain a precomputed table of hash values for words Explain the purpose of password salting -Answer- ensures that duplicate passwords are never stored. increases the key size making it less vulnerable to brute-force attacks.What is the most common form of authentication that is most likely to be entered incorrectly -Answer- password When I purchase a new wireless access point, what should I do first? -Answer- Change default credintials What is password history? -Answer- The number of passwords you can use before using the current password How can I prevent someone from reusing the same password? -Answer- Adjusting the minimum password age Explain what format a complex password takes. -Answer- Uses 3 of the following: 1. Uppercase 2. Lowercase 3. Number 4. Special Character How can I prevent a hacker from inserting a password multiple times? -AnswerAccount lockout - threshold What type of factor authentication is a smart card? -Answer- Multi-factor or dual factor What authentication method can be used by two third parties that participate in a joint venture? -Answer- federation What is an XML-based authentication protocol -Answer- Security Assertion Markup Language (SAML) What is Shibboleth? -Answer- Open source federation that uses SAML authentication What protocol is used to store and search for Active Directory (AD) objects -AnswerLDAP What authentication factor uses tickets, timestamps, and updated sequence numbers and is used to prevent replay attacks? -Answer- Kerberos What is a Ticket Granting Ticket (TGT) session? -Answer- User sends there credentials (username and password) to a domain controller that authenticates and provides a receive ticket allowing user access to the session. What is single sign-on? Give two examples? -Answer- Kerberos & Federation Services How can I prevent a pass-the-hash attack? -Answer- Not enabling NTLMGive an example of when you would use Open ID connect -Answer- When you need to access a device using 3rd party credentials (sign-in with google) Name two AAA servers and the ports associated with them. -Answer- TACACS+ on port 49 RADIUS on port 1812 What is used for accounting in an AAA server? -Answer- RADIUS on port 1813 What is the purpose of a VPN solution? -Answer- Secure connection for a remote location Why should we never use PAP authentication? -Answer- Passwords are transmitted in plain text What is Type II in biometric authentication an why is it a security risk? -Answer- Failure acceptance rate What is a time-limited password? -Answer- Password is only available for a limited amount of time How many times can you use an HOTP password? Is there a time restriction? -AnswerOne time; there is no time before it expires How does a CAC differ from a smart card and who uses a CAC? -Answer- Military personal What type of account is a service account? -Answer- An administrative account that allows for an application to run with higher privileges. (firewall) How many accounts should a system administrator have? -Answer- Two accounts one for day-to-day and one for admin. task What do I need to do when I purchase a baby monitor? -Answer- Change the default username and password What is a privileged account? -Answer- Account with administrative rights What is the drawback for security if the company uses shard accounts? -Answer- When auditing account the activity cannot be traced to a single user The system administrator in a multinational corporation creates a user account using an employee's first name and last name. Why are they doing this time after time? -AnswerStandard naming conventionsWhat two actions do I need to complete when John Smith leaves the company? - Answer- Disable his account and reset the password What is account recertification? -Answer- Audit of user account and privileges What is the purpose of a user account review? -Answer- Ensures old accounts are deleted and current users have correct privileges What can I implement to find out immediately when a user is placed in a group that may give them a hight level of privilege? -Answer- SIEM System What will be the two possible outcomes if an auditor finds any working practices that do not confirm to the companies policy? -Answer- Either change of management or new policies If a contractor brings in five consultants for two months of mail server migration, how should I set up their accounts? -Answer- Accounts should be set up to expire on or before the last day of the contract. How can I ensure that users are only allowed access to the company network between the times of 9:00am - 5:00pm? -Answer- Rule-based access control that only allows for activity durning this time If I have a company that has five consultants who work in different shift patterns, how can I set up their accounts so that each of them can only access the network during thier individual shift? -Answer- Time of day restrictions that align with their schedules A brute-force attack cracks a password using all combinations of characters and will eventually crack a password. What can I do to prevent brute-force attacks? -AnswerAccount lockout The IT team have a global group called IT Admin; each member of the IT team are members of this group and therefore have full control access to the departmental data. Two new apprentices are joining the company and they need to have read access to the IT data. How can you achieve this with the minimum amount of administrative effort? - Answer- Create a group account with only the privileges required I have different login details and passwords to access Airbnb, Twitter, Facebook, and Google but I keep getting them mixed up and have locked myself out of these accounts from time to time. What can I implement on my Windows 10 laptop to help me? - Answer- Credential Manager I have moved departments, but the employees in my old department still use my old account for access; what should the company have done to prevent this from happening? What should their next action be? -Answer- Disable and lock out the account. The next action should be an account review.What is the purpose of ssh-copy-id command -Answer- The purpose is to copy and install public keys on a SSH server, and add to the list of authorized keys. When I log in to my Dropbox account from my phone, I get an email asking me to confirm that this was a legal login. What have I been subjected to? -Answer- Risky login What is the purpose of a password valut and how secure is it? -Answer- The purpose is to store passwords and keys. It is only as secure as the master key. What type of knowledge-based authentication would a bank normally use? -AnswerDynamic KBA that asks questions that have not already been answered What is a solution that helps protect privilege accounts? -Answer- Privileged access management stores privilege accounts in a bastion domain. FAR -Answer- False Acceptance Rate FRR -Answer- False rejection rate. Also called the false nonmatch rate. A rate that identifies the percentage of times a biometric authentication system incorrectly rejects a valid match. Why do cloud providers adopt a zero-trust model? -Answer- They treat every login as unsafe to prevent unauthorized attempts at login What authentication model gives access to computer system even though the wrong credentials are being used? -Answer- Biometric authentication In a cloud environment what is elasticity? -Answer- Allows you to increase or decrease the cloud resources as you need In which cloud environment would I install the software and then have to update the patches? -Answer- Infrastructure as a Service (IaaS) What cloud model would I not be allowed to migrate to? -Answer- Software as a Service (SaaS) What is the major benefit of using a public cloud? -Answer- No capital expenditures What is a cloud single-tenant model? -Answer- Private cloud were you own and the infastructure What is a cloud multitenant model? -Answer- Public Cloud Describe how community cloud operates. -Answer- Where people from the same industry design and share the cost of a bespoke application and its hosting.Who is responsible for disaster recovery of hardware in a cloud environment? -AnswerCloud Service Provider (CSP) What is a Cloud Access Security Broker (CASB)? -Answer- person who ensures that the policies between on-premise and the cloud are followed What model is it if you own the premise and all of the IT infrastructures reside there? - Answer- On-premise What is a hybrid cloud model? -Answer- Where a company uses a mix of on-premise and the cloud What is distributive allocation? -Answer- Ensures that the load is spread evenly among resources. Ensuring that no one resource gets overloaded. Ex. load balancer. What type of model deals with Identity and Access Management? -Answer- Security as a Service (SECaaS) Where will a diskless virtual host access its storage? -Answer- Storage Area Network (SAN) If you have a virtual switch that resides on a SAN, what connector will you use for a VLAN? -Answer- iSCSI What type of disks does a SAN use? -Answer- Fast disk, SSDs What is the machine that holds a number of VMs called? -Answer- Host; needs to have fast CPU, memory, and disk speed What is a guest, and what can you use as a rollback option? -Answer- A guest is a Virtual Machine (VM); and you can use snapshots for roll backs. In a virtual environment what is a sandbox and how does it relate to chroot jail? - Answer- A sandbox is a separation of the Virtual Machine from the rest of the environment. Chroot jail is the Linux version of a sandbox. Which is faster for data recovery: a snapshot or a backup tape? -Answer- Snapshoot What is a Type 1 Hypervisor? -Answer- Bare-metal hypervisor that doesn't need to be installed on an OS; examples include Hyper-V, ESX, Xen. What is a Type 2 Hypervisor? -Answer- Must be installed on a OS; examples include VirtualBoxWhy does HVAC produce availability for a data center? -Answer- HVAC supplies cold air and removes hot air What do you call the cloud model where people from the same industry share resources and the cost of the cloud model? -Answer- Community Cloud What is an example of cloud storage for a personal user? -Answer- iCloud, Google Drive, OneDrive, Dropbox Explain the functionality of Fog Computing. -Answer- Is an intermediary between the device and the cloud. It allows the data to be processed closer to the device. What is edge computing? -Answer- It allows data to be stored closer to the sensors rather than miles away in a data center What are containers? -Answer- Allows for the isolation of the applications and its files and libraries so the application is independent What is infrastructure as code? -Answer- This allows for the automation of your infrastructure What are cloud resource policies? -Answer- The combination of business and IT functions into a single business solution What is system sprawl, and what is a way to prevent it? -Answer- This is where a virtual machine or host has run out of resources. The best way to mitigate is to use thin provisioning. What is the best way to protect against VM escape? -Answer- VM escape is where an attacker will use a vulnerable VM to attack the host of another VM. Best protection is to ensure the hypervisor and all VMs are fully patched. What is a cloud region, and how can it provide redundancy? -Answer- A region consisting of multiple physical location called zones; data can be spread across multiple zones to provide redundancy. What is secret management and why encryption levels protect the secret management key? -Answer- Uses a vault to store keys, passwords, tokens, and SSH keys used for privileged accounts. It uses RSA-2048 bit keys Explain the main difference between LRS and ZRS. Which one is the cheapest? - Answer- LRS replicates three copies of your data in a physical location (the cheapest). ZRS replicates three copies of your data to three separate zon [Show More]
Last updated: 2 years ago
Preview 1 out of 19 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$9.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 22, 2022
Number of pages
19
Written in
Seller

Reviews Received
Additional information
This document has been written for:
Uploaded
Sep 22, 2022
Downloads
0
Views
293











.png)
 A Total Of 100 Questions With Complete Solutions And Verified Answers.png)
 Questions With Complete Solutions And Answers.png)
.png)
.png)
.png)
.png)
.png)

 A Total Of 100 Questions With Complete Solutions And Verified Answers.png)

