Business > EXAM > FedVTE Enterprise Cyber security Operations 33 Questions with Verified Answers,100% CORRECT (All)
FedVTE Enterprise Cyber security Operations 33 Questions with Verified Answers,100% CORRECT
Document Content and Description Below
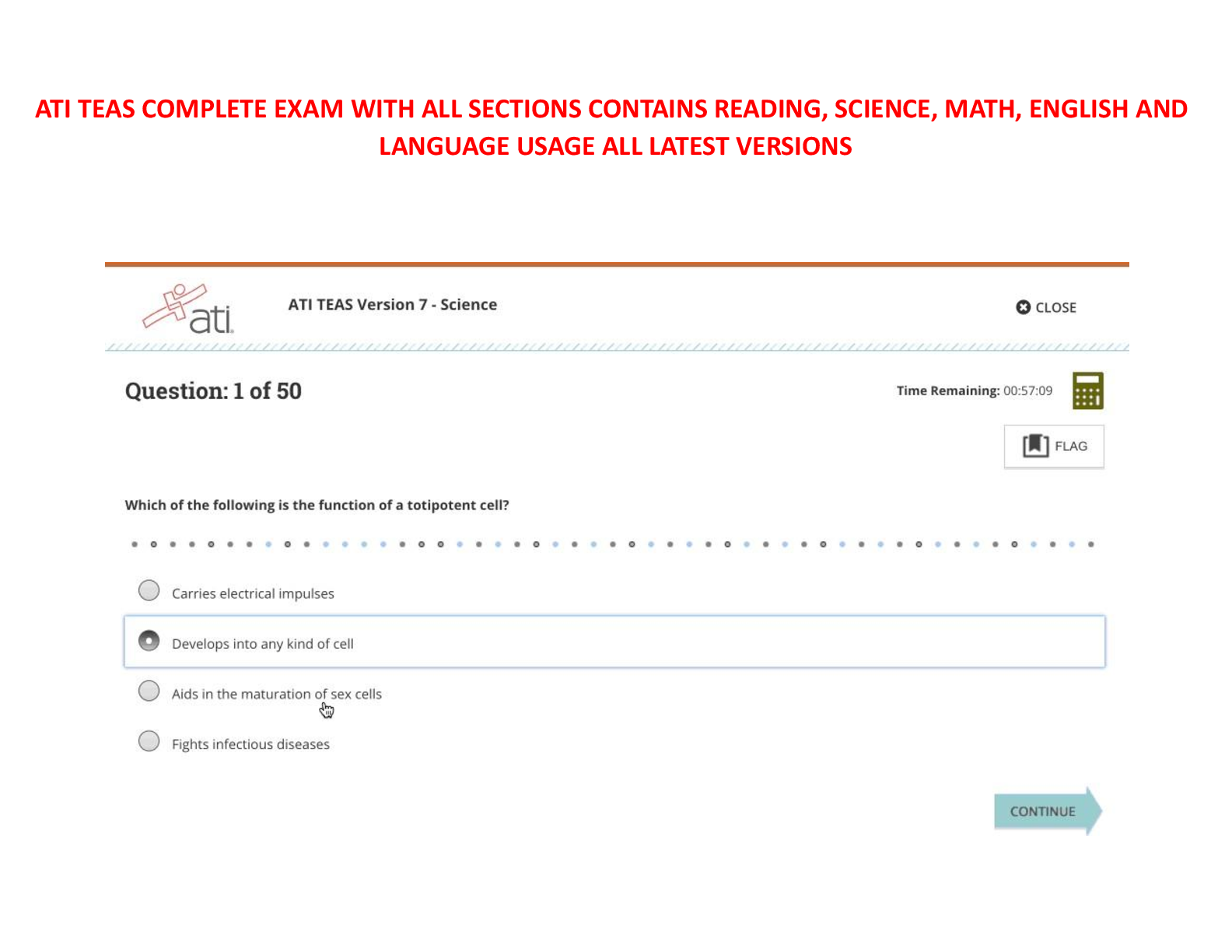
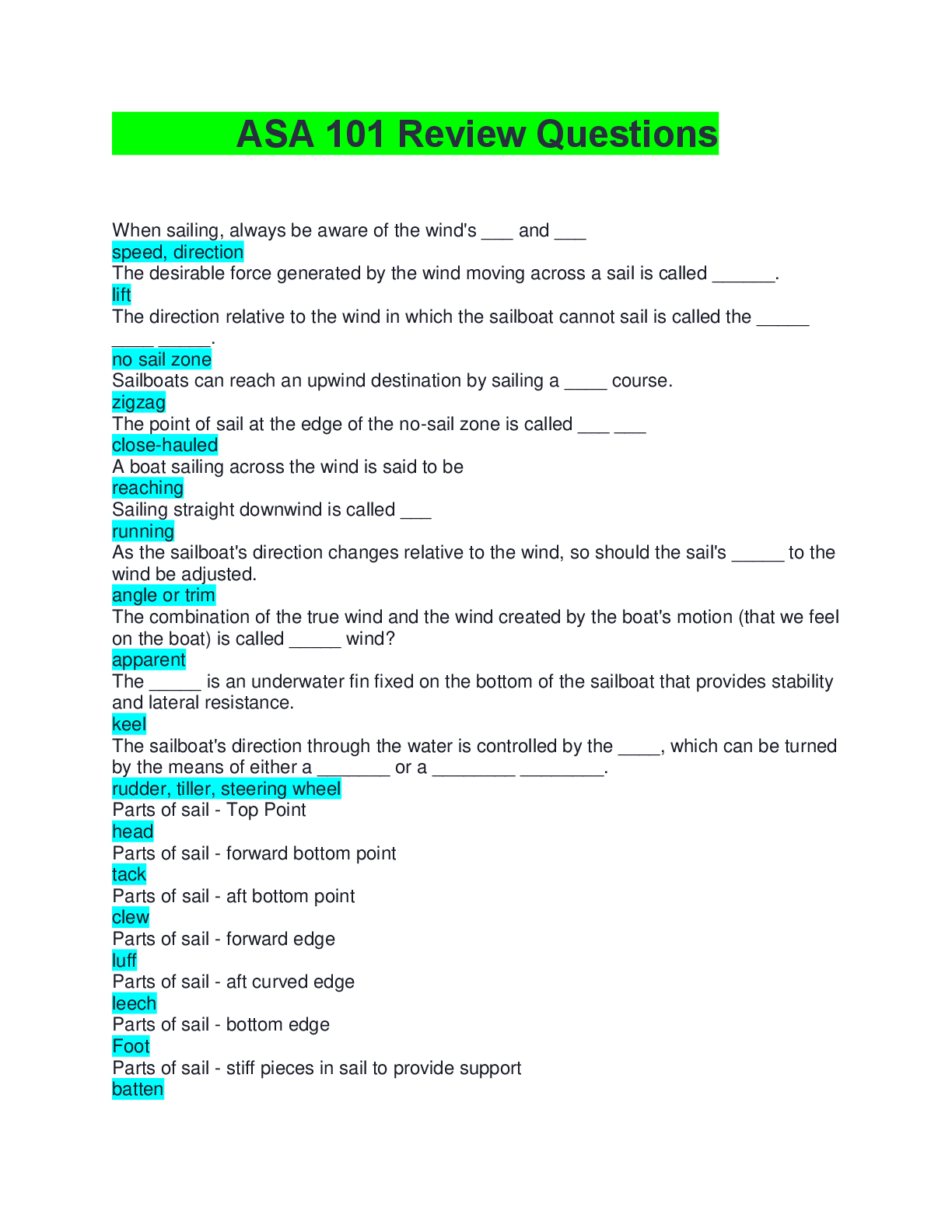
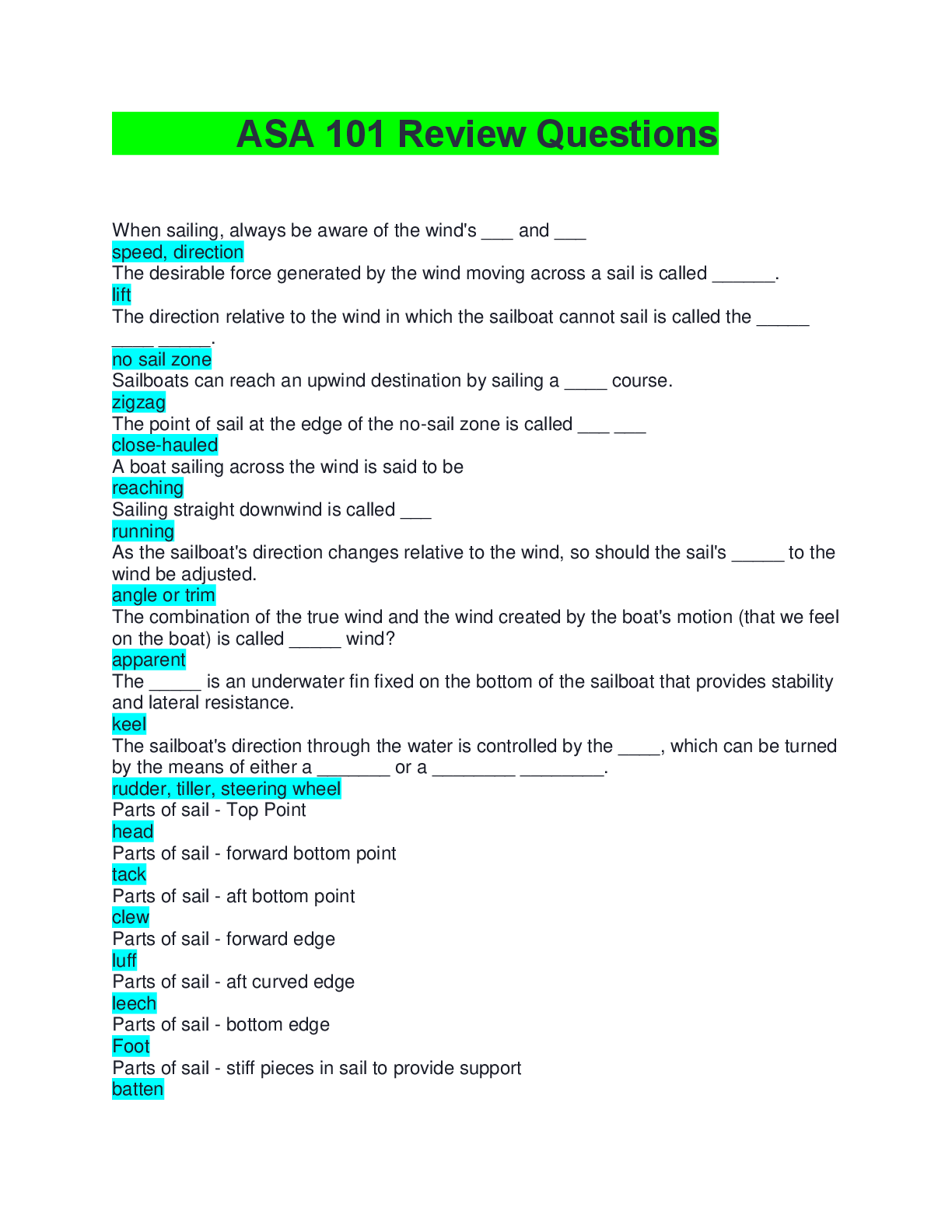
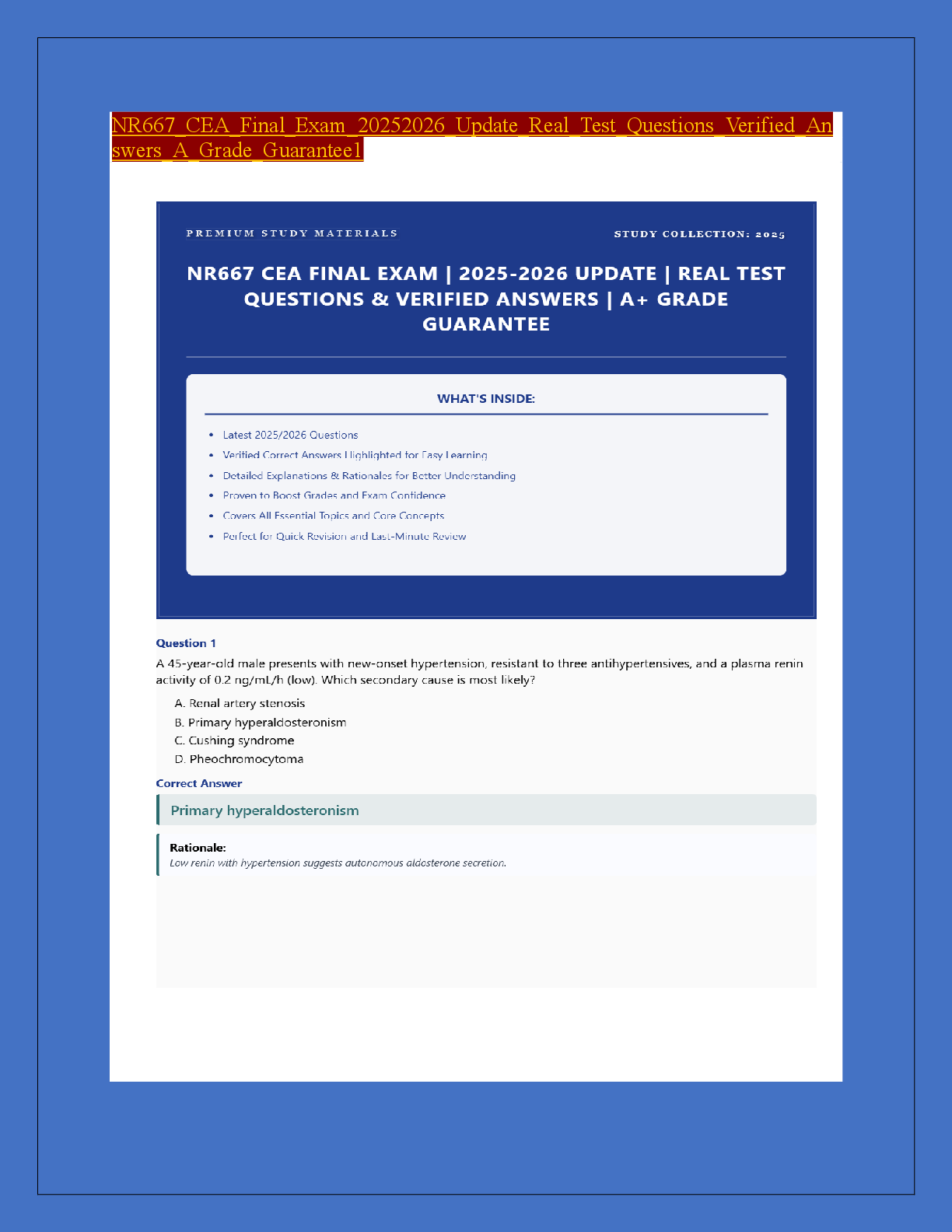
FedVTE Enterprise Cyber security Operations 33 Questions with Verified Answers The acronym VPN stands for: - CORRECT ANSWER Virtual Private Network Executives are responsible for managing and ... overseeing enterprise risk management. - CORRECT ANSWER True The internal audit department is investigating a possible accounting breach. One of the auditors is sent to interview the following employees: Employee A works in the accounts receivable office and is in charge of entering data into the finance system; Employee B works in the accounts payable office and is in charge of approving purchase orders; Employee C is the manager of the finance department, supervises Employee A and Employee B, and can perform the functions of both Employee A and Employee B. Which of the following should the auditor suggest be done to avoid future security breaches? - CORRECT ANSWER The manager should only be able to review the data and approve purchase orders. An electrical utility has employed a consultant to perform a controls assessment of the personnel system, backend business operations, and the SCADA system used in their facility. Which of the following correctly states the risk management options that the consultant should use during the assessment? - CORRECT ANSWER Avoid, transfer, mitigate, and accept. The acronym SOA stands for: - CORRECT ANSWER Statement of Applicability Which of the following are steps in the risk management process? - CORRECT ANSWER All of the Above Cybersecurity should be involved throughout the entire system development life cycle. - CORRECT ANSWER True A Physical Security Manager is ready to replace 30 analog surveillance cameras with IP cameras with built in web management. There are several security guard desks on different networks that must be able to view the cameras without unauthorized people viewing the video as well. The selected IP camera vendor does not have the ability to authenticate users at the camera level. Which of the following should be used to BEST secure this environment? - CORRECT ANSWER Create an IP camera network and deploy a proxy to authenticate users prior to accessing the cameras. What is an advantage of cloud computing? - CORRECT ANSWER Improved performance Cybersecurity is primarily about implementing a checklist of requirements. - CORRECT ANSWER False A retail merchant has had a number of issues in regards to the integrity of sensitive information across all of its customer databases. This has resulted in the merchants share price decreasing in value by more than one third and the merchant has been threatened with losing their ability to process credit card transactions. The new Chief Information Security Officer (CISO) as a result has initiated a program of work to solve the issues. The business has specified that the solution needs to be enterprise grade and meet the following requirements: Work across all major platforms, applications and infrastructure; Tracks activity of all users, including administrators; Operates without negatively impacting the performance of production platforms, applications, and infrastructures; Provides real-time incident reporting; Displays incidents in a dashboard view for easy recognition; Includes a report generator where business units are able to query against companys system assets. In order to solve this problem, which of the following security solutions will BEST meet the above requirements? - CORRECT ANSWER Implement an enterprise-based SIEM solution to process the logs of the major platforms, applications, and infrastructure. Open source material is a good resource for gathering substantial information on a desired target. - CORRECT ANSWER True The agile process emphasizes which of the following over processes and tools? - CORRECT ANSWER Individuals and Interactions Jurisdiction and Breach Notification are examples of what type of potential risk? - CORRECT ANSWER Legal Which of the following is considered the necessary research done before launching a scan? - CORRECT ANSWER Network Reconnaissance Cloud computing does NOT require a constant Internet connection. - CORRECT ANSWER False Which of the following should be developed during the SDLC? - CORRECT ANSWER All of the Above HTML5 is the latest version of the markup language. - CORRECT ANSWER True Chain of Custody shows who controlled, secured and obtained a piece of evidence. - CORRECT ANSWER True There should never be different levels of regulations within a single business unit. - CORRECT ANSWER False New zero day attacks are being discovered on a regular basis against a broad range of IT systems. Which of the following best practices should a security manager do to manage the risks being faced through these attack vectors? - CORRECT ANSWER Maintain a list of critical systems. Which of the following BEST explains SAML? - CORRECT ANSWER A security attestation model built on XML and SOAP based services, which allows for the exchange of AandA data between systems and supports Federated Identity Management. An intrusion detection system logged an attack attempt from a remote IP address. One week later, the attacker successfully compromised the network. Which of the following MOST likely occurred? - CORRECT ANSWER No one was reviewing the IDS event logs. A government agency has a major new initiative to virtualize as many servers as possible, due to power and rack space capacity at its two data centers. The agency has prioritized virtualizing older servers first as the hardware is nearing end of life. The two initial migrations include Windows 2000 hosts (domain controllers and front-facing web servers) and open source Linux hosts (front facing web servers). Which of the following should occur based on best practices? - CORRECT ANSWER Each data center should contain separate virtual environments for the web servers and for the domain controllers. Which of the following is an agreement between two or more organizations to work together to allow information exchange? - CORRECT ANSWER Interoperability The DoD has specific mandatory requirements for data encryption. - CORRECT ANSWER True A new IDS appliance is generating a very large number of events, most of which are not security-related. Select the approach which best resolves this issue. - CORRECT ANSWER Adjust IDS filters that are creating false positives. Good metrics are SMART. The M in the acronym SMART stands for: - CORRECT ANSWER Measurable Which of the following can be useful in information gathering? - CORRECT ANSWER All of the Above File Transfer Protocol (FTP) is secure. - CORRECT ANSWER False Impact measures are inherently organization specific. - CORRECT ANSWER True A Security Manager is selecting web conferencing systems for internal use. The system will only be used for internal employee collaboration. All of the following should be priority issues for the security manager EXCEPT: - CORRECT ANSWER PBX integration of the service The firm's CISO has been working with the Purchasing and the Project Management Office on soliciting bids for a series of HIDS and NIDS products for a major installation in the firm's new Hong Kong office. After reviewing RFQs received from three vendors, the company has not gained any real data regarding the specifications about any of the solutions and want that data before the procurement continues. Which of the following will the CISO do at this point to get back on track in this procurement process? - CORRECT ANSWER Contact the three submitting vendor firms and have them submit supporting RFIs to provide more detailed information about their product solutions. [Show More]
Last updated: 2 years ago
Preview 1 out of 4 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

ALL FedVTE Exam (21 Sets) Questions with Verified Answers,100% CORRECT
FedVTE Cyber Risk Management for Technicians Questions with Answers,Cyber security Analyst Quiz FedVTE 40 Questions with Verified Answers,FedVTE Windows Operating System Security 50 Questions with Ver...
By securegrades 2 years ago
$0.5
21
Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 04, 2023
Number of pages
4
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 04, 2023
Downloads
0
Views
107