Computer Science > QUESTIONS & ANSWERS > CyberRookie CSX Fundamentals - Section 4: Security of Networks, Systems, Applications and Data with (All)
CyberRookie CSX Fundamentals - Section 4: Security of Networks, Systems, Applications and Data with Complete Elaborations
Document Content and Description Below
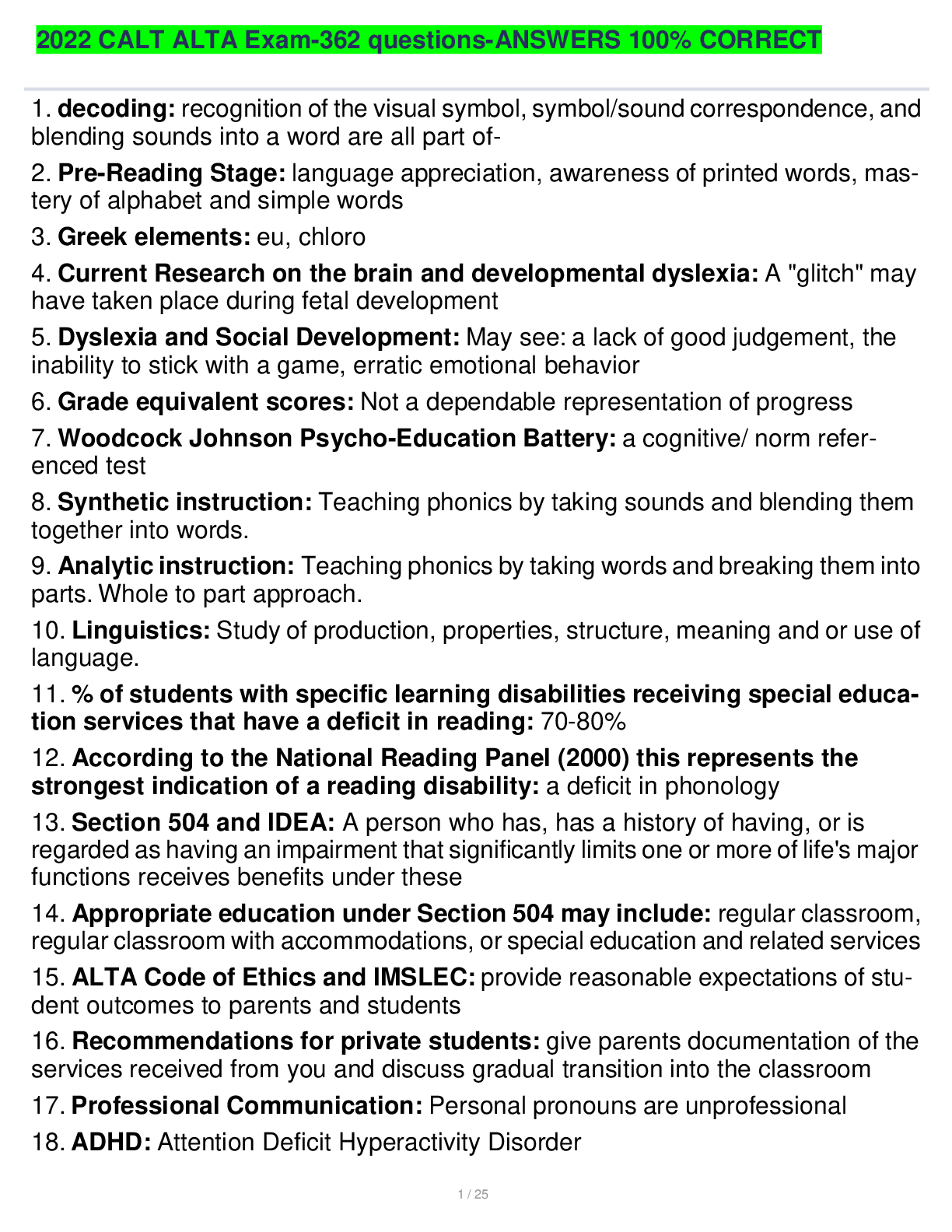
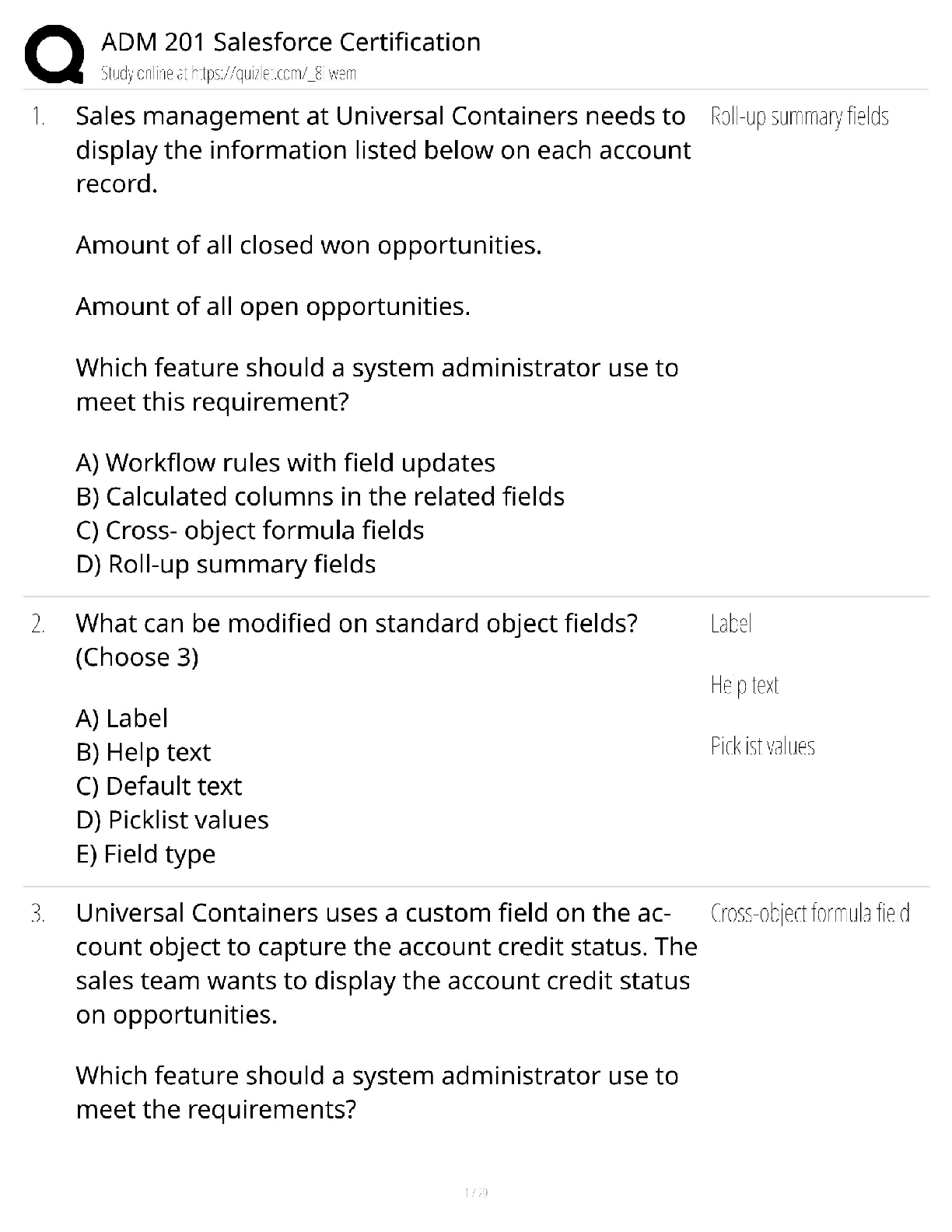
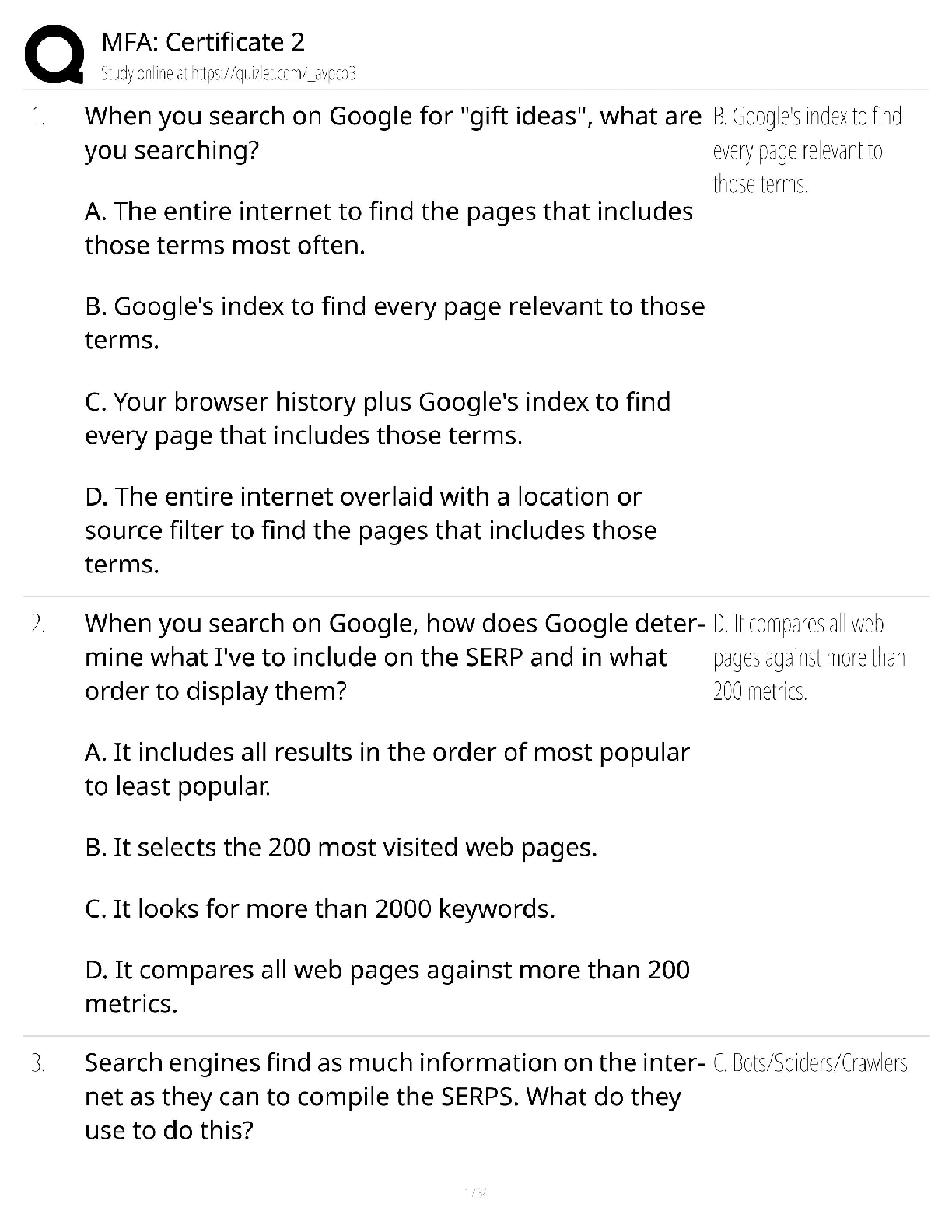
CyberRookie CSX Fundamentals - Section 4: Security of Networks, Systems, Applications and Data with Complete Elaborations 1 / 24 1. risk: Is defined as the possibility of loss of a digital asset re ... sulting from a threat exploiting a vulnerability 2. cyberrisk assessment: Of these attributes of risk must be analyzed to determine an organization's particular risk. 3. risk assessment methodology inputs: Asset identification, threat assessment and vulnerability assessment 4. cyberrisk assessment: Process begins with an examination of the risk sources (threats and vulnerabilities) for their positive and negative consequences. 5. risk: Can be ranked according to likelihood and impact. 6. Information used to estimate impact and likelihood usually comes from: - Past experience or data and records, Reliable practices, international standards or guidelines, Market research and analysis, Experiments and prototypes, Economic, engineering or other models, Specialist and expert advice 7. cyberrisk assessment: Existing controls and other mitigation strategies are evaluated to determine the level and effectiveness of risk mitigation currently in place and identify deficiencies and gaps that require attention. 8. If risk is not properly analyzed: The implementation of security is left to guesswork. 9. risk analyses: Can be oriented toward one of the inputs, making the risk assessment asset-oriented, threat-oriented or vulnerability-oriented 10. Asset: Important assets are defined first, and then potential threats to those assets are analyzed. Vulnerabilities are identified that may be exploited to access the asset. 11. Threat: Potential threats are determined first, and then threat scenarios are developed. Based on the scenarios, vulnerabilities and assets of interest to the adversary are determined in relation to the threat. [Show More]
Last updated: 3 years ago
Preview 1 out of 24 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

CyberRookie CSX Fundamentals Exam FULL SOLUTION PACK(ALL CyberRookie CSX Fundamentals Exams AND STUDY QUESTIONS ARE HERE ,ALL ANSWERED CORRECTLY)
CyberRookie CSX Fundamentals - Section 6: Security Implications and adoption of evolving technology CyberRookie CSX Fundamentals - Section 4: Security of Networks, Systems, Applications and Data wi...
By Alphascore 3 years ago
$14
9
Reviews( 0 )
$7.50
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Nov 01, 2022
Number of pages
24
Written in
All
Additional information
This document has been written for:
Uploaded
Nov 01, 2022
Downloads
0
Views
141


 with Complete Solution.png)
 Career Information with Complete Solution.png)


 for E-6 Career Information_watermark.png)