*NURSING > QUESTIONS & ANSWERS > WGU Master's Course C706 - Secure Software Design Latest 2022; (All)
WGU Master's Course C706 - Secure Software Design Latest 2022;
Document Content and Description Below
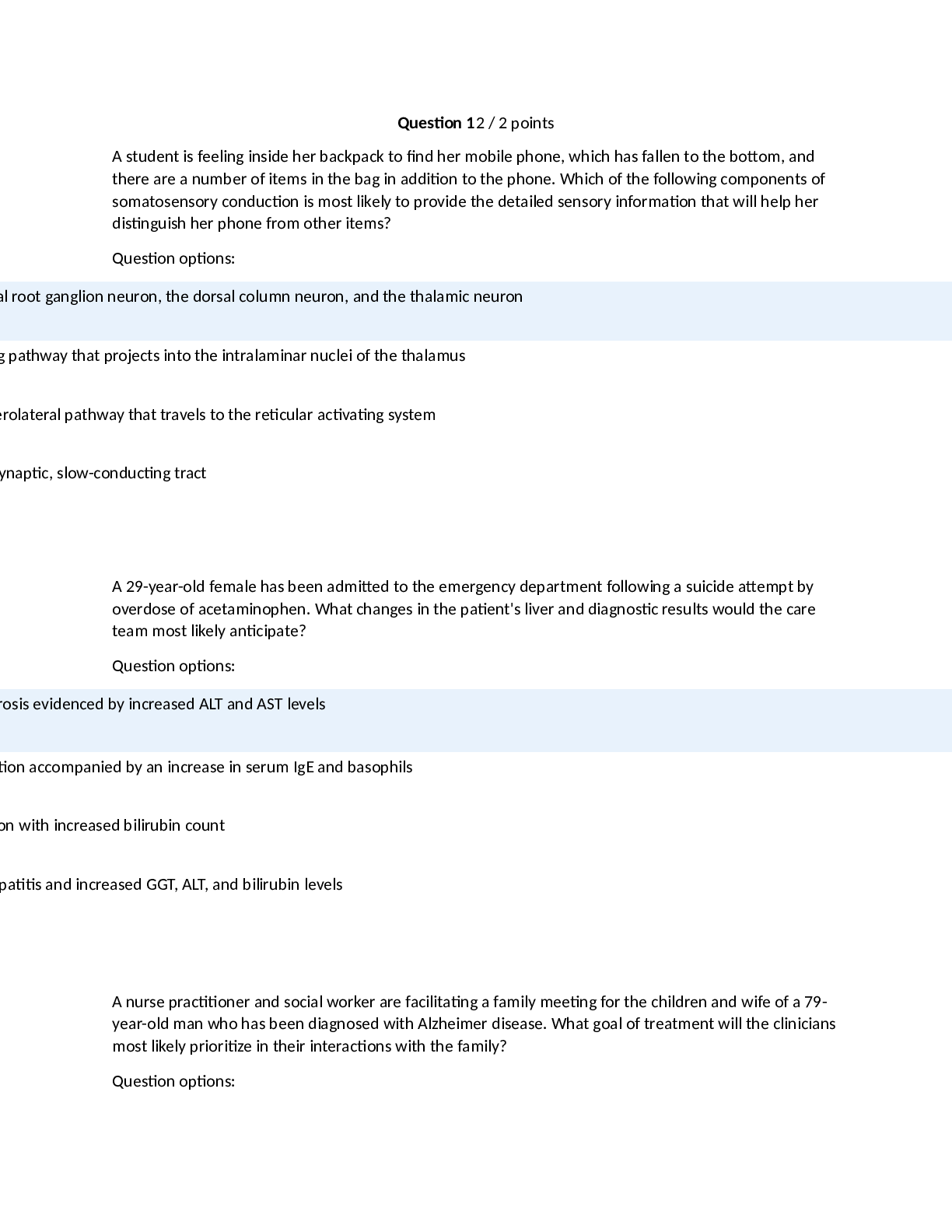
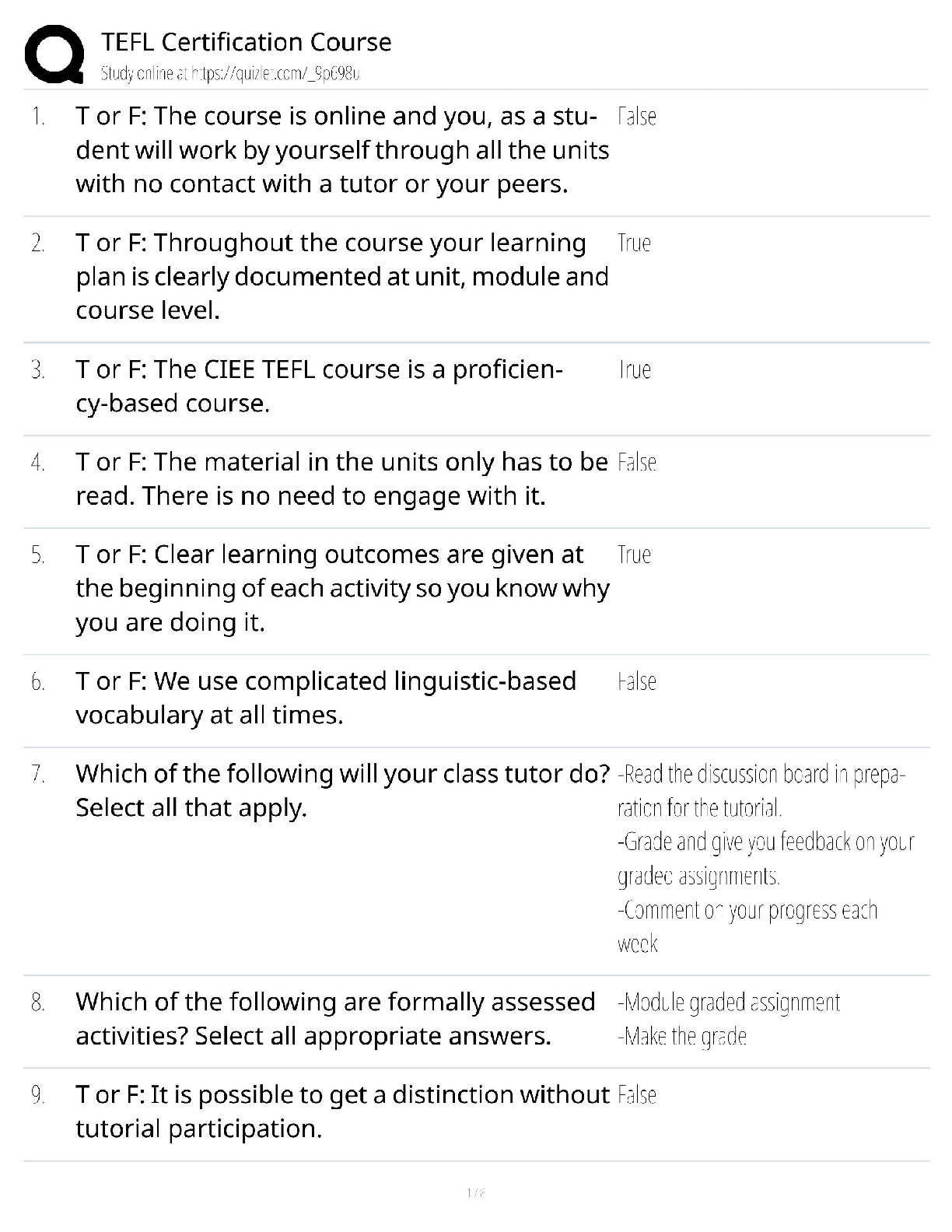
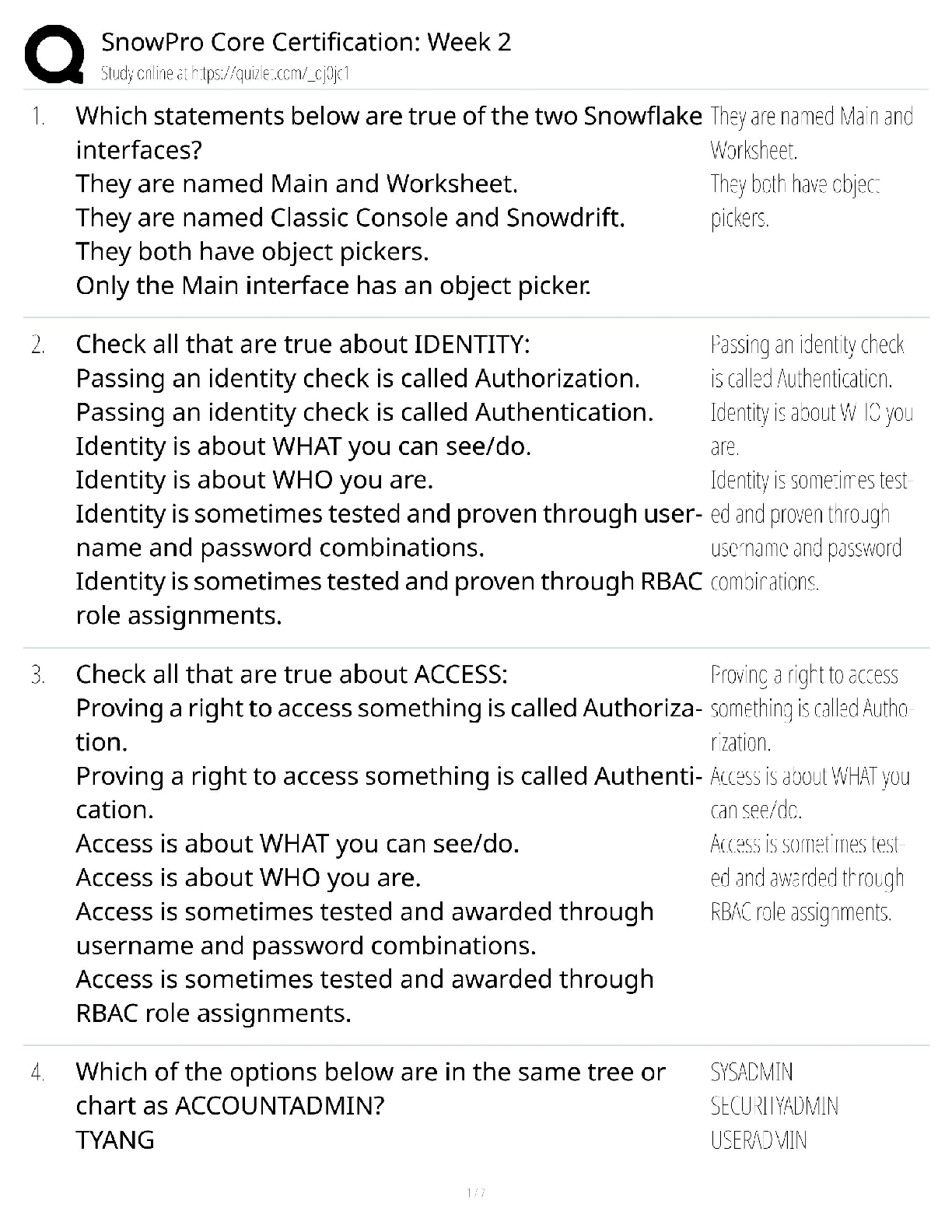
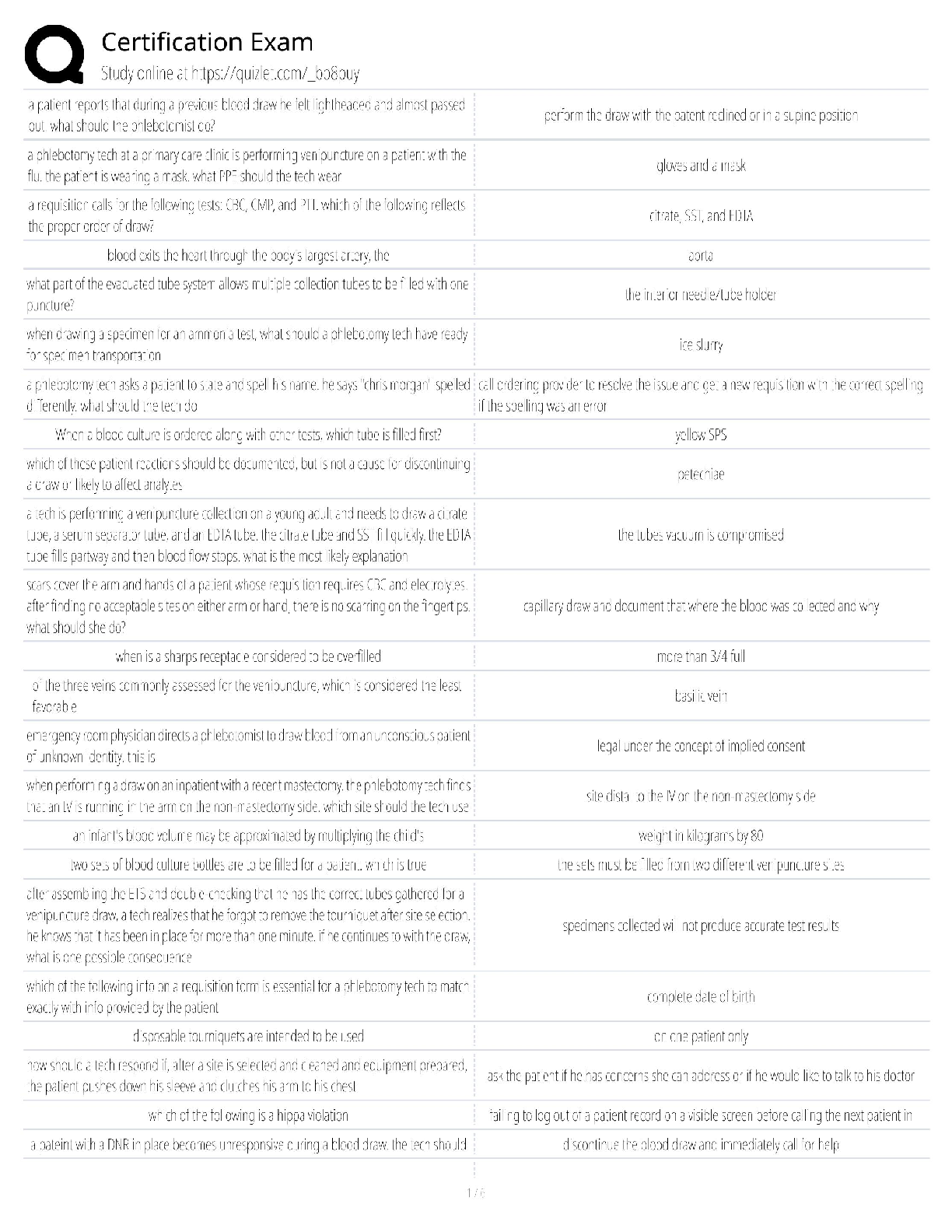
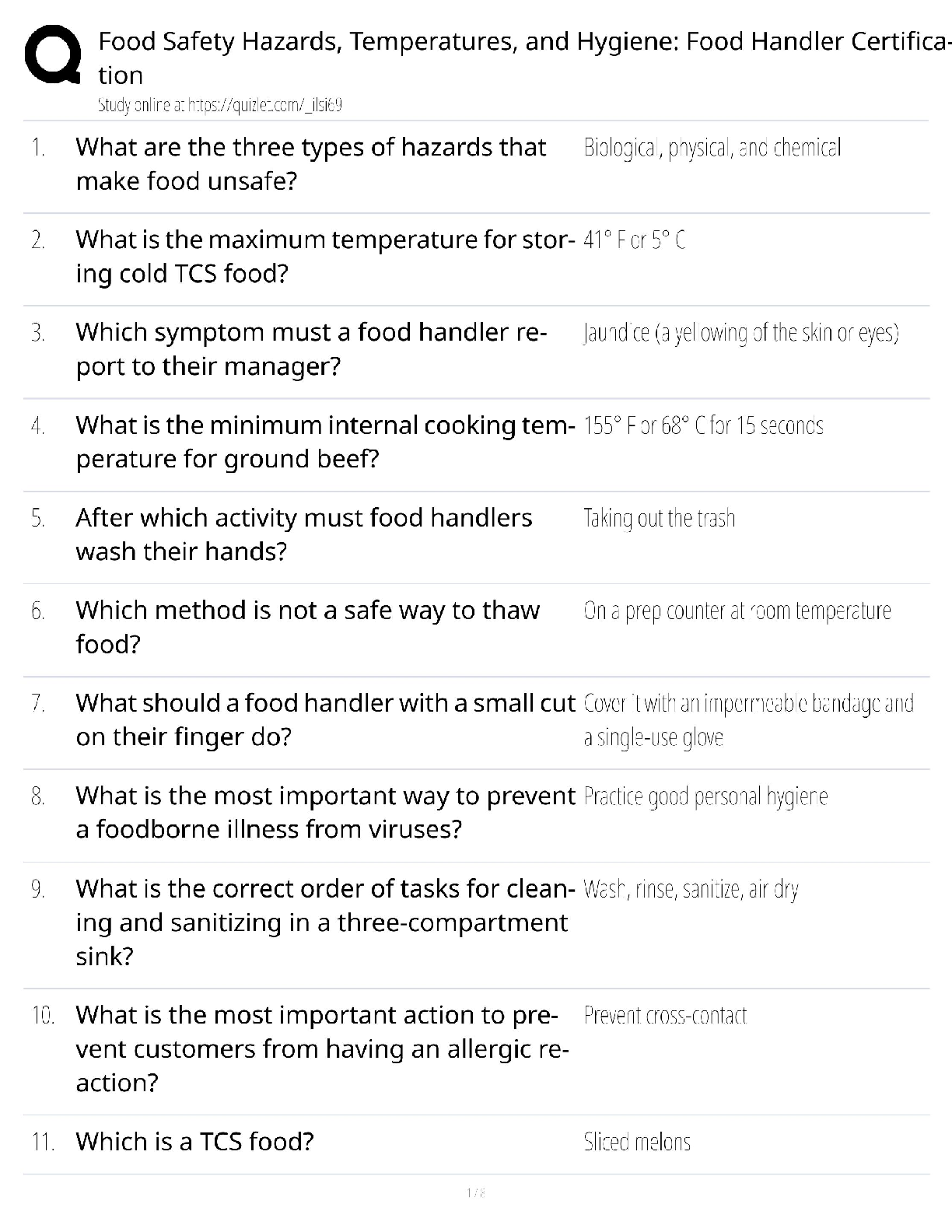
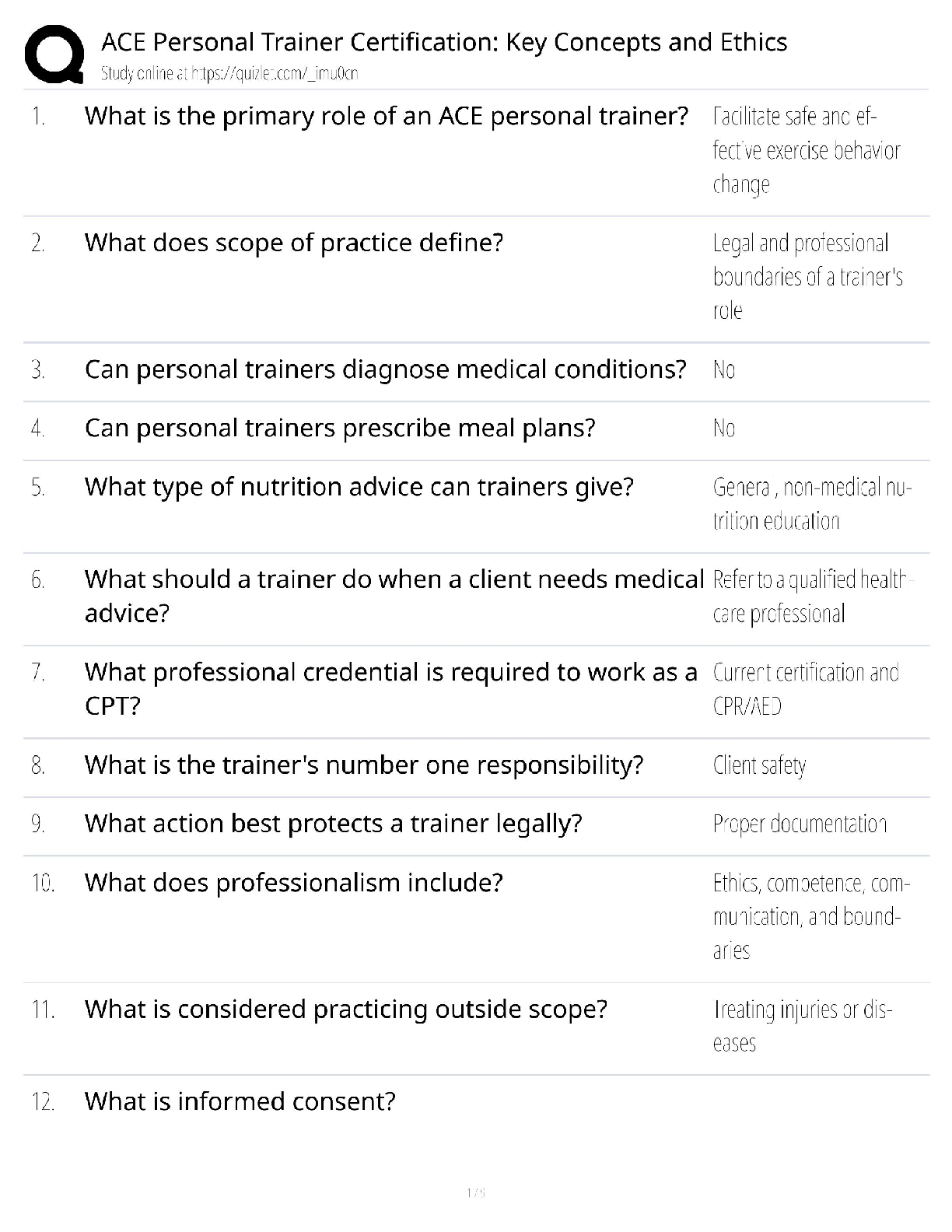
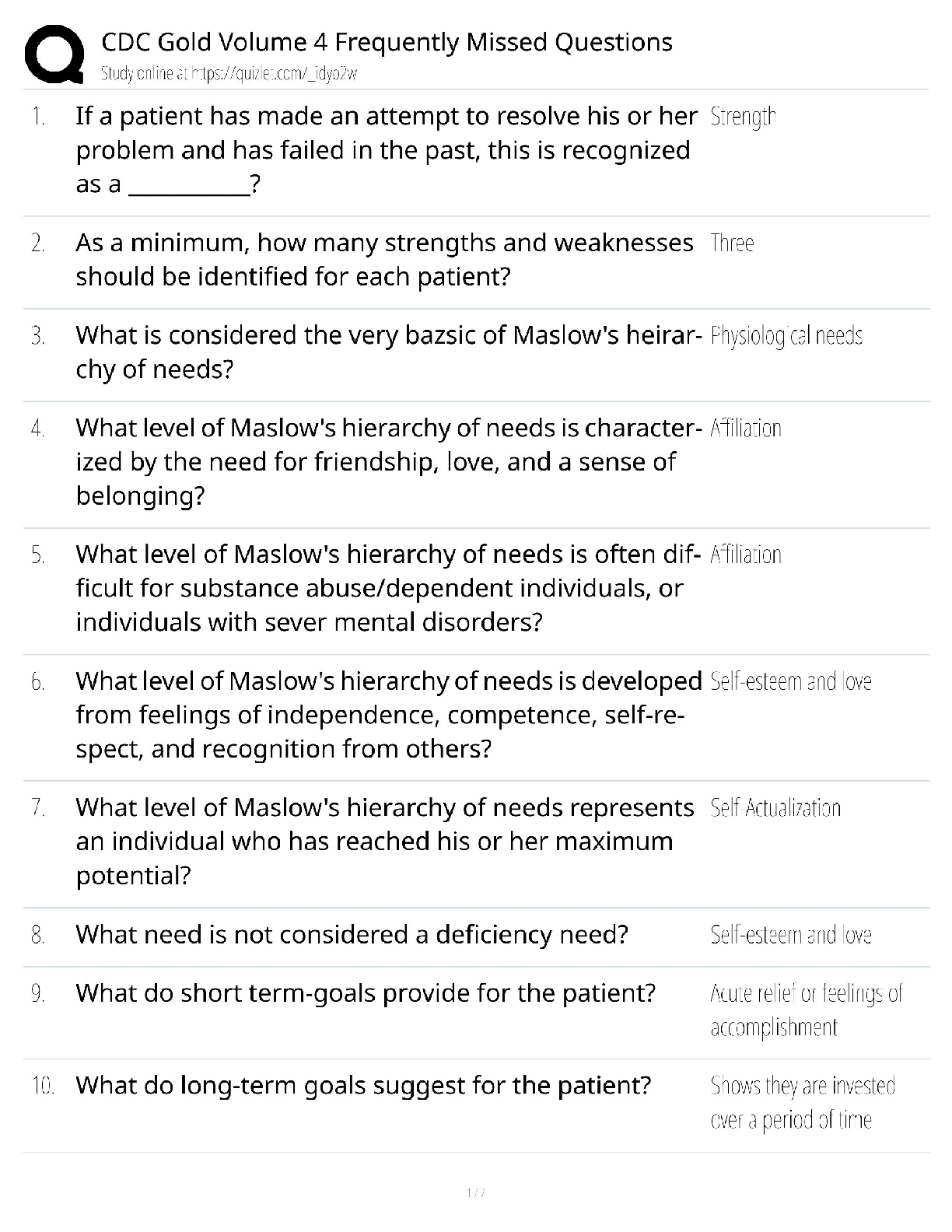
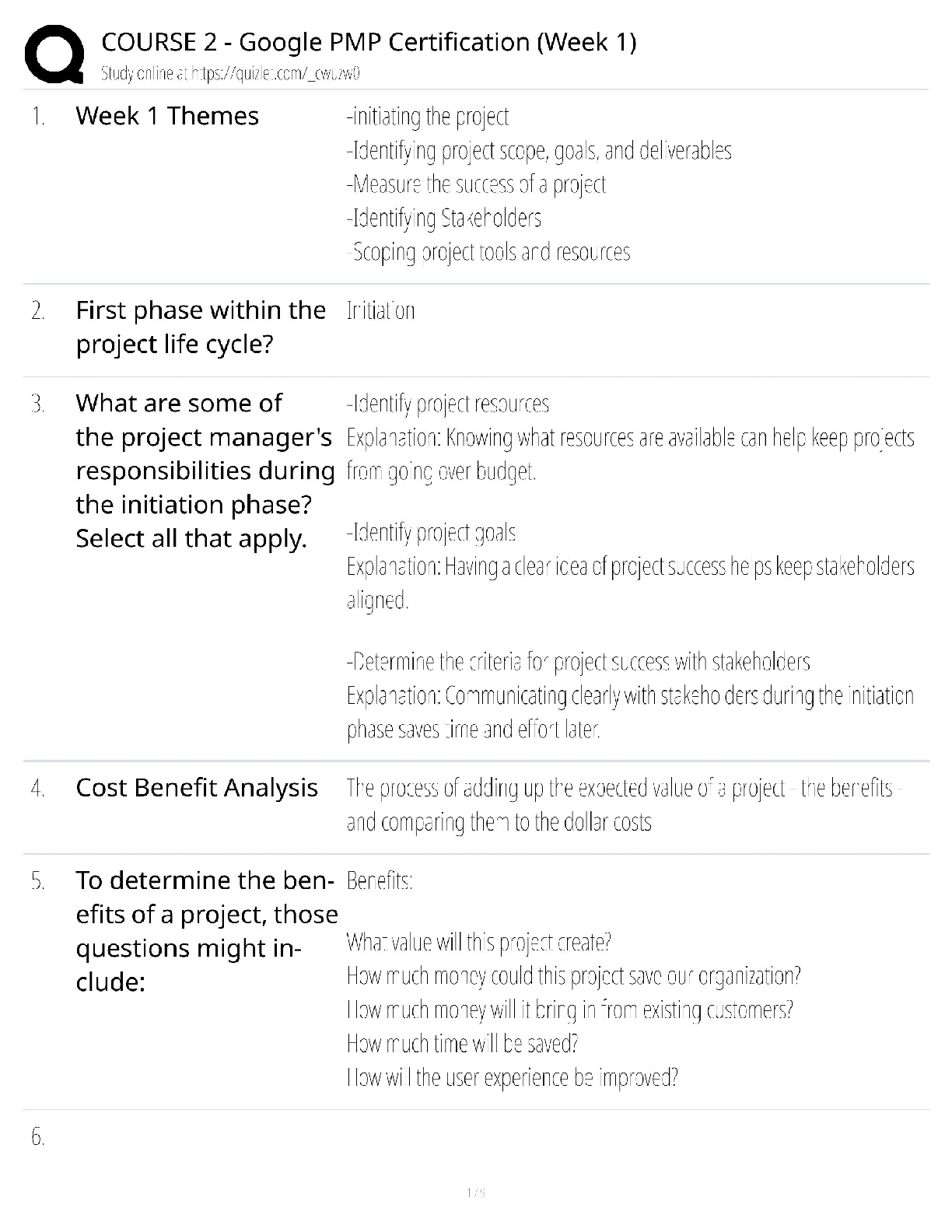
WGU Master's Course C706 - Secure Software Design Latest 2022; Western Governors University Which due diligence activity for supply chain security should occur in the initiation phase of the software ... acquisition life cycle? A Developing a request for proposal (RFP) that includes supply chain security risk management B Lessening the risk of disseminating information during disposal C Facilitating knowledge transfer between suppliers D Mitigating supply chain security risk by providing user guidance Correct Answer- A Which due diligence activity for supply chain security investigates the means by which data sets are shared and assessed? A on-site assessment B process policy review C third-party assessment D document exchange and review Correct Answer- D Consider these characteristics: -Identification of the entity making the access request -Verification that the request has not changed since its initiation -Application of the appropriate authorization procedures -Reexamination of previously authorized requests by the same entity Which security design analysis is being described? A Open design B Complete mediation C Economy of mechanism D Least common mechanism Correct Answer- B Which software security principle guards against the improper modification or destruction of information and ensures the nonrepudiation and authenticity of information? A Quality B Integrity C Availability D Confidentiality Correct Answer- B What type of functional security requirement involves receiving, processing, storing, transmitting, and delivering in report form? A Logging B Error handling C Primary dataflow D Access control flow Correct Answer- C Which nonfunctional security requirement provides a way to capture information correctly and a way to store that information to help support later audits? A Logging B Error handling C Primary dataflow D Access control flow Correct Answer- A Which security concept refers to the quality of information that could cause harm or damage if disclosed? A Isolation B Discretion C Seclusion D Sensitivity Correct Answer- D Which technology would be an example of an injection flaw, according to the OWASP Top 10? A SQL B API C XML D XSS Correct Answer- A A company is creating a new software to track customer balance and wants to design a secure application. Which best practice should be applied? A Develop a secure authentication method that has a closed design B Allow mediation bypass or suspension for software testing and emergency planning C Ensure there is physical acceptability to ensure software is intuitive for the users to do their jobs D Create multiple layers of protection so that a subsequent layer provides protection if a layer is breached Correct Answer- D A company is developing a secure software that has to be evaluated and tested by a large number of experts. Which security principle should be applied? A Fail safe B Open design [Show More]
Last updated: 3 years ago
Preview 1 out of 65 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$12.50
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Dec 11, 2022
Number of pages
65
Written in
All
Additional information
This document has been written for:
Uploaded
Dec 11, 2022
Downloads
0
Views
215





.png)

.png)
.png)
.png)