Computer Science > QUESTIONS & ANSWERS > Palo Alto PCCET Questions and Answers (All)
Palo Alto PCCET Questions and Answers
Document Content and Description Below
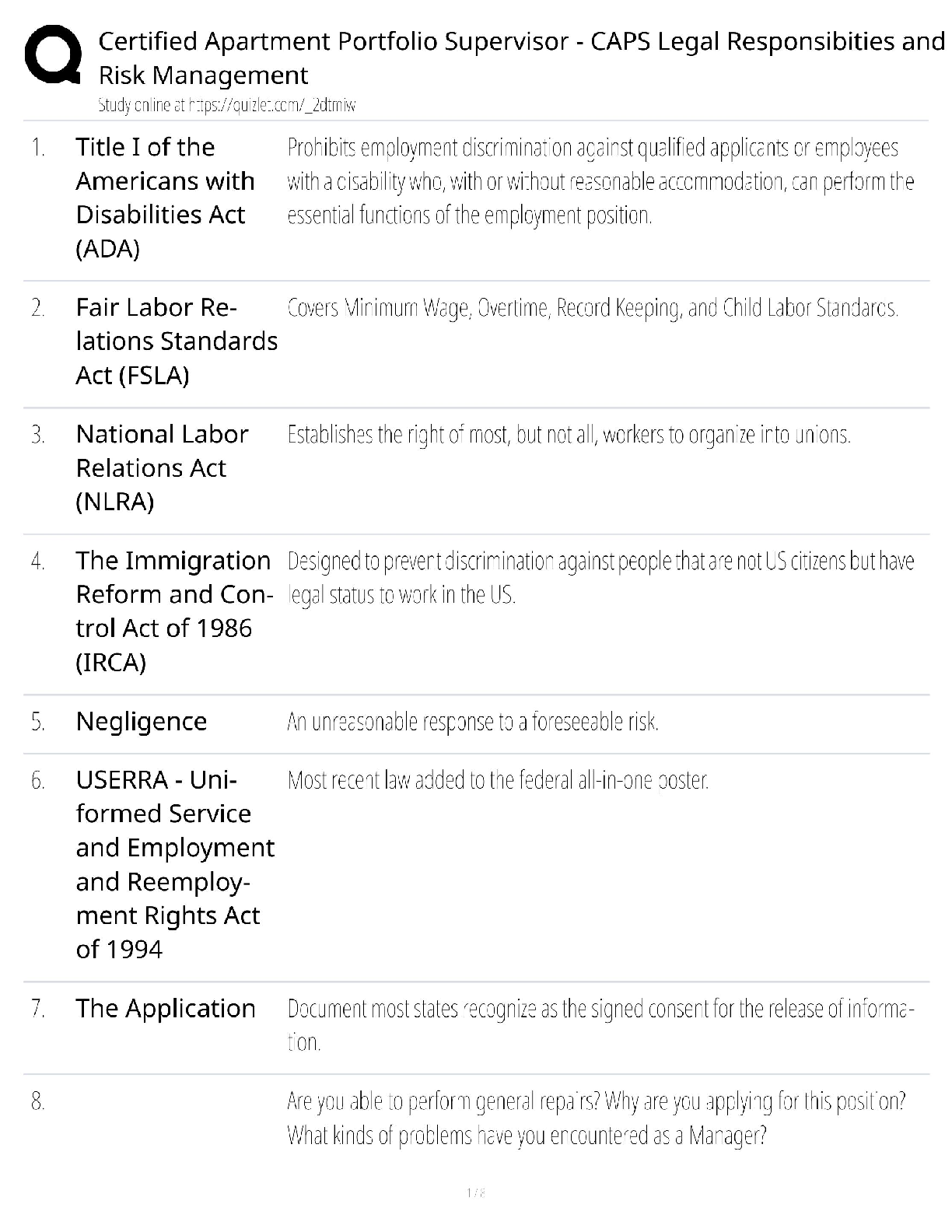
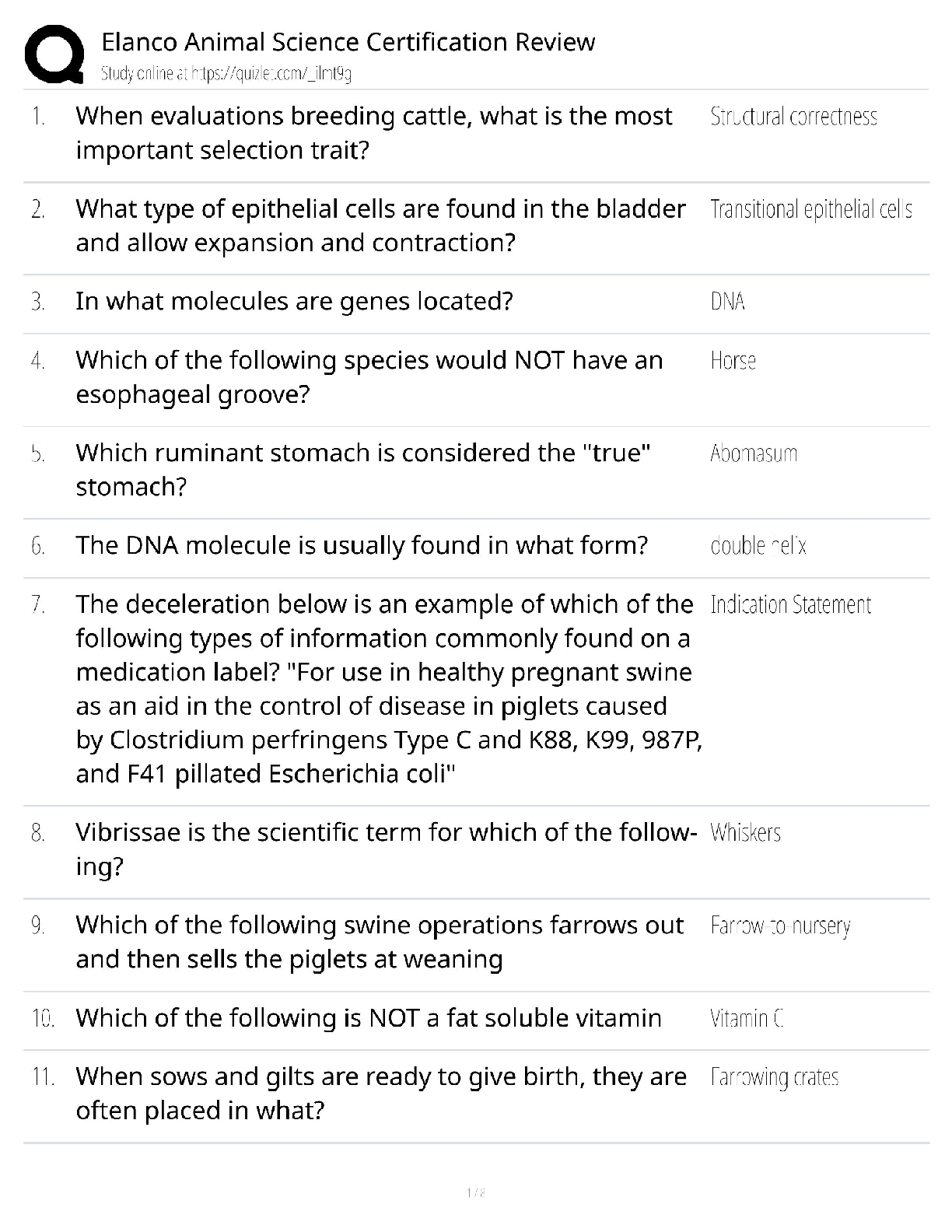
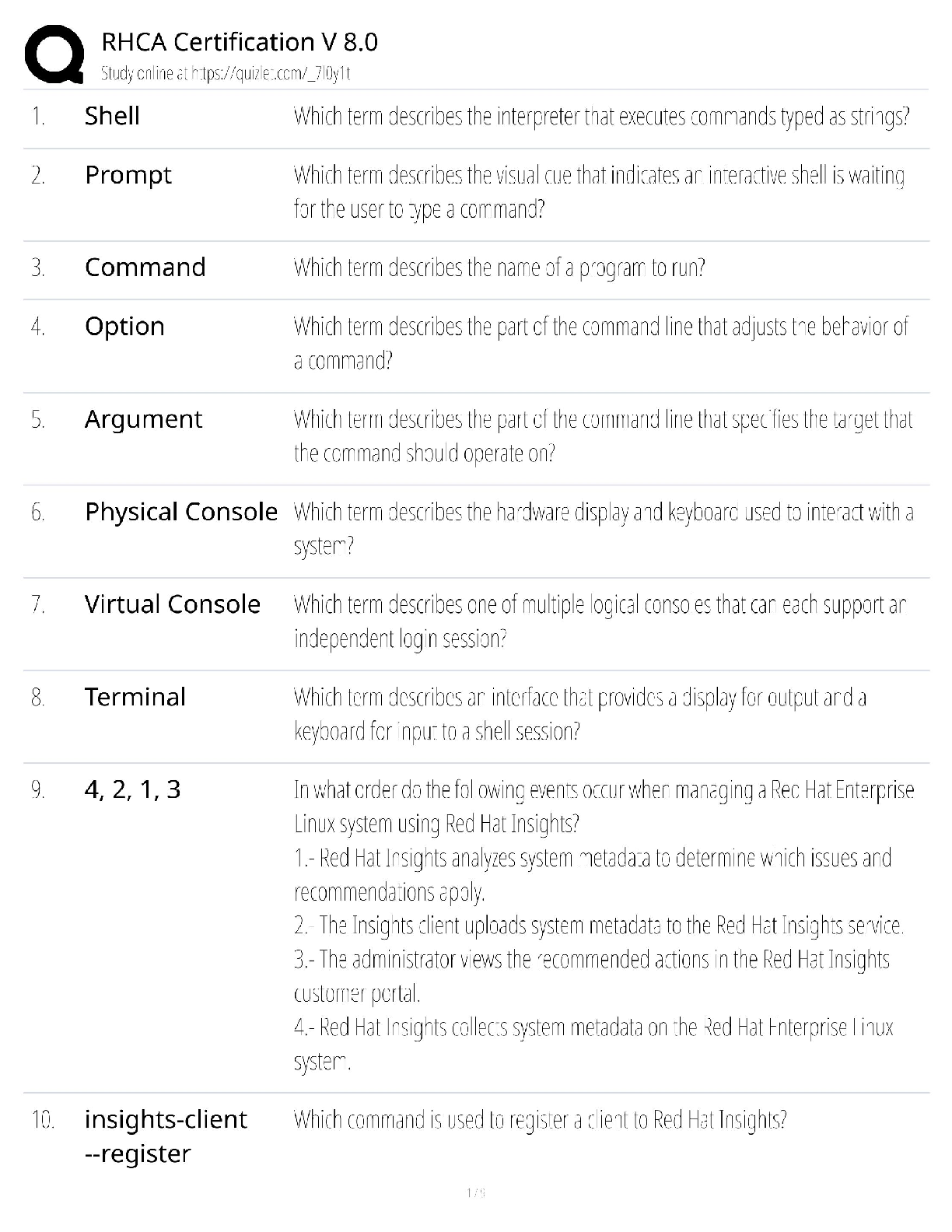
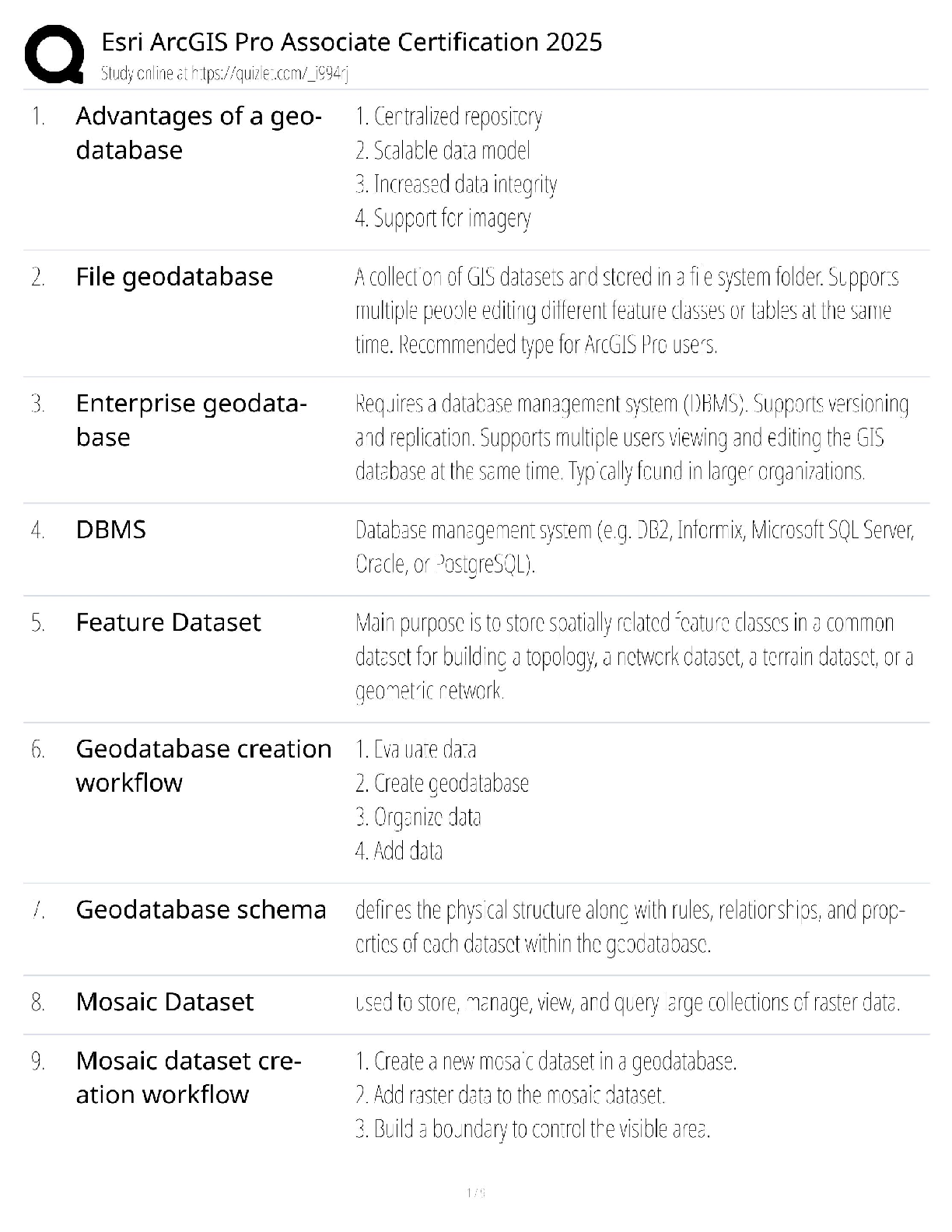
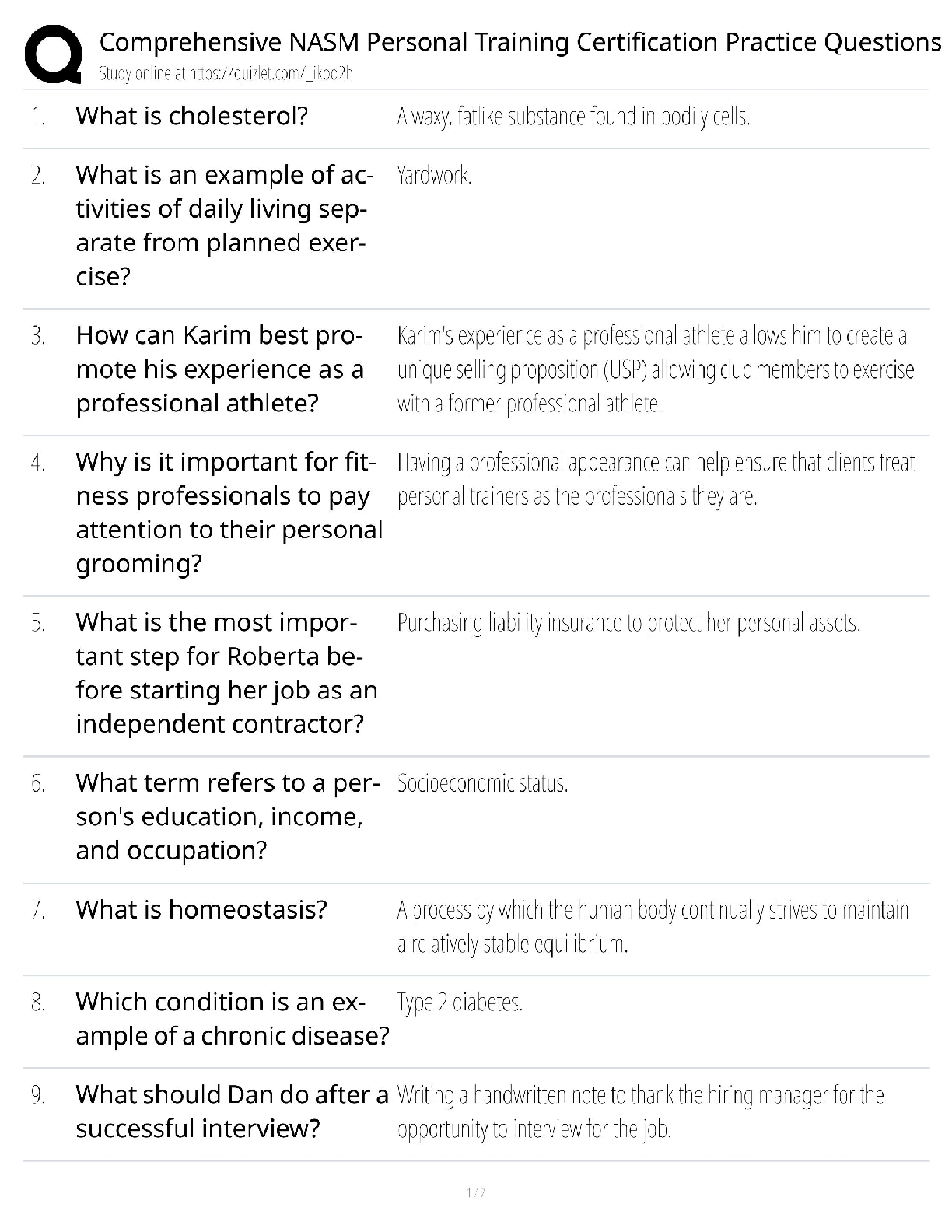
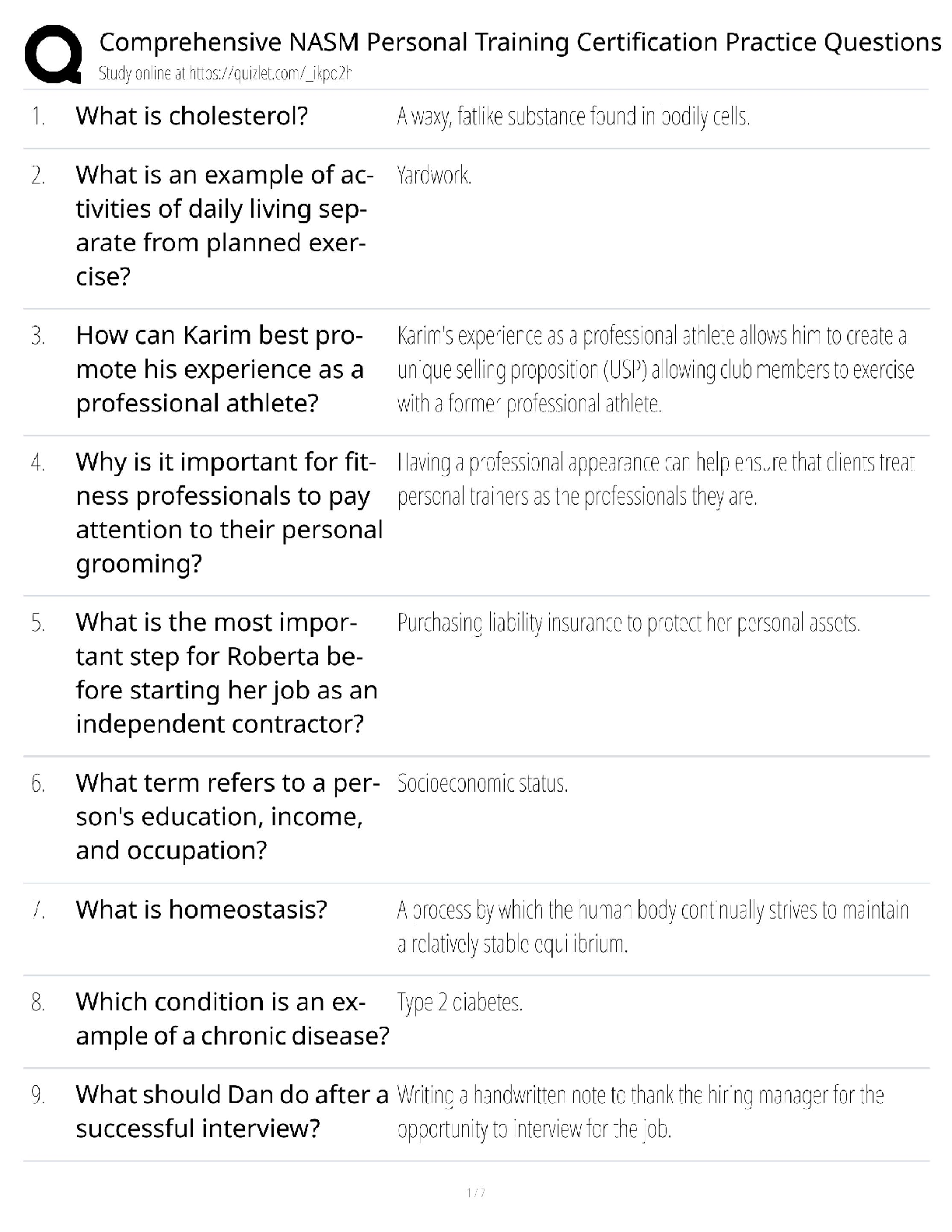
Palo Alto PCCET Questions and Answers Which type of cyberattack sends extremely high volumes of network traffic such as packets, data, or transactions that render the victim's network unavailable or ... unusable? A. distributed denial-of-service (DDoS) B. spamming botnet C. phishing botnet D. denial-of-service (DoS) - answerA Which core component of Cortex combines security orchestration, incident management, and interactive investigation to serve security teams across the incident lifecycle? A. AutoFocus B. Cortex XDR C. Cortex XSOAR D. Cortex Data Lake - answerC Which type of advanced malware has entire sections of code that serve no purpose other than to change the signature of the malware, thus producing an infinite number of signature hashes for even the smallest of malware programs? A. distributed B. polymorphic C. multi-functional D. obfuscated - answerB Which type of phishing attack is specifically directed at senior executives or other high-profile targets within an organization? A. whaling B. watering hole C. pharming D. spear phishing - answerA Which wireless security protocol includes improved security for IoT devices, smart bulbs, wireless appliances, and smart speakers? A. WPA2 B. WPA3 C. WPA1 D. WEP - answerB Which tactic, technique, or procedure (TTP) masks application traffic over port 443 (HTTPS)? A. using non-standard ports B. hopping ports C. hiding within SSL encryption D. tunneling - answerC Which specific technology is associated with Web 3.0? A. social networks B. instant messaging C. remote meeting software D. blockchain - answerD Which Wi-Fi attack leverages device information about which wireless networks it previously connected to? A. evil twin B. man-in-the-middle C. Jasager D. SSLstrip - answerC Which malware type is installed in the BIOS of a machine, which means operating system level tools cannot detect it? A. rootkit B. logic bomb C. ransomware D. spyware - answerA Which Zero Trust capability provides a combination of anti-malware and intrusion prevention technologies to protect against both known and unknown threats, including mobile device threats? A. least privilege B. secure access C. inspection of all traffic D. cyberthreat protection - answerD Which three options describe the relationship and interaction between a customer and SaaS? (Choose three.) A. subscription service B. extensive manpower required C. internet- or application-based D. complex deployment E. convenient and economical - answerACE Mobile devices are easy targets for attacks for which two reasons? (Choose two.) A. They have poor battery-charging capabilities. B. They use speaker phones. C. They stay in an always-on, always-present state. D. They roam in unsecured areas. - answerCD Which path or tool is used by attackers? A. storage-area networks (SAN) B. anti-malware update C. SaaS D. threat vector - answerD Which kind of server is a master server that is designed to listen to individual compromised endpoints and respond with appropriate attack commands? A. command and control B. bot C. web D. directory services - answerA What type of malware can have multiple control servers distributed all over the world with multiple fallback options? A. logic bombs B. rootkits C. advanced or modern D. exploits - answerC Which type of malware disables protection software? A. anti-AV B. Trojan horse C. ransomware D. worm - answerA Another term for a bot is a "zombie". (True or False) - answerT The spread of unsolicited content to targeted endpoints is known as what? A. spamming B. pharming C. phishing D. exploiting - answerA Which type of attack utilizes many endpoints as bots or attackers in a coordinated effort, and can be extremely effective in taking down a website or some other publicly accessible service? A. Bluetooth B. adware C. distributed denial-of-service D. man-in-the-middle - answerC [Show More]
Last updated: 3 years ago
Preview 1 out of 89 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 16, 2022
Number of pages
89
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 16, 2022
Downloads
0
Views
150











.png)