Information Systems Management > QUESTIONS & ANSWERS > CISSP Exam Review. 100% Mastery of concepts. Approved. (All)
CISSP Exam Review. 100% Mastery of concepts. Approved.
Document Content and Description Below
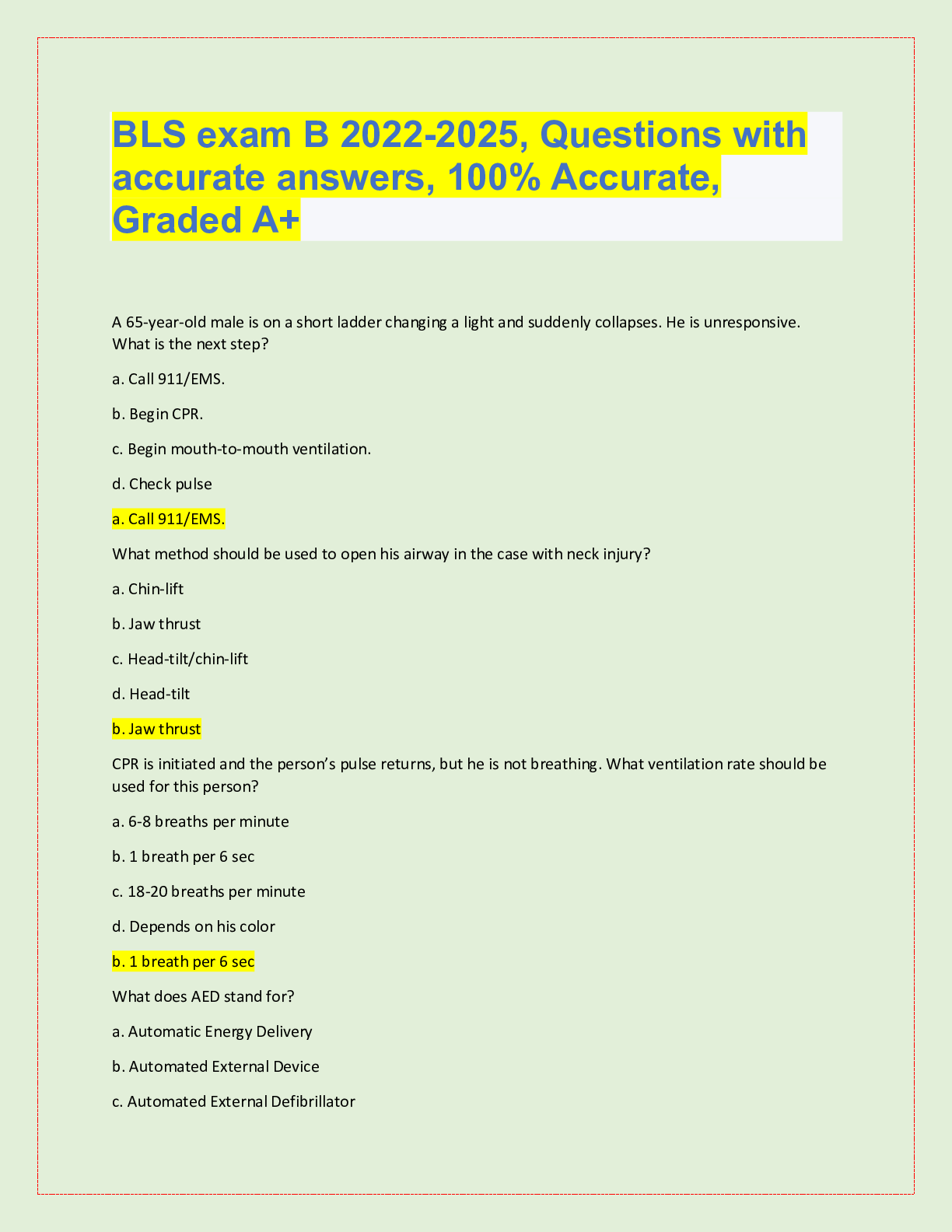
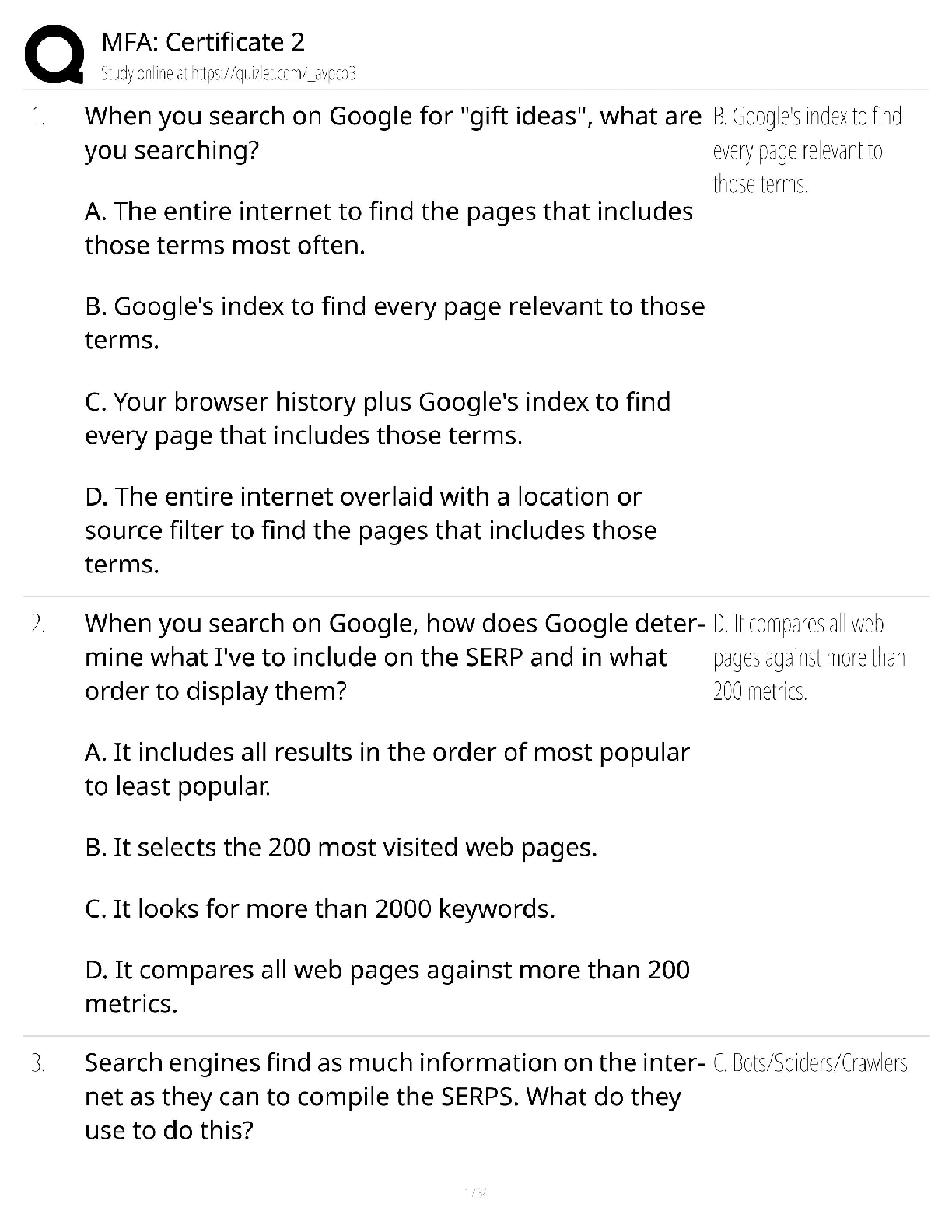
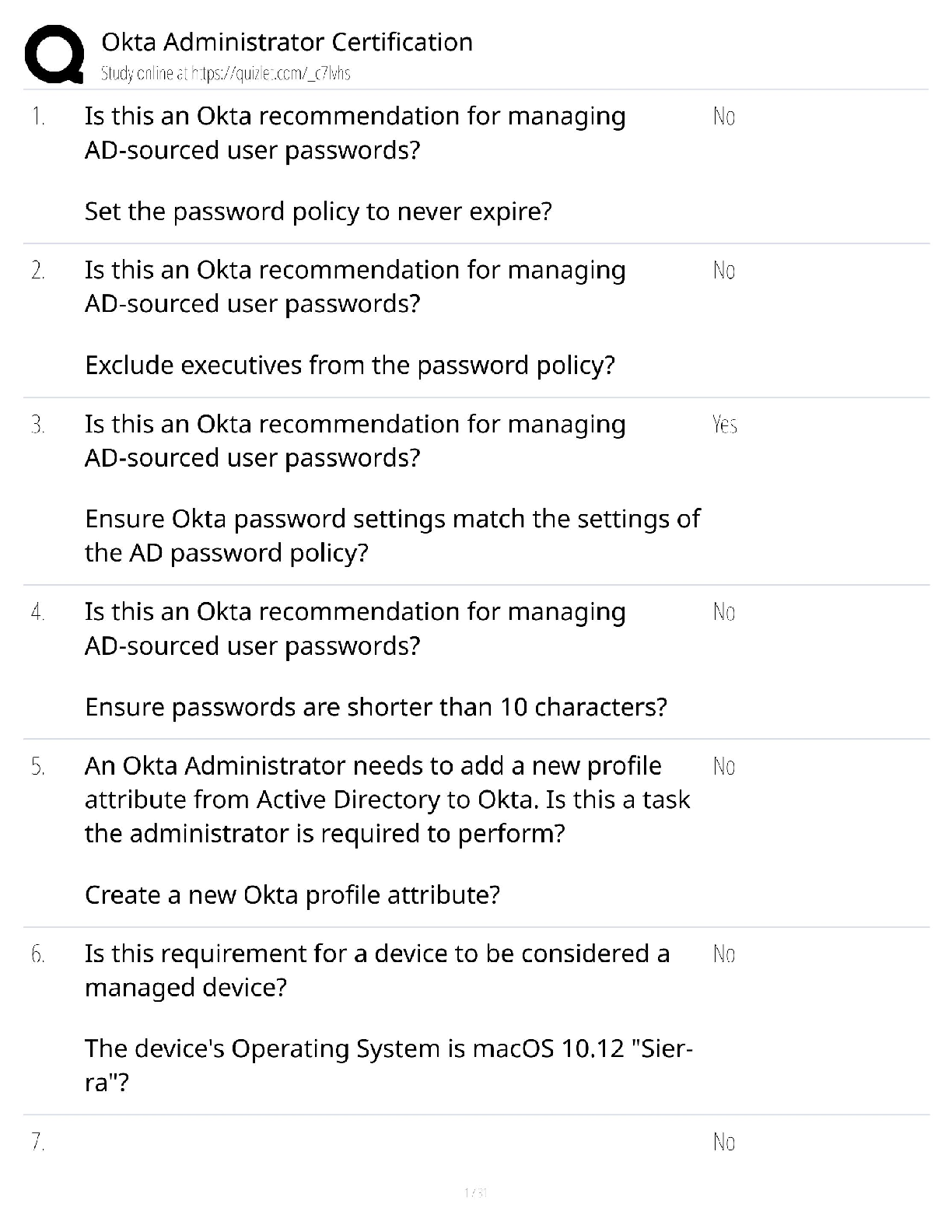
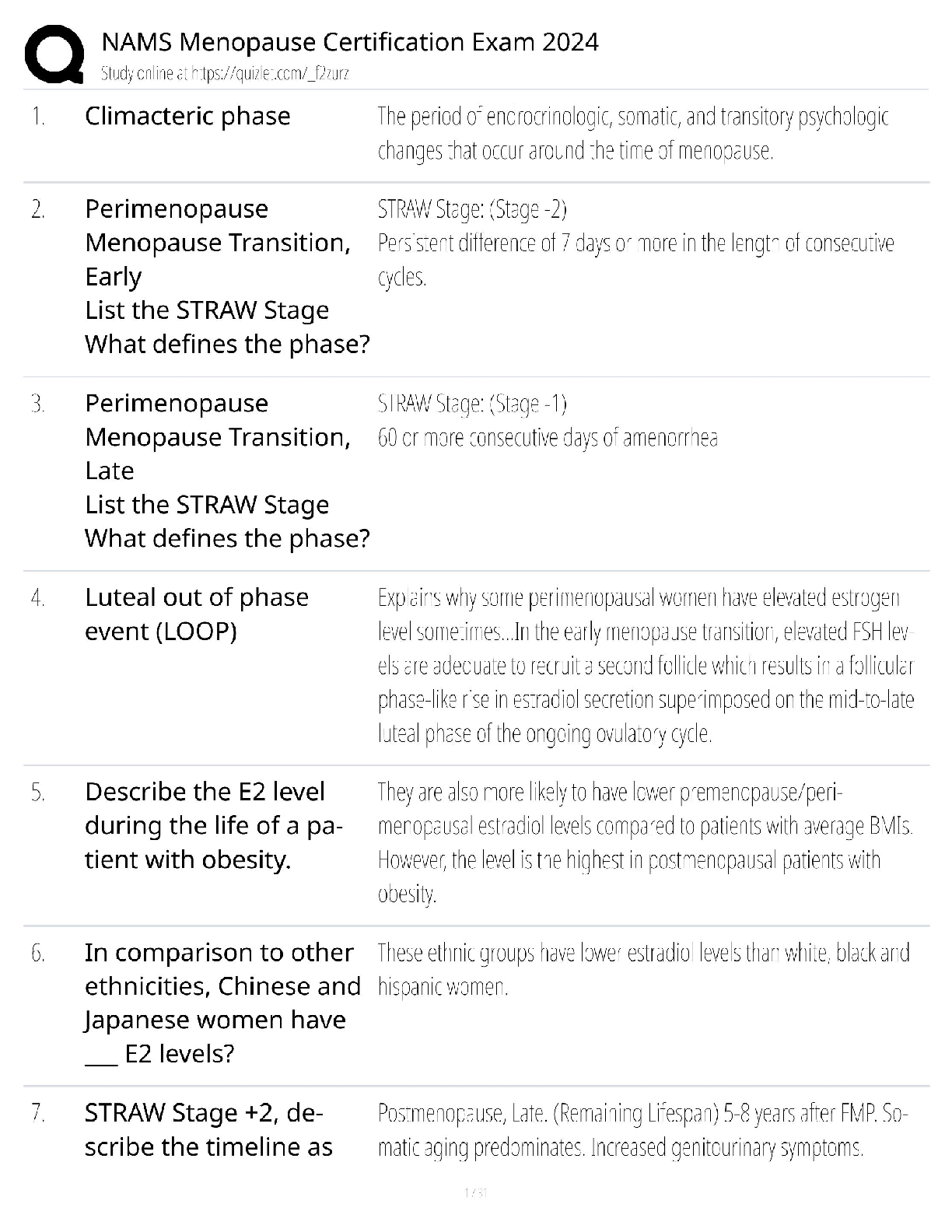
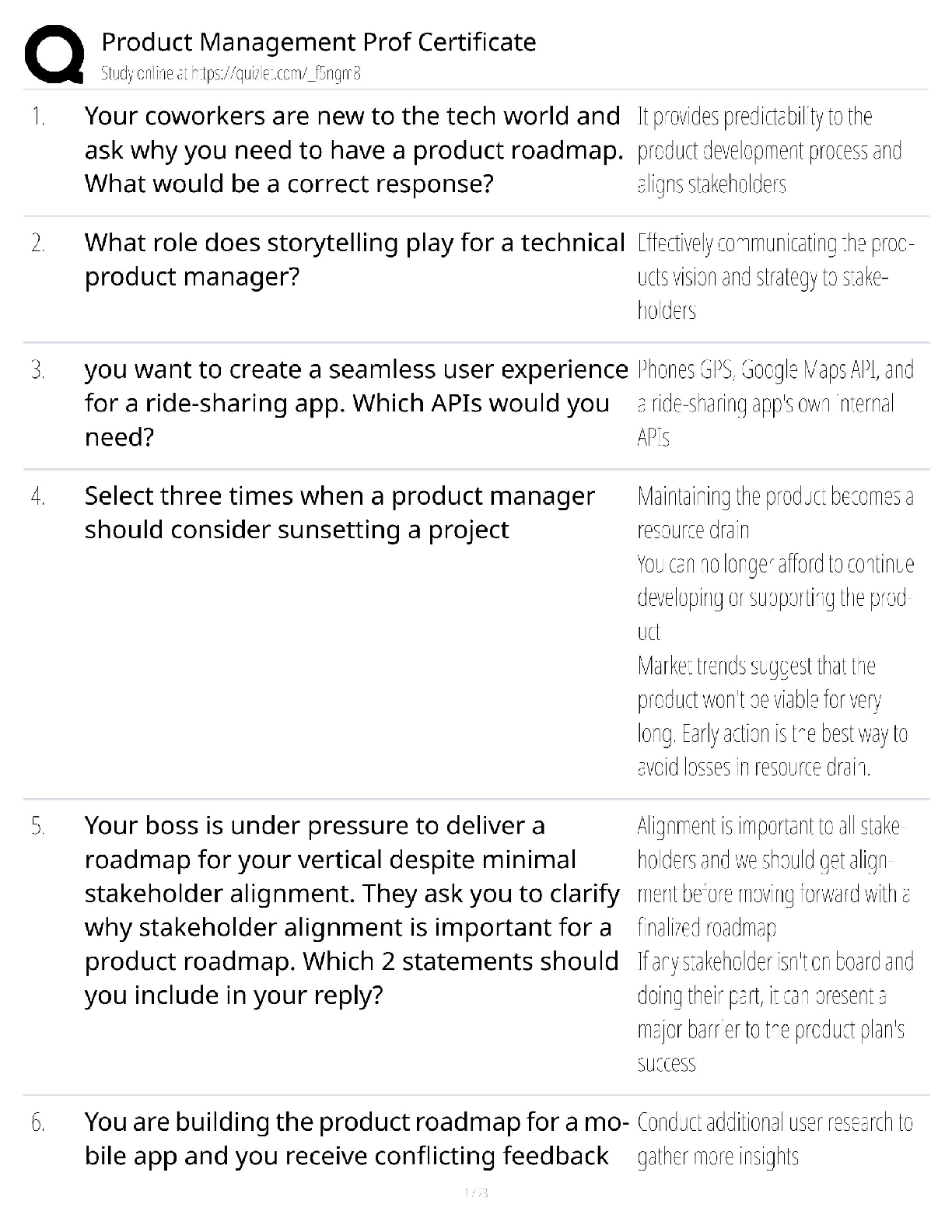
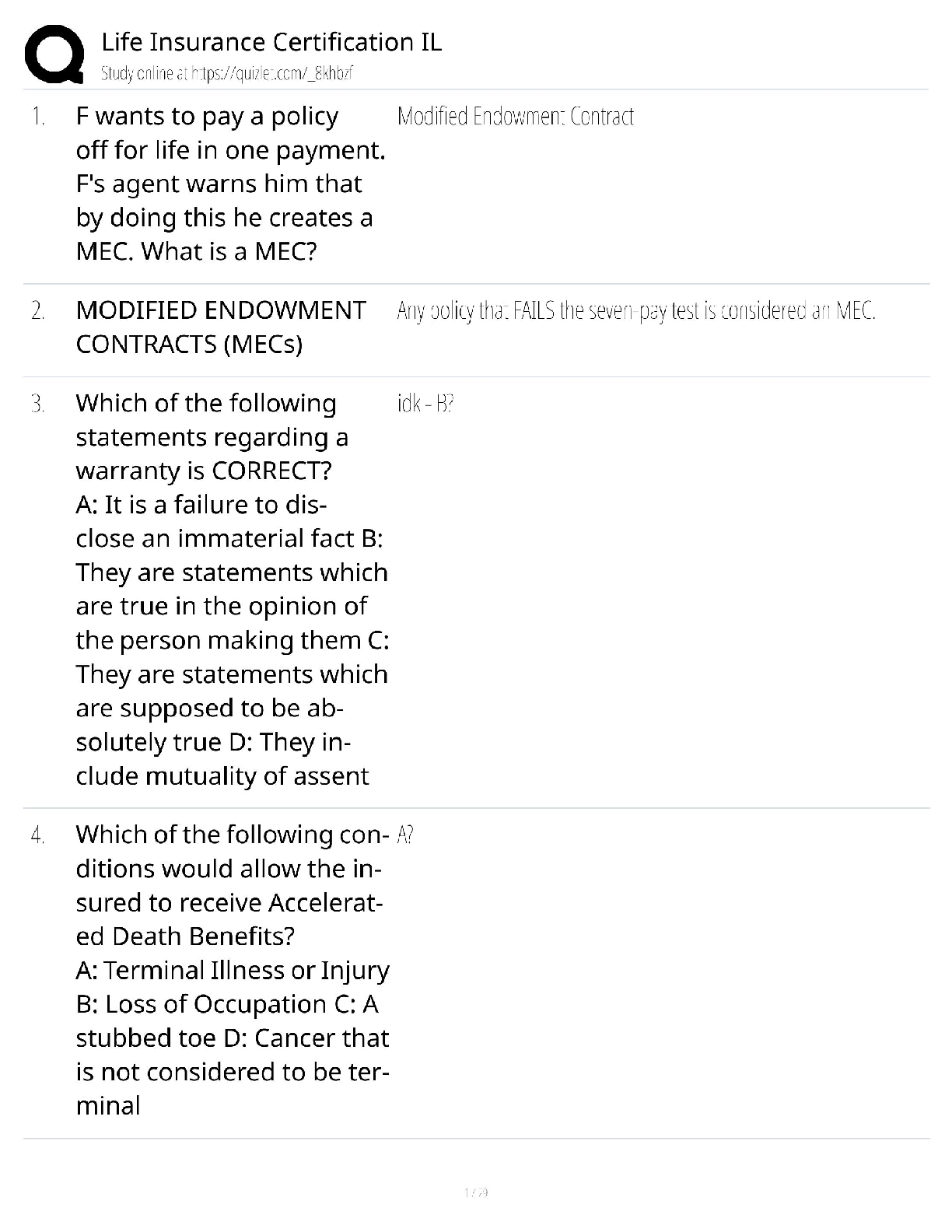
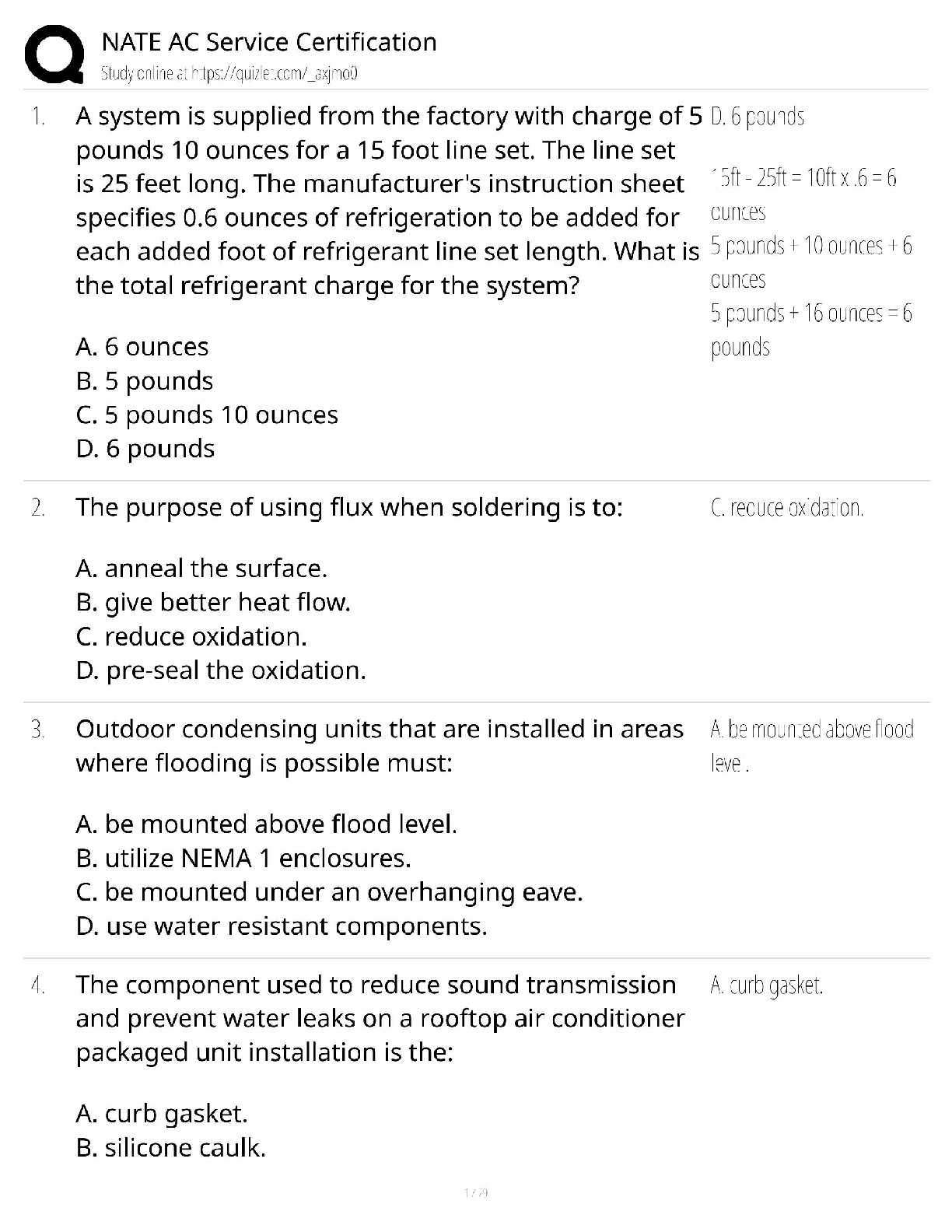
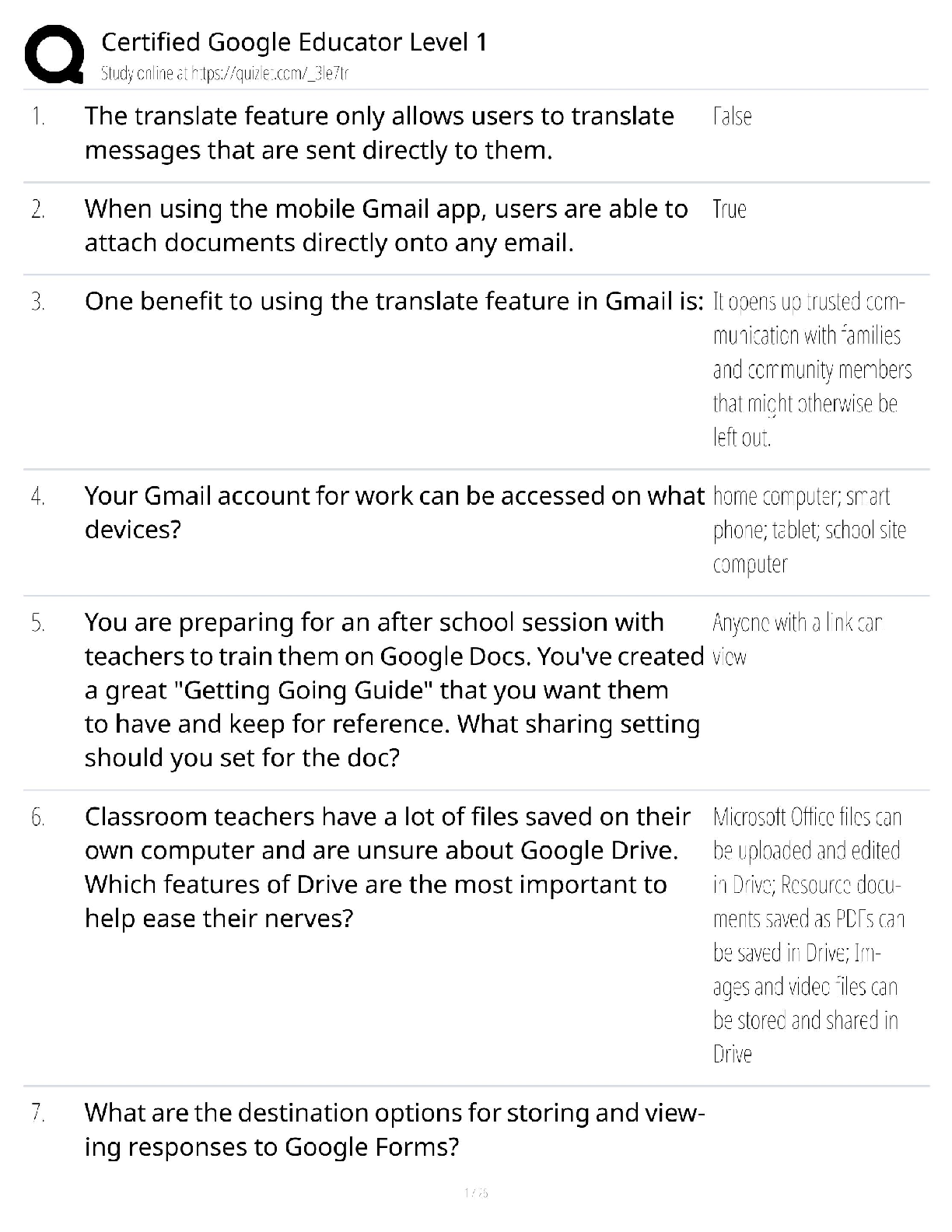
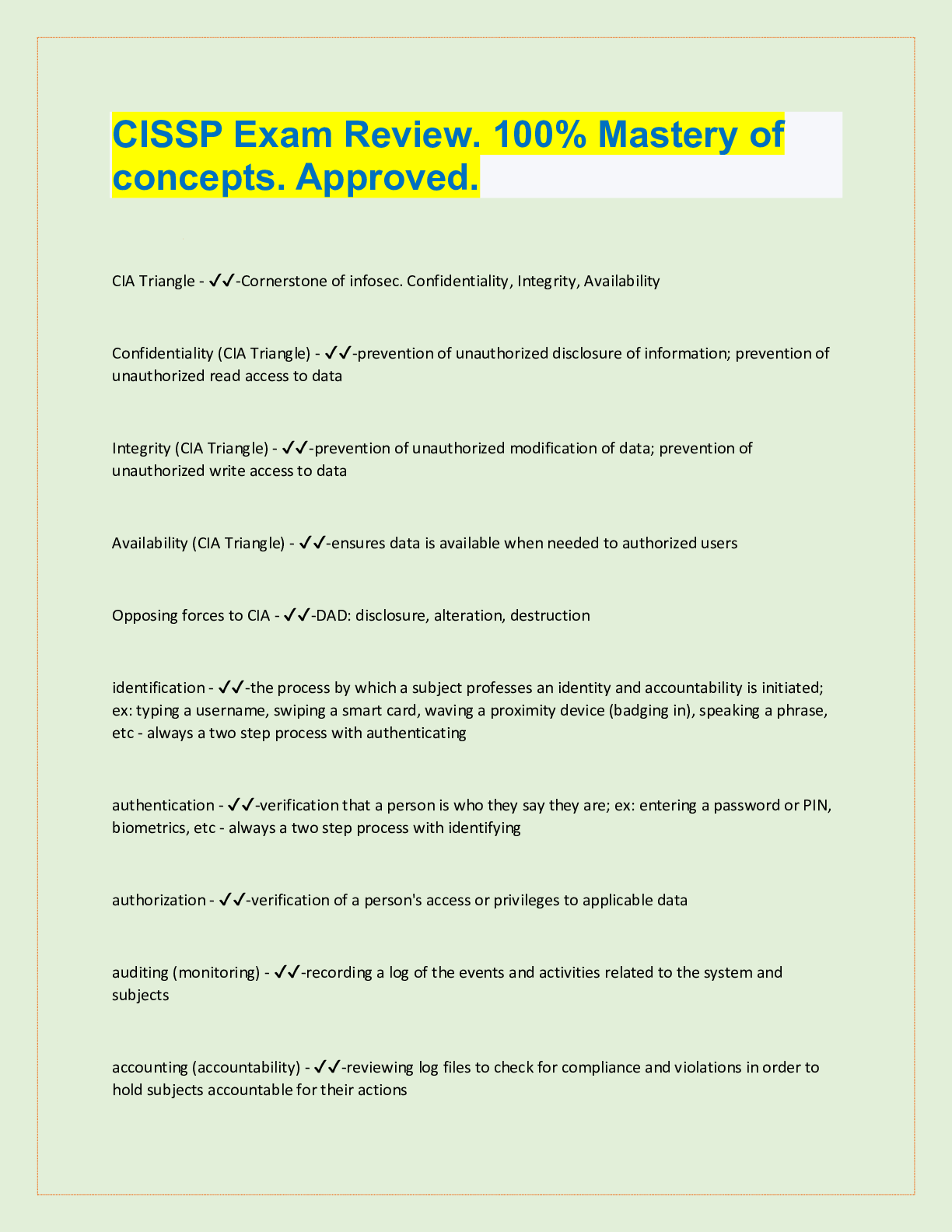
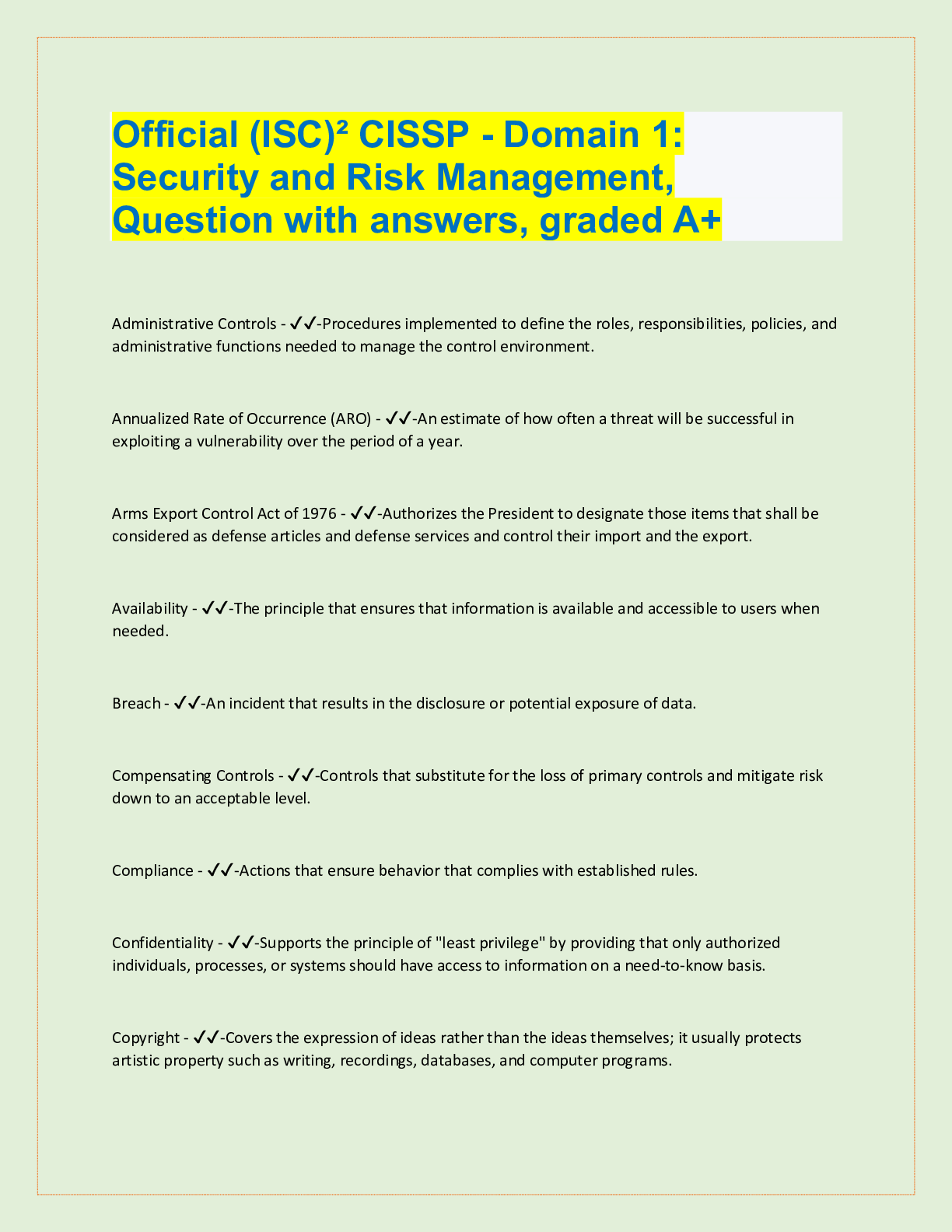
CISSP Exam Review. 100% Mastery of concepts. Approved. CIA Triangle - ✔✔-Cornerstone of infosec. Confidentiality, Integrity, Availability Confidentiality (CIA Triangle) - ✔✔-prevention of ... unauthorized disclosure of information; prevention of unauthorized read access to data Integrity (CIA Triangle) - ✔✔-prevention of unauthorized modification of data; prevention of unauthorized write access to data Availability (CIA Triangle) - ✔✔-ensures data is available when needed to authorized users Opposing forces to CIA - ✔✔-DAD: disclosure, alteration, destruction identification - ✔✔-the process by which a subject professes an identity and accountability is initiated; ex: typing a username, swiping a smart card, waving a proximity device (badging in), speaking a phrase, etc - always a two step process with authenticating authentication - ✔✔-verification that a person is who they say they are; ex: entering a password or PIN, biometrics, etc - always a two step process with identifying authorization - ✔✔-verification of a person's access or privileges to applicable data auditing (monitoring) - ✔✔-recording a log of the events and activities related to the system and subjects accounting (accountability) - ✔✔-reviewing log files to check for compliance and violations in order to hold subjects accountable for their actions non-repudiation - ✔✔-a user cannot deny having performed a specific action subject - ✔✔-an entity that performs active functions to a system; usually a person, but can also be script or program designed to perform actions on data object - ✔✔-any passive data within the system ISC2 Code of Ethics Canons (4) - ✔✔-1. protect society, commonwealth, infrastructure 2. act honorably, justly, responsibly, legally 3. provide diligent and competent service 4. advance and protect the profession strictly applied in order; exam questions in which multiple canons could be the answer, choose the highest priority per this order policy - ✔✔-mandatory high level management directives; components of policy 1. purpose: describes the need for policy 2. scope: what systems, people, facilities, organizations are covered 3. responsibilities: specific duties of involved parties 4. compliance: effectiveness of policy, violations of policy procedure - ✔✔-low level step by step guide for accomplishing a task standard - ✔✔-describes the specific use of technology applied to hardware or software; mandatory guideline - ✔✔-discretionary recommendations (e.g. not mandatory) baseline - ✔✔-a uniform way of implementing a standard 3 access/security control categories - ✔✔-1. administrative: implemented by creating org policy, procedure, regulation. user awareness/training also fall here 2. technical: implemented using hardware, software, firmware that restricts logical access to a system 3. physical: locks, fences, walls, etc preventive access control (can be administrative, technical, physical) - ✔✔-prevents actions from occurring by applying restrictions on what a user can do. example: privilege level detective access control (can be administrative, technical, physical) - ✔✔-controls that alert during or after a successful attack; alarm systems, or closed circuit tv corrective access control (can be administrative, technical, physical) - ✔✔-repairing a damaged system; often works hand in hand with detective controls (e.g. antivirus software) recovery access control (can be administrative, technical, physical) - ✔✔-controls to restore a system after an incident has occurred; deterrent access control (can be administrative, technical, physical) - ✔✔-deters users from performing actions on a system compensating access control (can be administrative, technical, physical) - ✔✔-additional control used to compensate for weaknesses in other controls as needed risk formula - ✔✔-risk = threat x vulnerability x impact market approach (for calculating intangible assets) - ✔✔-assumes the fair value of an asset reflects the price which comparable assets have been purchased in transactions under similar circumstances income approach (for calculating intangible assets) - ✔✔-the value of an asset is the present value of the future earning capacity that an asset will generate over the rest of its lifecycle cost approach (for calculating intangible assets) - ✔✔-estimates the fair value based on cost of replacement exposure factor (EF) - ✔✔-percentage of value the asset lost due to incident single loss expectancy (SLE) - ✔✔-asset value (AV) times exposure factor AV x EF = SLE expressed in a dollar value annual rate of occurrence (ARO) - ✔✔-number of losses suffered per year annualized loss expectancy (ALE) - ✔✔-yearly cost due to risk SLE x ARO = ALE legally defensible security - ✔✔-to obtain legal restitution a company must demonstrate a crime was committed, suspect committed that crime, and took reasonable efforts to prevent the crime files are accurate, policy in place, proper authentication, compliance with laws and regulation layering (defense in depth) - ✔✔-the use of multiple controls in a series (one after another, linearly); no one control can protect against all possible threats; top down approach - ✔✔-senior management responsible for initiating and defining policies; middle management fleshes out policy into standards, baselines, guidelines, and procedures; end users must comply with all policies strategic plan - ✔✔-long term plan that is fairly stable; defines the org's security purpose; useful to forecast about 5 years and serves as a planning horizon - long term goals and vision (high level) tactical plan - ✔✔-midterm plan developed to provide more details on accomplishing goals set forth in the strat plan; generally useful for a year; more granular than strat plan operational plan - ✔✔-short term, highly detailed plan based on strat and tactical plans; valid only for a short time; very low level and granular; provides direction for many areas and issues change management - ✔✔-ensure that any change does not lead to reduced or compromised security; also responsible for roll backs; make all changes subject to detailed documentation and auditing data classification - ✔✔-process of organizing items, objects, subjects, into groups, categories, or collections with similarities; formalize and stratify the process of securing data based on assigned labels of importance and sensitivity government/military classification - ✔✔-TS > Sec > Confidential > sensitive > unclassified commercial/private section classifications - ✔✔-confidential/private > sensitive > public senior manager role - ✔✔-person who is ultimately responsible for the security and protection of an orgs assets; signs off on all activities and policy; overall success and failure rests on this role data owner - ✔✔-responsible for classifying information for placement and protection within policy/solutions; often delegates actual management of the data to a custodian data custodian - ✔✔-responsible for implementing the prescribed protection defined by the security policy and senior management; responsible for the day to day tasks of maintaining the data/system COBIT 5 (control framwork) Control Objectives for Information and Related Technology - ✔✔-principles for governance and management of enterprise IT 1. meeting stakeholder needs 2. covering the enterprise end to end 3. applying a single framework 4. enabling a holistic approach 5. separating governance from management regulatory policy - ✔✔-required whenever industry or legal standards are applicable to your organization (NERC CIP, FISMA) advisory policy - ✔✔-discusses behaviors and activities that are acceptable and defines consequences of violations (most fall into this category) informative policy - ✔✔-provides information about a specific subject; ex: company goals, mission statements STRIDE threat categorization - ✔✔-Spoofing, tampering, repudiation, information disclosure, denial of service, elevation of privilege spoofing - ✔✔-goal of gaining access to a target system through the use of a falsified identity; can be used against IP addresses, MAC address, user names, system names, SSIDs, email addresses, etc tampering - ✔✔-any action resulting in the unauthorized changes or manipulation of data repudiation - ✔✔-the ability of a user or attacker to deny having performed a specific action or activity (plausible deniability) information disclosure - ✔✔-distribution of private, confidential, or controlled information to external or unauthorized entities denial of service (DoS) - ✔✔-attempts to prevent authorized use of a resource. can be accomplished through flaw exploitation, connection overloading, or traffic flood [Show More]
Last updated: 2 years ago
Preview 1 out of 31 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)
CISSP test BUNDLE, QUESTIONS AND ANSWERS, VERIFIED.
CISSP test bank - Exam questions to study/review 1. Top questions with accurate answers, 100% Accurate. VERIFIED.
By Topmark 2 years ago
$36
14
Reviews( 0 )
$12.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Mar 14, 2023
Number of pages
31
Written in
All
Additional information
This document has been written for:
Uploaded
Mar 14, 2023
Downloads
0
Views
81