Question
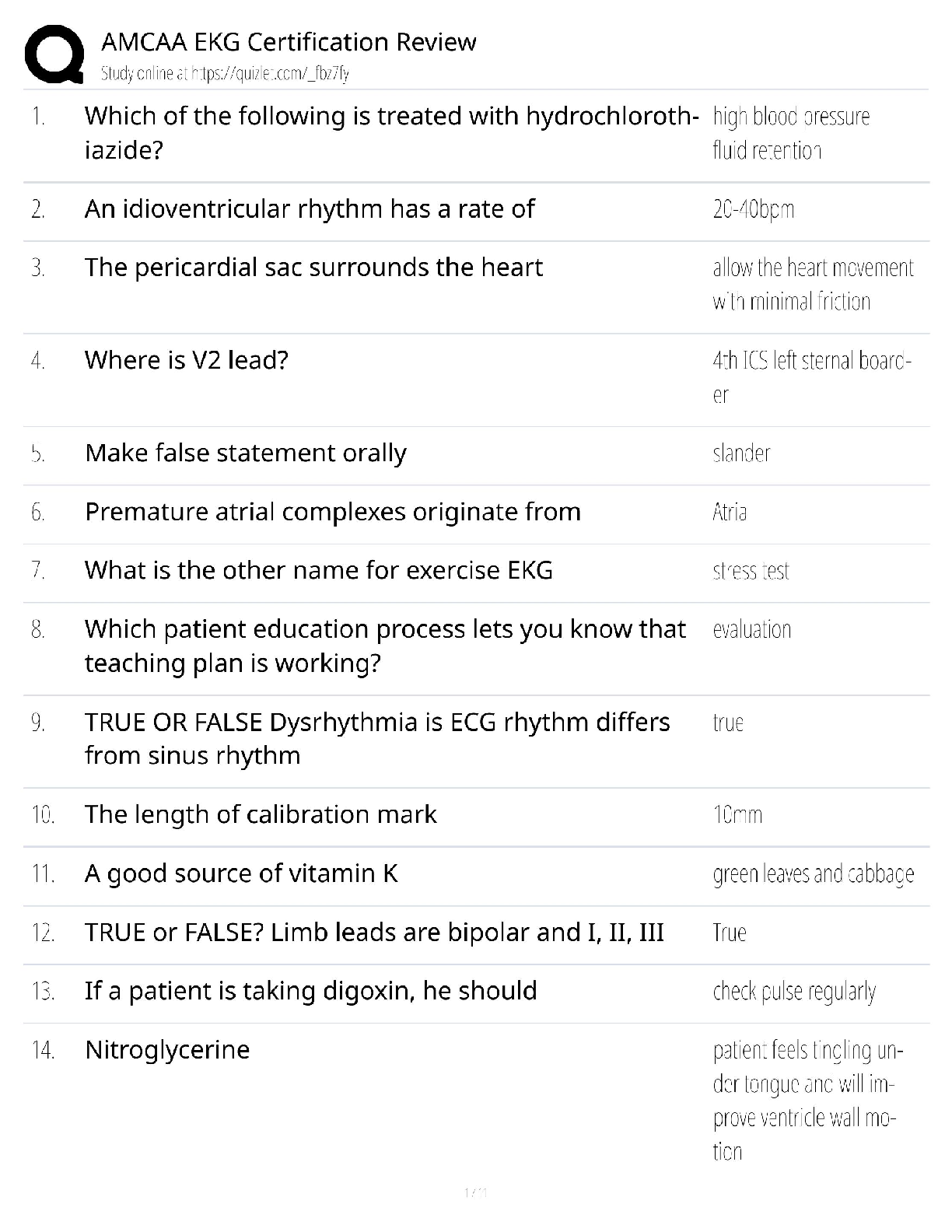
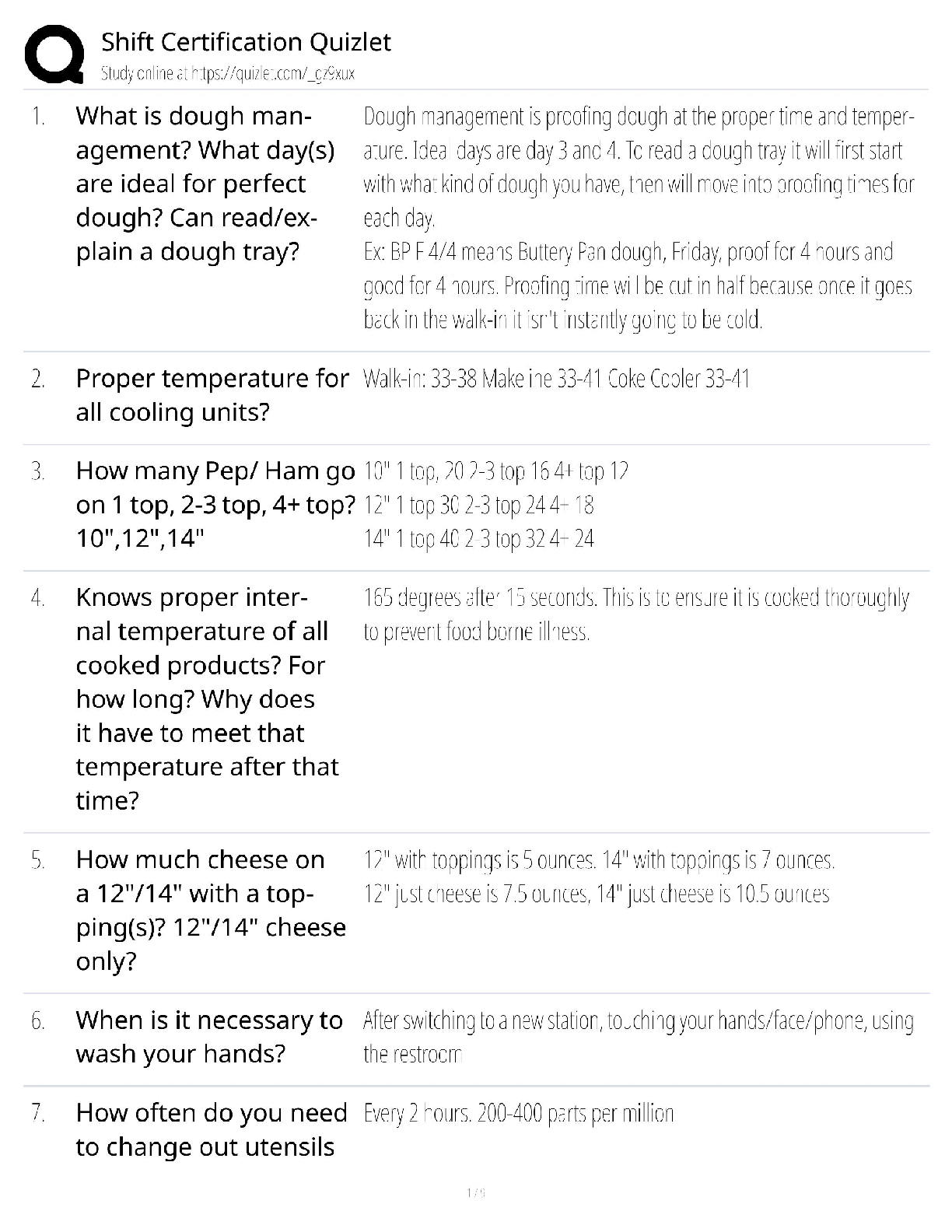
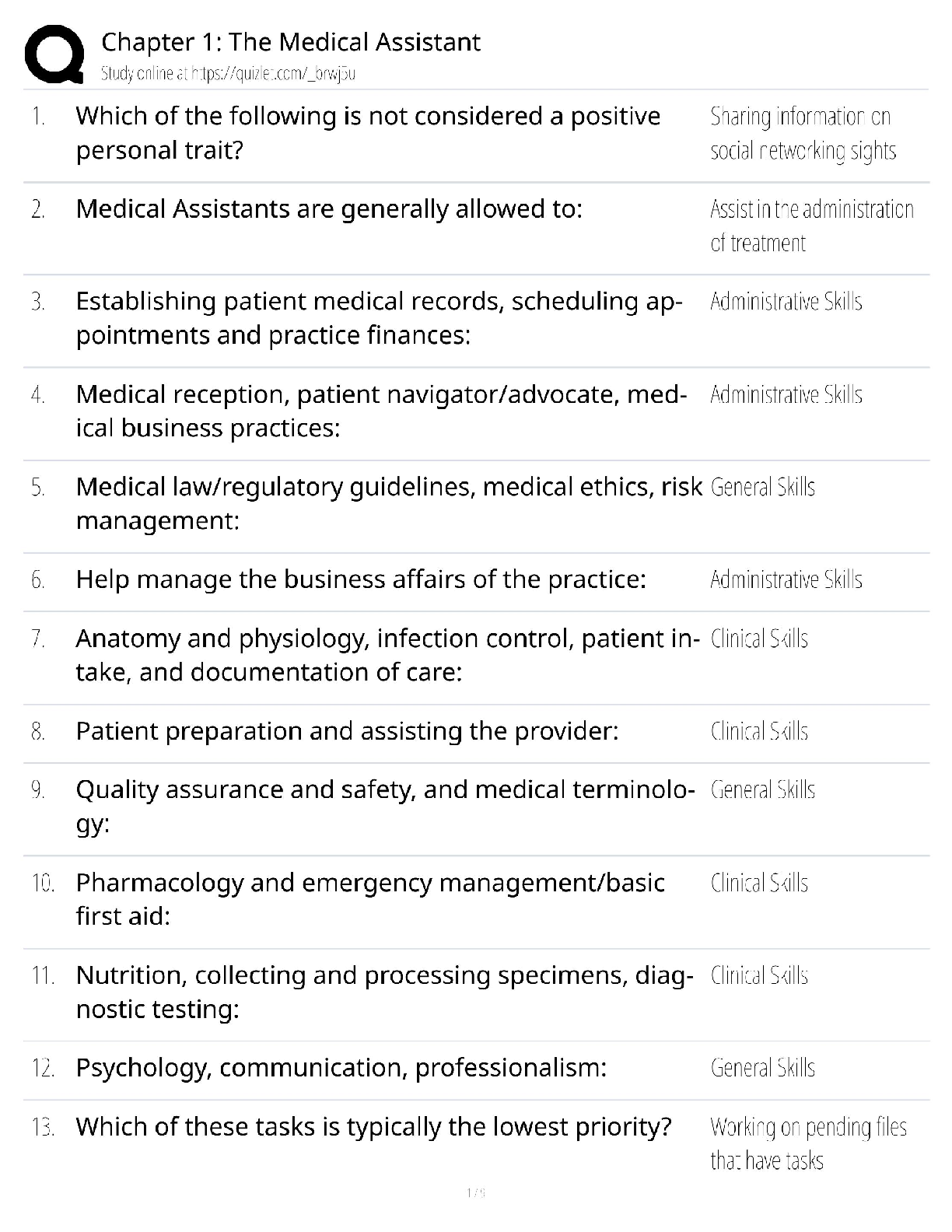
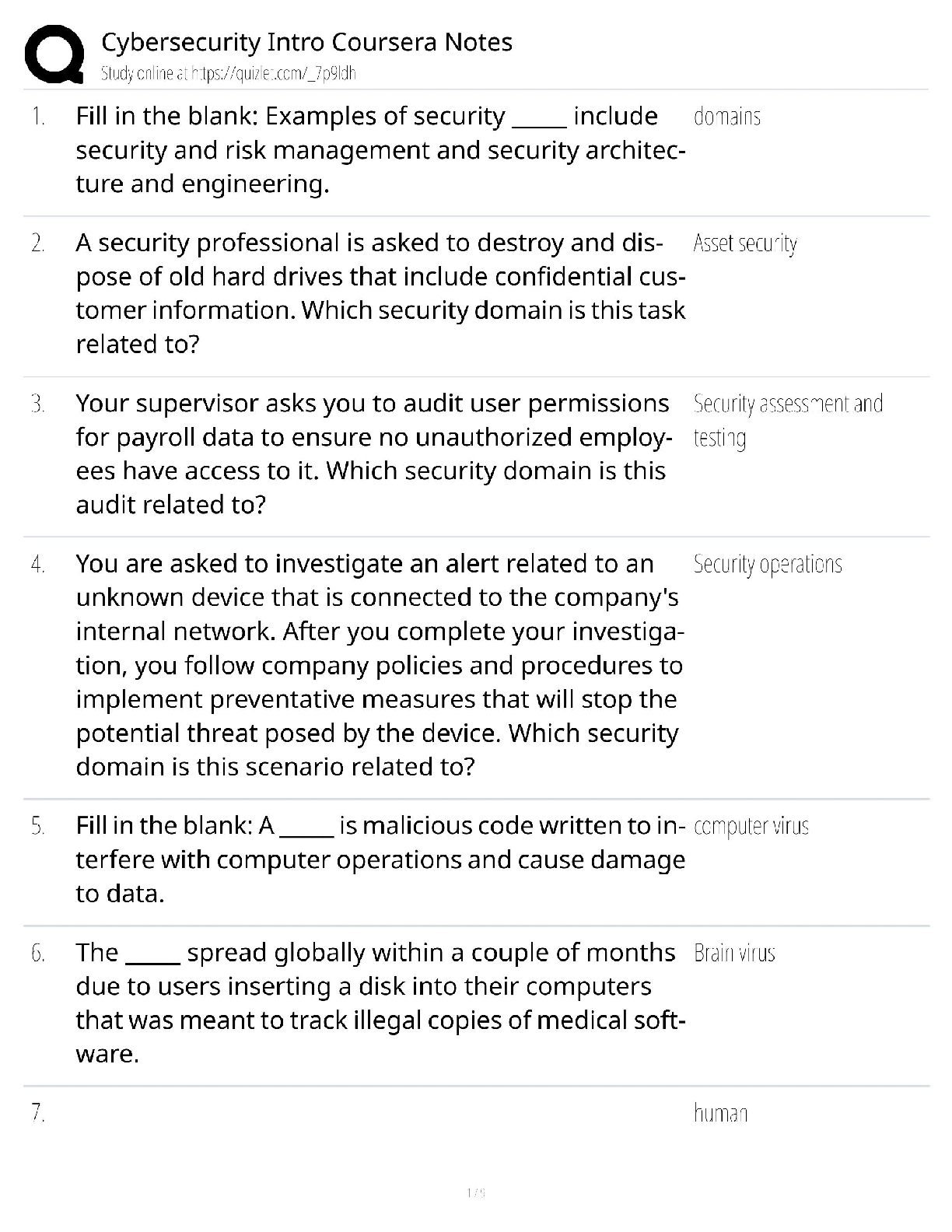
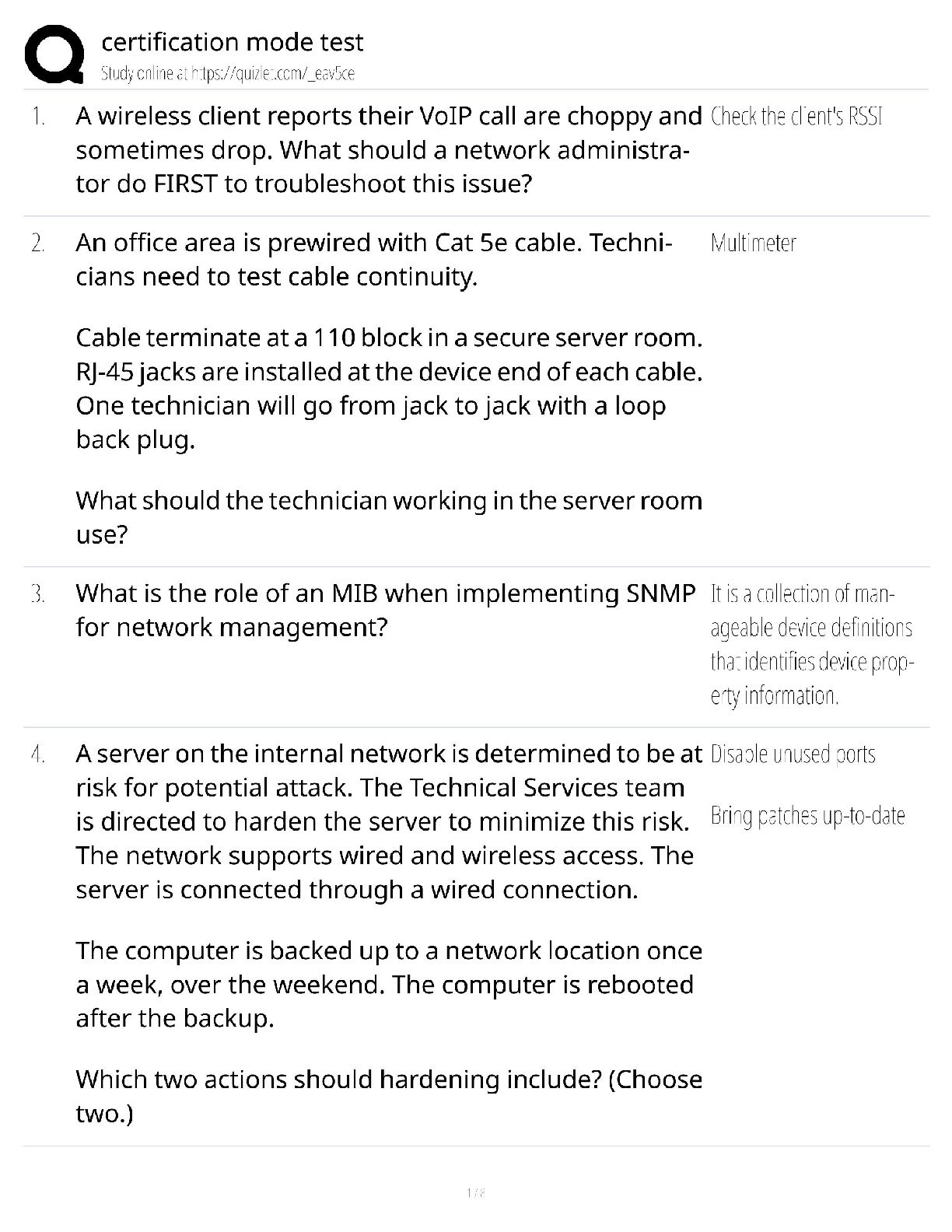
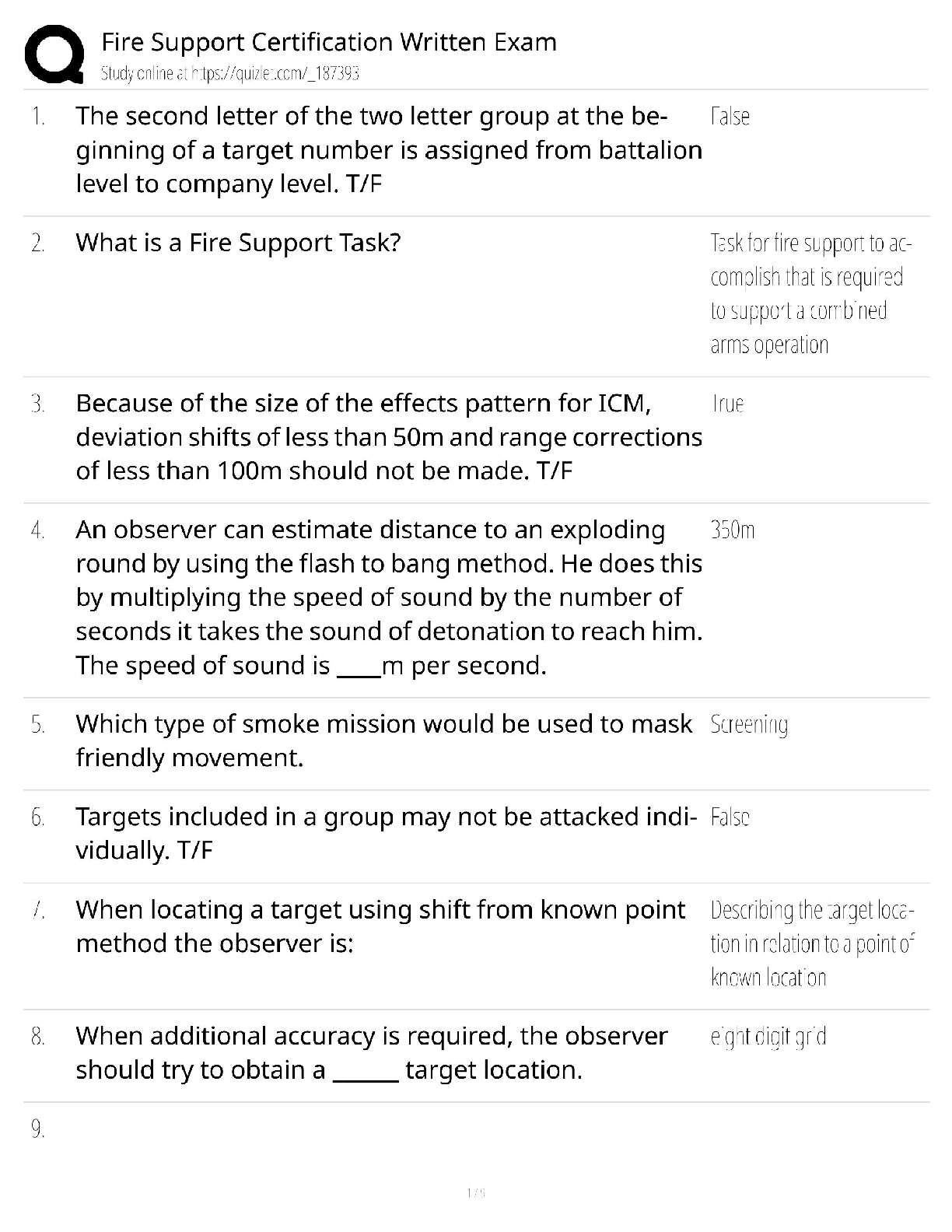
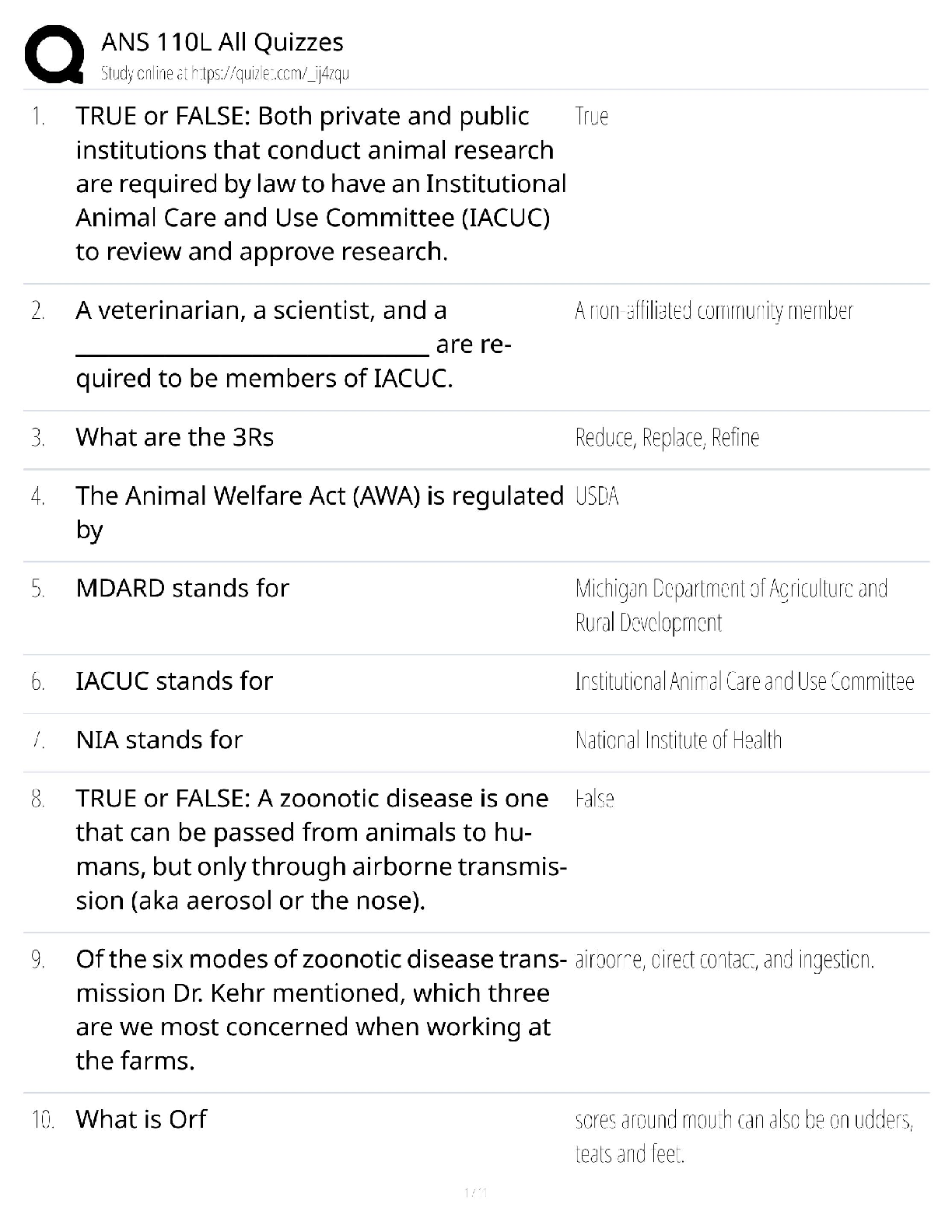
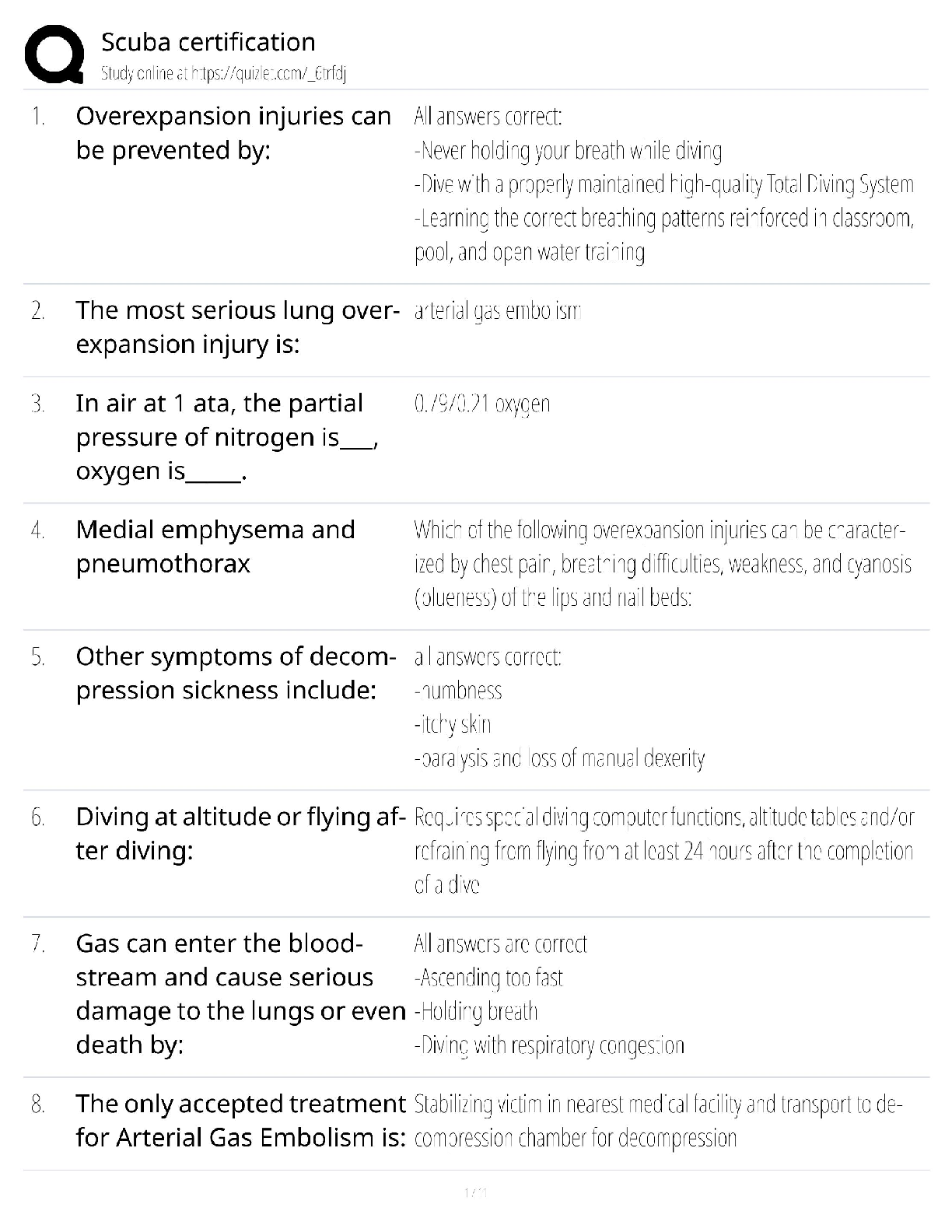
Answered step-by-step
Please choose one of the following threat actors for this (choose A or B):
A) OilRig
B) OCEANLOTUS
slide deck addressing five key areas for chosen threat actor:
1) Hackers are not all
...
Question
Answered step-by-step
Please choose one of the following threat actors for this (choose A or B):
A) OilRig
B) OCEANLOTUS
slide deck addressing five key areas for chosen threat actor:
1) Hackers are not all the same; they range in skill, resources, and capability and often go by
different names. How would you classify this threat actor? Do they go by any aliases? Where are they from? How would you rate the skill level and resources available to this threat actor?
2) Hackers are motivated to act for specific reasons. What are the motivations of your threat actor?
What is the specific geo-political context they are operating in and what insight does that give you for why they are operating in this manner?
3) Hackers utilize specific tradecraft, tactics, and processes to act on their motivations.
Describe the range of efforts used by your threat actor to engage in the hacking process. Utilize the Lockheed Martin Kill Chain to help describe those efforts.
4) Hackers utilize the hacking process to achieve certain "end-effects" on their target. Provide
examples or case studies of attacks your threat actor has been involved with over the years and describe their primary, secondary, and second order effects.
5) Not all hackers represent a strategic problem for policy makers. How would you characterize
your threat actor, are they chiefly a private problem for businesses or a public concern for policy makers? How should policy makers respond? Engineering & TechnologyComputer ScienceCYBER SECU J
Share Question
Comments (7)
Answer & Explanation
Solved by verified expert
1. The OceanLotus hacking group is back with a new campaign in 2019 complete with new exploits, decoys, and self-extracting malicious archives.
Also known as APT32, SeaLotus, APT-C-00, and Cobalt Kitty, OceanLotus is a hacking group which operates across Asia and focuses on gathering valuable intel on corporate, government, and political entities across Vietnam, the Philippines, Laos, and Cambodia.
Human rights outfits, the media, research institutes, and maritime construction firms are the hackers' preferred targets and past attacks against these types of organizations have been linked to their campaigns.
APT32 or OceanLotus is a Vietnam-based threat actor that has been active since 2014. The group has compromised various industries like manufacturing, network security, technology infrastructure, banking, media, and consumer products. Their signature malware payload includes WINDSHIELD, KOMPROGO, SOUNDBITE, and PHOREAL.
OceanLotus has recently started using a new backdoor, which sideloads into a legitimate Symantec dll file. They leverage ActiveMime files that employ social engineering methods to entice the victim into enabling macros.
2. OceanLotus is behind a series of fake news websites and Facebook pages meant to target victims with malicious software. They seem to have two main goals in the campaign:
Gather information about the visitors to the fake media sites through a web profiling framework. Target victims with malware meant to log targets' keystrokes.
It looks like OceaLotus has been sending victims links to its sites through spearphishing or social media messaging. It must be noted that the fake sites are not entirely malicious. The news topics it contains focus on trending issues in Vietnam and Southeast Asia.
[Show More]
![Preview image of Engineering & Technology Computer Science CYBER SECURITY[ ANSWERED STEP BY STEP WITH EXPLANATION]. document](https://scholarfriends.com/storage/QuestionZX.png)







.png)

.png)
.png)
.png)