Data Systems > QUESTIONS & ANSWERS > SAP Midlevel Questions and Answers 100% Pass (All)
SAP Midlevel Questions and Answers 100% Pass
Document Content and Description Below
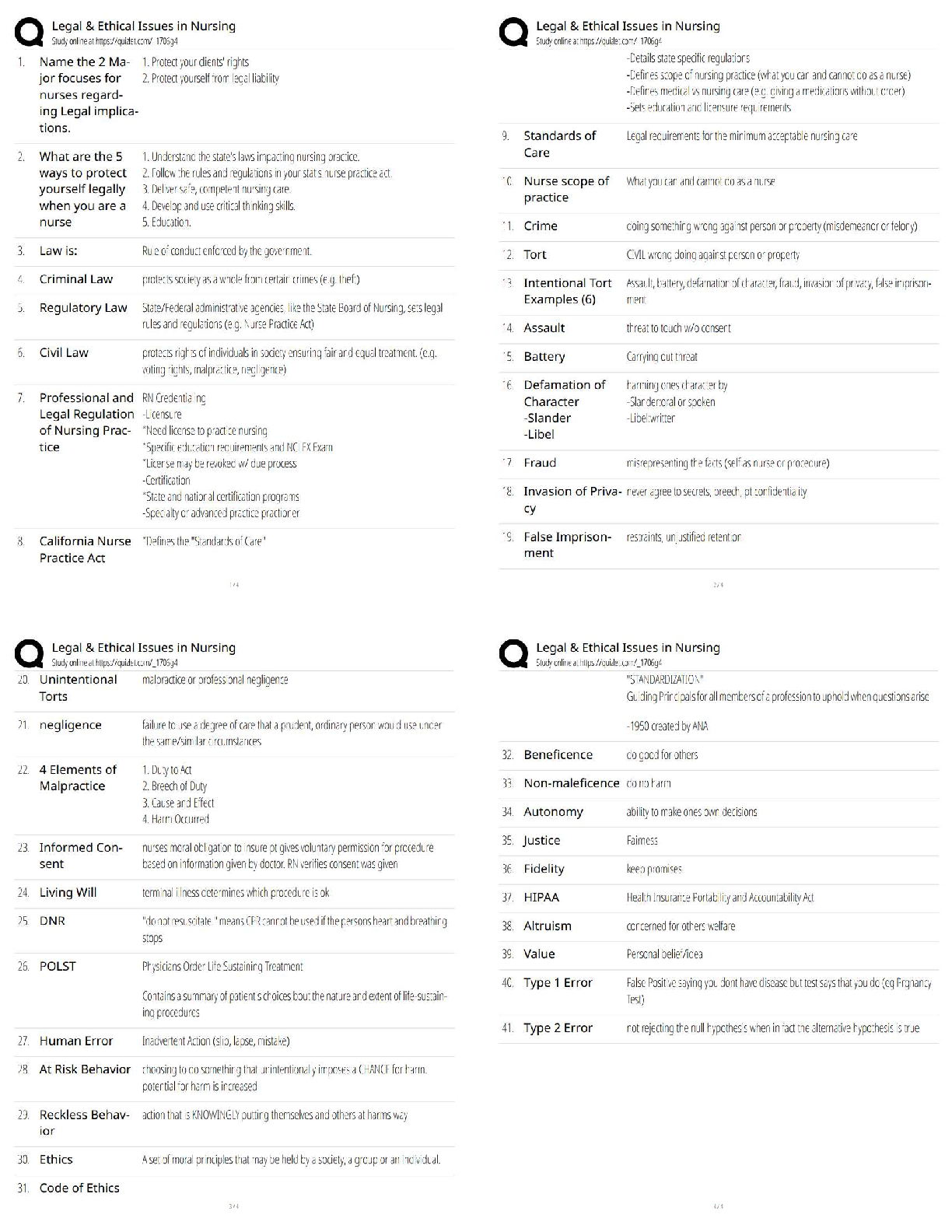
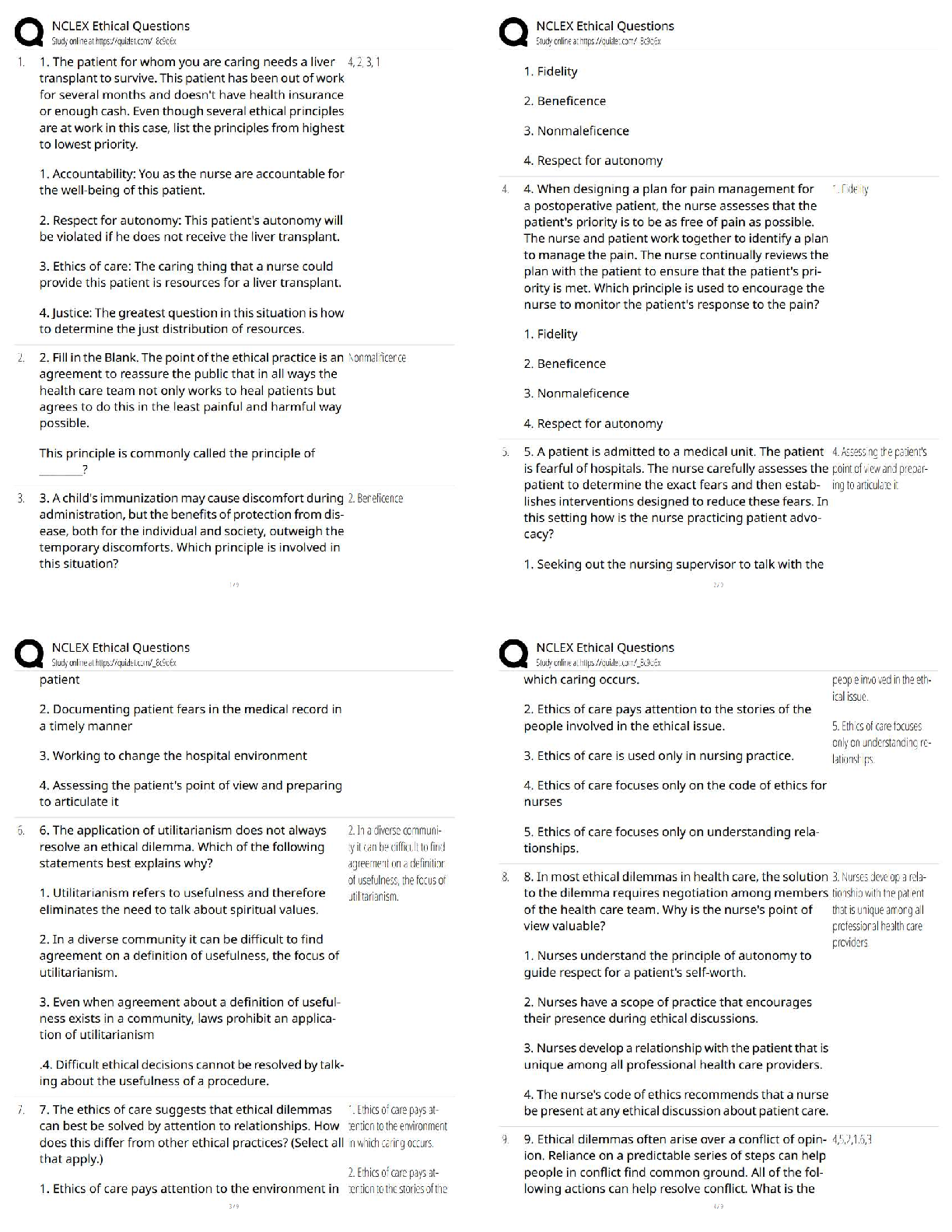
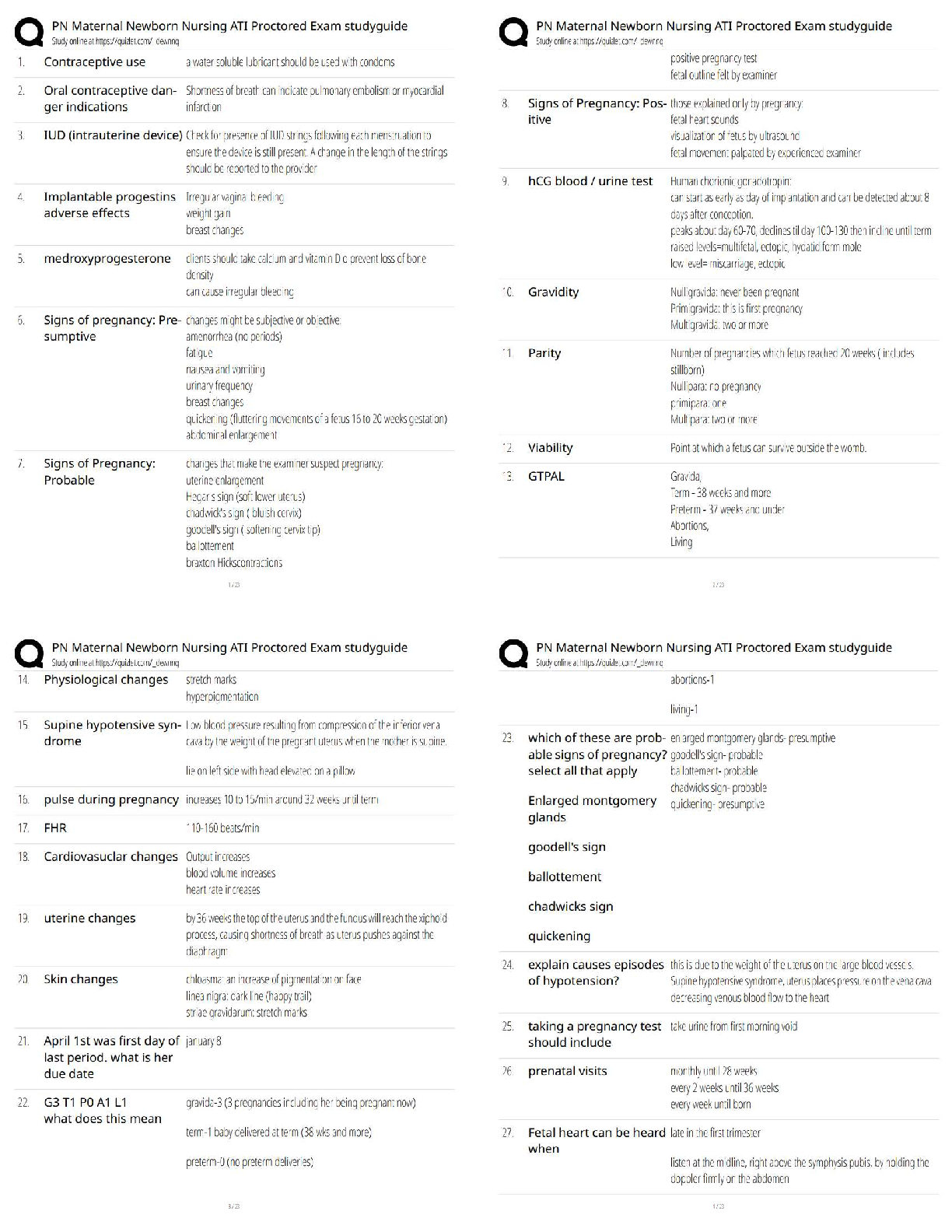
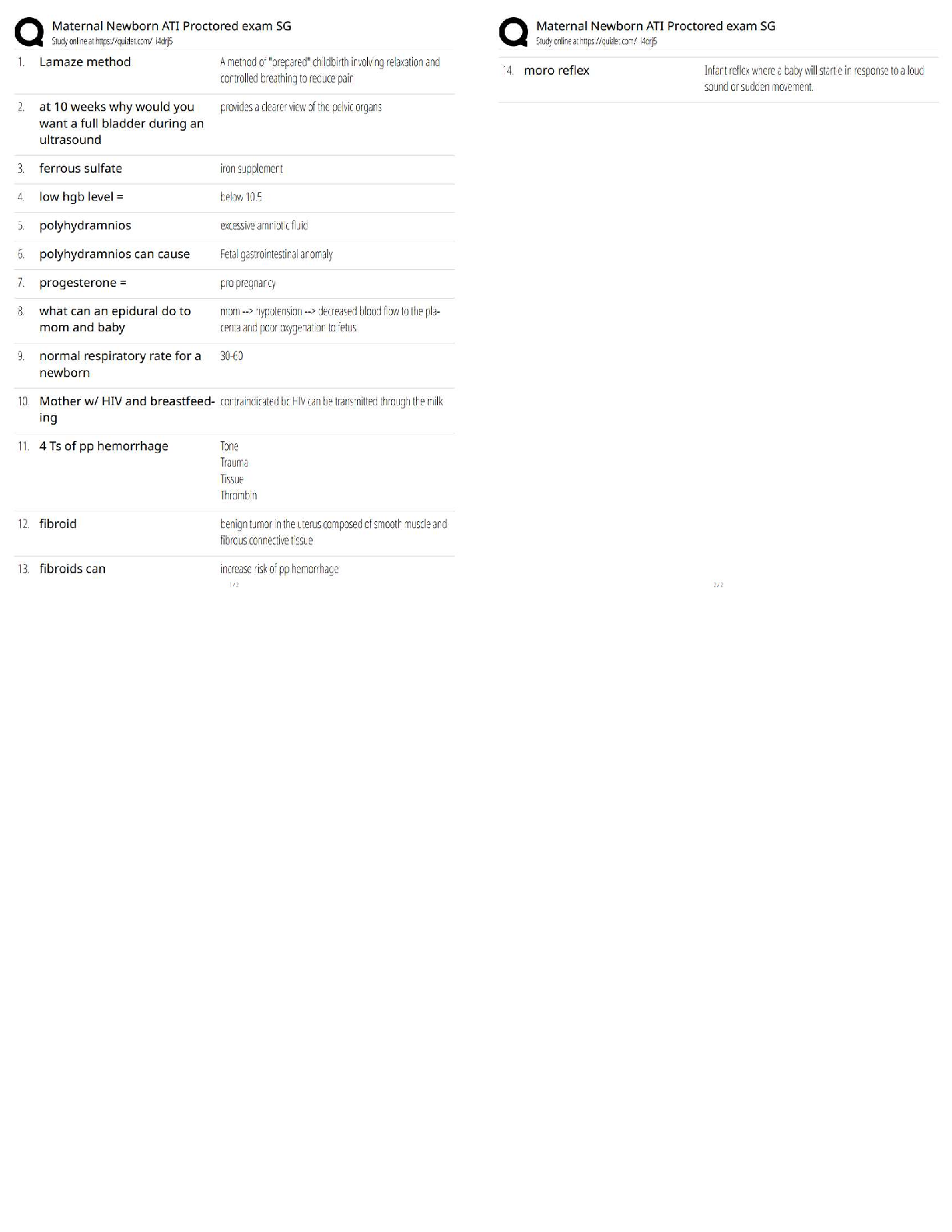
SAP Midlevel Questions and Answers 100% Pass This order prescribes a uniform system for classifying, safeguarding, and declassifying national security information, including information relating to ... defense against transnational terrorism. ✔✔Executive Order 13526 of December 29, 2009 Information may be originally classified under the terms of Executive Order 13526 of December 29, 2009 only if all of the following four (4) conditions are met: ✔✔(1) an original classification authority is classifying the information; (2) the information is owned by, produced by or for, or is under the control of the United States Government; (3) the information falls within one or more of the categories of information listed in section 1.4 of this order; and (4) the original classification authority determines that the unauthorized disclosure of the information reasonably could be expected to result in damage to the national security, which includes defense against transnational terrorism, and the original classification authority is able to identify or describe the damage. The unauthorized disclosure of which reasonably could be expected to cause exceptionally grave damage to the national security that the original classification authority is able to identify or describe. ✔✔Top Secret The unauthorized disclosure of which reasonably could be expected to cause serious damage to the national security that the original classification authority is able to identify or describe. ✔✔Secret The unauthorized disclosure of which reasonably could be expected to cause damage to the national security that the original classification authority is able to identify or describe. ✔✔Confidential Classification Authority: The authority to classify information originally may be exercised only by: ✔✔(1) the President and the Vice President; (2) agency heads and officials designated by the President; and (3) United States Government officials delegated this authority The Risk Management process provides a systematic approach to acquire and analyze the information necessary for protecting assets and allocating security resources. (True or False) ✔✔True An asset can be defined as anything that ______. (Select all that apply) [ ] Is of value [ ] Requires protection [ ] Has a weakness ✔✔Is of Value Requires Protection Persons, facilities, materials, information, and activities are categories of ______. [ ] Assets [ ] Threats [ ] Countermeasures [ ] Vulnerabilities ✔✔Assets An asset value should be assigned based on the perspective of the ____________. [ ] Asset Owner [ ] Program Manager [ ] Asset Manager [ ] Chief of Security ✔✔Asset Owner A car bombing resulting in massive loss of life is an example of a/an ______. [ ] Security weakness [ ] Threat category [ ] Undesirable event [ ] Vulnerability ✔✔Undesirable Event Impact is defined as the amount of loss or damage that can be expected from a successful asset attack or other undesirable event. (True or False) ✔✔True When determining the cost associated with a lo [Show More]
Last updated: 2 years ago
Preview 1 out of 67 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$11.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Feb 22, 2023
Number of pages
67
Written in
All
Additional information
This document has been written for:
Uploaded
Feb 22, 2023
Downloads
0
Views
131








.png)