Information Technology > QUESTIONS & ANSWERS > AWS Pro Questions with accurate answers, Graded A. 2022/2023. RATED A (All)
AWS Pro Questions with accurate answers, Graded A. 2022/2023. RATED A
Document Content and Description Below
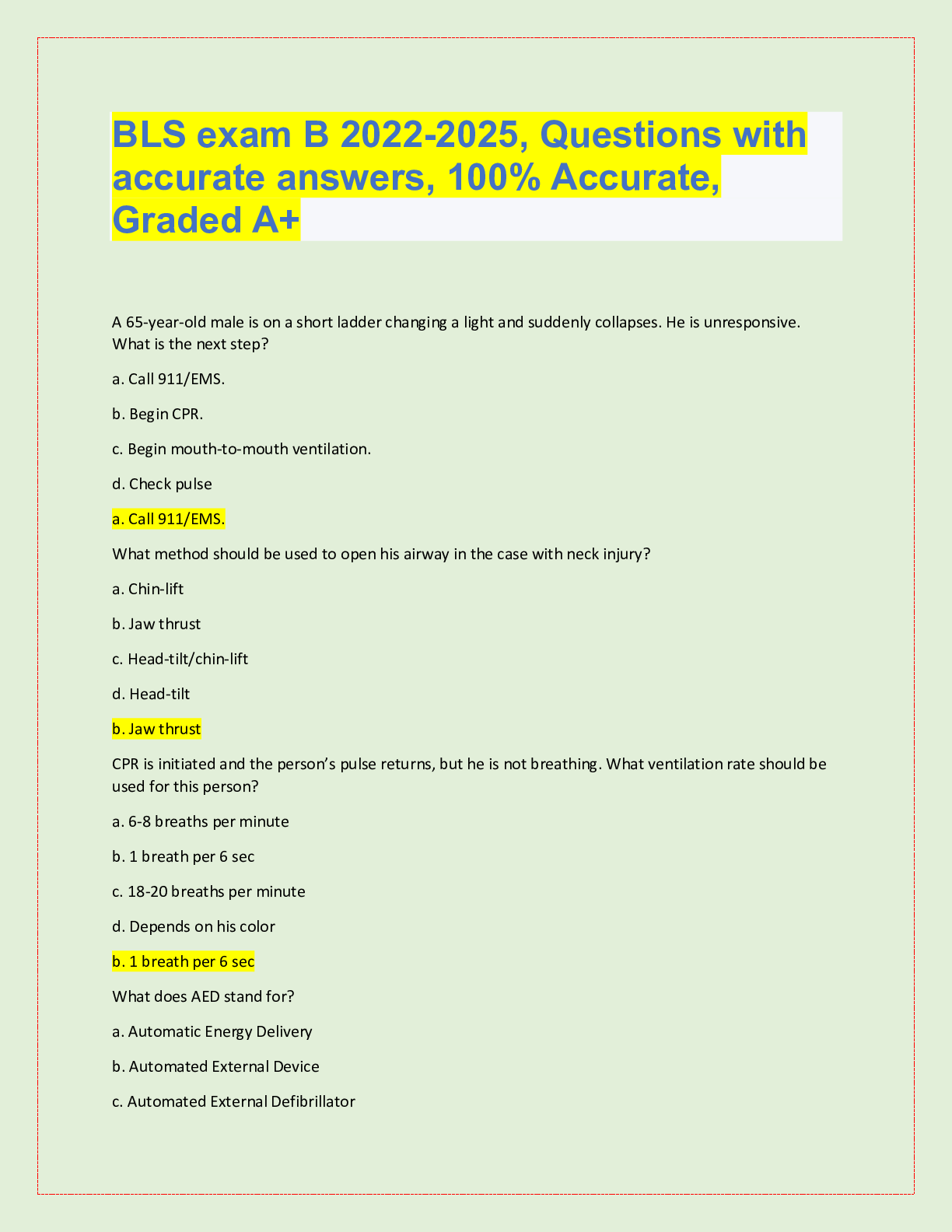
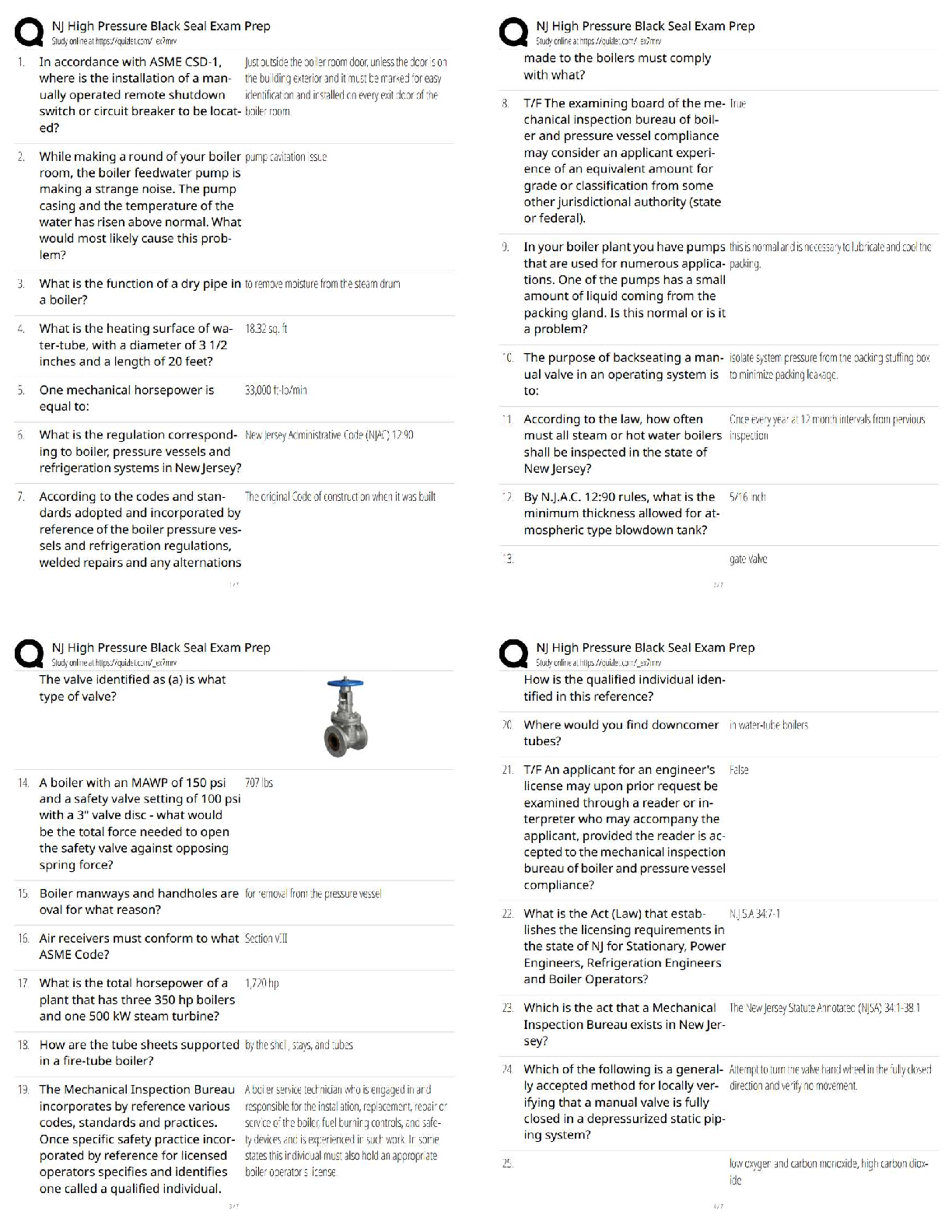
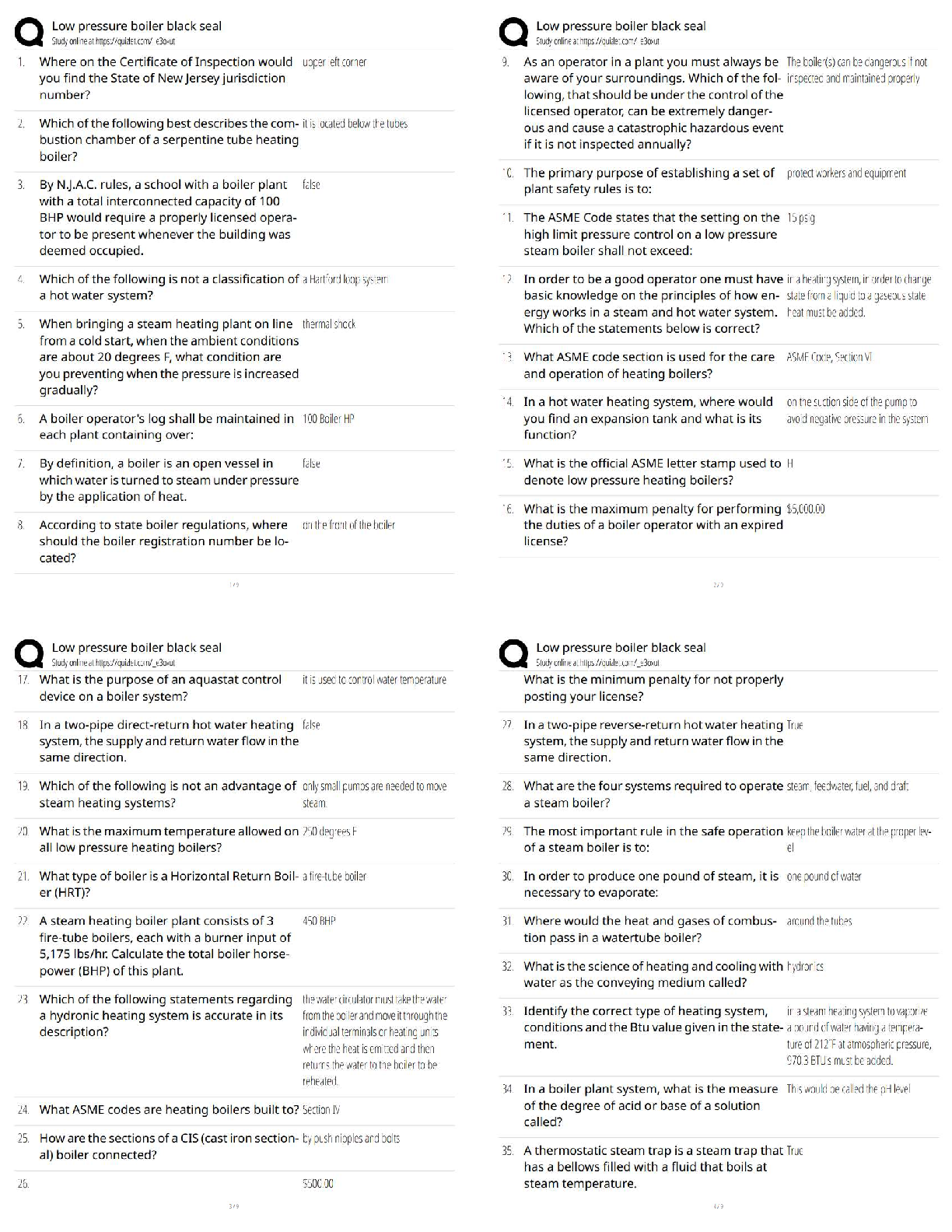
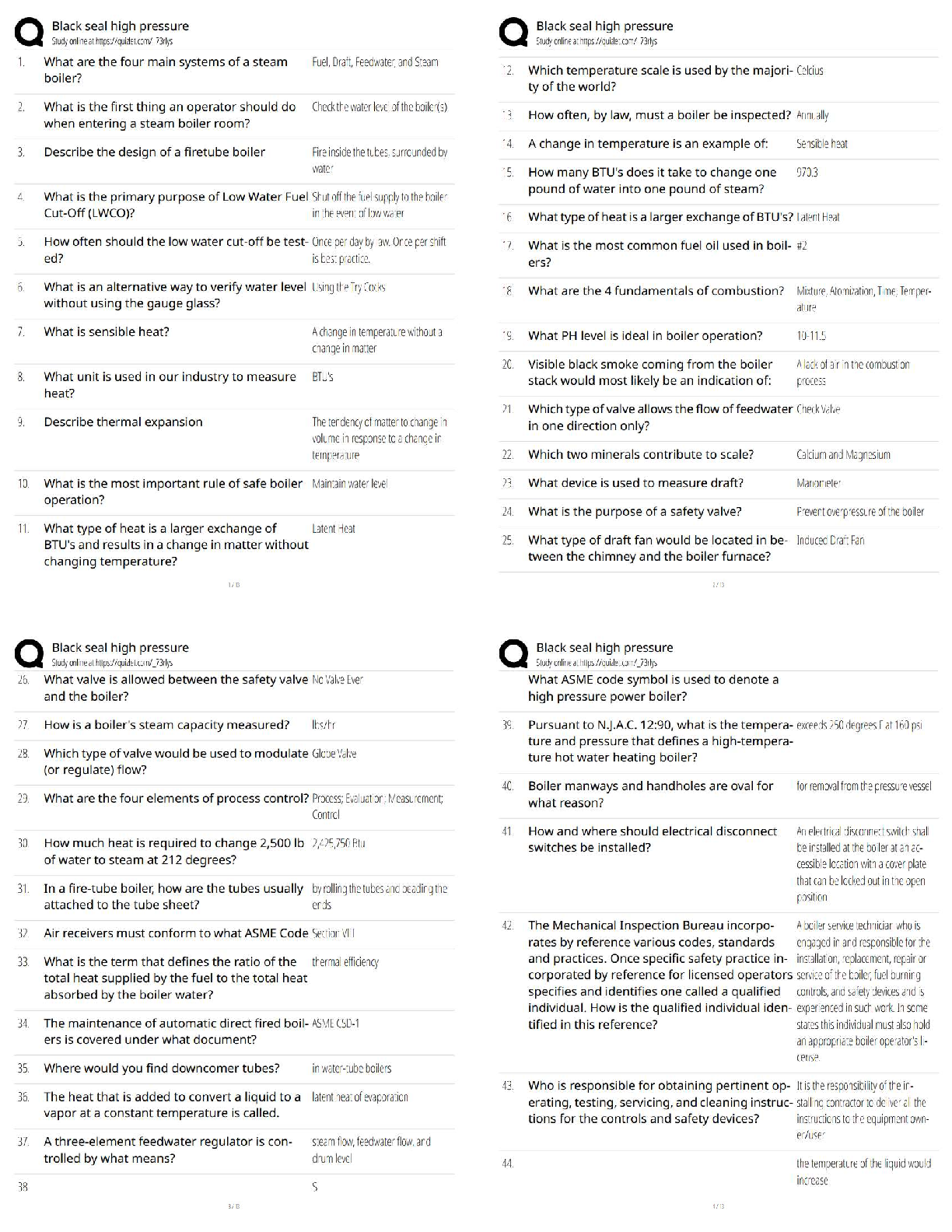
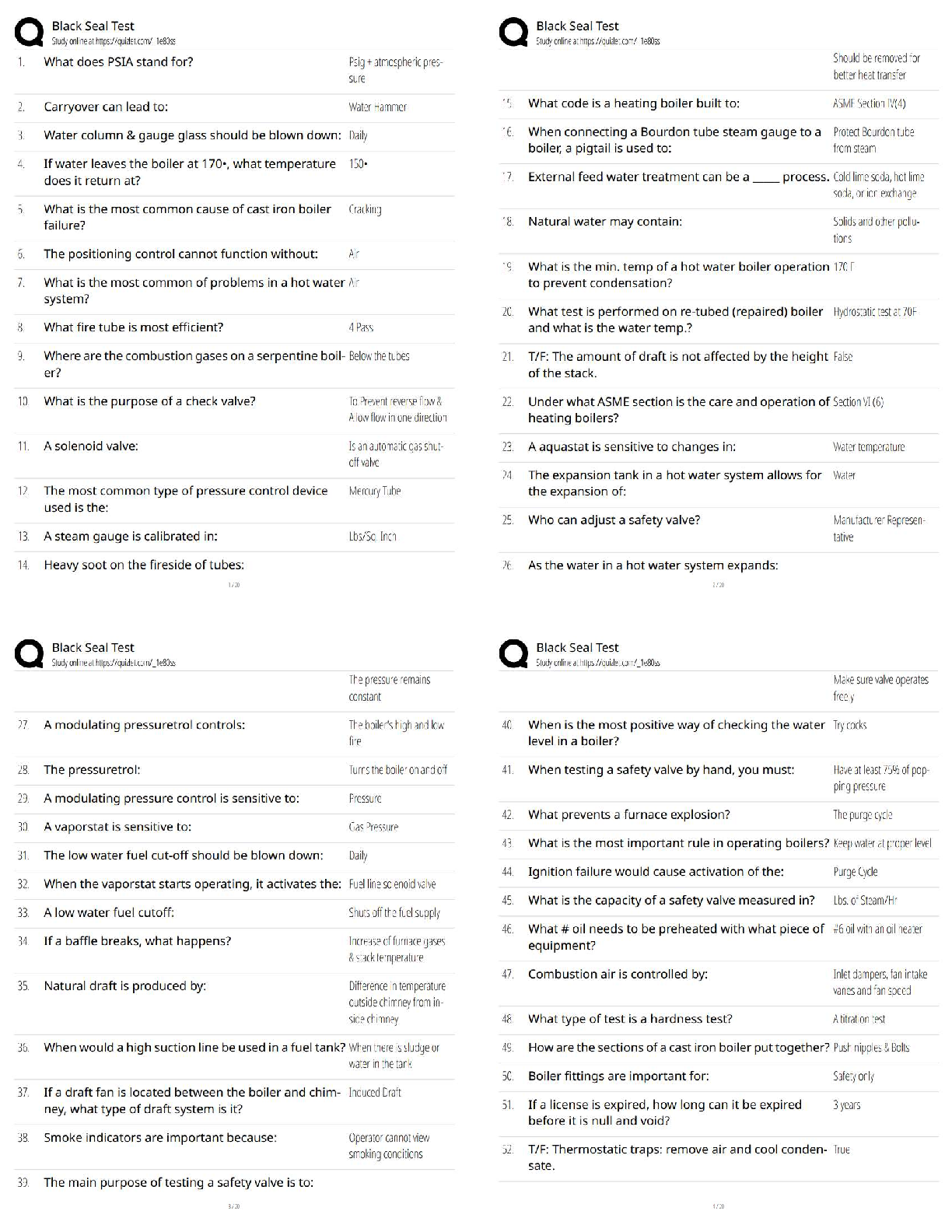
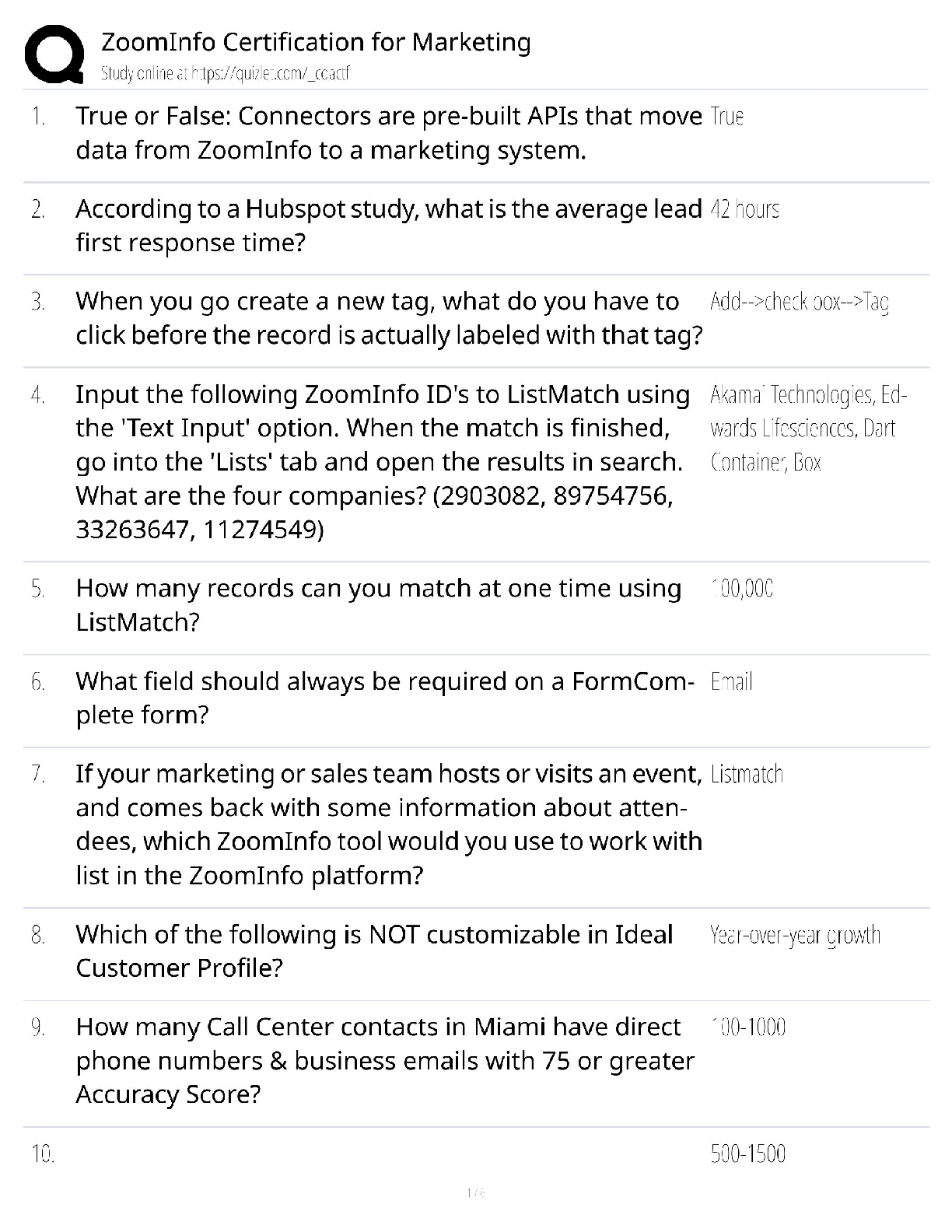
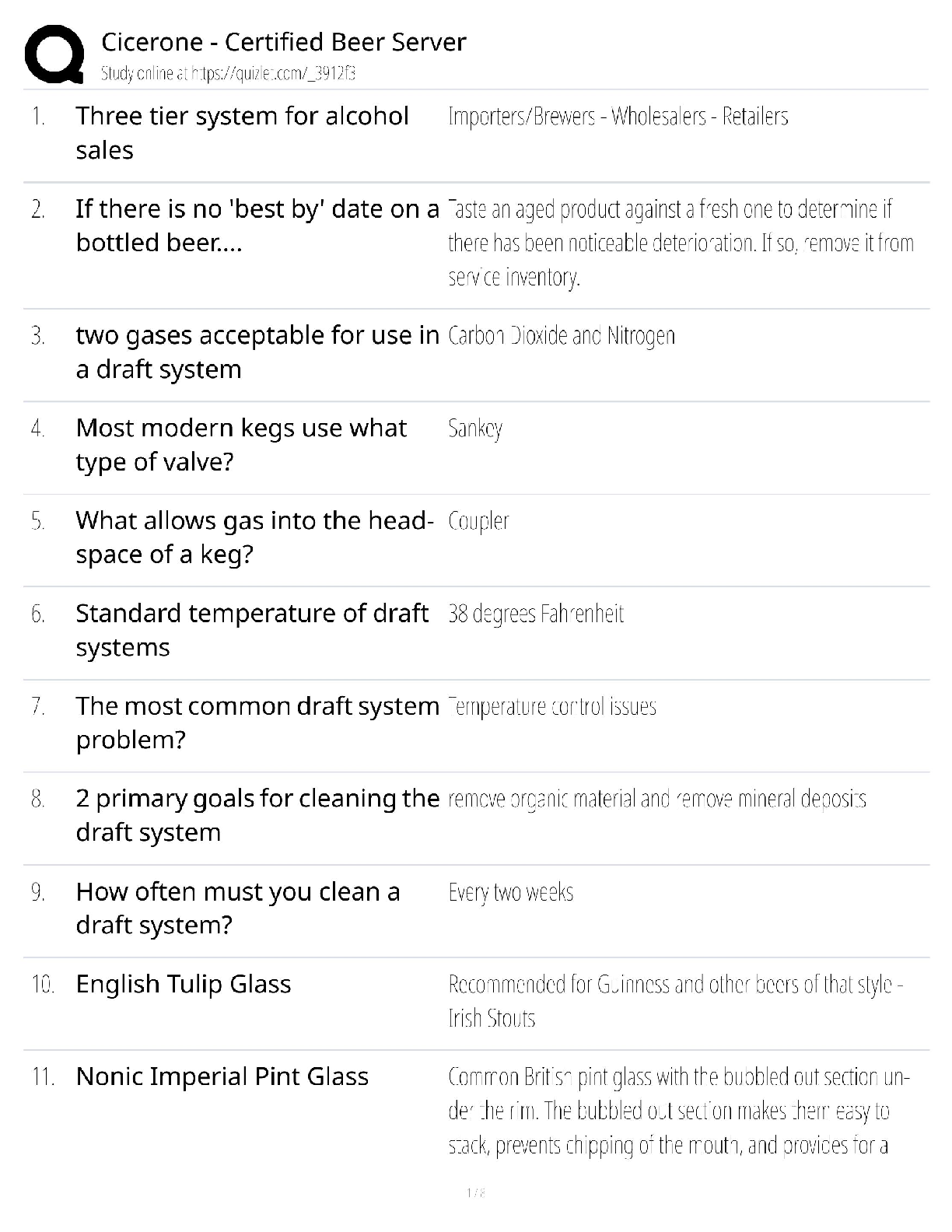
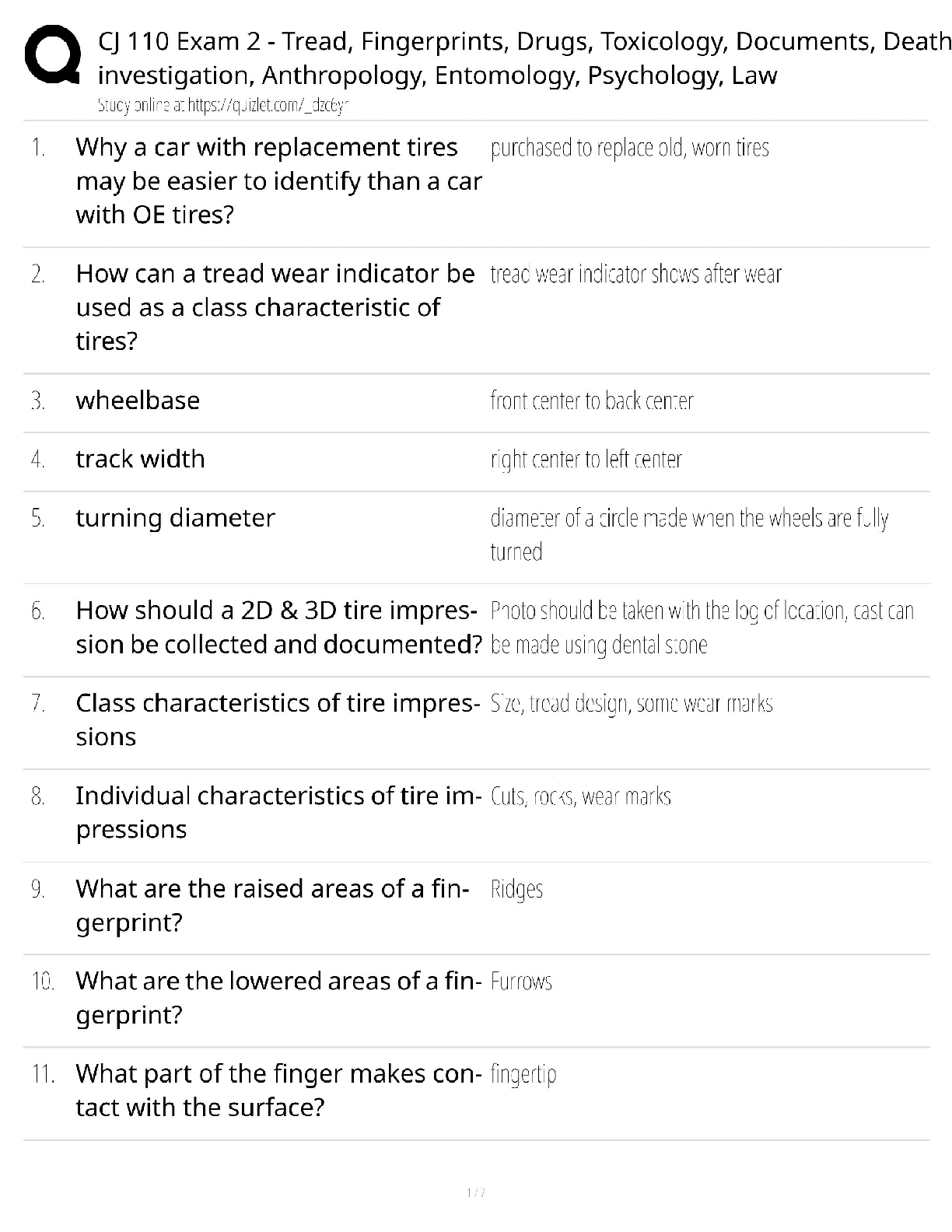
AWS Pro Questions with accurate answers, Graded A. 2022/2023. RATED A A development team that is currently doing a nightly six-hour build which is lengthening over time on -premises with a large ... and mostly underutilized server would like to transition to a continuous integration model of development on AWS with multiple builds triggered within the same day. However, they are concerned about cost, security, and how to integrate with existing on-premises applications such as their LDAP and email servers which cannot move off-premises. The development environment needs a source code repository, a project management system with a MySQL database, resources for performing builds, and a storage location for QA to pick up builds from. What AWS services combination would you recommend to meet the development team;s requirements? - ✔?A VPC with a VPN Gateway back to their on-premises servers, Amazon EC2 for the source-code repository with attached Amazon EBS volumes, Amazon EC2 and Amazon RDS MySQL for the project management system, EIPs for the source code repository and project management system, SQS for a build queue, An Auto Scaling group of EC2 instances for performing builds and S3 for the build output. (VPN gateway is required for secure connectivity. SQS for build queue and EC2 for builds) An AWS customer is deploying a web application that is composed of a front-end running on Amazon EC2 and confidential data that is stored on Amazon S3. The customers security policy requires that the all access operations to this sensitive data must be authenticated and authorized by centralized access managements system that is operated by separate security team. In addition, the a web application team that owns and administrators the EC2 web front-end instances is prohibited from having any ability to access the data that circumvents this centralized access management system. Which of the following configuration will support these requirements: - ✔?Configure the web application to authenticate end-users against the centralized access management system. Have the web application provision trusted users STS tokens entitling the download of approved data directly from Amazon S3 (Controlled access and admins cannot access the data as it needs authentication) Your company runs a complex customer relations management system that consists of around 10 different software components all backed by the same Amazon Relation Database Service (RDS) database. you adopted AWS OpsWorks to simplify management and deployment of that application and created an AWS OpsWorks stack with layers for each of the individual components. An internal security policy requires that all instances should run on the latest Amazon Linux AMI and that instances must be replaced within one month after the latest Amazon Linux AMI has been released. AMI replacements should be done without incurring apllication downtime or capacity problems. You decide to write a script to be run as soon as a new Amazon Linux AMI is released. Which solutions support the security policy and meet your requirements? - ✔?- Create a new stack and layers with identical configuration, add instances with the latest Amazon Linux AMI specified as a custom AMI to the new layer, switch DNS to the new stack, and tear down the old stack. (Blue-Green Deployment) - Add new instances with the latest Amazon Linux AMI specified as a custom AMI to all AWS OpsWorks layers of your stack, and terminate the old ones. Your customer is implementing a video on-demand streaming platform on AWS. The requirements are; support for multiple devices such as iOS, Andorid, and PC as client devices, using a standard client player, using streaming technology (not download,) and scalable architecture whit cost effectiveness. Which architecture meets the requirements? - ✔?Store the video contents to Amazon S3 as an origin server. Configure the Amazon CloudFront distribution with a download option to stream the video contents (Refer link) When deploying a highly available 2-tier web application on AWS, which combination of AWS Services meets the requirements? 1. AWS Direct Connect 2. Amazon Route 53 3. AWS Storage Geteway 4. Elastic Load Balancing 5. Amazon EC2 6. Auto Scaling 7. Amazon VPC 8. AWS Cloud Trail - ✔?2,4,5 and 6 You have been asked to virtually extend two existing data centers into AWS to support a highly available application that depends on existing, on0premises resources located in multiple data centers and static content that is served from an Amazon Simple Storeage Service (S3) bucket. Your disign current includes a dual-tunnel VPN connection between your CGW and VGW. Which component of your architecture represents a potential single point of failure that you should condider changing to make the solution more highly available? - ✔?Add another CGW in a different data center and create another dual-tunnel VPN connection. (Refer link) A customer is running an application in US-West (northern California) region and wants to setup disaster recovery failover to the Asian Pacific (Singapore) region. The customer is interested in chieving alow Recovery Point Objective (RPO) for an Amazon Relational Database Service (RDS) multi-AZ MySQL database instance. which approach is best suited to this need? - ✔?Asynchronous replication A research scientist is planning for the one-time launch of an Elastic MapReduce cluster and is encouraged by her manager to minimize costs. The cluster is designed to ingest 200TB of genomisc data with a total of 100 Amazon Elastic Compute Cloud (EC2) instances and is expected to run for around four hours. The resulting data set must be stored temporaly until archived into an Amazon Relational Database Service (RDS) Oracle instance. Which option will help save the most money while meeting requirements? - ✔?Store ingest and output files in Amazon S3. Deploy on-demand for the master and core nodes and spot for the task nodes. Your company currently has a highly available web application running in production. The application's web front-end utilize an Elastic Load Balancer and Auto Scaling across three Availability Zones. During peak load, your web servers operate at 90% utilization and leverage a combination of Heavy Utilization Reserved Instances for steady state load and On-Demand and Spot Instances for peak load, You are tasked with designing a cost effective architecture to allow the application to recover quickly in the event that an Availability Zone is unavailable during peak load. Which option provides the most most effective high availability architectural design for this application? - ✔?Increase auto scaling capacity and scaling thresholds to allow the web-front to cost-effectively scale across all availability zones to lower aggregate utilization levels that will allow an availability zone to fail during peak load without affecting the applications availability. (Ideal for HA to reduce and distribute load) A large enterprise wants to adopt CoudFormation to automate administrative tasks and implement the security principles of least priviledge and separation of duties. They have identified the following roles with the corresponding tasks in the company: - network administrators: create, modify and detele VPCs, subnets, NACLs, routing tables, and security groups - application operators: deploy complete application stacks (ELB, Auto-Scaling groups, RDS) whereas all resources must be deployed in the VPCs managed by the network administrators Both groups must maintain their own CloudFormation templates and should be able to create, update and delete only their own CloudFormation stacks. The company has followed your advice to create two IAMP groups, one for applications and one for networks. Both IAM groups are attached to IAM policies that grant rights to perform the necessary task of each group as well as the creation, update and deletion of CloudFormation stacks. Given setup and requirements, which statements represents valid design condiderations? - ✔?- Network stack updates will fail upon attempts to delete a subnet with EC2 instances (Subnets cannot be deleted with instances in them) - Restricting the launch of EC2 instances into VPCs requires resource level permissions in the IAM policy of the application group (IAM permissions need to be given explicitly to launch instances ) A customer is in the process of deploying multiple applications to AWS that are owned and operated by defferent development teams. Each development team maintains the authorization of its users independently from other teams. The customer's information security team would like to be able to delegate use authoriztion to the individual development teams but independently apply restrictions to the users permissions based on factor such as the user's device and location. For example, the information security team would like to grant read-only permissions to a user who defined by the development team as read/write whenever the user is authenticating from outside the corporate network. What steps can the information security team take to implement this capability? - ✔?Add additional IAM policies to the application IAM roles that deny user privileges based on information security policy. (Different policy with deny rules based on location, device and more restrictive wins) Your customer needs to create an application to allow contractors to upload videos to Amazon Simple Storeage Service (S3) so they can be transcoded into a different format. She creates AWS Indentity and Access Management (IAM) users for her application developers, and in just one week, thay have the application hosted on a fleet of Amazon Elastic Compute Cloud (EC2) instances. The attached IAM role is assigned to the instances. As expected, a contractor who authenticates to the application is givent a pre-signed URL that points to the location for video upload. However, contractors are reporting that they cannot upload their videos. Which of the following are valid reasons for this behavior? - ✔?- The application is not using valid security credentials to generate the pre-signed URL. - The pre-signed URL has expired. You are designing a file-sharing service. This service will have milions of files in it. Revenue for the service will come from fees based on how much storeage a user is using. You also want to store metadata on each file, such as title, description and whether the object is public or private. How do you archive all of these goals in a way that is economical and can scale to millions of users. - ✔?Store all files in Amazon S3. Create Amazon DynamoDB tables for the corresponding key-value pairs on the associated metadata, when objects are uploaded. To enable end-end HTTPS connections from the user's browser to the origin via CloudFront, which of the following options be valid? - ✔?- Use 3rd-party CA certificate in the origin and CloudFront default certificate in CloudFront - Use 3rd-party CA certificate in both origin and CloudFront A gaming company adopted AWS CoudFormation to automate load-testing of their games. They have created an AWS CloudFormation template for each gaming environment and one for the load-testing stack. The load-testing stack creates an Amazon Relational Database Service (RDS) Postgres database and two web servers running on Amazon Elastic Compute Cloud (EC2) that send HTTP Requests, measure response times, and write the results into the database. A test run usually takes between 15 and 30 minutes. Once the tests are done, the AWS CloudFormation stacks are torn down immediately. The test results written to the Amazon RD5 database must remain accessible for visualization and analysis. Select possible solutions that allow access to the test results after the AWS CloudFormation load-testing stack is detected. - ✔?- Define a deletion policy of type Retain for the Amazon QDS resource to assure that the RDS database is not deleted with the AWS CloudFormation stack. - Define a deletion policy of type Snapshot for the Amazon RDS resource to assure that the RDS database can be restored after the AWS CloudFormation stack is deleted. You've been tasked with moving an e-commerce web application from a customer's datacenter into a VPC. The application must be fault tolerant and well as highly scalable. Moreover, the customer is adamant that service interruptions not affect the user experience. As you near lanuch, you discover that the application currently uses multicast to share session state between web servers. in order to handle session state within the VPC, you shoose to. - ✔?Store session state in Amazon ElastiCache for Redis (scalable and makes the web applications stateless) Your company has recently extended its datacenter into a VPC on AWS to add burst computing capacity as needed. Menmbers of your Network Operations Center need to be able to go to the AWS Management Console and administer Amazon EC2 instances as necessary. you don't want to create new IAM users for each NOC menber and make those users sign in again to the AWS Management Console. Which option below will meet the nees for your NOC members? - ✔?Use your on-premises SAML 2.O-compliant identity provider (IDP) to grant the NOC members federated access to the AWS Management Console via the AWS single sign-on (SSO) endpoint. Your company sells consumer devices and need to record the first activation of all sold devices. Devices are not activated untill the information is written on a persistent database. Activation data is very important for your company and must be analyzed daily with a MapReduce job. The excution time of the data analysis process must be less than three hours per day. Devices are usually sold evenly during the year, but when a new device model is out, there is a predictable peak in actinations, that is, for a few days there are 10 times or event 100 times activations than in the average day. Which of the following databases and analysis framework would you implement to better optimize costs and performance for this workload? - ✔?Amazon DynamoDB and Amazon Elastic MapReduce with Spot instances. you have an application running on an EC2 instance which will allow users to download files from a private S3 bucket using a pre-signed URL. Before generating the URL, the application should verify the existence of the file in S3. How should the application use AWS credentials to access the S3 bucket securely? - ✔?Create an IAM role for EC2 that allows list access to objects in the S3 bucket. Launch the instance with the role, and retrieve the role's credentials from the EC2 Instance metadata A public archives organization is about to move a pilot application they are running on AWS into production. You have been hired to analyze their application architecture and give cost-saving recommendations. The application displays scanned historical documents. Each documents is split into individual image tiles at multiple zoom levels to improve responsiveness and ease of use for the end users. At maximum zoom level the average document will be 8000x6000 pixels in size, split into multiple 40px x 40px image tiles. The tiles are batch processed by Amazon Elastic Compute Cloud (EC2) instances and put into an Amazon Simple Storeage Service (S3) bucket. A browser-based JavaScript viewer fetches tiles from the Amazon (S3) bucket and displays them to users as thay zoom and pan around each document. The average storage size of all zoom levels for a document is approvizmately 30MB of JPEG tiles. Originals of each document are archived in Amazon Glacier. The company expects to process and host over 500.000 scanned documents in the first year. What are your recommendations? - ✔?- Deploy an Amazon CloudFront distribution in front of the Amazon 53 tiles bucket. - Decrease the size (width/height) of the individual tiles at the maximum zoom level. - Use Amazon 53 Reduced Redundancy Storage for each zoom level. Your social media monitoring application uses a Python app running on AWS Elastic Beanstalk to inject tweets, Facebook updates and RS feeds into an Amazon Kinesis stream. A second AWS Elastic Beanstalk app generates key performance indicators into an Amazon DynamoDB table and powers a dashboard application. What is the most efficient option to prevent any data loss for this application? - ✔?Add a third AWS Elastic Beanstalk app that uses the Amazon Kinesis S3 connector to archive data from Amazon Kinesis into Amazon S3. For a 3-tier, customer facing, inciement weather site utilizing a MySQL database running in a Region which has two AZs (Availability Zone), which architecture provides fault tolerance within the Region for the application that mninimally requires 6 web tier servers and 6 application tier servers running in the web and application tiers and one MySQL databse? - ✔?A web tier deployed across 2 AZs with 6 EC2 (Elastic Compute Cloud) instances in each AZ inside an Auto Scaling Group behind an ELB (elastic load balancer), and an application tier deployed across 2 AZs with 6 EC2 instances in each AZ inside an Auto Scaling Group behind an ELB. and a Multi-AZ RDS (Relational Database Service) deployment. (As it needs Fault Tolerance with minimal 6 servers always available) A startup deploys its photo-sharing site in a VPC. An elastic load balancer sitributes web traffic across two subnets. The load balancer session stickiness is configured to use the AWS-generated session cookie, with a session TTL of 5 minutes. The web server Auto Scaling group is configured as min-size=4, max-size=4. The startup is preparing for a public launch, by running load-testing software installed on a single Amazon Elastic Compute Cloud (EC2) instance running in us-west-2a. After 60 minutes of load-testing, the web server logs show the following: .... Which recommendations can help ensure that load-testing HTTP request are evenly distributed across the four webservers? - ✔?- Re-configure the load-testing software to re-resolve DNS for each web request. (Refer link) - Use a third-party load-testing service which offers globally distributed test clients. (Refer link) Your multi-national customer wants to rewrites a website portal to "take advantage of AWS best practices". Other information that you have for this large Enterprise customer is as follow: - Part of the portal is an employee-only section, and authentication must be against the corporate Active Directory. - You used a web analytics website to discover that on average there were 140.000 visitors per month over the past year, a peak of 187.000 unique visitors last month, and a minimum of 109.000 unique visitors two months ago. You have no information about what percentage of these visitors represents employees who signed into the portal. - The seb analytics website also revealed that traffic breakdown is 40 percent South America, 50 percent North America, and 10 percent other. - The customer's primary data center is located in So Paulo Brazil. - Their chief technology officer believes that response time for logging in to the employee portal is a primary metric, because employees complain that the current website is too slow in this regards. When you present your proposed application architecture to the customer, which of the following should you propose as part of the architecture? - ✔? You have been asked design network connectivity between your existing data centers and AWS. Your application's EC2 instances must be able to connect to existing backend resources located in your data center. Network traffic between AWS and your data centers will start small, but ramp up to 10s of GB per second over the course of serveral months. The success of your application is dependents upon getting to market quickly. Which of the following design options will allow you to meet your objectives? - ✔?Provision a VPN connection between a VPC and existing on -premises equipment, submit a DirectConnect partner request to provision cross connects between your data center and the DirectConnect location, then cut over from the VPN connection to one or more DirectConnect connections as needed. You are moving an existing traditional system to AWS, and during the migration discover that there is a master server which is a single point of failure. Having examined the implementation of the master server you realise there is not enough time during migration to re-engineer it to be highly available, though you do discover that it stores its state in a local MySQL database. In order to minimize down-time you select RD5 replace the local database and configure master to use it, what steps would best allow you to create a seft-healing architecture. - ✔?Migrate the local database into multi-AWS RDS database. Place master node into a multi-AZ auto-scaling group with a minimum of one and maximum of one with health checks To meet regulatory requirement, a pharmaceuticals company need to archive data after a drug trial test concluded. Each drug trial test may generate up to several thousands of files, with conpressed file sizes ranging from 1 byte to 100MB. Once archived, data rarely needs to be restored, and on the rare occasion when restoration needed, the compnay has 24 hours to restore specific files that bmatch certain metadata. Searches must be possible by numeris file ID, drug name, participant names, date ranges, and other metadata. Which is the most-effective architectural approach that can meet ther requirement? - ✔?First, compress and then concatenate all files for a completed drug trial test into a single Amazon Glacier archive. Store the associated byte ranges for the compressed files along with other search metadata in an Amazon RDS database with regular snapshotting. When restoring data, query the database for files that match the search criteria, and create restored files from the retrieved byte ranges. A media production company wants to deliver high-definition raw video material for preproduction and dubbing to customers all around the world. They would like to use Amazon CloudFront for their scenario, and they require the ability to limit downloads per customer and video file to a configurable number. A CloudFront download distribution with TTL = 0 was already setup to make sure all client HTTP request hit an authentication backent on Amazon Elastic Compute Cloud (EC2)/Amazon Relational Database Service (RDS) first, which is responsible for restricting the number of downloads. content is stores in Amazon Simple Storage (S3) and configured to be accessible only via CloudFront. What else needs to be done to achieve an architecture that meets the requirement? - ✔?- Enable URL parameter forwarding, let the authentication backend count the number of downloads per customer in RDS, and return the content S3 URL unless the download limit is reached. - Configure a list of trusted signers, let the authentication backend count the number of download requests per customer in RDS, and return a dynamically signed URL unless the download limit is reached. You tried to integrate two subsystems (front-end and back-end) with an HTTP interface to one large system. These subsystems don't store any state inside. All state is stored in an Amazon DynamoDB table. You have launched each of these two subsystems from a separate AMI. Black box testing has shown that these servers have stopped running and are issuing malformed requests that do not meet HTTP specifications from the clients. Your developers have discover and fixed this issue, and you deploy the fix to the two subsystems as soon as possible without service disruption. What are the most effective options to deploy the fixes? - ✔?- Use AWS OpsWorks auto healing for both the front'end and back-end instance pair. - Use Elastic Load Balancing in front of the front-end subsystem and Auto scaling to keep the specified number of instances - Use Elastic Load Balancing in front of the back-end subsystem and Auto scaling to keep the specified number of instances You are designing Internet connectivity for your VPC. The Web servers must be available on the Internet. The application must have a highly available architecture. Which alternatives should you consider? - ✔?- Place all your web servers behind ELB. Configure a Route53 CNAME to point to the ELB DNS name. - Assign EIPs to all web servers. Configure a Route53 record set with all EIP [Show More]
Last updated: 3 years ago
Preview 1 out of 16 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

AWS bUNDLE. ALL EXAMINABLE QUESTIONS WITH ANSWERS. PASS EASY.
ALL AWS PAPERS. QUESTIONS WITH ANSWERS. RATED A
By Topmark 3 years ago
$32
28
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 24, 2022
Number of pages
16
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 24, 2022
Downloads
0
Views
209