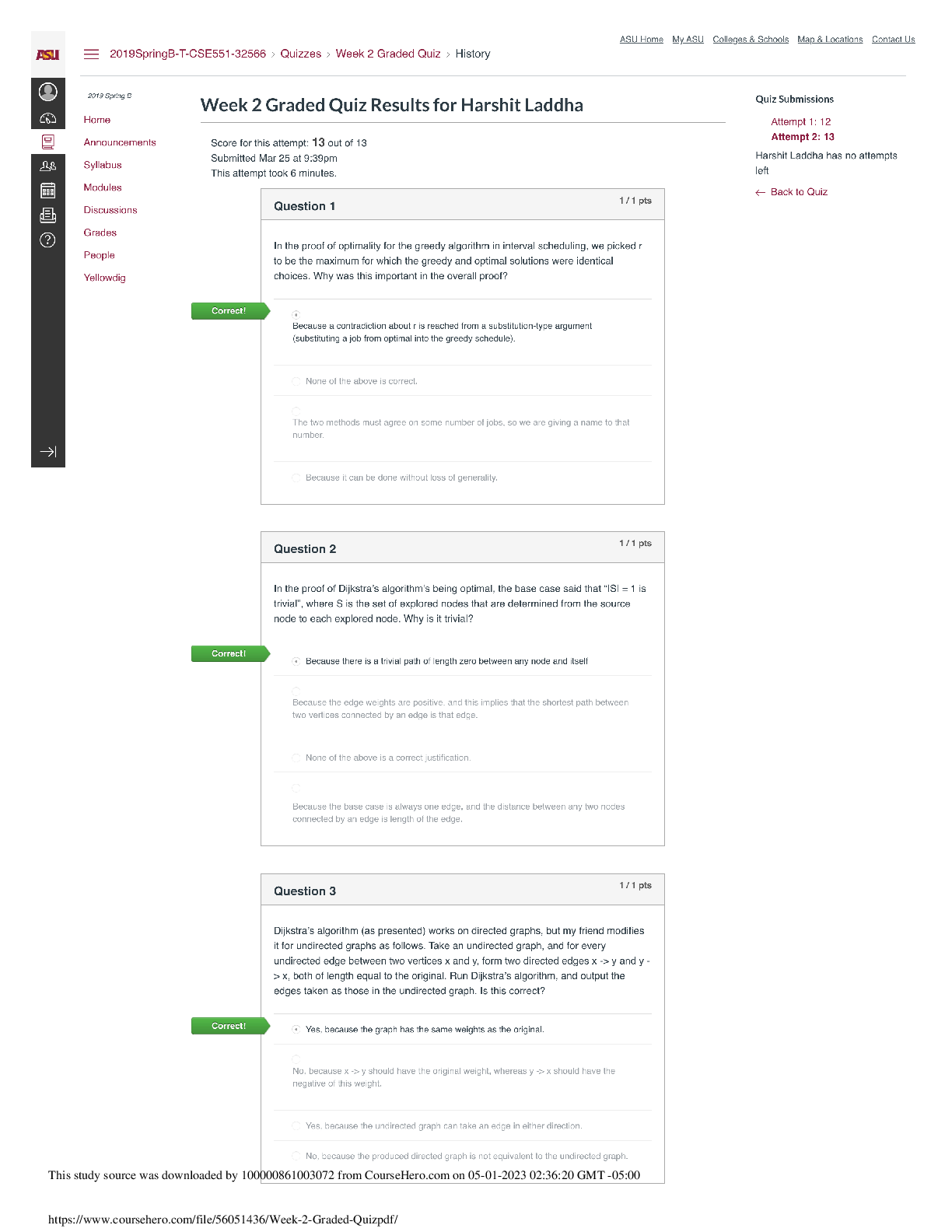
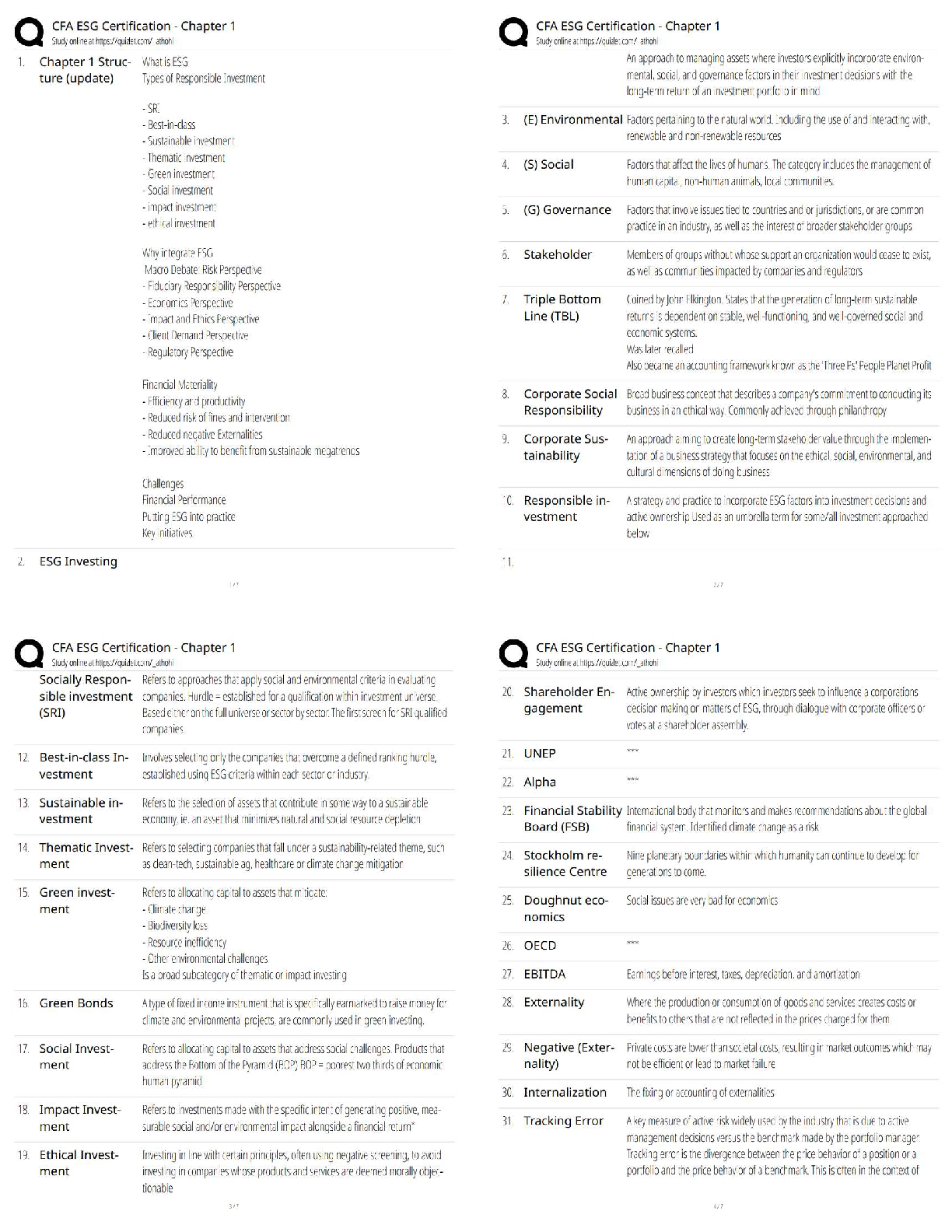
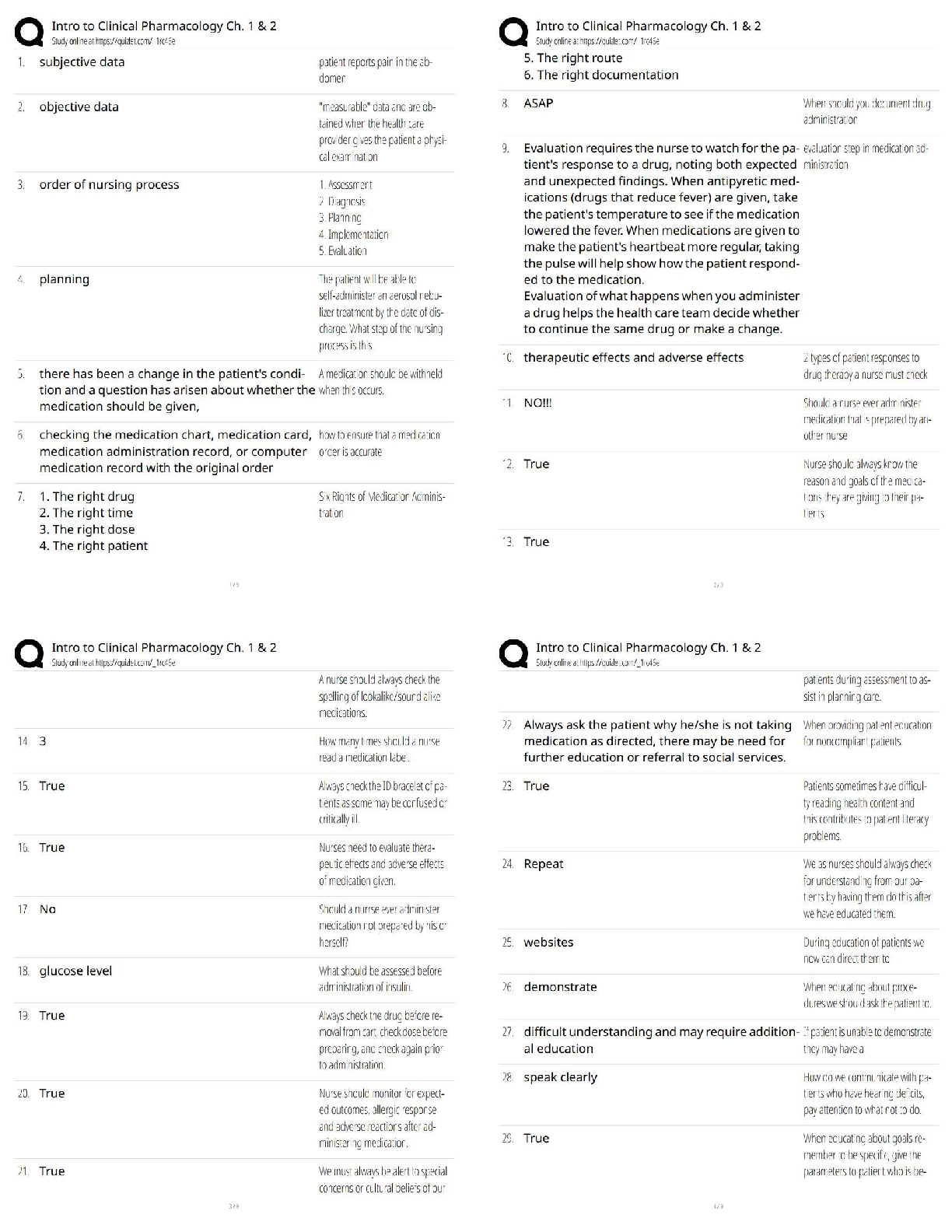
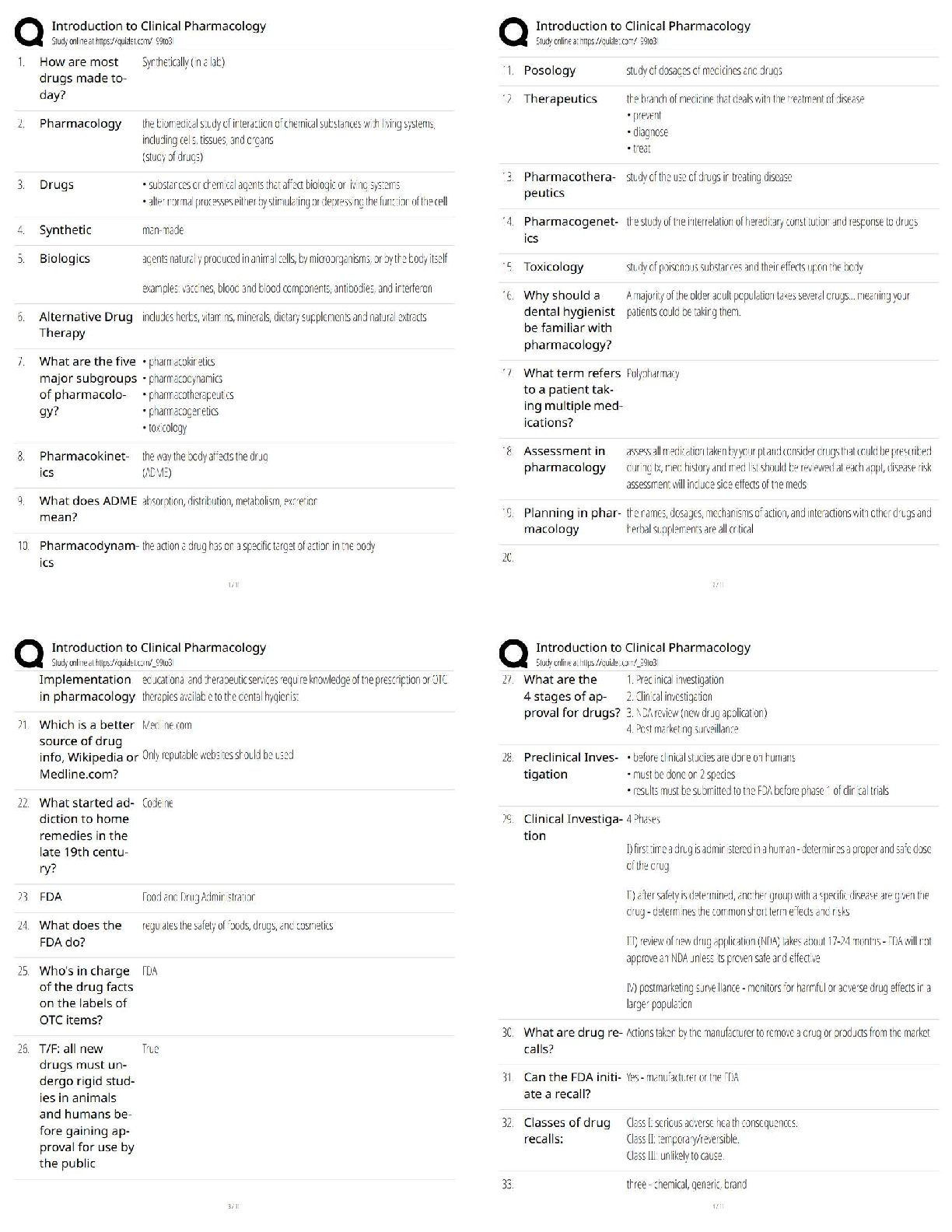
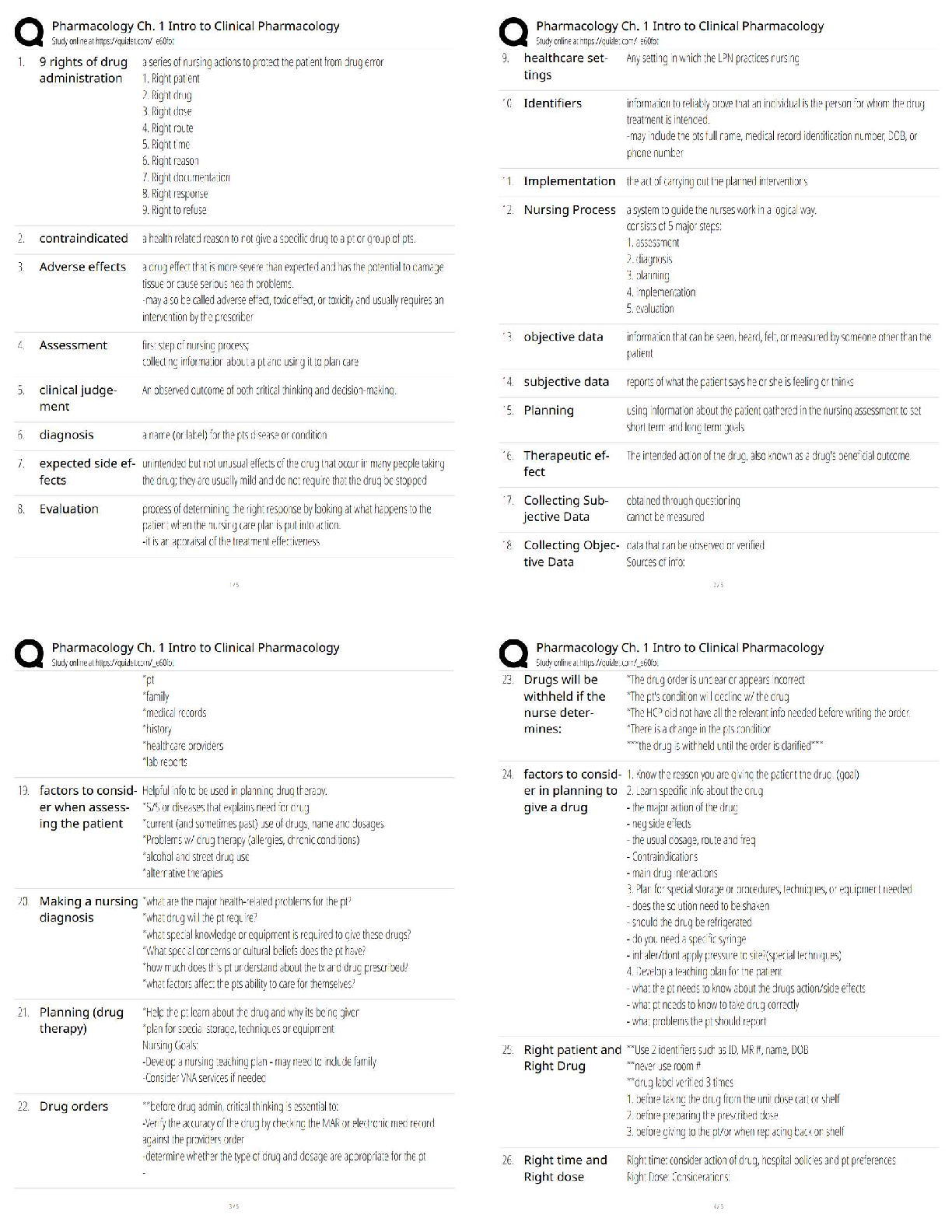
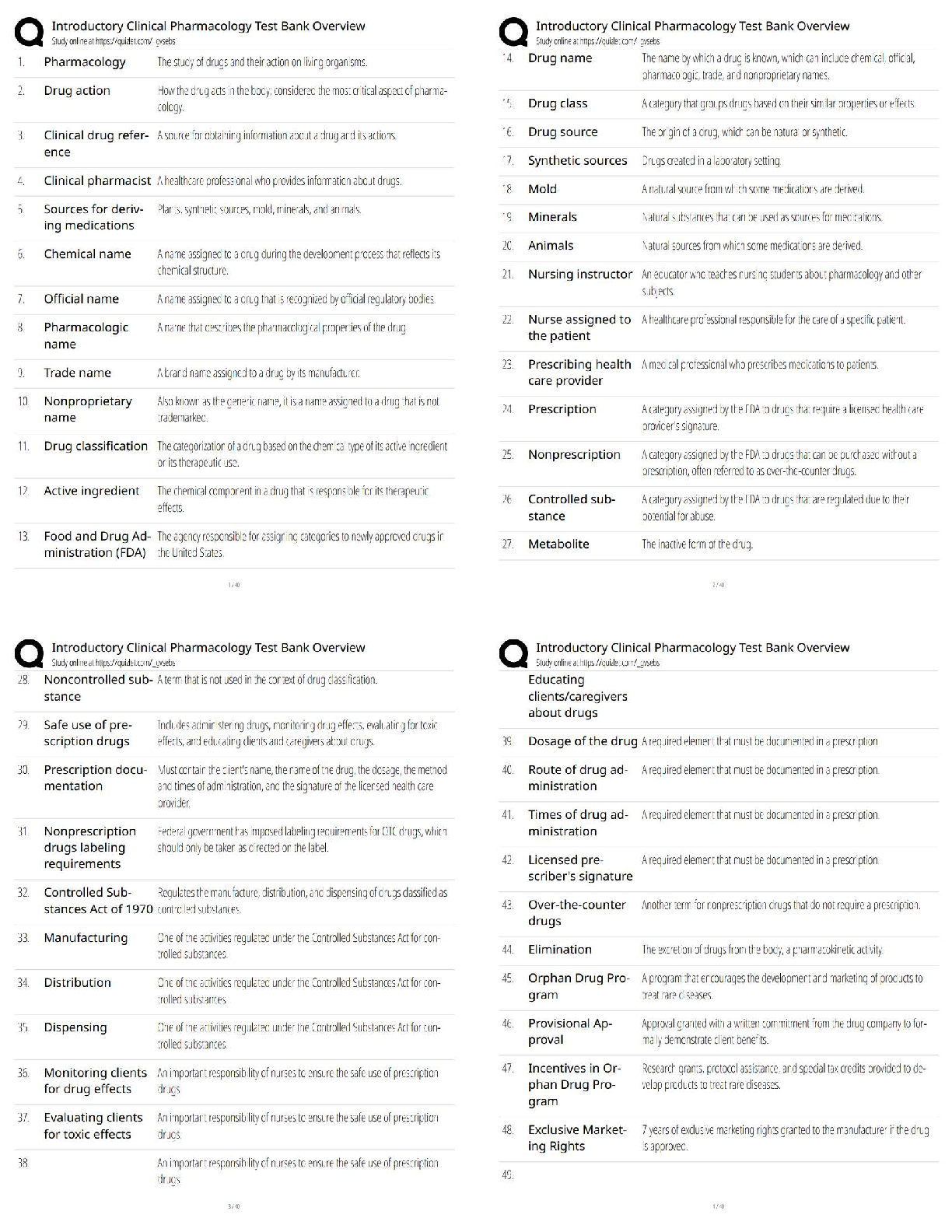
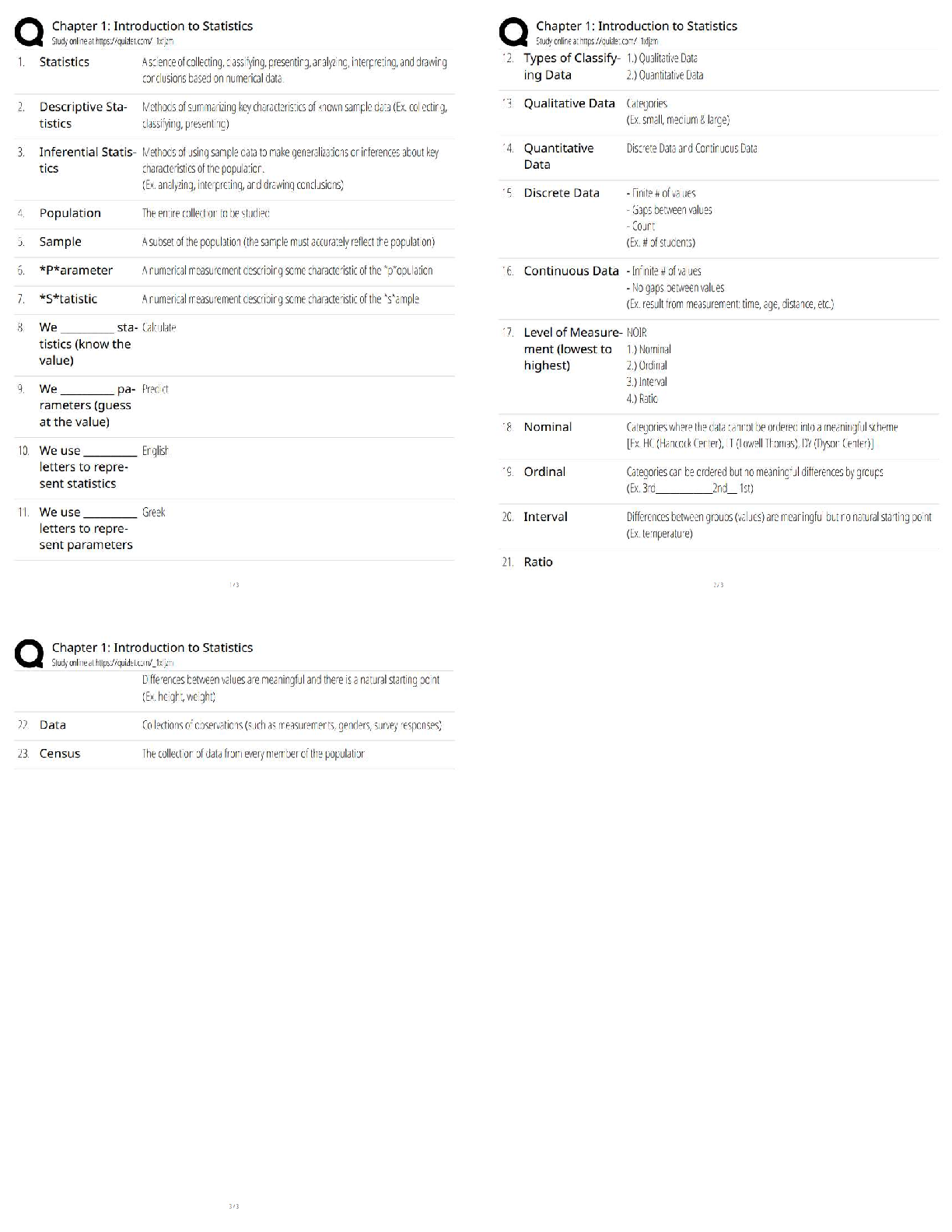
4.06 IDENTITY THEFT WEBQUEST
Total Points: 60
Using information in the lesson, plus the Internet, answer the following questions.
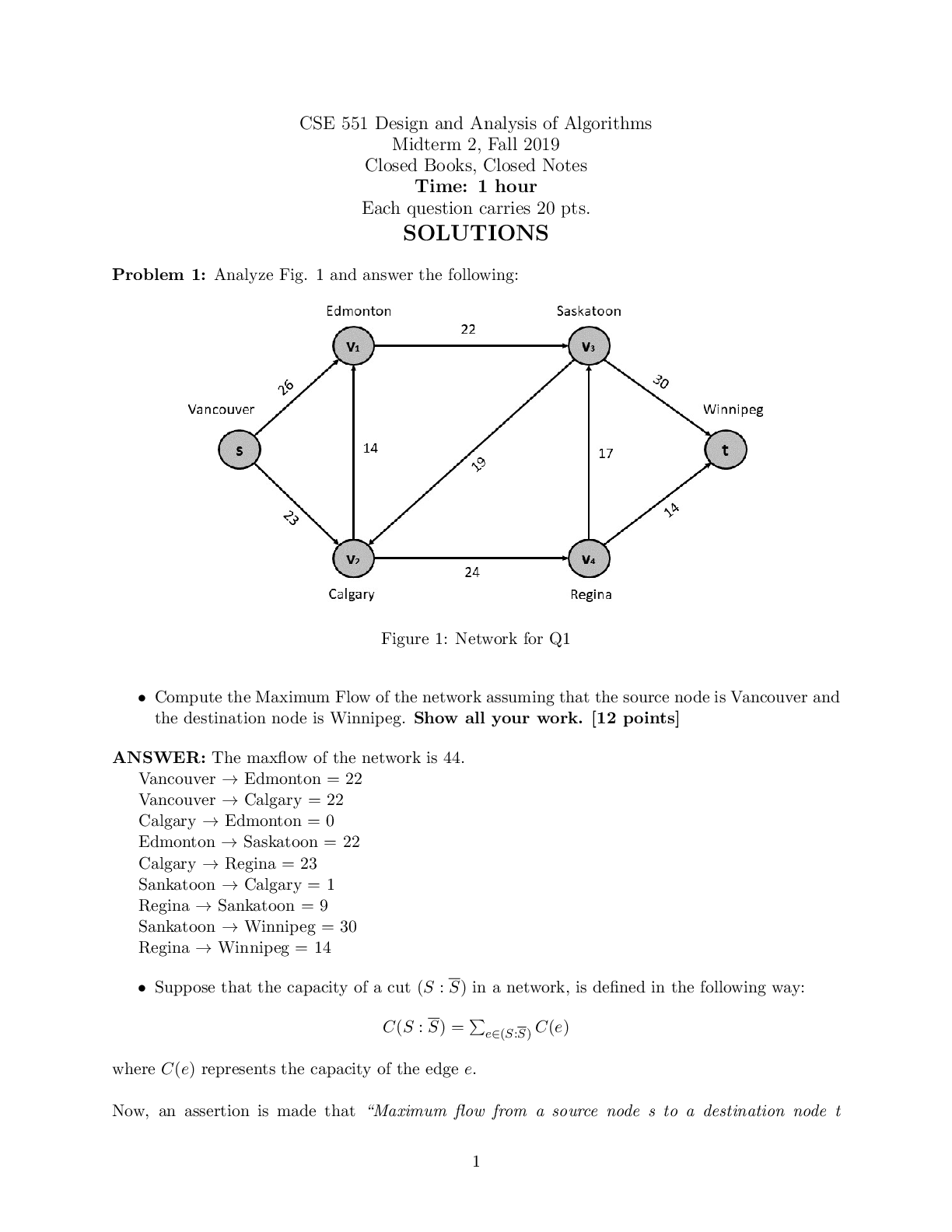
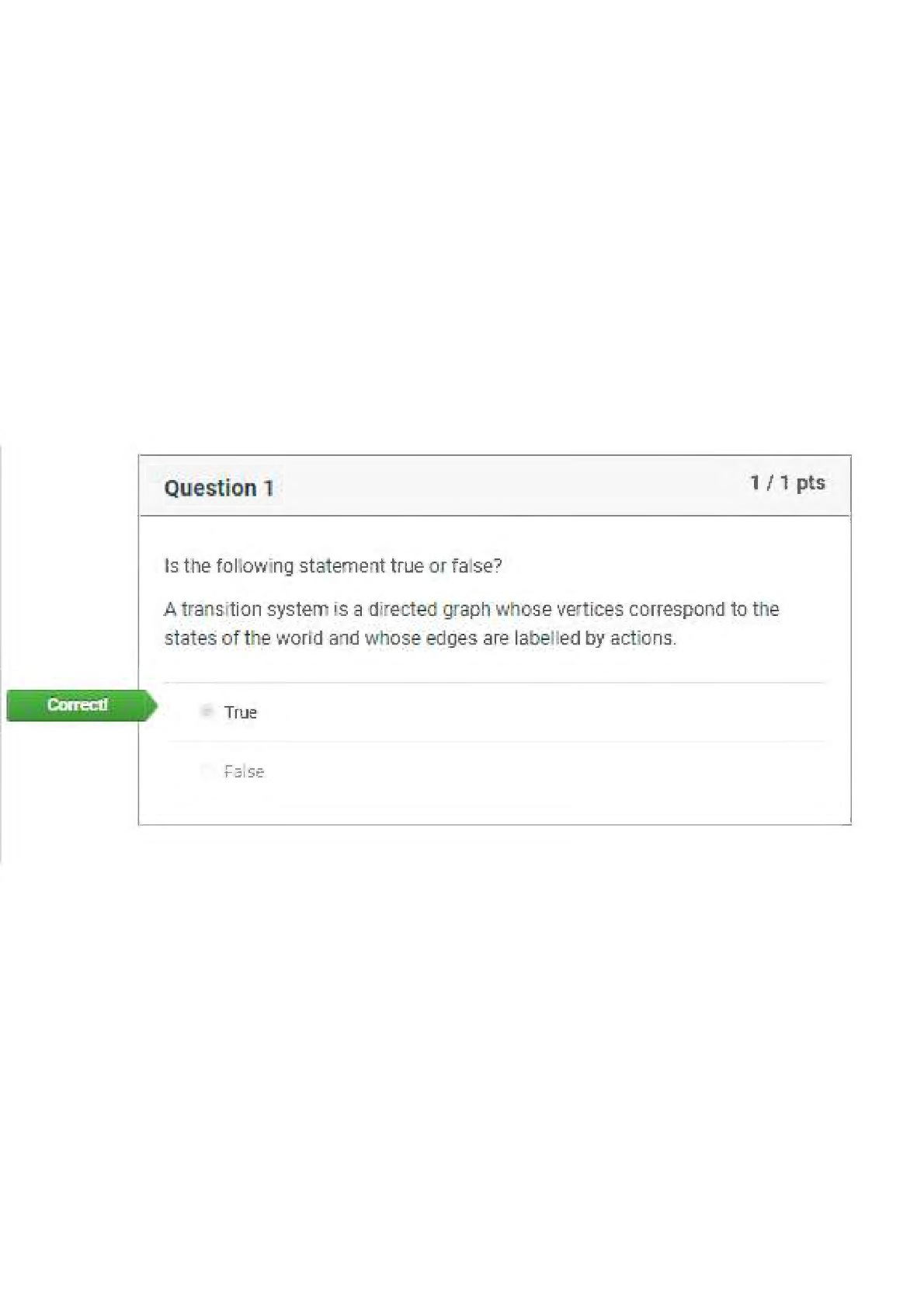
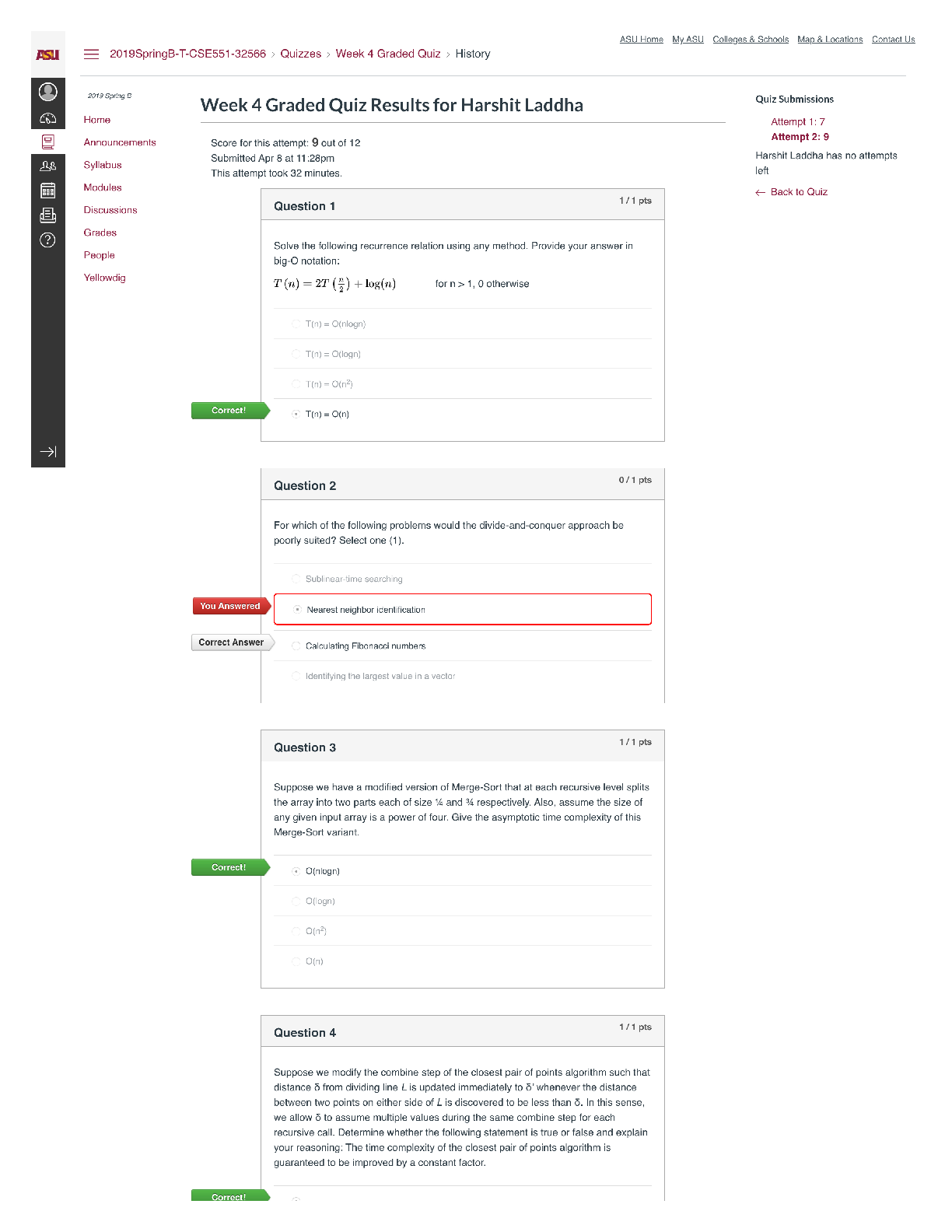
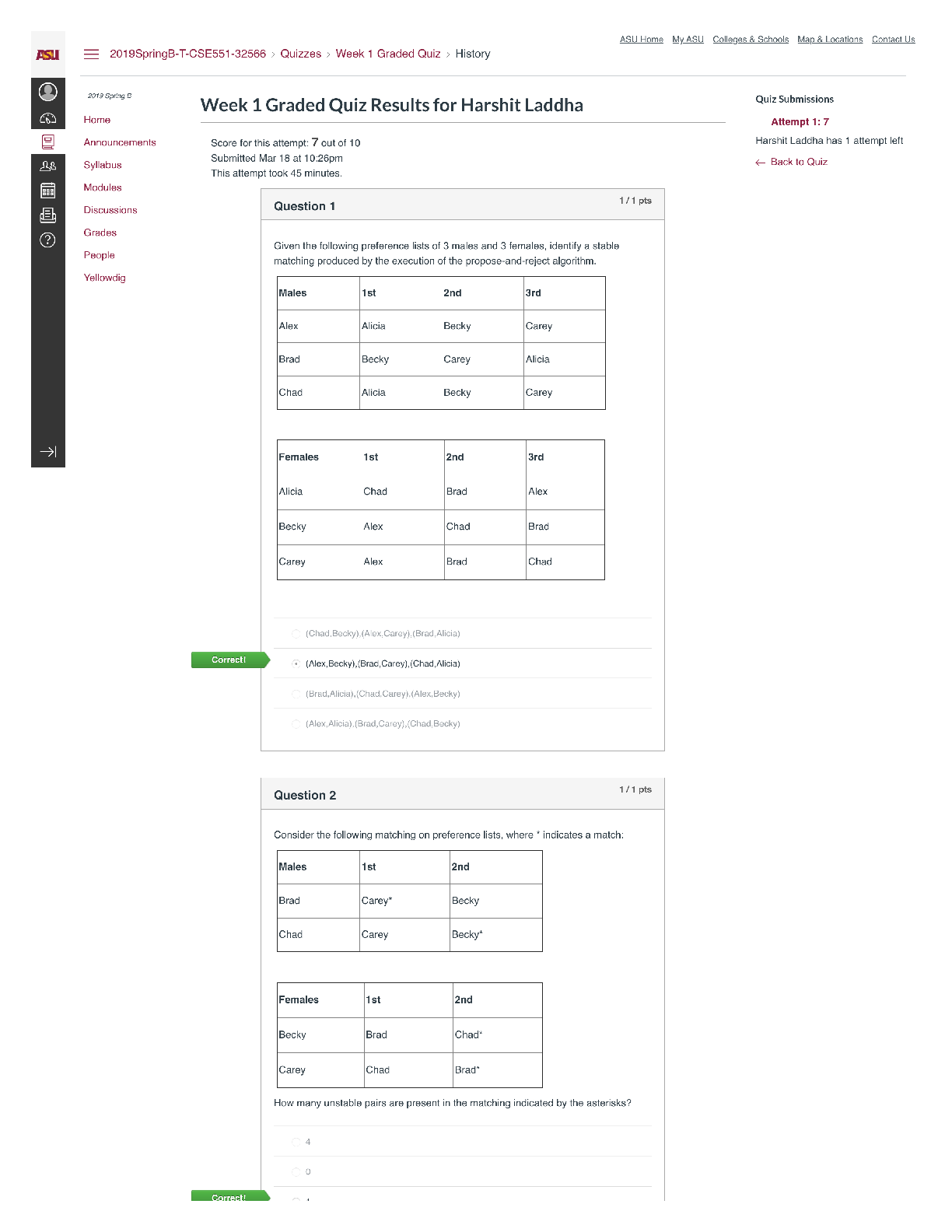
1. Define “identity theft”. The fraudulent acquisition and use of a persons private
id
...
4.06 IDENTITY THEFT WEBQUEST
Total Points: 60
Using information in the lesson, plus the Internet, answer the following questions.
1. Define “identity theft”. The fraudulent acquisition and use of a persons private
identifying, usually for financial gain.
2. List two ways in which one’s identity could be stolen from a credit card
3. Once a person has had their identity stolen, what can they do? (Google: Steps to take
after identity has been stolen)
• file a report with the federal trade commission
• contact your local police department
4. List five things a person can do to avoid having their identity stolen.
5. What things do you do now that put your identity at risk?
6. What changes can you make in your life which will help protect your identity?
7. Name one specific group of people targeted for Identity Theft?
8. On the Internet, find two personal stories of fraud. (Google: Identity Theft Story) What
are the consequences for the victim? Write one paragraph about each (that’s two
paragraphs) personal story you find.
/
Answer
In the criminal context , fraud must be proved “beyond a reasonable doubt”. If
convicted of a crime, a defendant may be sentenced to jail, probation, or fines. In
private civil lawsuits, the standard of lower and punishment is often resolution, and
monetary damages.
9. Should you trust your friends with your personal information? Why or why not. No
10. Using the Internet, find the latest ways thieves gain access to personal information
(Google latest ways to steal identity)
11. List 3 examples of Strong Passwords (don’t actually put your password in this space)
12. Write an example of a salesperson using an unethical sales practice:
13. Explain the difference between data that is encrypted and data that has not been
encrypted:
14. How do firewalls and antivirus software help protect you from financial fraud and/or
keep your identity safe?
15. Why is it a good idea to clear your browser’s cache?
16. List two examples of a fraudulent scheme that comes through your email.
17. Finish the following sentence: If it’s too good to be true,
[Show More]