Computer Networking > Summary > Summary Cyber Awareness 2022-2023 Knowledge Check (95 Answered questions_ all correct) (All)
Summary Cyber Awareness 2022-2023 Knowledge Check (95 Answered questions_ all correct)
Document Content and Description Below
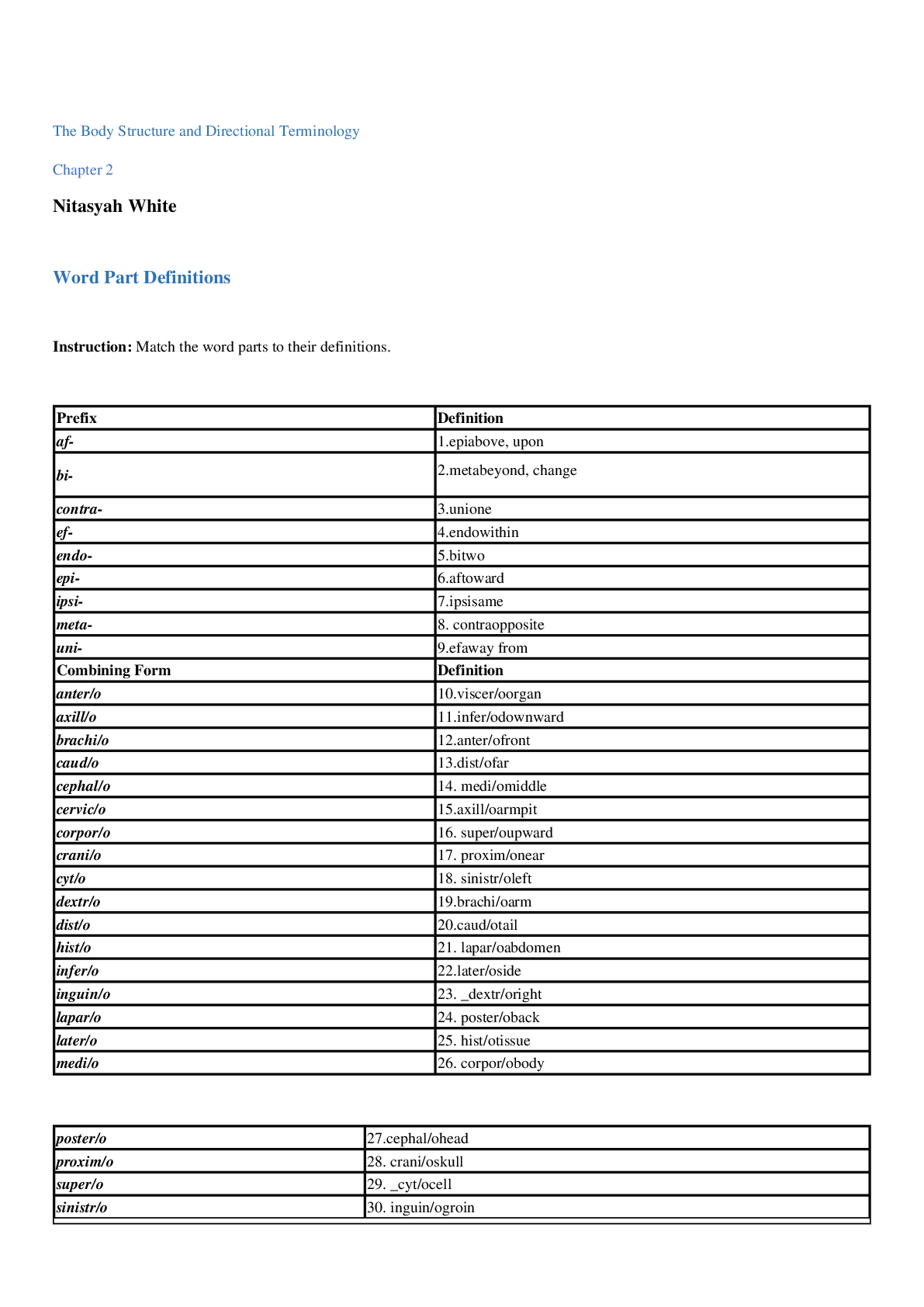
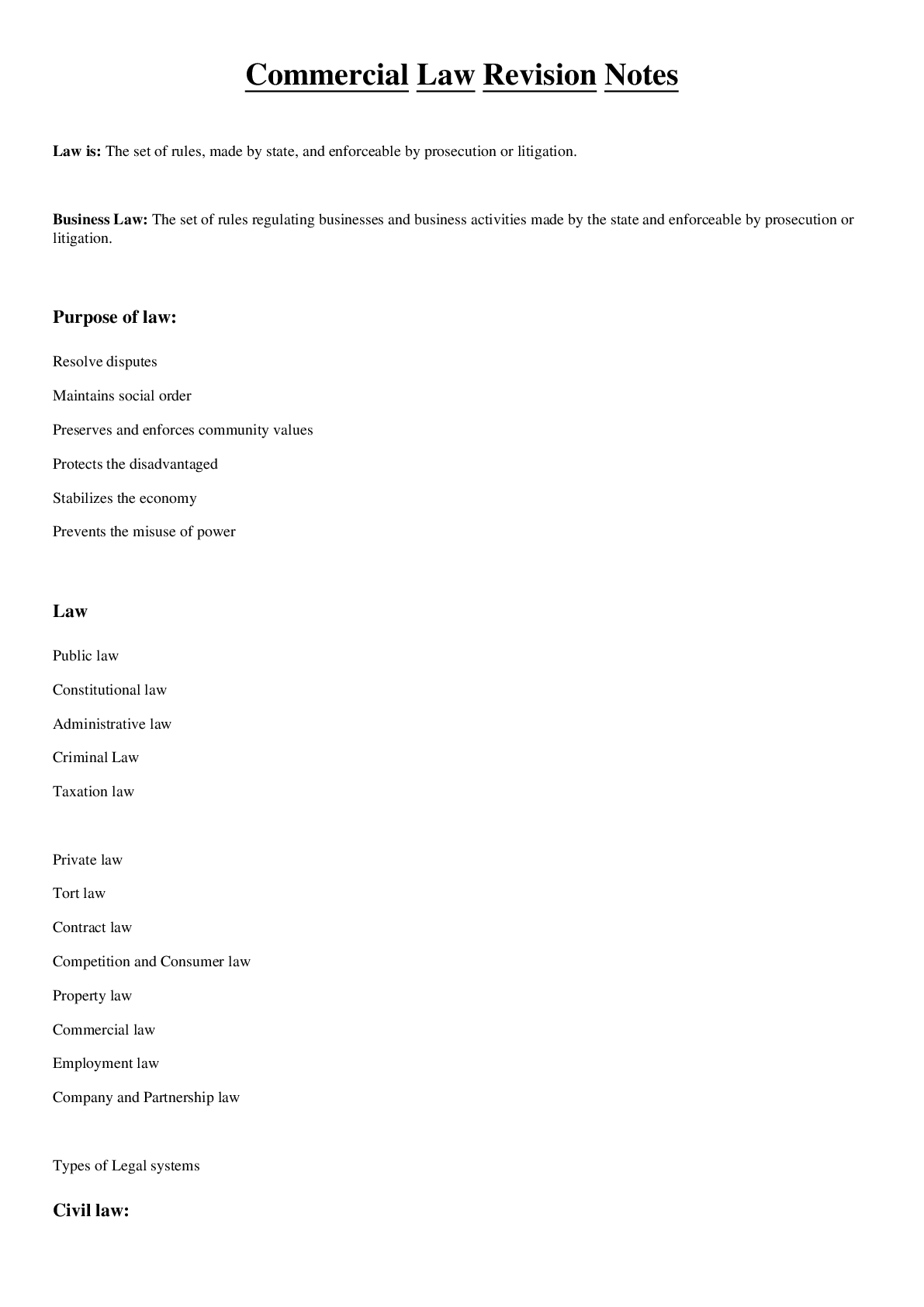
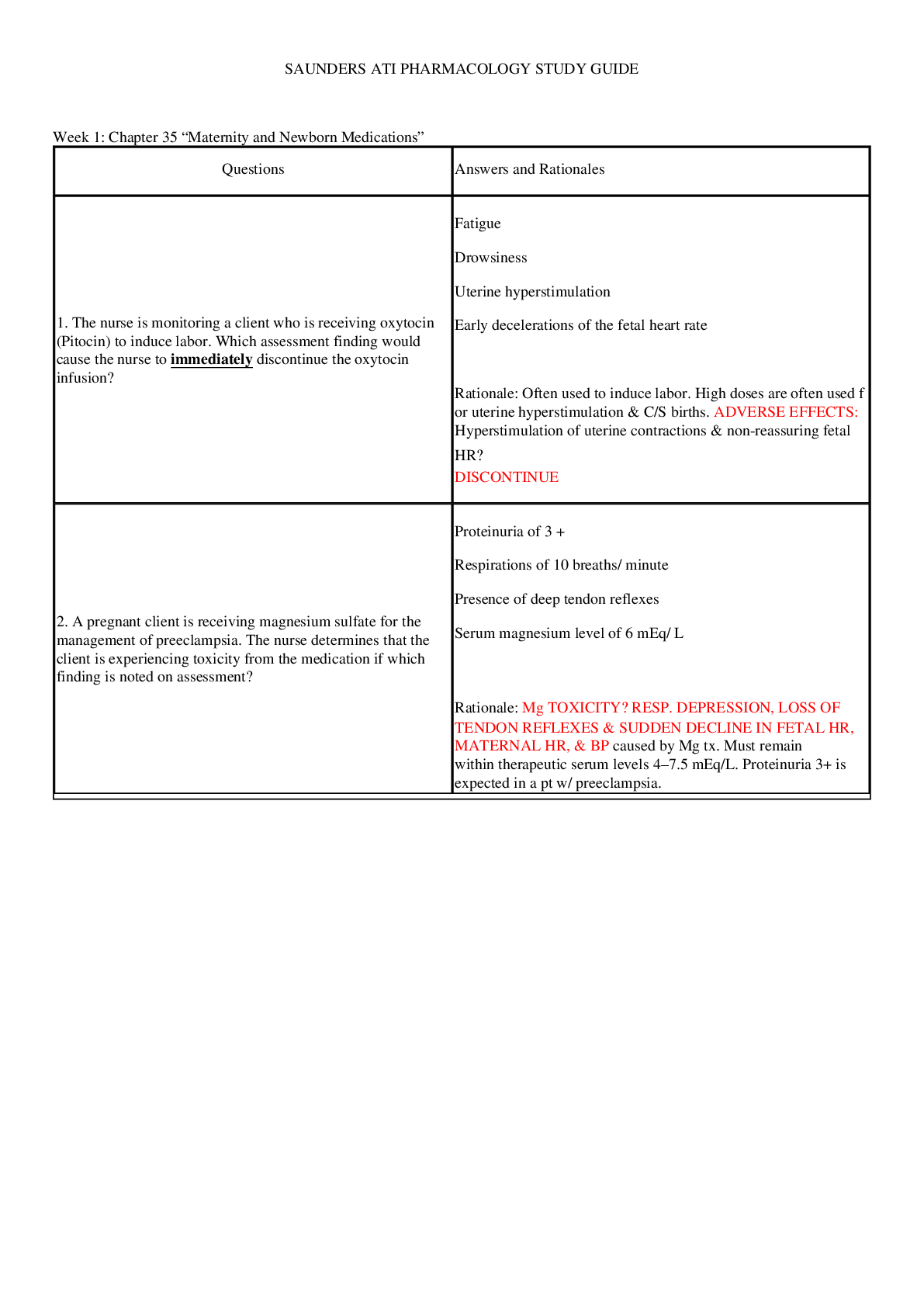
Cyber Awareness 2022-2023 Knowledge Check (Answered) 1. How many potential insider threat indicators does a person who is married with two children, vacations at the beach every year, is pleasant to w... ork with, but sometimes has poor work quality display? 2. What is the best response if you find classified government data on the internet? 3. After reading an online story about a new security project being developed on the military installation where you work, your neighbor asks you to comment about the article. You know this project is classified. What should be your response? 4. What is a proper response if spillage occurs? 5. What should you do if a reporter asks you about potentially classified information on the web? 6. A user writes down details from a report stored on a classified system marked as Secret and uses those details to draft an unclassified briefing on an unclassified system without authorization. What is the best choice to describe what has occurred? 7. How many potential insider threat indicators does a coworker who often makes others uneasy by being persistent in trying to obtain information about classified projects to which he has no access, is boisterous about his wife putting them in credit card debt, and often complains about anxiety and exhaustion display? 8. Which of the following can an unauthorized disclosure of information classified as Confidential reasonably be expected to cause? 9. Which classification level is given to information that could reasonably be expected to cause serious damage to national security? 10. When classified data is not in use, how can you protect it? 11. Which is a good practice to protect classified information? 12. Which of the following is a good practice to aid in preventing spillage? 13. What is required for an individual to access classified data? 14. What type of activity or behavior should be reported as a potential insider threat? 15. Which of the following practices reduces the chance of becoming a target by adversaries seeking insider information? 16. Which scenario might indicate a reportable insider threat security incident? 17. Why might [Show More]
Last updated: 2 years ago
Preview 1 out of 8 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$7.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Mar 28, 2023
Number of pages
8
Written in
Additional information
This document has been written for:
Uploaded
Mar 28, 2023
Downloads
0
Views
107








.png)