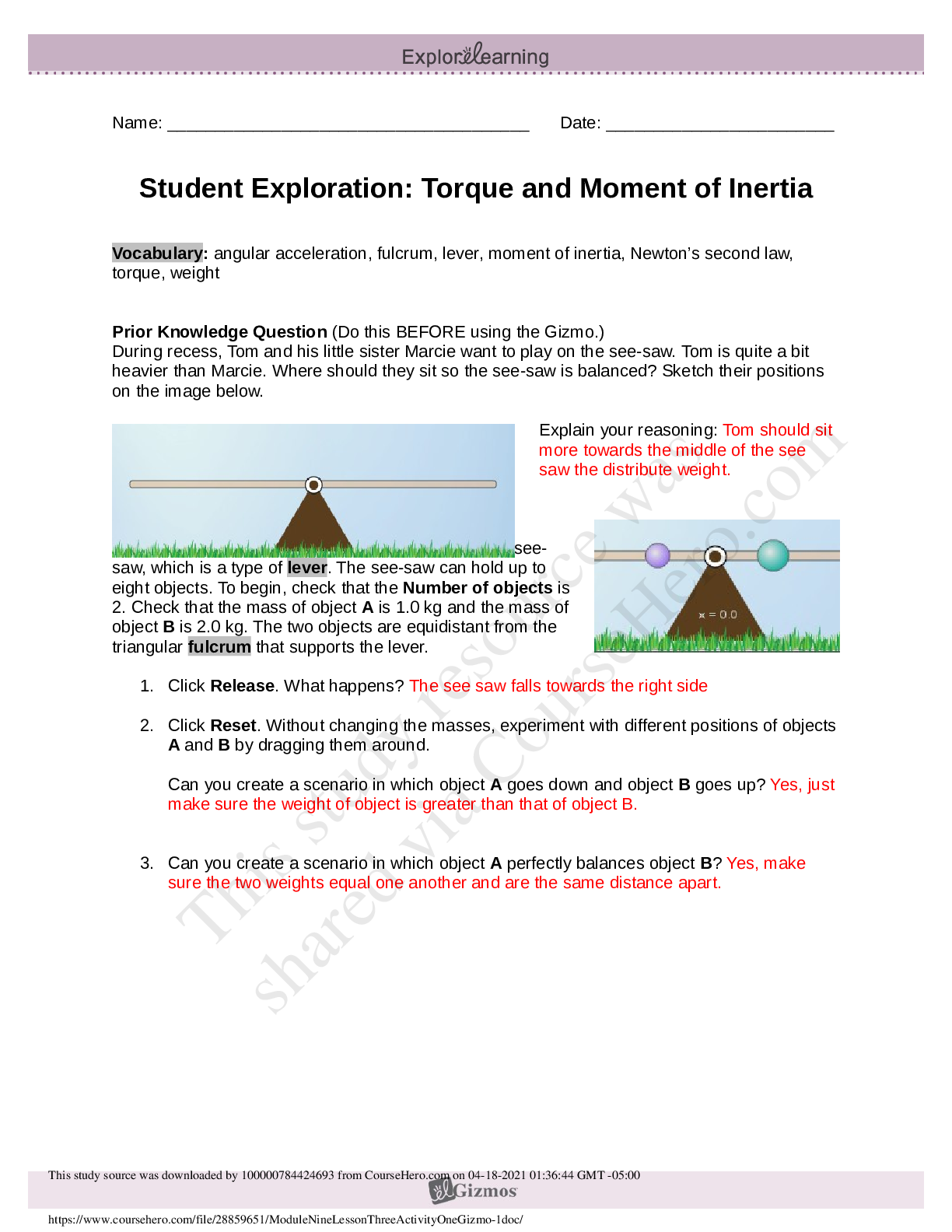
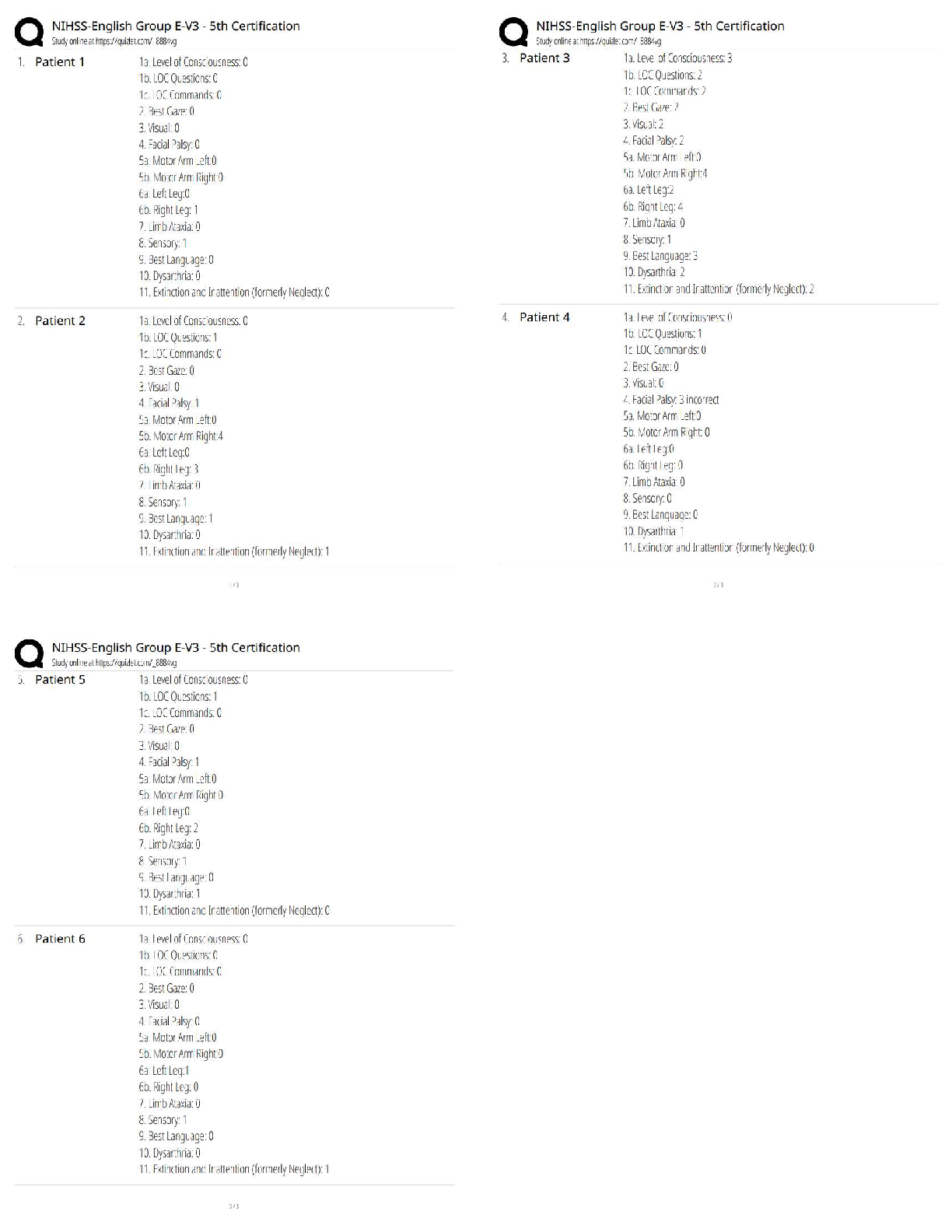
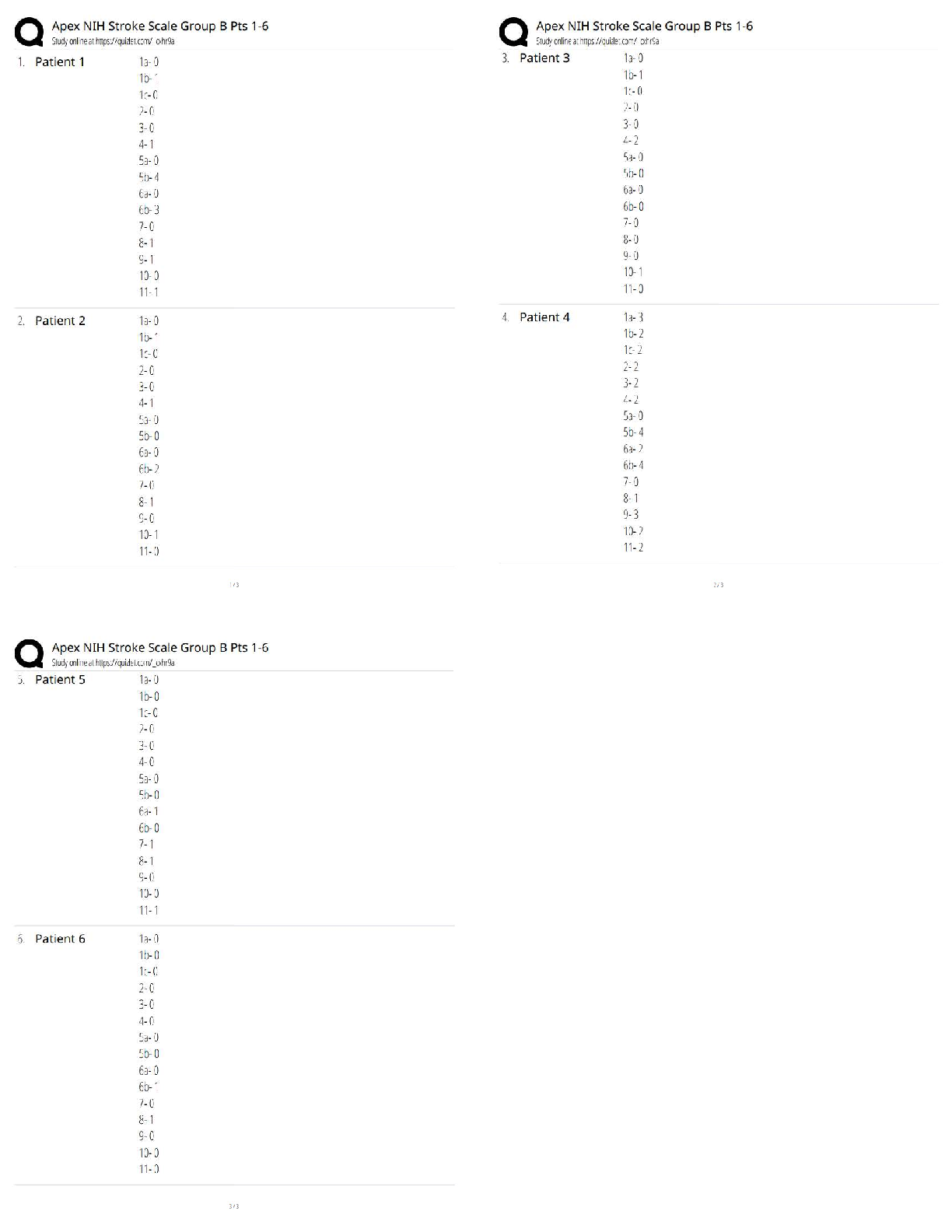
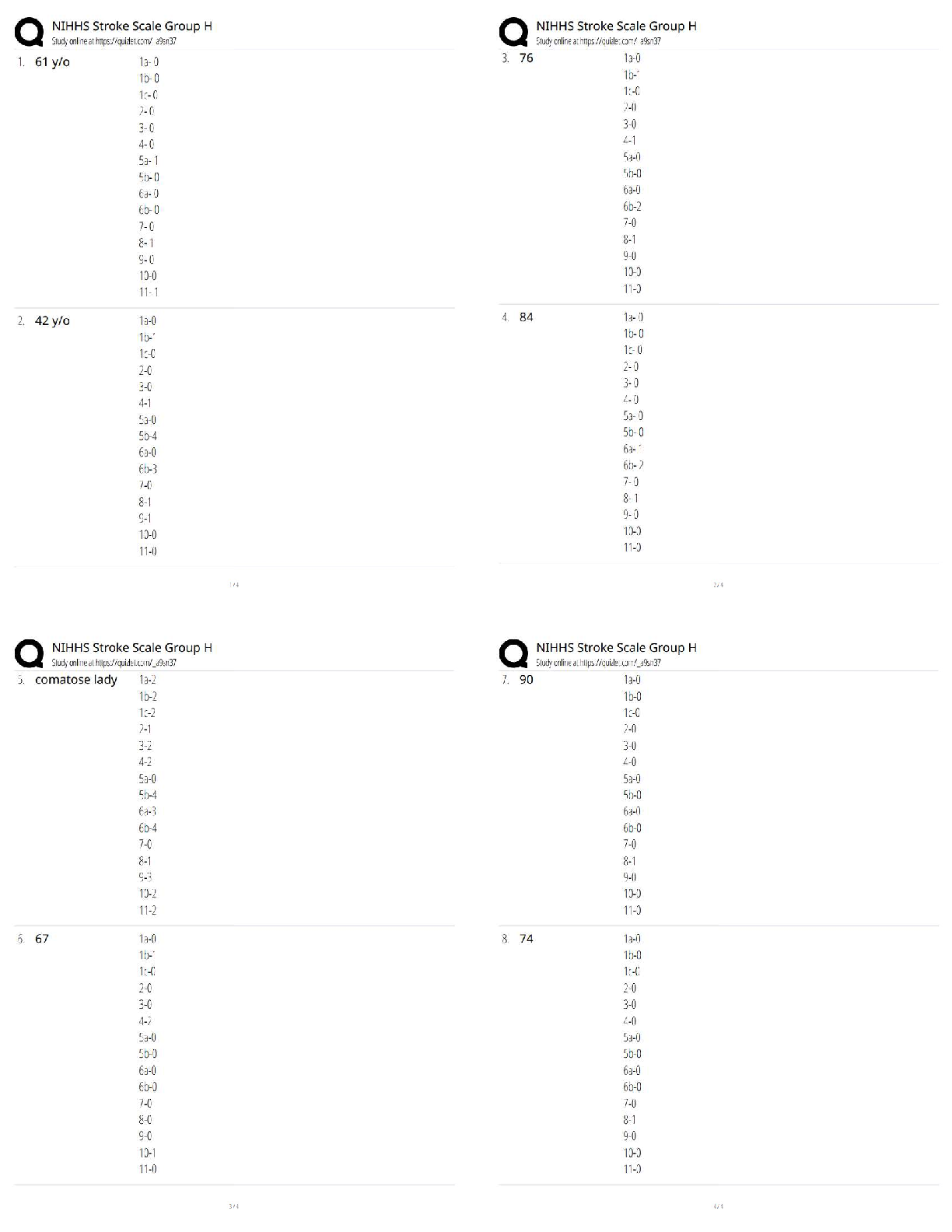
– University of the People.png)
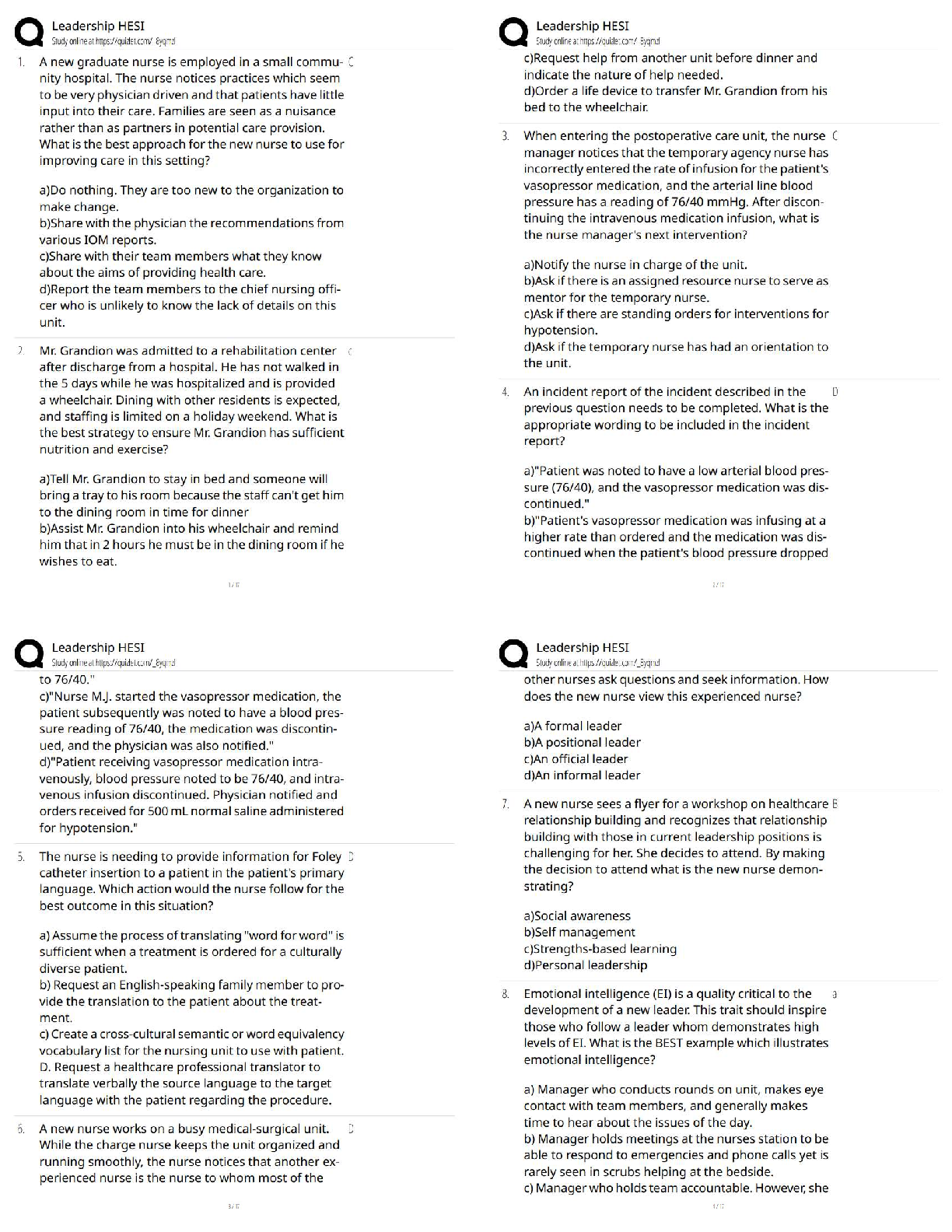
MATH 1280 Practice Milestone UNIT 1 Introduction to Statistics (2020) – University of the People | MATH1280 Practice Milestone UNIT 1 Introduction to Statistics (2020)
$ 16.5

INSTRUCTOR’S SOLUTIONS MANUAL SEARS & ZEMANSKY’S UNIVERSITY PHYSICS 15TH EDITION WAYNE ANDERSON A. LEWIS FORD
$ 30
.png)
Home Inspector National Exam Prep Questions and Answers Latest Updated 2022 Rated A+
$ 15
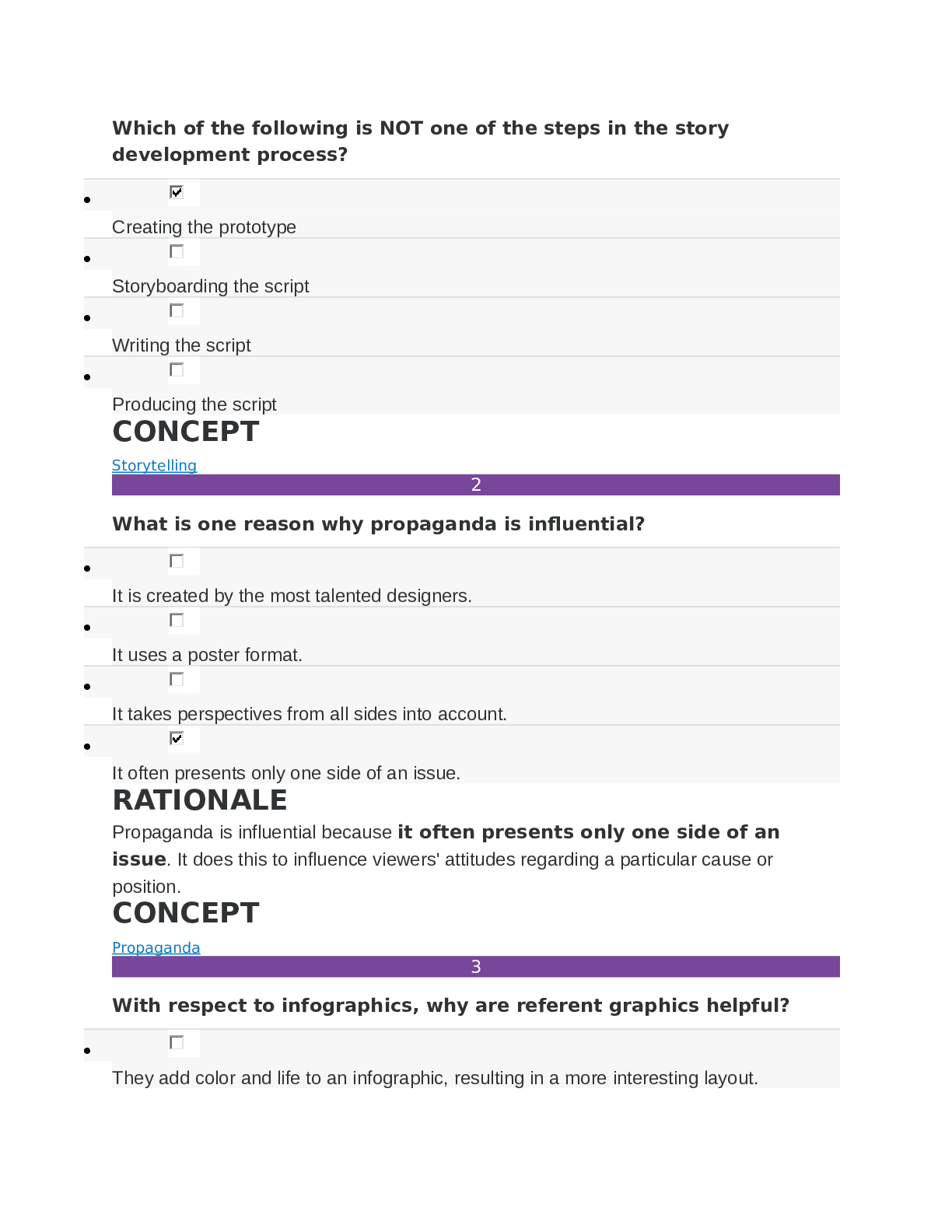
SOPHIA PATHWAY Visual Communication - Final Test_ Answered Latest Fall 2020.
$ 18

EDR 610 Quiz 1 Question with Answers,GRADED A.
$ 17

OCR_A Level Chemistry A_H432/03 Mark Scheme Oct 2021 | Unified Chemistry
$ 6.5

Sophia Visual Communication - Unit 1 Milestone 1, Exam Elaborations Questions with Complete Answers
$ 15

My Personal Ethical Theory and Justifying Killing Capstone Essay
$ 7

AQA A LEVEL BIOLOGY PAPER 3 2020 MARK SCHEME
$ 12
.png)
NR 509 Week 1 Midweek Comprehension QUIZ (March 2020) Graded with all answers correct
$ 5
.png)
NR 500 Area of Interest-Week 5 - Foundational Concepts and Applications September
$ 10

MN 502 Unit 5 Quiz - Question and Answers | VERIFIED ANSWERS
$ 10

Instructor’s Solution Manual Artificial Intelligence A Modern Approach Fourth Edition Stuart J. Russell and Peter Norvig
$ 16.5

GSA SmartPay Purchase Account (Account Holders). Questions with accurate answers. Rated A+
$ 5

DTS Basic - DTS Travel Documents _ DTS 101 | Questions with Complete Solutions
$ 6

2023 FRONTIER CERTIFICATION WITH MARKIN SCHEME
$ 10

Test Bank & Solution manual for Personal Finance, Fourth Canadian Edition (4th Edition) by Jeff Mad
$ 29

Week 1 Assignment.docx Running head: SUPPORTING DIVERSITY
$ 10
ACC 210 – PRACTICE FINAL EXAM Questions and Verified Correct Answers Latest Update 2024 Guaranteed A+
$ 18.5
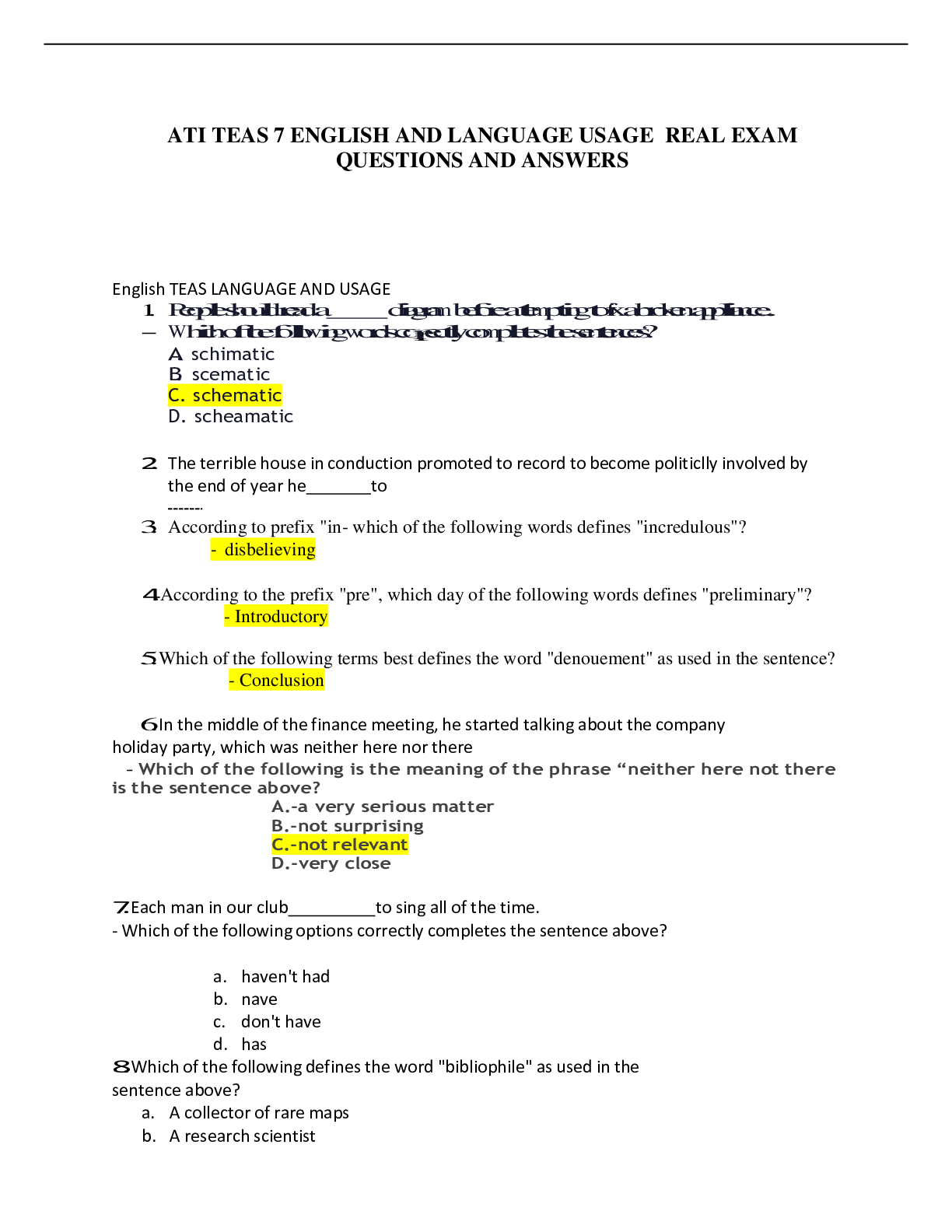
ATI TEAS 7 ENGLISH AND LANGUAGE USAGE REAL EXAM QUESTIONS AND ANSWERS
$ 16

ECDI 2271 - Chapter 1 Understanding Children's Creative Thought and Expression
$ 13.5

TEST BANK for Data Analytics for Accounting, 3rd Edition By Vernon Richardson, Ryan Teeter and Katie Terrell.
$ 24
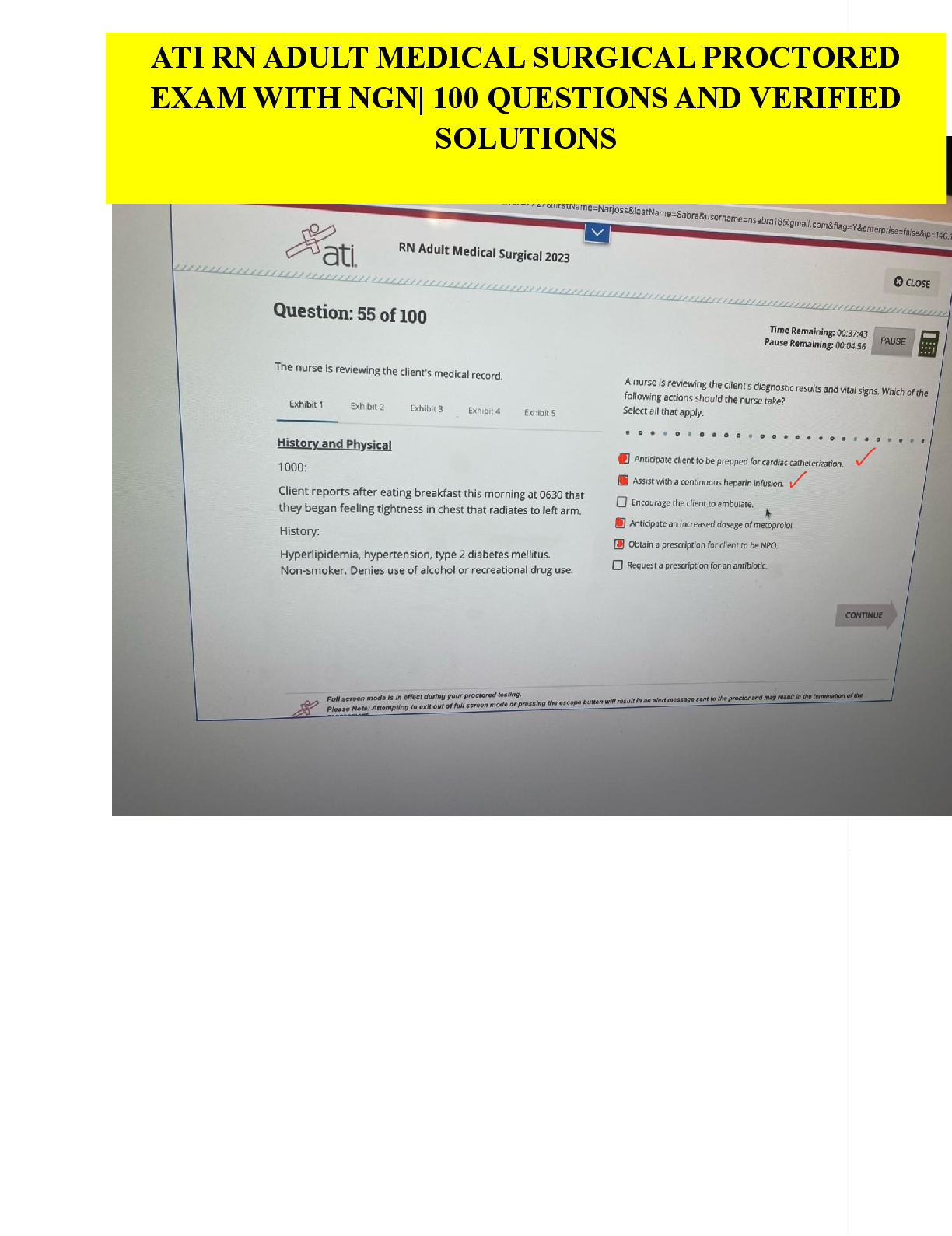
ATI RN ADULT MEDICAL SURGICAL PROCTORED EXAM WITH NGN 100 QUESTIONS AND VERIFIED SOLUTIONS
$ 61

WGU C708 unit 4 latest 2022 already passed
$ 5

NR-601 Mature and Aging Adult Week 6 Discussion Post
$ 2.5

Illinois State Dental Jurisprudence Exam (Pre-Test Review) Q & S 2024
$ 10

Solution Manual For Statistics Learning from Data, 3rd Edition by Roxy Peck, Catherine Case Chapter 1-16
$ 19

Edexcel a level english language question p aper 1 june 2023+ mark scheme
$ 10

AQA GCSE MATHEMATICS 8300/1F Foundation Tier Paper 1 Non-Calculator Mark scheme June 2021 Version: 1.0 Final
$ 6.5

Midterm Exam: NR 509/ NR509 Advanced Physical Assessment Midterm Exam Questions with Verified Answers (Latest 2025/ 2026)- Chamberlain
$ 12.5
.png)
WGU C720 – Questions and Answers Latest 2022 Rated A
$ 13
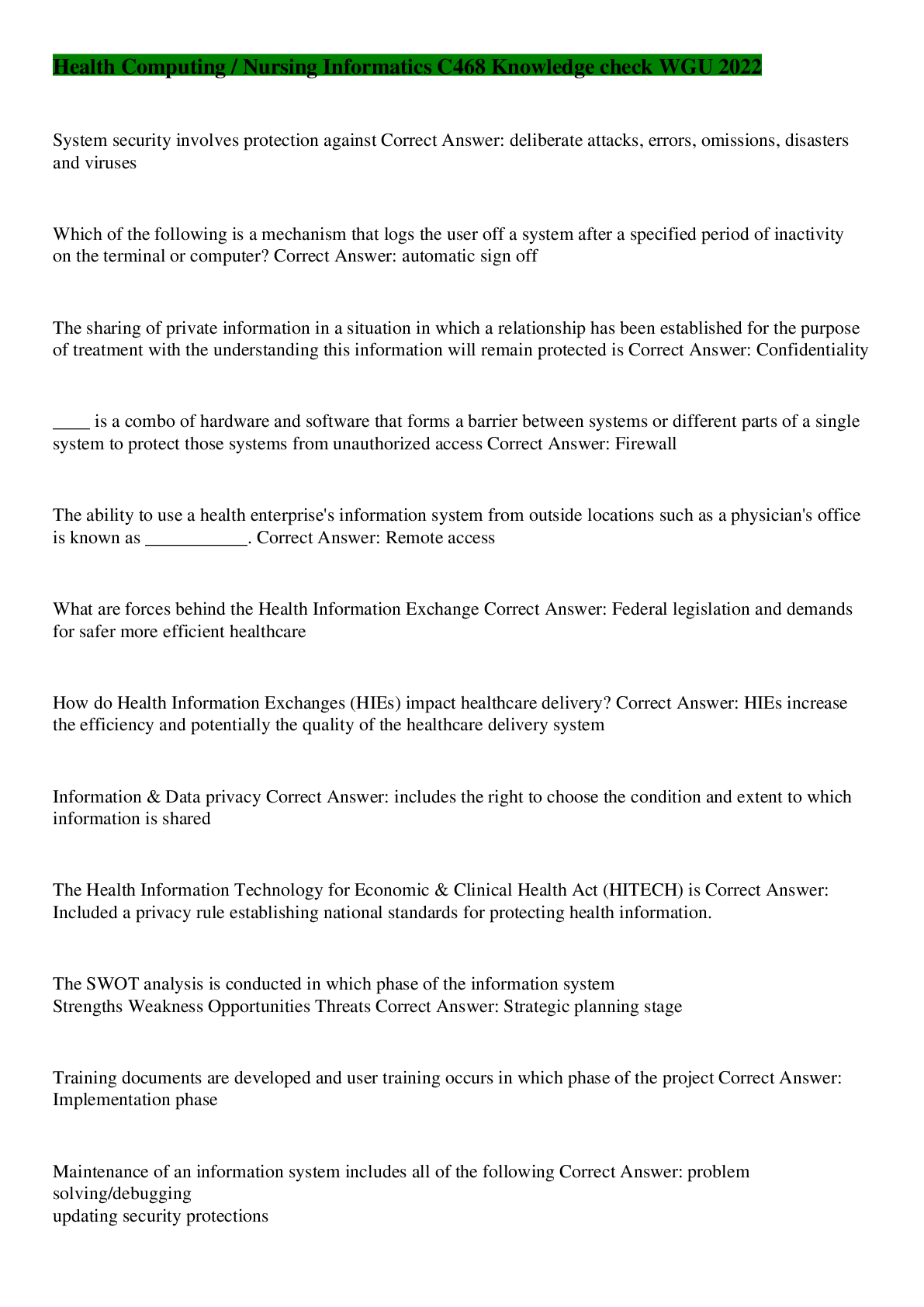
Health Computing / Nursing Informatics C468 Knowledge check WGU 2022
$ 7

eBook Building and Managing High-Performance Distributed Teams 1st Edition By Alberto S. Silveira Jr.
$ 30.5

Designing and Implementing a Microsoft Azure AI Solution AI-102 Exam Dumps, AI-102 Exam Questions AI-102 PDF Dumps, AI-102 VCE Dumps.
$ 10
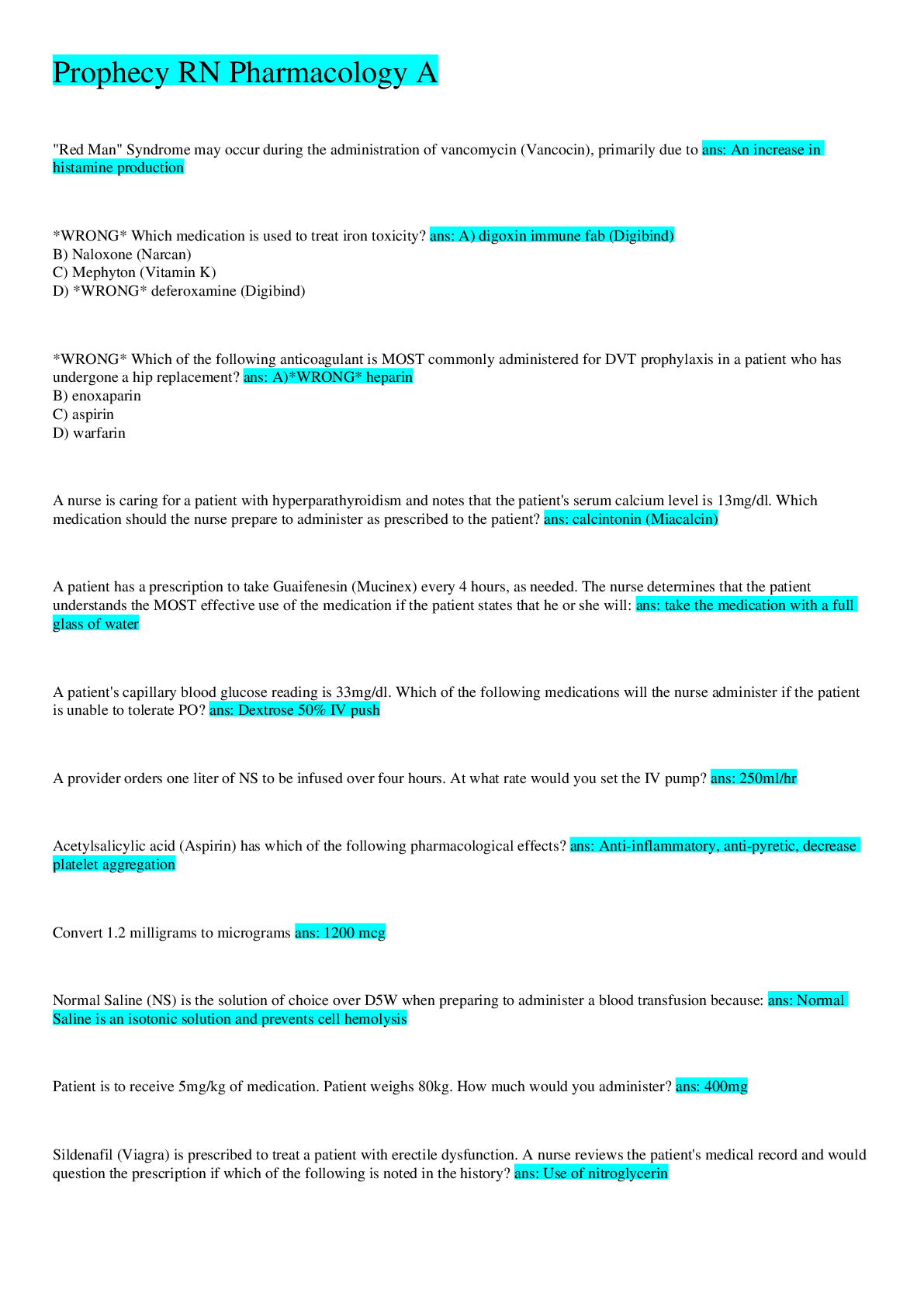
(solved) Prophecy RN Pharmacology A; latest 2022 all correct
$ 13
Pearson Edexcel A Level 3 GCE (9GE0/03) Geography Advanced PAPER 3 + mark scheme june 2024
$ 8

eBook(EPUB) Corporate Psychopathy Investigating Destructive Personalities in the Workplace 1st Edition By Katarina Fritzon, Nathan Brooks, Simon Croom
$ 29

(ASU online) Health Informatics Database Modelling & Applications Final Exam Guide Q & S 2024
$ 14

Managing and Using Information Systems A Strategic Approach, 7th Edition Pearlson, Saunders, Galletta TEST BANK.
$ 26

NR 601 Week 4 Midterm Review; Video Key Points Summary
$ 4.5

AQA GCSE PHYSICS 8463/2H Paper 2 Higher Tier Mark scheme 1.0 Final Mark Scheme 2020
$ 12

Cambridge International AS & A Level Mathematics Probability & Statistics 1 Worked Solutions Manual By Dean Chalmers (Solution Manual)
$ 20

GLO-BUS Decisions & Reports years 7/ GLOBUS Decisions & Reports years; Latest 2019/20 Complete Guide, Already Graded A.
$ 8.5

USPAP 100 Practice Test Questions and Answers 100% Pass
$ 9

OCR A Level History A Y101/01 Alfred and the Making of England QP 2021
$ 10

American Public University - HIMA 100 / HIMA100 - WEEK 6 - QUIZ Graded A
$ 12

Test Bank for Business Law: Text and Cases: Legal, Ethical, Global, and Corporate Environment 12th Edition by Kenneth W. Clarkson, Roger LeRoy Miller, Frank B. Cros
$ 17

UHC Medicare Basics Test 2021
$ 9

TOEIC: Intermediate Politics, Government, and Society Vocabulary Set 3
$ 19.5
ATI Pharmacology proctored exam study guide latest updated 2022
$ 9

NURS 6670 FINAL EXAM Study Guide Mental Health Case Studies Chapters 1 to 39 | Complete Solution guide | Walden University
$ 9

CTS Questions and Answers with Complete Solutions
$ 19

Pearson Edexcel Level 3 GCE_Physics_8PH0/02 Question Paper 2020 | Core Physics II
$ 6.5
Pearson Edexcel A Level 3 GCE (9FR0/01) French Advanced Paper 1: Listening, Reading and Translation + mark scheme June 2024
$ 8
Field Radio Operator Question and Answers 2023
$ 15

Dental Materials: Clinical Applications for Dental Assistants and Dental Hygienists 3rd Edition by Hatrick & Eakle | All Chapters 1-19 | TEST BANK
$ 26
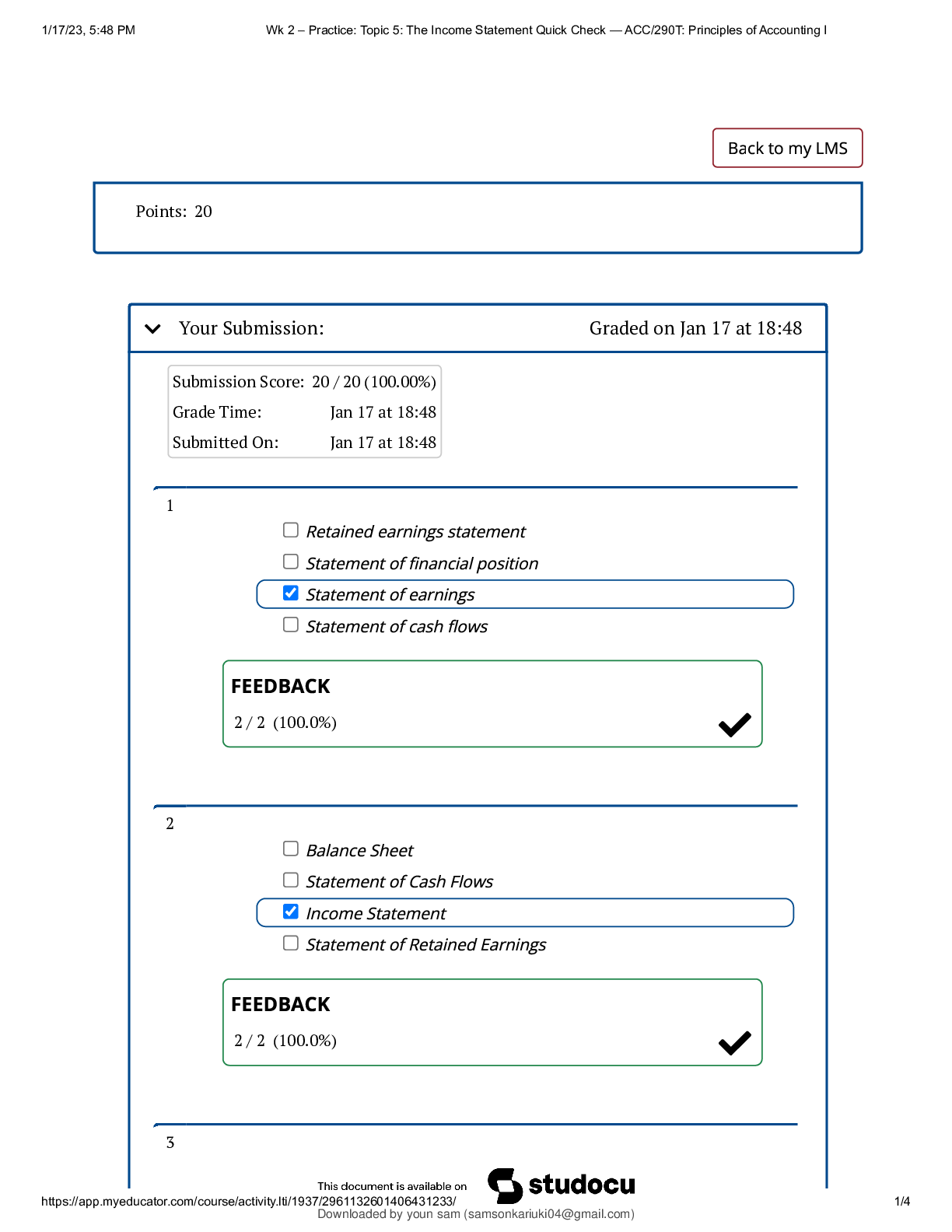
ACC/290T: Principles of Accounting Week 2 | Topic 5: The Income Statement Quick Check | Answered.
$ 6

A Level Further Mathematics A_Y541/01 Question Paper Oct 2021 | Pure Core 2
$ 7.5

Mark Scheme (Results) Summer 2022 Pearson Edexcel GCSE In Physical Education Short Course (3PE0) Paper 01 Theory Edexcel and BTEC Qualifications
$ 8

ATI fundamentals, ATI RN Fundamentals Proctored Focus study guide 2022/2023
$ 10
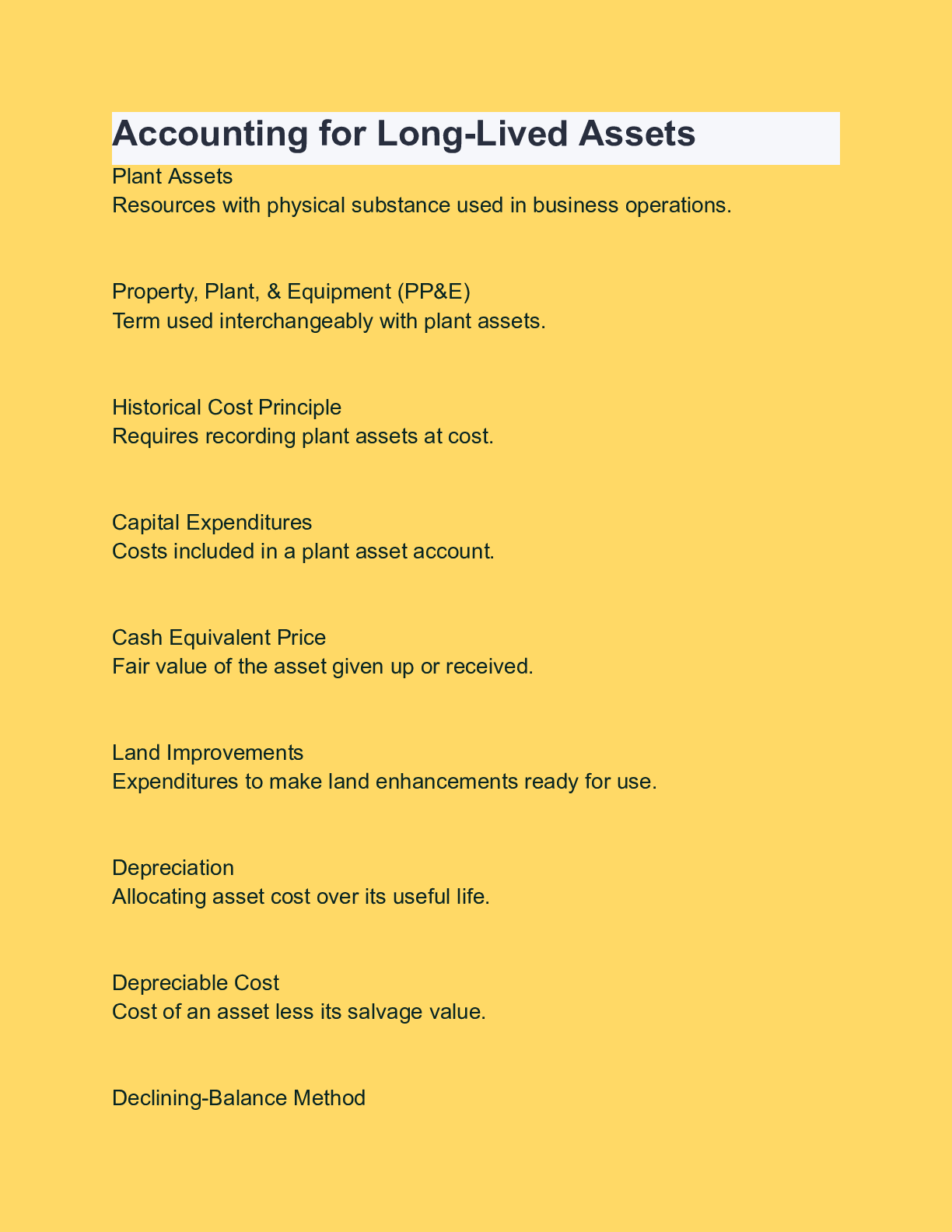
Accounting for Long-Lived Assets
$ 7

University of Maryland, University College BIO 101BIO101_FINAL_1206
$ 6

BSC203 Introduction to ICT Research Methods - Assignment 2 - Project Management Portfolio: Develop a prototype of a smartwatch-based system that uses camera and GPS
$ 10
.png)
WGU C464 Terms and Examples
$ 10
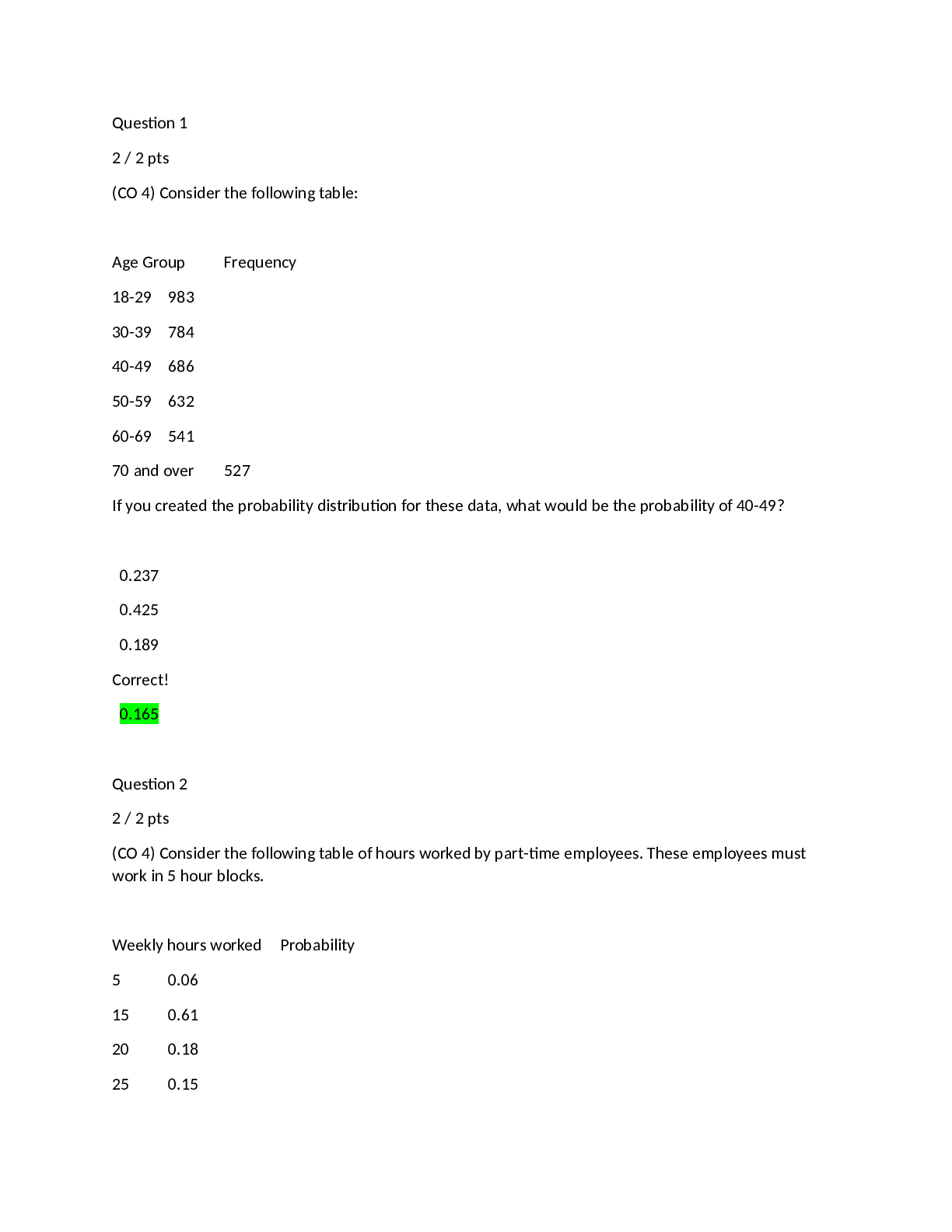
MATH 221 Week 5 Quiz: Statistics for Decision-Making (100% CORRECT ANSWERS)
$ 13

wk2assignment.psy615.pdf Running head: WEEK 2 ASSIGNMENT PSY 615 Week 2 Assignment: Per
$ 10
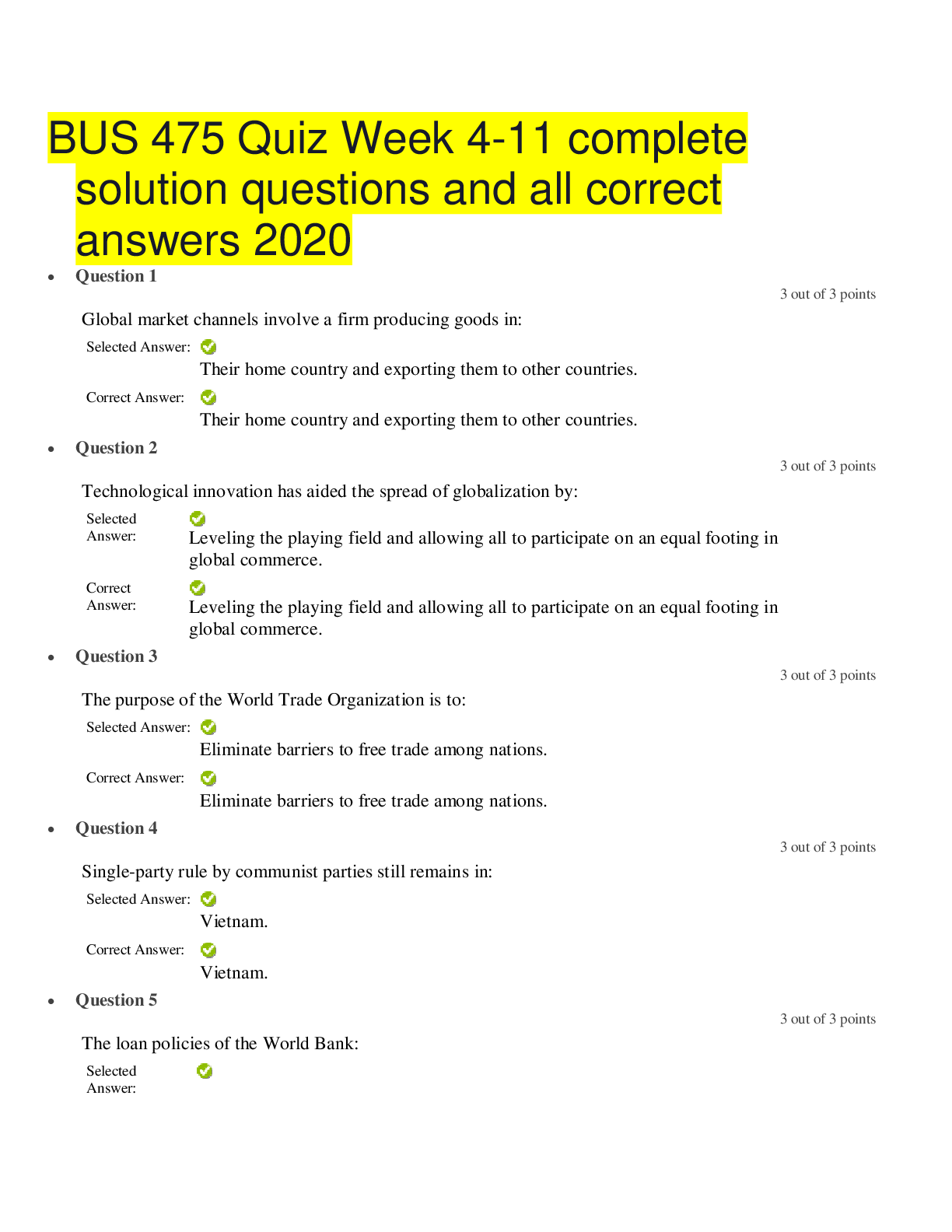
BUS 475 Quiz Week 4-11 complete solution questions and all correct answers 2020 liberty university
$ 9.5

(CS) ICSC 3120 C952 Computer Architecture Complete FA 2025 (With Solns)
$ 12

eBook [PDF] Essential Interviewing A Programmed Approach to Effective Communication 9th Edition By Evans, Hearn, Uhlemann, Ivey
$ 30

Ben A. Kapinsky Jr.– Pediatrics CC – Fatiuge, shortness of breath, and cough | Demographic description – chief complaint – Hx and PE key findings – risk factors
$ 8

AQA June 2022 Question Paper AS PHYSICS Paper 2 7407/2
$ 7

Commercial Law 1 (JHA131): Exam Questions and Answers Commercial Law 1 (University of South Africa) COMMERCIAL LAW I (CLA1501) Revision Questions & Answers
$ 9.5

Methods Toward a Science of Behavior and Experience 10th Edition William J. Ray TEST BANK & INSTRUCTORS MANUAL
$ 22
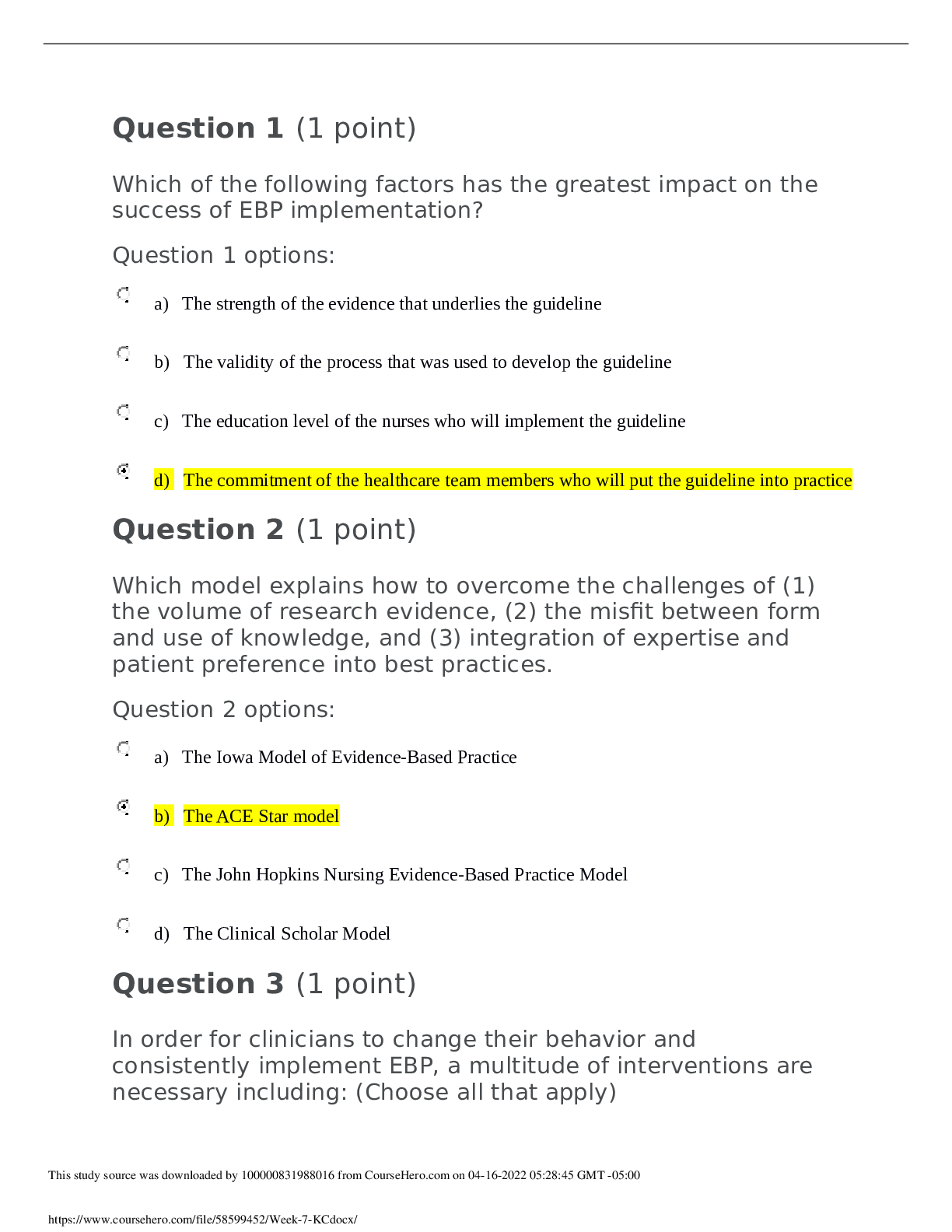
NSG 5003 Week 7 Knowledge Check Quiz - Advanced Pathophysiology
$ 3

Instructor's Solutions Manual F U N D A M E N T A L S OF PROBABILITY WITH STOCHASTIC PROCESSES FOURTH EDITION SAEED GHAHRAMANI
$ 16

Maternity Newborn and Women’s Health Nursing A Case-Based Approach 1st Edition O’Meara. All chapter 1-30 | TEST BANK
$ 15
EDEXCEL GCSE ENGLISH LITERATURE 2022 PAPER 2 OPTION 1 QP
$ 2

eBook [PDF] A Course for Teaching English Learners, 3rd Edition By Lynne Diaz-Rico
$ 30
2023 AQA GCSE GEOGRAPHY 8035/2 Paper 2 Challenges in the Human Environment Question Paper & Mark scheme (Merged) June 2023 [VERIFIED]
$ 7

STR581 FINAL EXAM,GRADED A
$ 18
NSG 5003 Week 5 Knowledge Check
$ 5

[eBook][PDF] IBM SPSS Statistics 26 Step By Step A Simple Guide And Reference, 16th Edition By Darren George, Paul Mallery
$ 14.5

STRAIGHTERLINE MICRO 250 – Principles of Microeconomics Exam 2025 Questions and Answers
$ 17.5
 (2).png)
AQA A-LEVEL PHYSICS 7408/2 Paper 2 Mark scheme June 2022 Version: 1.0 Final
$ 5.5

Agile 56978 E1
$ 9.5

Pearson Edexcel IAL in AS Level History (WHI01/1) Paper 1: Depth Study with Interpretations Option 1A: France in Revolution, 1774-99. Mark Scheme (Results) January 2022
$ 4

NBCOT Latest Predictor Questions and answers. 2022/2023
$ 10

A Level Computer Science H446/01 Computer Systems June 2023 QP
$ 4

Primerica Focused exam (basic principles) Questions with 100% Accurate answers/2022/2023 update.
$ 4
St. Petersburg College-POLI 330N Week 3 Assignment: Essay – Developing a Democracy-Already_Graded_A_100%_Correct
$ 6.5

OCR A Level Further Mathematics B (MEI) Y433/01 Modelling with Algorithms Wednesday 8 June 2022 – Afternoon
$ 9

Test Bank for Systems Analysis and Design 11th Edition By Kenneth Kendall, Julie Kendall
$ 22

eBook PDF Sociology A Brief Introduction (2024 Release) 14th Edition By By Richard T. Schaefer
$ 30

MAIN VERSION PRIORITY ONE EXIT EXAM - QUESTIONS AND ANSWERS ) SCORED A







.png)