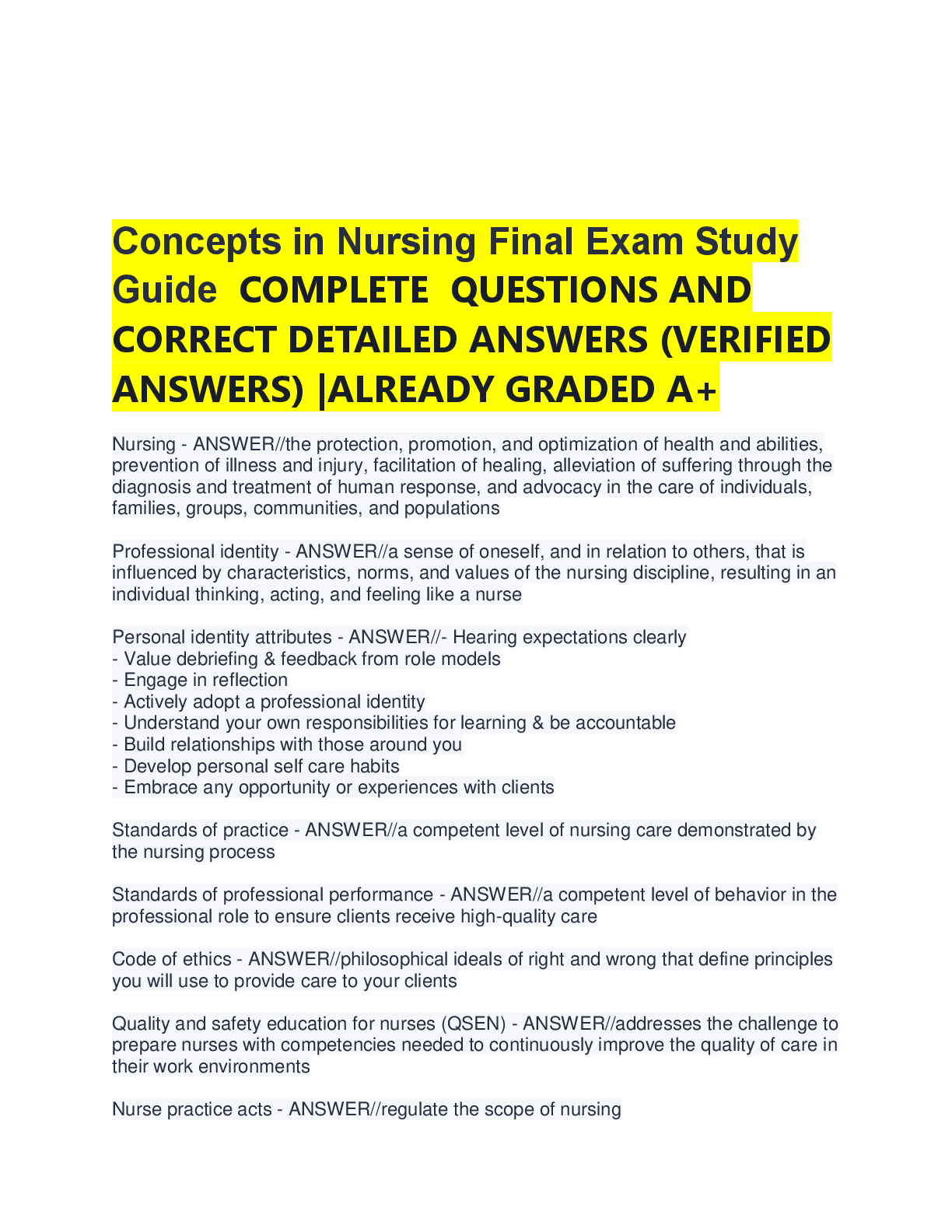
"Which phase of the cloud data lifecycle allows both read and process functions to be performed?
(A) Share
(B) Store
(C) Create
(D) Archive"
Create
"Which phase of the cloud data security lifecycle typically occurs
...
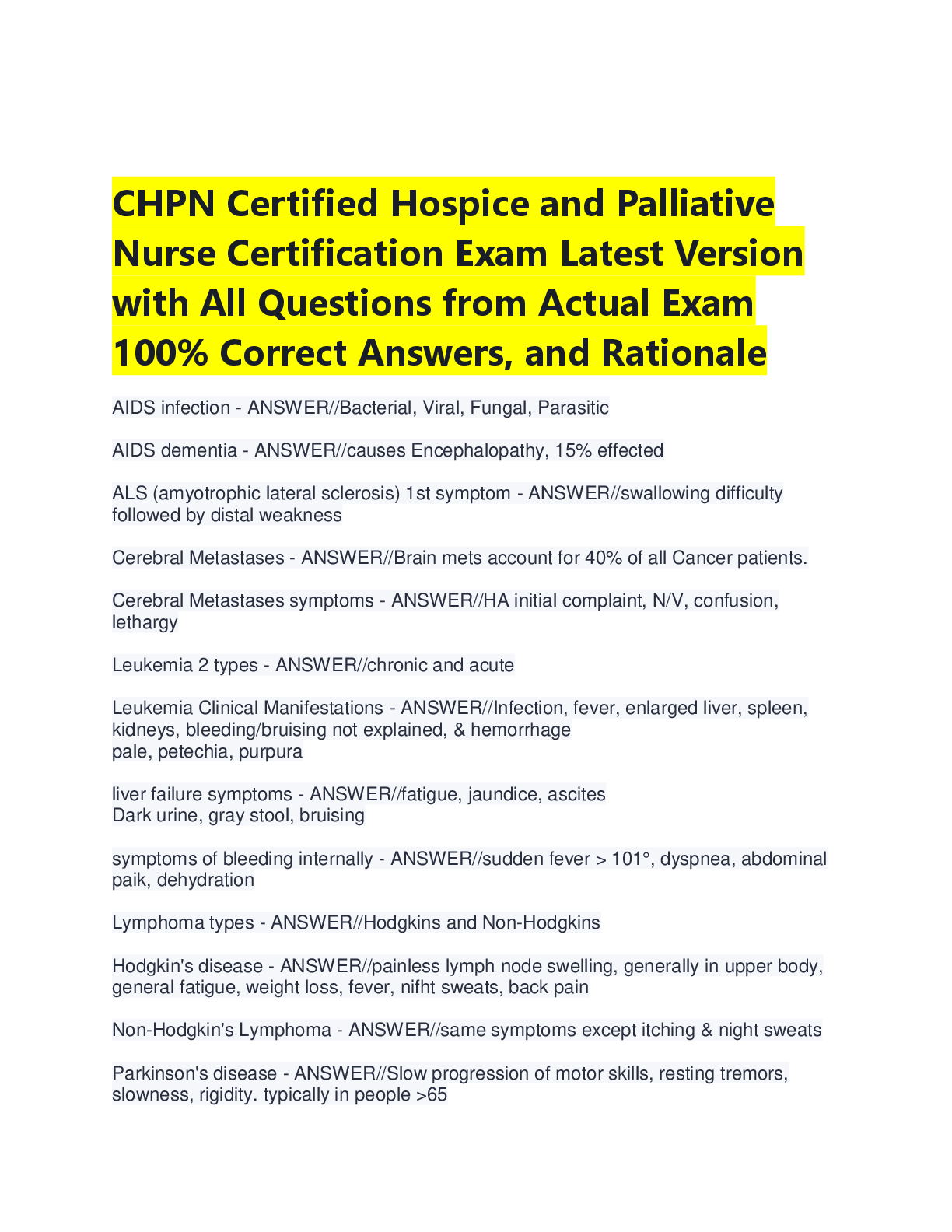
"Which phase of the cloud data lifecycle allows both read and process functions to be performed?
(A) Share
(B) Store
(C) Create
(D) Archive"
Create
"Which phase of the cloud data security lifecycle typically occurs simultaneously with creation?
(A) Use
(B) Share
(C) Store
(D) Destroy"
Store
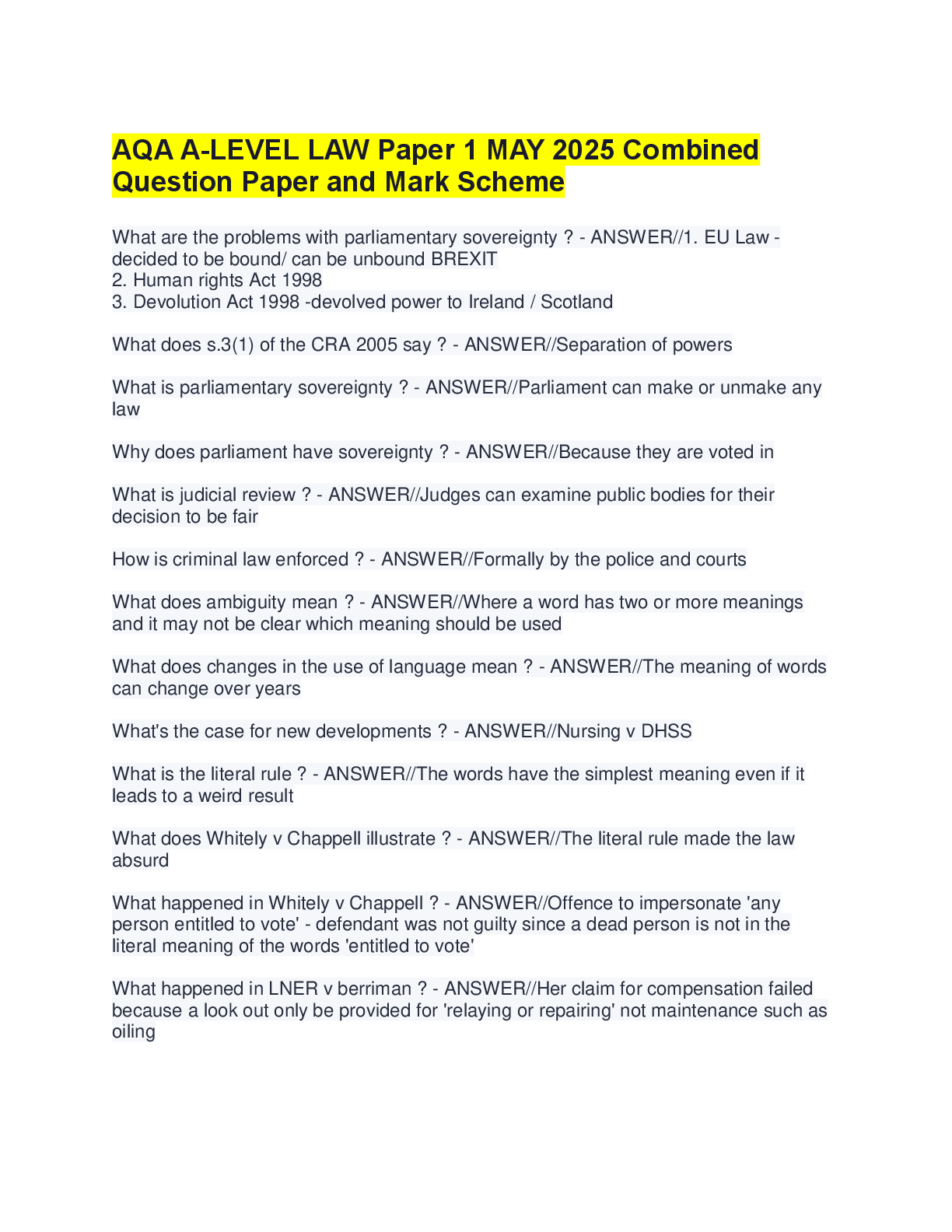
"Which phase of the cloud data life cycle uses content delivery networks?
(A) Share
(B) Create
(C) Destroy
(D) Archive"
Share
"Which phase of the cloud data life cycle is associated with crypto-shredding?
(A) Use
(B) Store
(C) Share
(D) Destroy"
Destroy
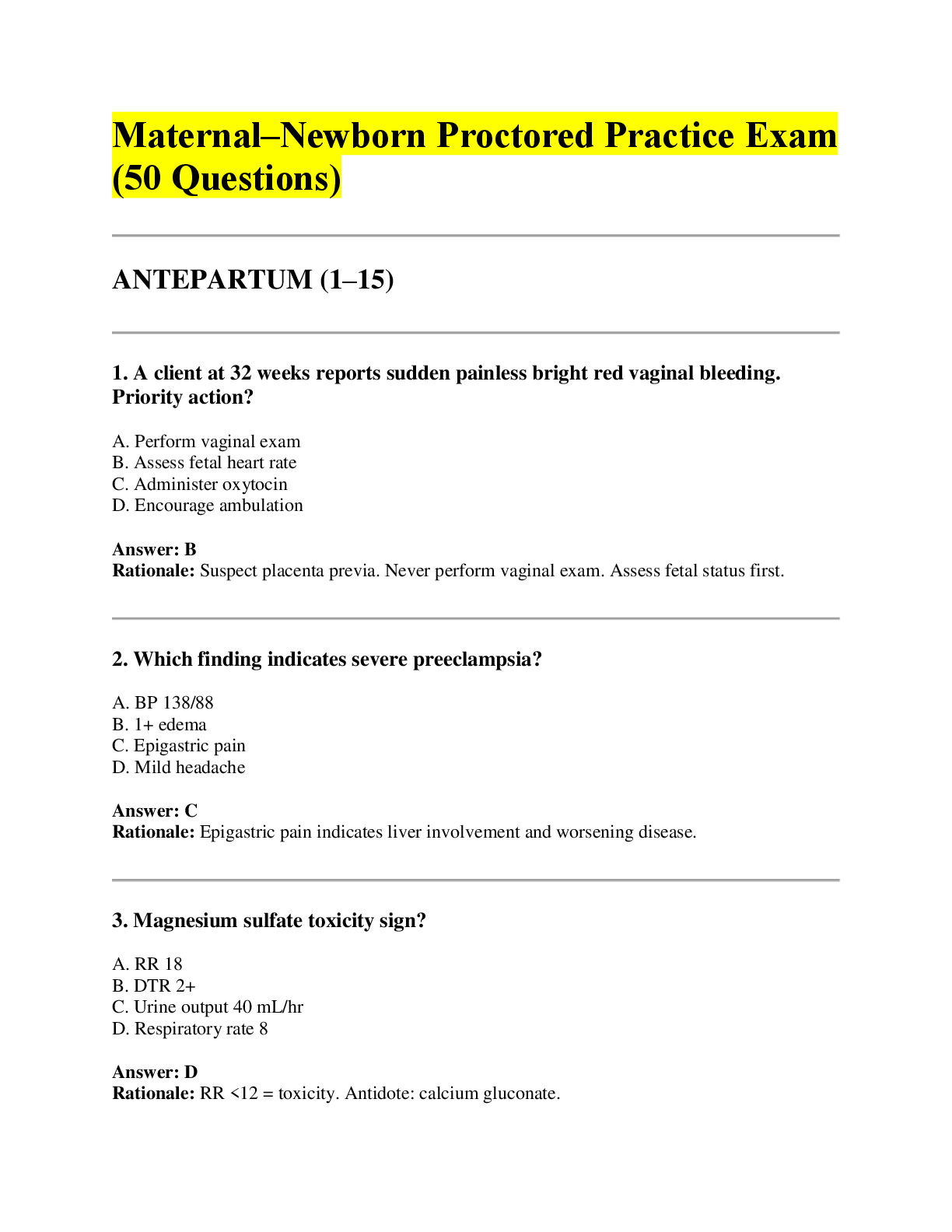
"Which cloud data storage architecture allows sensitive data to be replaced with unique
identification symbols that retain all the essential information about the data without
compromising its security?
(A) Obfuscation
(B) Tokenization
(C) Anonymization
(D) Randomization"
Tokenization
"Which methodology could cloud data storage utilize to encrypt all data associated in an
infrastructure as a service (IaaS) deployment model?
(A) Sandbox encryption
(B) Client-side encryption
(C) Polymorphic encryption
(D) Whole-instance encryption"
Whole-instance encryption
"There is a threat to a banking cloud platform service. The developer needs to provide inclusion
in a relational database that is seamless and readily searchable by search engine algorithms.
Which platform as a service (PaaS) data type should be used?
(A) Structured
(B) Unstructured
(C) Long-term storage
(D) Short-term storage"
Structured
"Which platform as a service (PaaS) storage architecture should be used if an organization wants
to store presentations, documents, and audio files?
(A) Block
(B) Object
(C) Distributed
(D) Relational database"
Object
"Which technique scrambles the content of data using a mathematical algorithm while keeping
the structural arrangement of the data?
(A) Tokenization
(B) Dynamic masking
(C) Proxy-based encryption
(D) Format-preserving encryption"
Format-preserving encryption
[Show More]