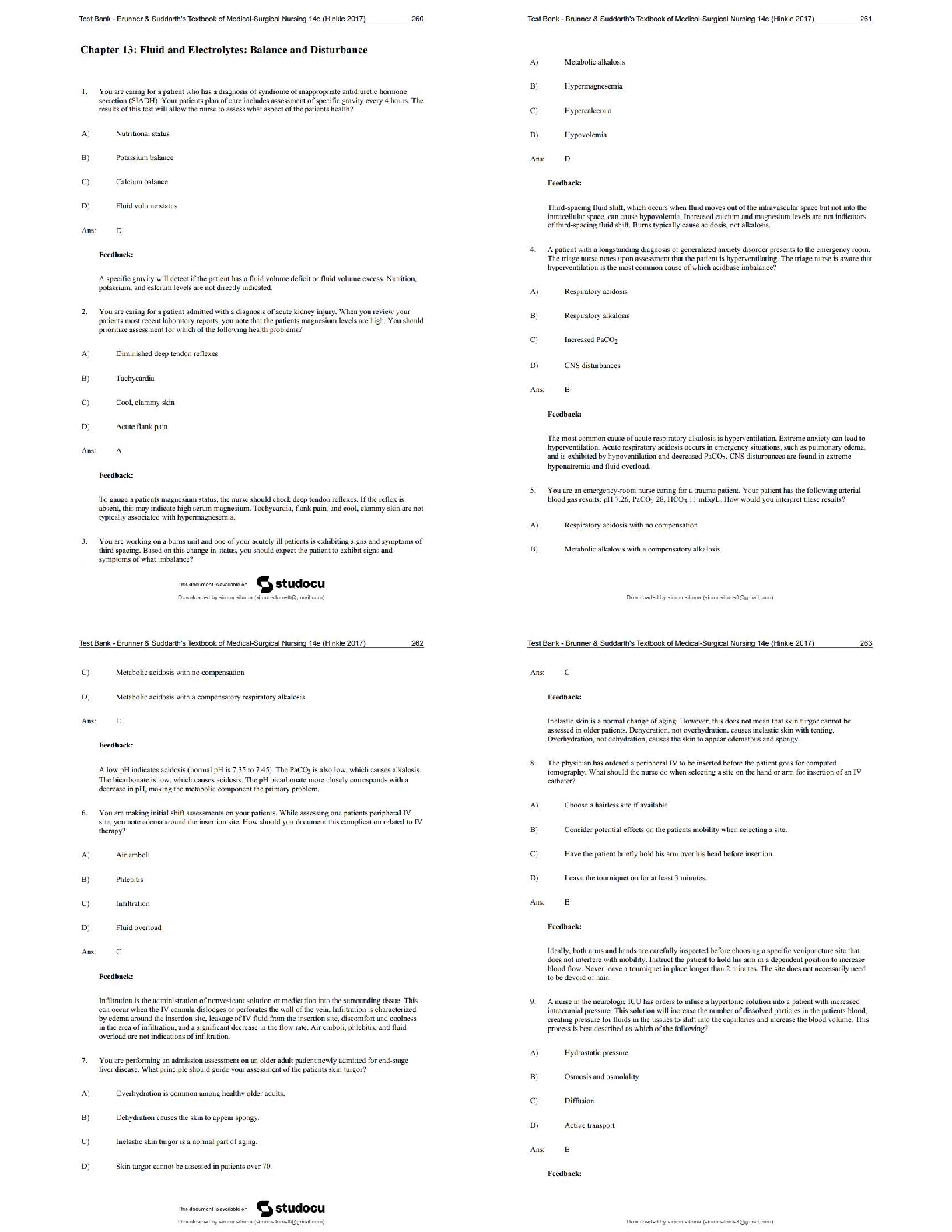
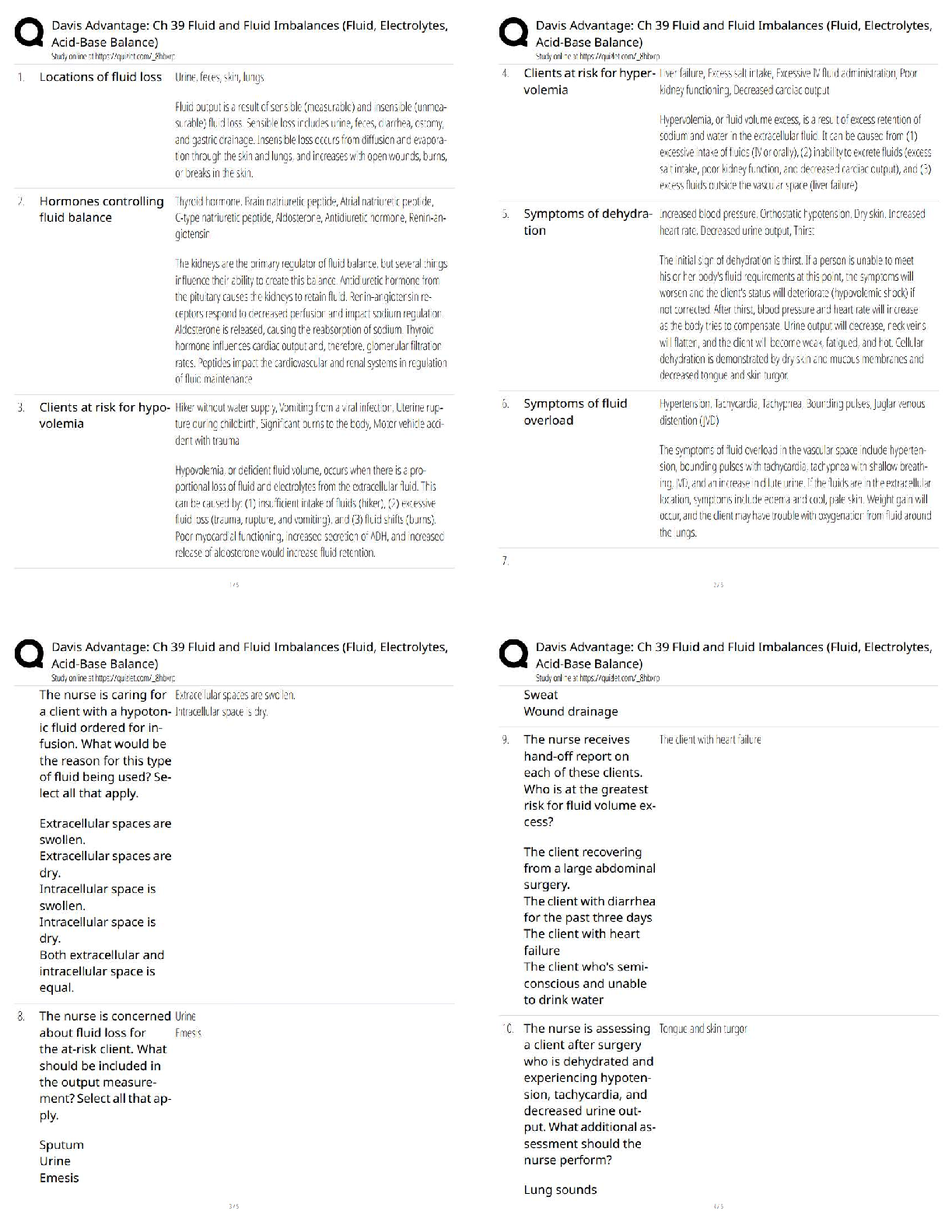
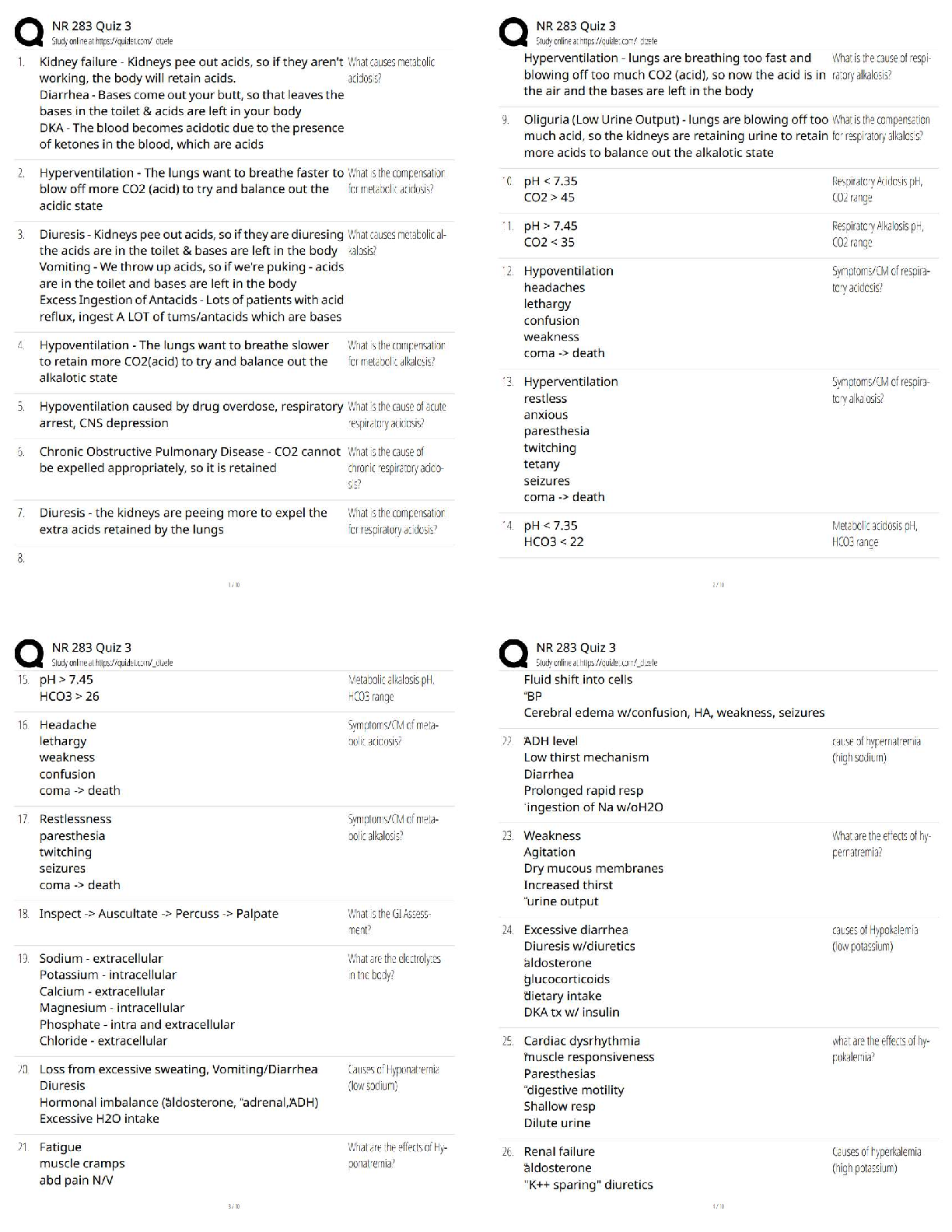
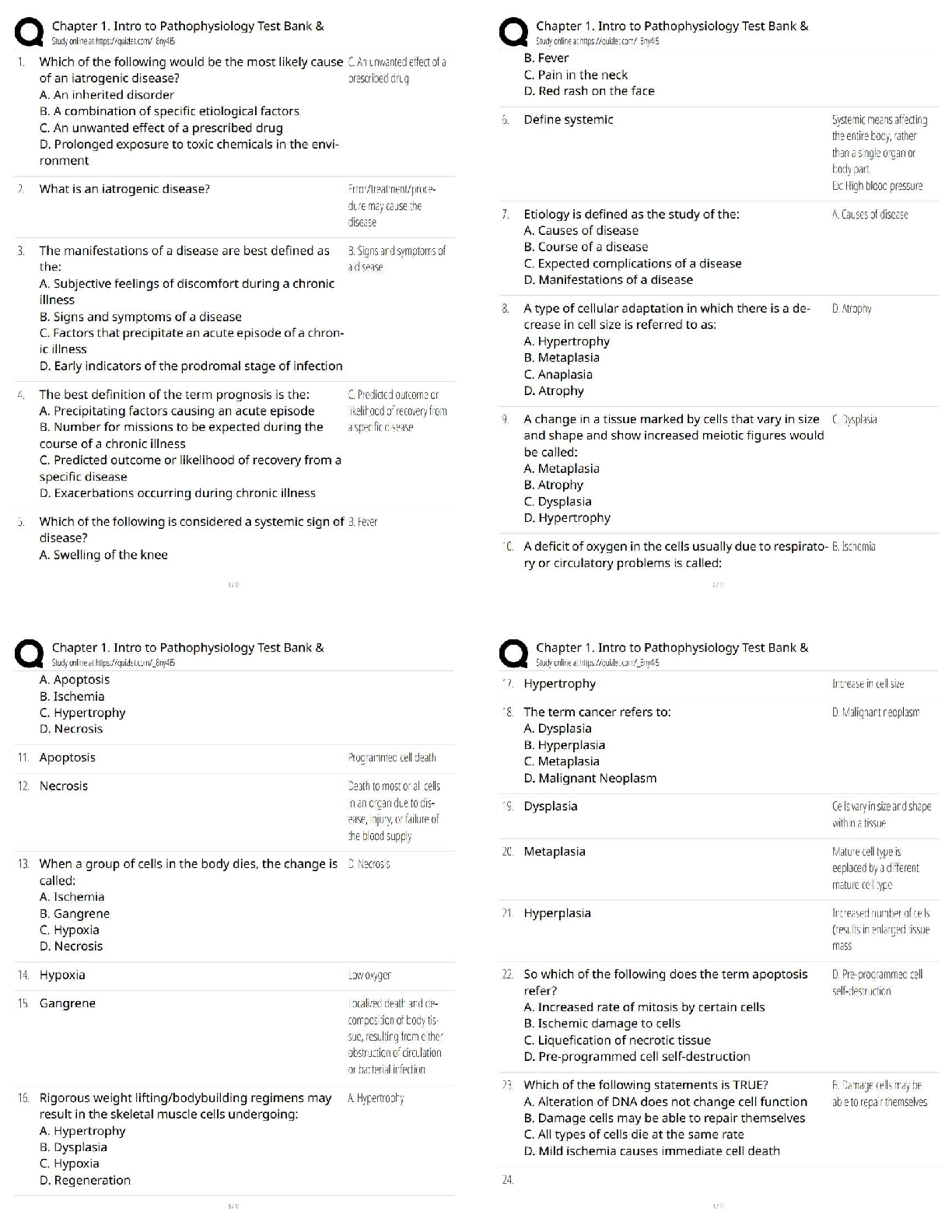
Name all OSI layers - THE CORRECT ANSWER IS Application, Presentation, Session, Transport, Network, Data Link, Physical. Name all TCP/IP layers - THE CORRECT ANSWER IS Application, Transport, internet, Network Access. Na
...
Name all OSI layers - THE CORRECT ANSWER IS Application, Presentation, Session, Transport, Network, Data Link, Physical. Name all TCP/IP layers - THE CORRECT ANSWER IS Application, Transport, internet, Network Access. Name Four TCP head flags - THE CORRECT ANSWER IS ACK, FIN, SYN, URG, PSH, RST Which layer does HTTP protocl reside in the OSI model. - THE CORRECT ANSWER IS Layer 7, Application. Which layer does Ethernet reside in the OSI model. - THE CORRECT ANSWER IS Layer 2, Data link. Which Layer does IPv4 & IPv6 reside in TCP/IP model. - THE CORRECT ANSWER IS Layer 4, transport. RFC 1918 addresses - THE CORRECT ANSWER IS 10.0.0.0 - 10.255.255.255 (10/8 prefix) 172.16.0.0 - 172.31.255.255 (172.16/12 prefix) 192.168.0.0 - 192.168.255.255 (192.168/16 prefix) Name the well know, registered and dynamic port ranges. - THE CORRECT ANSWER IS Well Known(0-1023), Registed(1024-49,151) & Dynamic(49,152-65,535) What is an ephemeral port? - THE CORRECT ANSWER IS An ephemeral port is a short-lived transport protocol port for Internet Protocol (IP) communications. Can be used by both TCP & UDP. What does IANA stand for? - THE CORRECT ANSWER IS Internet Assigned Numbers Authority Name 10 common ports and there protocols. - THE CORRECT ANSWER IS FTP21, SSH22, DHCP67(C), DHCP68(S), NTP123, MYSQL3306, RDP3389, HTTP80, HTTPS443, SMB445, KERBEROS88, CHARGEN19(UDP), DNS53, TACAS49, WHOIS43, MSSQL1433, HIDDEN MSSQL2433. Name five network types. - THE CORRECT ANSWER IS LAN, WAN, MAN, VLAN, WLAN, PAN. Name five network topologies - THE CORRECT ANSWER IS Mesh, Ring, star, Tree, Bus. Name five common ethernet and FDDI cable types. - THE CORRECT ANSWER IS 100Base5, 10Base2, 10BaseT, 100Base-FL, 1000Base-T. What is WIFI the alias for? - THE CORRECT ANSWER IS IEEE 802.11 What does VLAN stand for? - THE CORRECT ANSWER IS Virtual Local Area Network How does VLAN work? - THE CORRECT ANSWER IS Virtual Local Area Networks (VLANs) separate an existing physical network into multiple logical networks. Thus, each VLAN creates its own broadcast domain. Communication between two VLANs can only occur through a router that is connected to both. Name five common ICMP types. - THE CORRECT ANSWER IS 8-echo, 0-echo reply, 30-trace route, 5-redirect, 3-destination unreachable, 11, time execeed. What does ICMP stand for? - THE CORRECT ANSWER IS Internet Control Message Protocol What does TTL stand for? - THE CORRECT ANSWER IS Time to Live What is TTL? - THE CORRECT ANSWER IS TTL is a hop count system, and each router decreases the TTL by 1. Upon reaching 0, the packet is dropped. This way you don't have packets not reaching their destination and clogging the network. OS TLL numbers? - THE CORRECT ANSWER IS 128 Windows, 64 linux, 255 solaris(kapp) What is Traceroute - THE CORRECT ANSWER IS Traceroute is when you send a packet with a TTL value of 1 once it reaches the first router it will die sending a ICMP message to sender, at which point the sender can send another one with a value of 2 to see how far it will go. By doing this we can see how many hops it will take to reach our target. (A good way of enumeration of a network, when in a black box pen-test.) What is ping sweep? - THE CORRECT ANSWER IS Ping sweep is just a technique that can be used to find out which hosts are alive in a network or large number of IP addresses. Name Five Namp Flags. - THE CORRECT ANSWER IS (TCP SYN scan, -sS) (Null Scan, -sN) (Ping Scan, -sP) (Ack Scan, -sA) (OS dect, -O) What are the three firewall states? - THE CORRECT ANSWER IS Open, Filtered Dropped Blocked, Closed not listening. What is TCP window size? - THE CORRECT ANSWER IS Window size a method of controlling the flow of packets between two computers or network hosts. Decieded in the tcp three way handshake. What is encoding? - THE CORRECT ANSWER IS Encoding transforms data into another format using a scheme that is publicly available so that it can easily be reversed. What is encryption? - THE CORRECT ANSWER IS scrambles information into an alternative form that requires a key or password to decrypt the information back into its orginial form. What is hashing - THE CORRECT ANSWER IS Hashing serves the purpose of ensuring integrity, i.e. making it so that if something is changed you can know that it's changed. What is obfuscation? - THE CORRECT ANSWER IS The purpose of obfuscation is to make something harder to understand, usually for the purposes of making it more difficult to attack or to copy. What is symmetric encryption? - THE CORRECT ANSWER IS An encryption method in which the same key is used to encrypt and decrypt the data. What is asymmetric encryption? - THE CORRECT ANSWER IS An encryption method in which two keys (one private, one public) are used to encrypt and decrypt a message. Vunerable hashing algorithms - THE CORRECT ANSWER IS MD5, Sha-1, NTLM, LanMan. Eny Symmertric algorithms. - THE CORRECT ANSWER IS > DES > 3DES (or Triple DES) > RC4 > RC5 > AES (aka Rijndael) > Blowfish > Serpent > Twofish > CAST5 > IDEA Eny Asymmertric algorithms. - THE CORRECT ANSWER IS > Elliptic curve > RSA > Diffie-Hellman > DSA > Key serialization > ELGAMAL What is a hash collision? - THE CORRECT ANSWER IS A Hash Collision Attack is an attempt to find two input strings of a hash function that produce the same hash result. Because hash functions have infinite input length and a predefined output length, there is inevitably going to be the possibility of two different inputs that produce the same output hash. What is Ipsec. - THE CORRECT ANSWER IS Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts the packets of data sent over an Internet Protocol network. What are two modes of operation for IPsec. - THE CORRECT ANSWER IS Host-to-Host and Tunnelling mode. What does IKE stand for? - THE CORRECT ANSWER IS Internet Key Exchange What does the linux file permission of 777 mean - THE CORRECT ANSWER IS everyone(owner, group, users) has read write and excuate of the file. What is the definition of ACL? - THE CORRECT ANSWER IS Access control list. Common tool used on Microsoft operating system for managing process. - THE CORRECT ANSWER IS Task Manager. Where is the SAM file located? - THE CORRECT ANSWER IS C:WindowsSystem32driversetc What is an AS system. - THE CORRECT ANSWER IS autonomous system What is whois and what port ? - THE CORRECT ANSWER IS a public Internet database that contains information about Internet domain names and the people or organisations that registered the domains. It is a source of information that can be used to exploit system vulnerabilities. port 43. Name five DNS record. - THE CORRECT ANSWER IS CNAME, SOA, A, AAAA, MX, HINFO What does a cname record point to. - THE CORRECT ANSWER IS A Canonical Name or CNAME record is a type of DNS record that maps an alias name to a true or canonical domain name. CNAME records are typically used to map a subdomain such as www or mail to the domain hosting that subdomain's content. what does the mx record point to. - THE CORRECT ANSWER IS an MX recored points to a A record Difference between iterative and recurisve querys - THE CORRECT ANSWER IS Iterative Iterative DNS queries are ones in which a DNS server is queried and returns an answer without querying other DNS servers, even if it cannot provide a definitive answer. Iterative queries are also called non-recursive queries. Recursive Recursive DNS queries occur when a DNS client requests information from a DNS server that is set to query subsequent DNS servers until a definitive answer is returned to the client. What are the secuiry issues with recursive querys - THE CORRECT ANSWER IS Servers that support this type of request are vulnerable to fake requests from a spoofed IP address, causing a dos attack due to large number of requests. What does NNTP stand for ? - THE CORRECT ANSWER IS network news transfer protocol. Name five Network managment protocols - THE CORRECT ANSWER IS telnet, ssh, tftp, snmp, ntp, cisco reverse telnet. Why is telnet not secure - THE CORRECT ANSWER IS transfers everything over plain text. Why is TFTP not secure - THE CORRECT ANSWER IS It sends files over UDP not over TCP and does not have any built in encryption, also it does not support authentication functions. Name five networking protocols - THE CORRECT ANSWER IS ARP, VRRP, DHCP, STP, TACACS, CDP, HSRP. What does VRRP stand for - THE CORRECT ANSWER IS Virtual Router Redundancy Protocol What does CDP stand for? - THE CORRECT ANSWER IS Cisco Discovery Protocol What does TACACS stand for? - Terminal Access Control of Authentication and Control Systems - Terminal Access Controller Access Control System - Television Availability Control And Communication Standard - Teletype Authentication and Control of All Control Systems - THE CORRECT ANSWER IS Terminal access controller access control system SMTP 3 built in commands - THE CORRECT ANSWER IS VRFY EXPN RCPT TO What encryption cipher does WEP use - THE CORRECT ANSWER IS RC4 What does TKIP stand for and what does it do. - THE CORRECT ANSWER IS Temporal Key Integrity Protocol, What does EAP, LEAP, PEAP stand for - THE CORRECT ANSWER IS Extensible, lightweight, protected What is the type 5 secret for Cisco - THE CORRECT ANSWER IS MD5 What is the port for Netbios - THE CORRECT ANSWER IS 137/UDP SMB over TCP / CIFS port - THE CORRECT ANSWER IS tcp port 445 RDP port - THE CORRECT ANSWER IS TCP 3389 What can net view be used for - THE CORRECT ANSWER IS net view /domain - Lists domains net view /domain:example - lists hosts inside the domain 'example' net view command to list cache - THE CORRECT ANSWER IS net view ComputerName /CACHE net view how to list domains - THE CORRECT ANSWER IS net view /domain net view /domain:example Name two tools for netbios enumeration - THE CORRECT ANSWER IS nbstat nbtscan NetBios codes - THE CORRECT ANSWER IS Domain name ~ 00 G Domain master browser ~ 1B U Domain controller ~ 1C G Server ~ 29 U Workstation ~ 00 U Tools for enumerating domain controllers - THE CORRECT ANSWER IS nbtscan, nbenum nbtstat command - THE CORRECT ANSWER IS nbtstat -A Where is active directory stored in - THE CORRECT ANSWER IS %systemroot%NTDS.dit What does FSMO stand for ? - THE CORRECT ANSWER IS flexible single master operations How many FSMO roles are there? - THE CORRECT ANSWER IS There are 5 roles, Forest Wide Roles: Schema Master Domain Naming Domain Wide Roles: Relative ID Master (RID) PDC Emulator Infrastructure Master What does the master browser do in active directory - THE CORRECT ANSWER IS Used to collect the information to create / maintain the browse list within an AD forest LDAP port to query global catalogue - THE CORRECT ANSWER IS GC clients can use LDAP to query AD over TCP/3268. What is the Global Catalogue - THE CORRECT ANSWER IS It provides a searchable catalog of all objects in every domain in a multi-domain Active Directory Domain Services. What is the master browser - THE CORRECT ANSWER IS The Domain Master browser is necessary in a routed TCP/IP network, that is, when a Windows domain spans more than one TCP/IP network. SAM files locations - THE CORRECT ANSWER IS HKEY_ LOCAL_MACHINESAM. C:WindowsSystem32Config. How many bytes are there in LAN-MAN - THE CORRECT ANSWER IS 16 bytes long What is the max character limit on LAN-MAN password - THE CORRECT ANSWER IS 14 characters What encryption was used for LAN-MAN - THE CORRECT ANSWER IS DES What is the following hash AAD3B435B51404EEAAD3B435B51404EE - THE CORRECT ANSWER IS LMman empty hash What tools can be used to crack the NThash (NTLM) - THE CORRECT ANSWER IS Responder When was NTLMv1 added to Windows - THE CORRECT ANSWER IS Windows NT 3.1 Does NTLMv1 use salt in its hash - THE CORRECT ANSWER IS No, because of this it is very vulnerable to rainbow table attacks. What hash algorithm is used by NTLMv1 - THE CORRECT ANSWER IS MD4 What is a rainbow table?
[Show More]