DIT CERTIFICATION TEST PRACTICE,
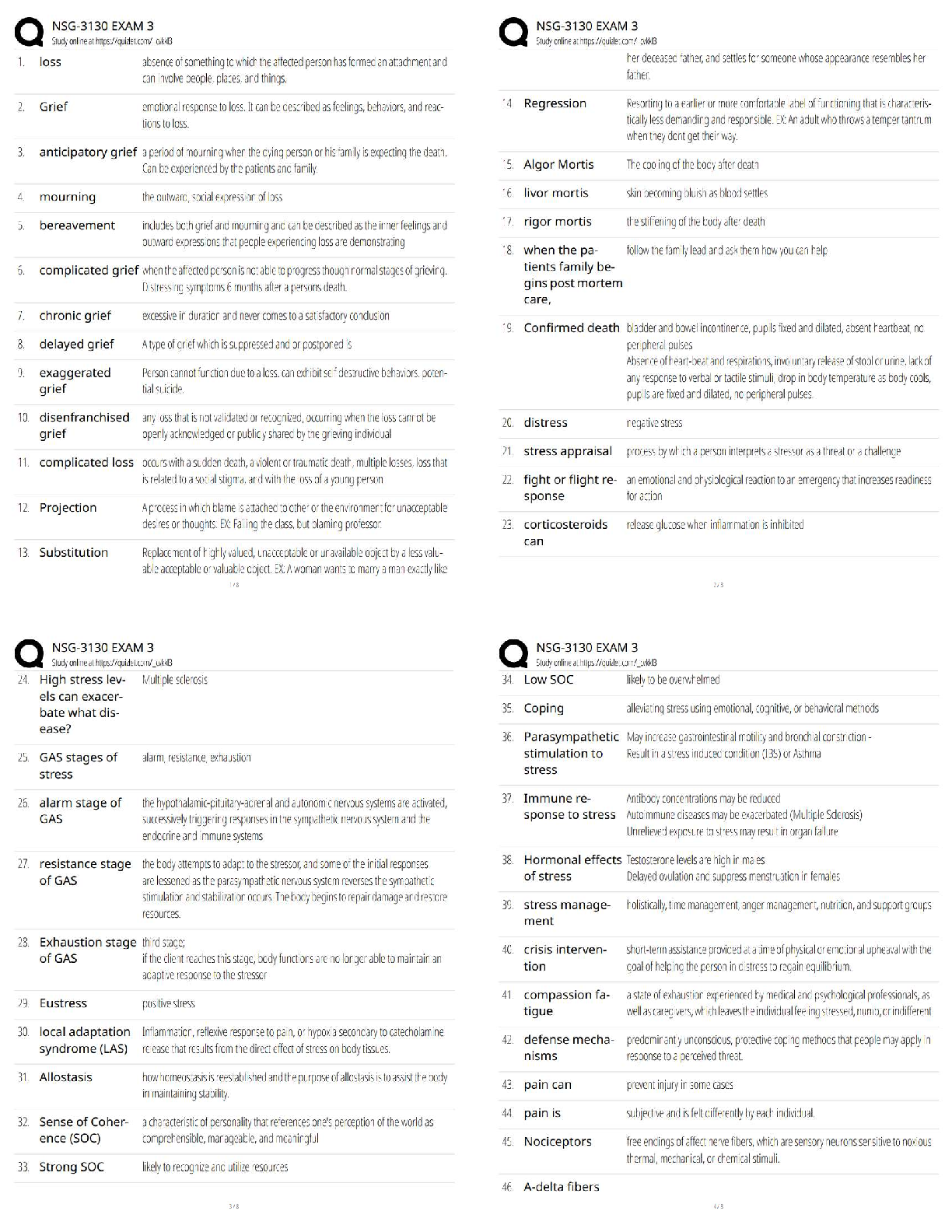
Questions and answers, 100% Accurate,
Graded A+
What is cloud computing? - ✔✔-the practice of using a network of remote servers hosted on the
Internet to store, manage, and process
...
DIT CERTIFICATION TEST PRACTICE,
Questions and answers, 100% Accurate,
Graded A+
What is cloud computing? - ✔✔-the practice of using a network of remote servers hosted on the
Internet to store, manage, and process data, rather than a local server or a personal computer.
What is ontology? - ✔✔-The study of how a particular knowledge domain, or system, is organized. An
ontology is the product of an ontological study.
what is the job of a network engineer? - ✔✔-To focus on the design, implementation, delivery and
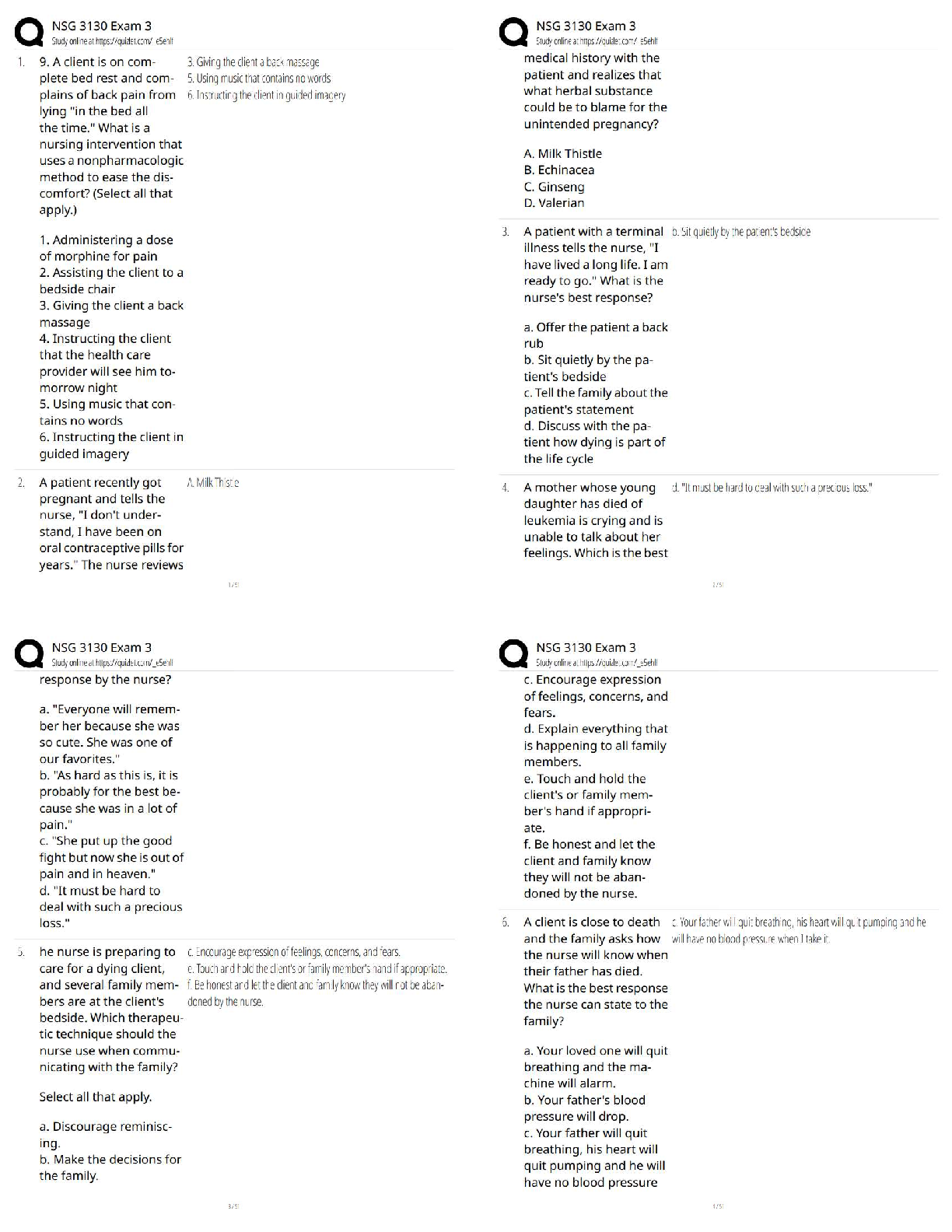
support of network components, policies and procedures used by an organization. Network engineers
are responsible for configuring and testing network devices, and setting up and maintaining the network
infrastructure.
What is MTA? - ✔✔-A messaging component that routes, delivers and receives e-mail.
Whats is a MDA (Mail Delivery Agent)? - ✔✔-An e-mail server program that receives sent messages and
delivers them to their proper destination mailbox.
What does POP3 servers do? - ✔✔-POP3 servers receive and hold incoming e-mail messages in the
appropriate mailbox on the server until users log on (authenticate themselves with a user name and
password) and download their mail. Once messages are downloaded, they are removed from the server
what do IMAP servers do? - ✔✔-IMAP server receives and holds your messages. When you log on with
your user name and password, you can read a message on the server, or you can view just the heading
and the sender of the message and decide whether to download it.
what is a mail client also refered to as? - ✔✔-MAIL USER AGENT
Because file attachments may contain malicious code that can be used to damage or infiltrate systems,
your company routinely scans all file attachments in incoming e-mail. Where does attachment scanning
take place? - ✔✔-At the server, usually just after the message has been received via SMTP
A domain name consists of letters (and sometimes numbers) separated by periods. Which of the
following is the host name component of a domain name? - ✔✔-The left-side component of the domain
name, which categorizes domains into groups by server name
Which of the following is a Web-based seminar or training session that is typically interactive, enabling
participants to communicate with the presenter and with each other via online chat? - ✔✔-Web
conference
Kim is using the YouTube graphics-editing application that she accesses via the Internet through her
browser. Kim does not own the application, nor can she download it. She is able to use the application
any time she needs to edit graphics. Although she does not have to pay for the access, she does notice
advertisements, which appear on the sidebar of the application's interface. The application Kim is using
may be classified as which of the following? - ✔✔-Software as a Service (SaaS)
Cloud computing is a computing paradigm in which? - ✔✔-users are able to access software and services
run by servers that reside on the Internet.
Cloud computing is software services that are provided over the Internet. Which of the following IT job
roles should be most familiar with cloud computing software, infrastructure and platform services? -
✔✔-Server administrator
What is restricted from downloading to the user's system when you configure browser security levels? -
✔✔-active content
Which of the following is true regarding smartphones and PIM applications? - ✔✔-Smartphone PIM
applications are designed to work in tandem with traditional desktop or laptop computers.
What could be a disadvantage for you to choose open-source, and thus a compelling enough reason to
purchase the licensed software instead of using the open-source solution? - ✔✔-Maintenance of an
open-source solution relies on developers who volunteer to work on the code.
What term is used to describe a software application that is secretly placed on a user's system to gather
information and relay it to outside parties, usually for advertising purposes? - ✔✔-Spyware
How many mail servers does the use of e-mail involve? - ✔✔-Two -- incoming mail is handled by one
server using Post Office Protocol (POP) or Internet Message Access Protocol (IMAP), and outgoing mail is
handled by another server using Simple Mail Transfer Protocol (SMTP).
How does a LAN differ from a WAN? - ✔✔-A LAN spans a confined geographic area, whereas a WAN
consists of multiple LANs.
When you sign in to your instant messaging (IM) service, your online status is advertised (or published)
to the people on your contacts list. What does this scenario represent? - ✔✔-Presencing
Non-repudiation is the security principle of providing proof that a transaction occurred between
identified parties. Which of the following can you use to enforce non-repudiation in an electronic data
transfer? - ✔✔-Digital signiture
Which technology can companies use to maximize processing power while protecting privacy and
sensitive materials? - ✔✔-Peer-to-peer networks on the Internet (P2P)
Intranets and extranets can both be considered subsets of the Internet. Which statement best describes
the difference between intranets and extranets? - ✔✔-Intranets are used within corporations by
employees, whereas extranets are used by corporations for non-public customer support.
Pretty Good Privacy (PGP) and Gnu Privacy Guard (GPG) are both used to encrypt? - ✔✔-e-mail
messages and their attachments
In contrast to meetings that take place in person, a Webcast offers the advantage of? - ✔✔-being
available for retransmission any time after the original event has taken place.
What is the function of a CAPTCHA? - ✔✔-To differentiate humans from automated senders during
online transactions
What are applets - ✔✔-Applets are small programs that can be embedded within web pages to perform
some specific functionality, such as computations, animations, and information processing. Applets are
written using the Java languag
[Show More]