Computer Science > EXAMs > FRS 301 Final Exam | Questions and Answers (Complete Solutions) (All)
FRS 301 Final Exam | Questions and Answers (Complete Solutions)
Document Content and Description Below
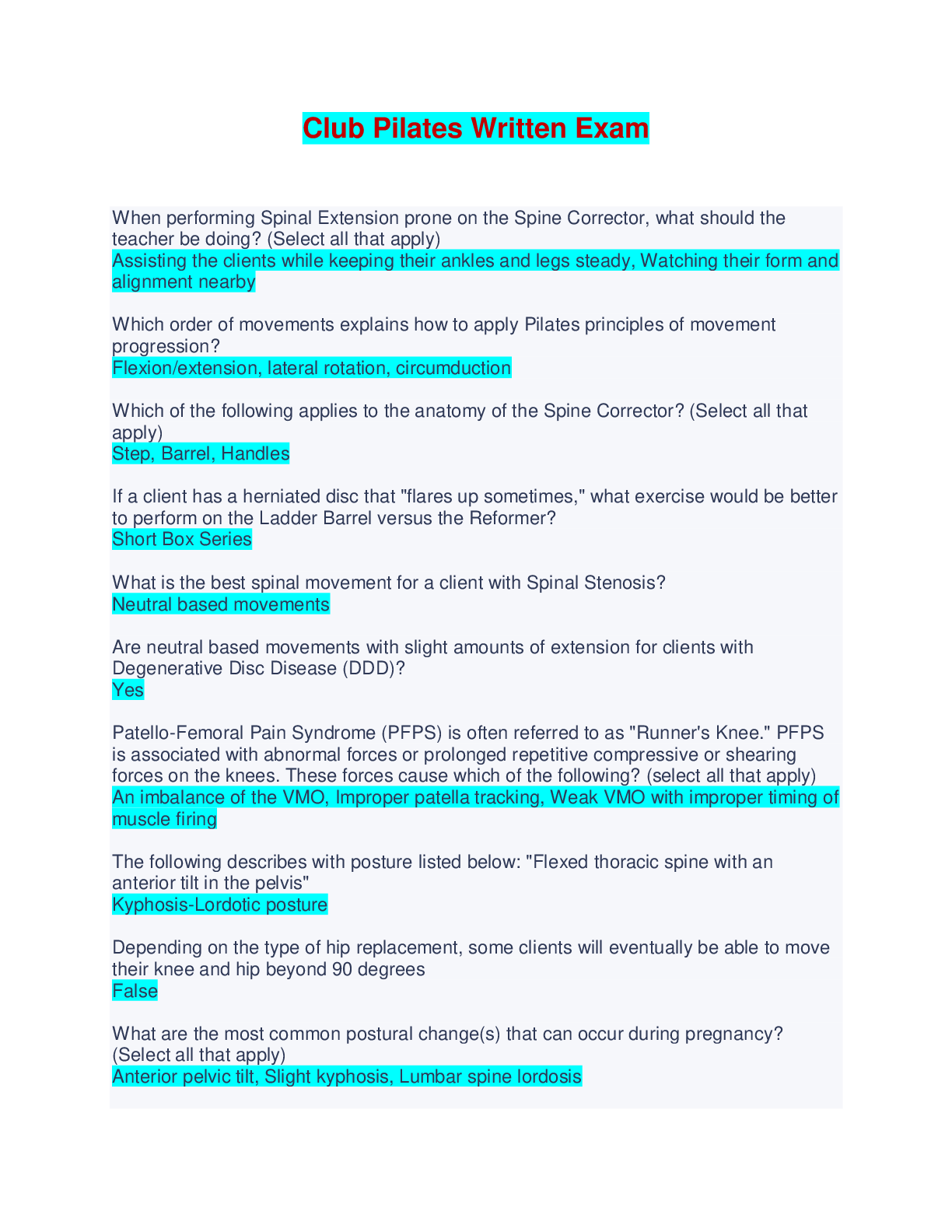
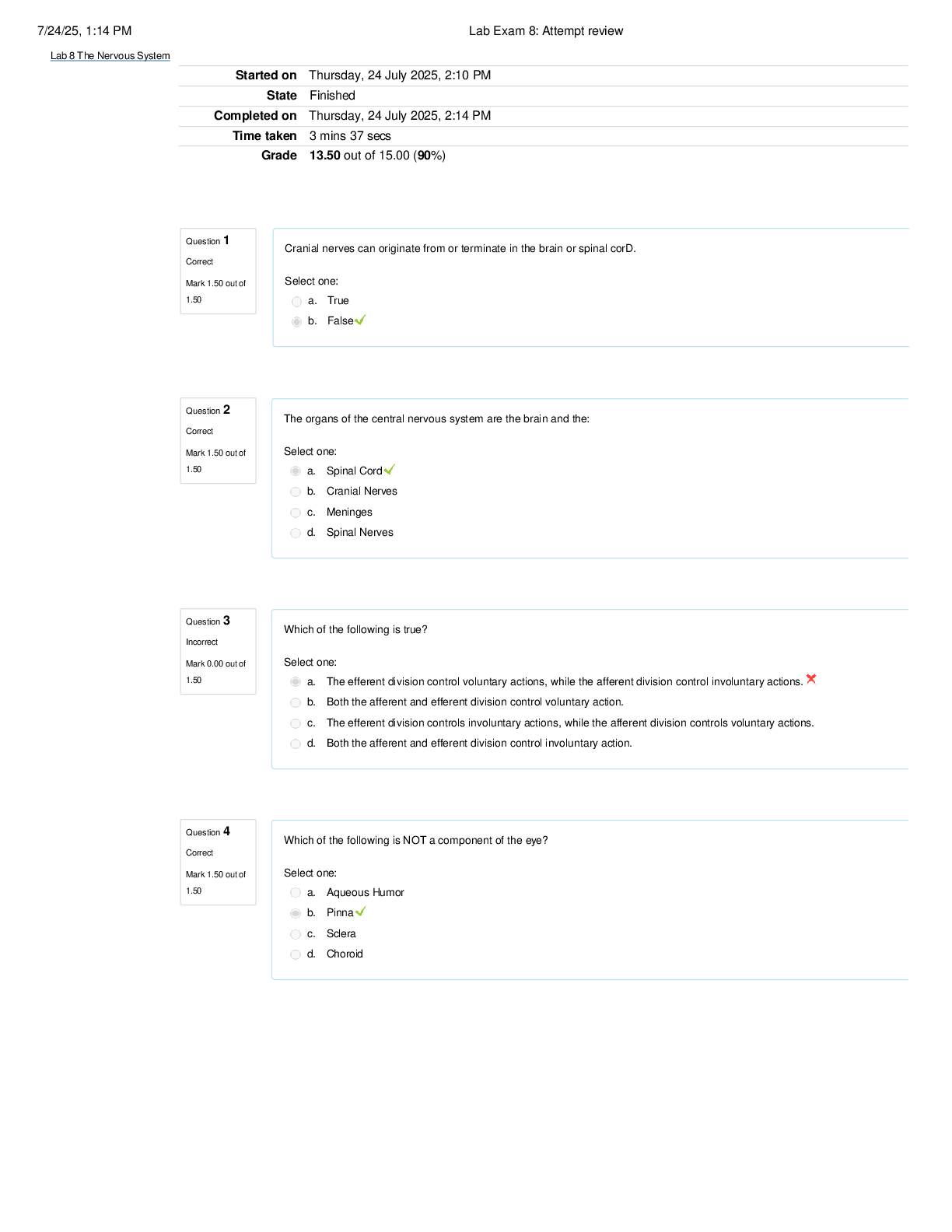
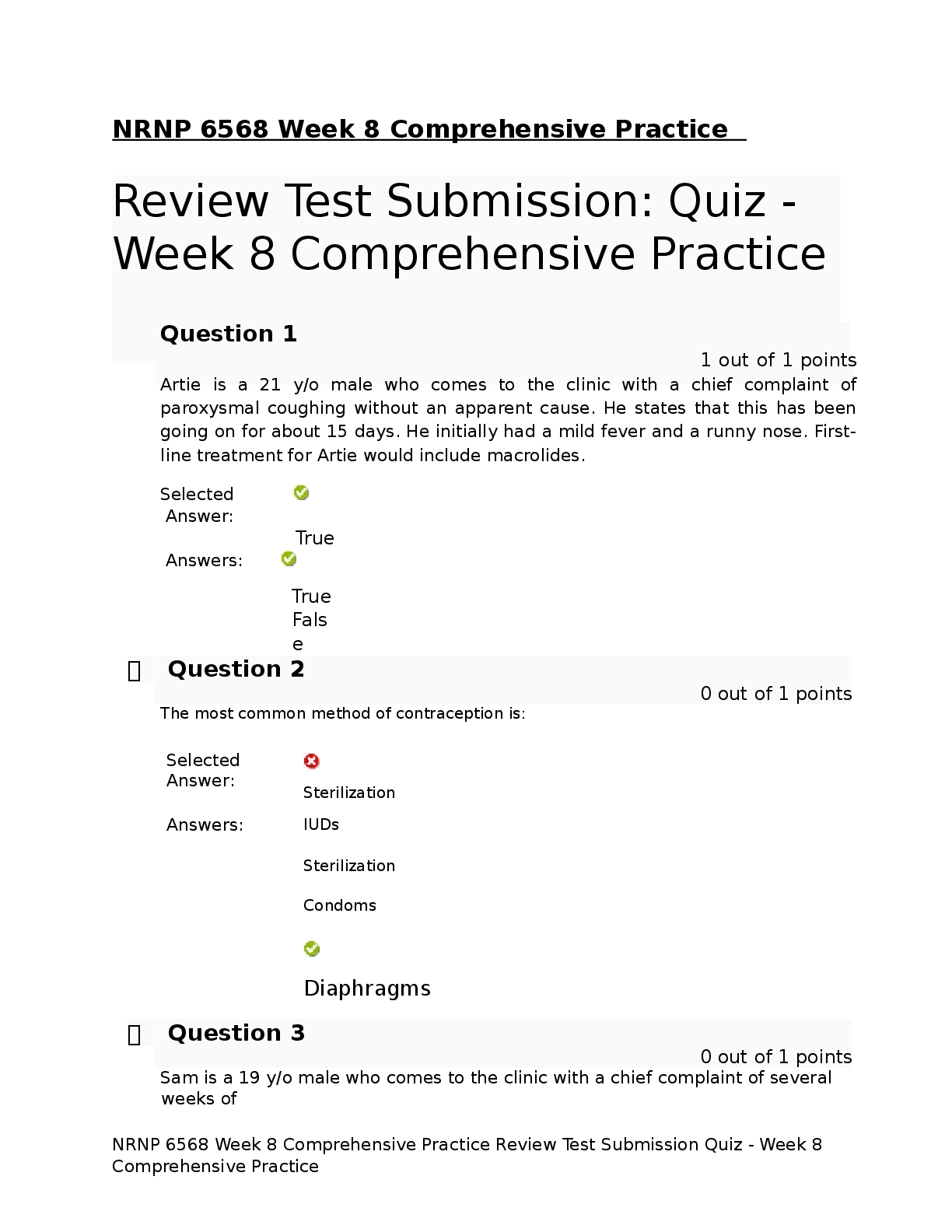
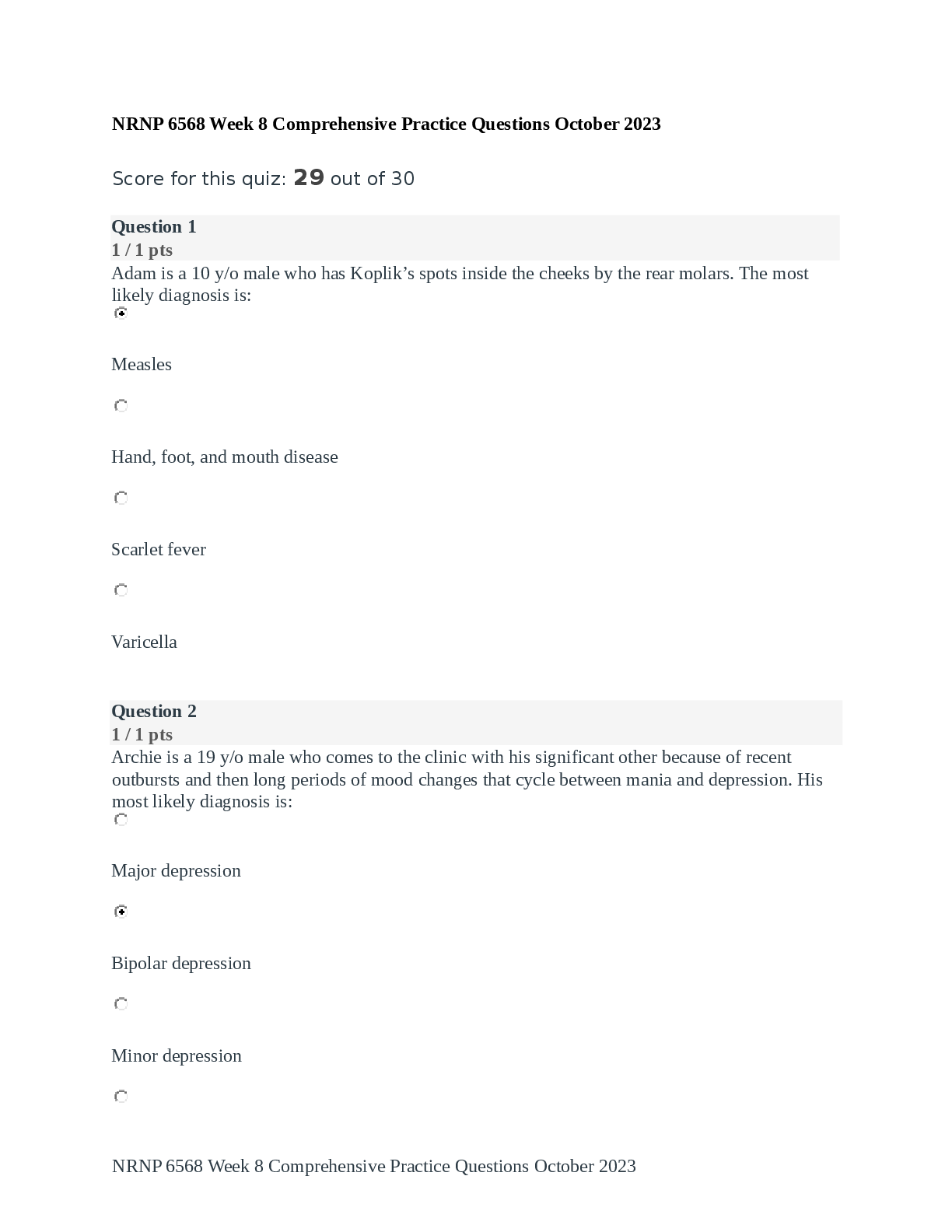
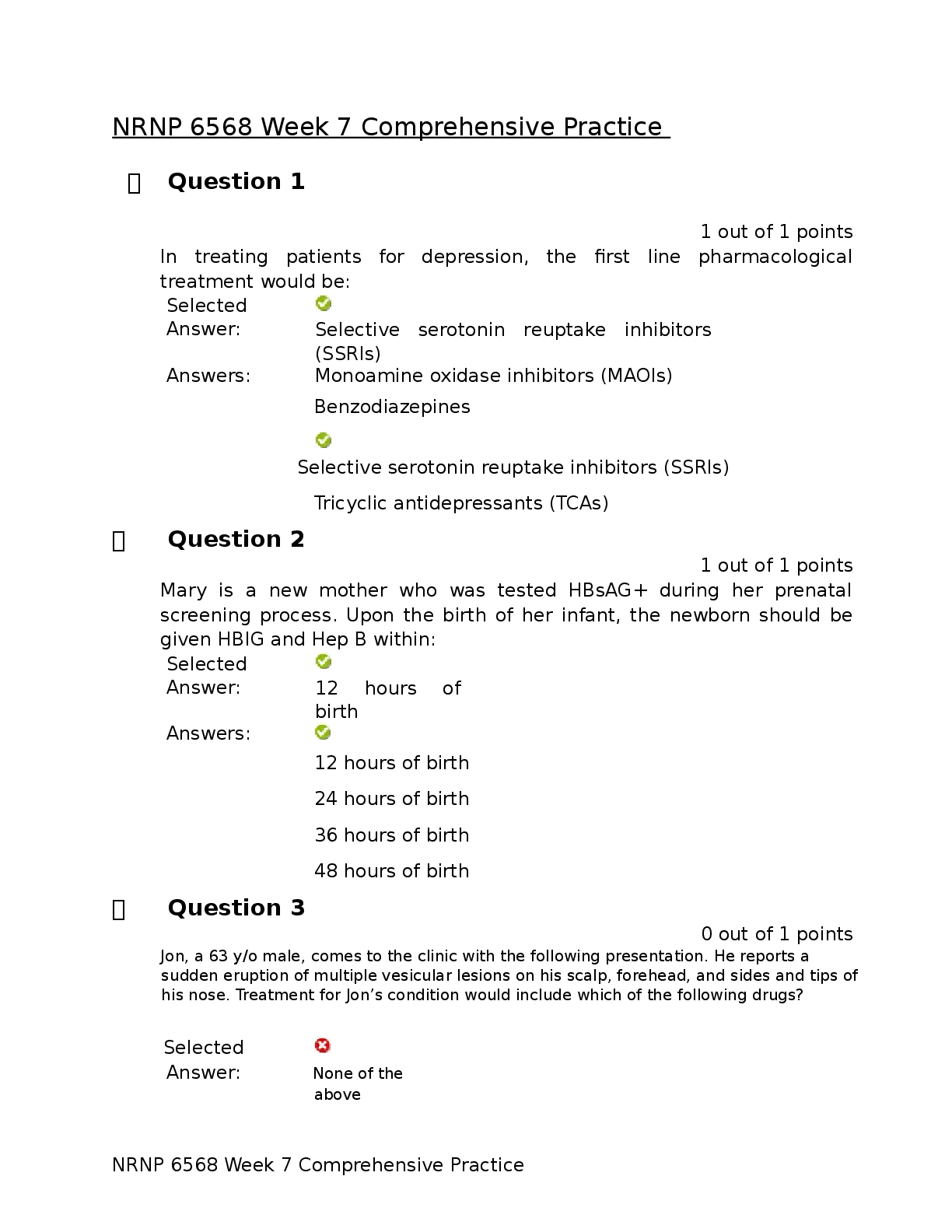
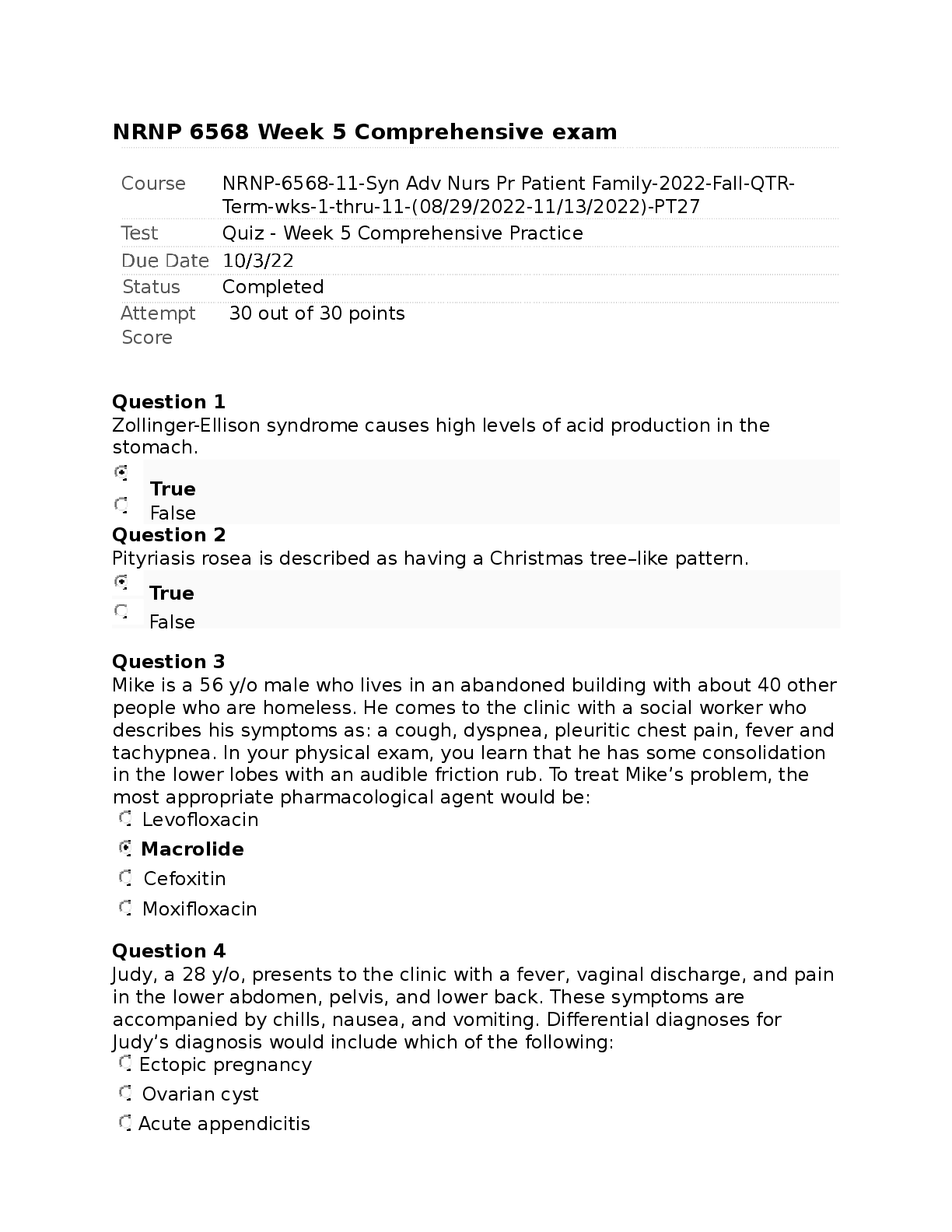
FRS 301 Final Exam | Questions and Answers (Complete Solutions) When an EnCase user double-clicks on a file within EnCase what determines the action that will result? A. The settings in the case fil ... e. B. The settings in the FileTypes.ini file. C. The setting in the evidence file. Search results are found in which of the following files? Select all that apply. A. The evidence file B. The configuration Searches.ini file C. The case file If cluster #3552 entry in the FAT table contains a value of ?? This would mean: A. The cluster is unallocated B. The cluster is the end of a file C. The cluster is allocated D. The cluster is marked bad The following GREP expression was typed in exactly as shown. Choose the answer(s) that would result. Bob@[a-z]+.com A. Bob@New zealand.com B. [email protected] C. [email protected] D. [email protected] You are an investigator and have encountered a computer that is running at the home of a suspect. The computer does not appear to be a part of a network. The operating system is Windows XP Home. No programs are visibly running. You should: A. Pull the plug from the back of the computer. B. Turn it off with the power button. C. Pull the plug from the wall. D. Shut it down with the start menu. A physical file size is: A. The total size in sectors of an allocated file. B. The total size of all the clusters used by the file measured in bytes. C. The total size in bytes of a logical file. D. The total size of the file including the ram slack in bytes. In Unicode, one printed character is composed of ____ bytes of data. A. 8 B. 4 C. 2 D. 1 If cluster number 10 in the FAT contains the number 55, this means: A. That cluster 10 is used and the file continues in cluster number 55. B. That the file starts in cluster number 55 and continues to cluster number 10. C. That there is a cross-linked file. D. The cluster number 55 is the end of an allocated file. How are the results of a signature analysis examined? A. By sorting on the category column in the Table view. B. By sorting on the signature column in the Table view. C. By sorting on the hash sets column in the Table view. D. By sorting on the hash library column in the Table view. The acronym ASCII stands for: A. American Standard Communication Information Index B. American Standard Code for Information Interchange C. Accepted Standard Code for Information Interchange D. Accepted Standard Communication Information Index The default export folder remains the same for all cases. A. True B. False The EnCase default export folder is: A. A case-specific setting that cannot be changed. B. A case-specific setting that can be changed. C. A global setting that can be changed. D. A global setting that cannot be changed. Hash libraries are commonly used to: A. Compare a file header to a file extension. B. Identify files that are already known to the user. C. Compare one hash set with another hash set. D. Verify the evidence file. Which is the proper formula for determining the size in bytes of a hard drive that uses cylinders (C), heads (H), and sectors (S) geometry? A. C X H + S B. C X H X S + 512 C. C X H X S X 512 D. C X H X S Within EnCase, clicking on Save on the toolbar affects what file(s)? A. All of the above B. The evidence files C. The open case file D. The configuration .ini files EnCase uses the _______________ to conduct a signature analysis. A. hash library B. file signature table C. both b and c D. file Viewers EnCase is able to read and examine which of the following file systems? A. NTFS B. EXT3 C. FAT D. HFS ROM is an acronym for: A. Read Open Memory B. Random Open Memory C. Read Only Memory D. Relative Open Memory If a floppy diskette is in the drive, the computer will always boot to that drive before any other device. A. False B. True A standard Windows 98 boot disk is acceptable for booting a suspect drive. A. True B. False Search terms are case sensitive by default. A. False B. True The following GREP expression was typed in exactly as shown. Choose the answer(s) that would result. Jan 1st, 2?0?00 A. Jan 1st , 1900 B. Jan 1st , 2100 C. Jan 1st , 2001 D. Jan 1st , 2000 An evidence file can be moved to another directory without changing the file verification. A. False B. True Pressing the power button on a computer that is running could have which of the following results? A. The computer will instantly shut off. B. The computer will go into stand-by mode. C. Nothing will happen. D. All of the above could happen. E. The operating system will shut down normally. How does EnCase verify that the evidence file contains an exact copy of the suspect hard drive? A. By means of a CRC value of the suspect hard drive compared to a CRC value of the data stored in the evidence file B. By means of an MD5 hash of the suspect hard drive compared to an MD5 hash of the data stored in the evidence file. C. By means of a CRC value of the evidence file itself. D. By means of an MD5 hash value of the evidence file itself. By default, EnCase will display the data from the end of a logical file, to the end of the cluster, in what color: A. Red B. Red on black C. Black on red D. Black A SCSI drive is pinned as a master when it is: A. The only drive on the computer. B. The primary of two drives connected to one cable. C. Whenever another drive is on the same cable and is pinned as a slave. D. A SCSI drive is not pinned as a master. The following GREP expression was typed in exactly as shown. Choose the answer(s) that would result. [^a-z]Tom[^a-z] A. Tomato B. Tom C. Toms D. Stomp This question addresses the EnCase for Windows search process. If a target word is within a logical file, and it begins in cluster 10 and ends in cluster 15 (the word is fragmented), the search: A. Will not find it unlessile slack is checked on the search dialog box. B. Will find it because EnCase performs a logical search. C. Will not find it because EnCase performs a physical search only. D. Will not find it because the letters of the keyword are not contiguous. An evidence file was archived onto five CD-Rom disks with the third file segment on disk number three. Can the contents of the third file segment be verified by itself while still on the CD? A. No. Archived files are compressed and cannot be verified until un-archived. B. No. All file segments must be put back together. C. Yes. Any segment of an evidence file can be verified through re-computing and comparing the CRCs, even if it is on a CD. D. No. EnCase cannot verify files on CDs. You are a computer forensic examiner tasked with determining what evidence is on a seized computer. On what part of the computer system will you find data of evidentiary value? A. Microprocessor or CPU B. USB controller C. Hard drive D. PCI expansion slots You are a computer forensic examiner explaining how computers store and access the data you recovered as evidence during your examination. The evidence was a log file and was recovered as an artifact of user activity on the ____________, which was stored on the _____________, contained within a ____________ on the media. A. partition, operating system, file system B. operating system, file system, partition C. file system, operating system, hard drive D. operating system, partition, file system You are a computer forensic examiner investigating a seized computer. You recovered a document containing potential evidence. EnCase reports the file system on the forensic image of the hard drive is FAT (File Allocation Table). What information about the document file can be found in the FAT on the media? (Choose all that apply.) A. Name of the file B. Date and time stamps of the file C. Starting cluster of the file D. Fragmentation of the file E. Ownership of the file You are a computer forensic examiner investigating media on a seized computer. You recovered a document containing potential evidence. EnCase reports the file system on the forensic image of the hard drive is NTFS (New Technology File System). What information about the document file can be found in the NTFS master file table on the media? (Choose all that apply.) A. Name of the file B. Date and time stamps of the file C. Starting cluster of the file D. Fragmentation of the file E. Ownership of the file You are preparing to lead a team to serve a search warrant on a business suspected of committing large-scale consumer fraud. Ideally, you would you assign which tasks to search team members? (Choose all that apply.) A. Photographer B. Search and seizure specialists C. Recorder D. Digital evidence search and seizure specialists You are a computer forensic examiner at a scene and have determined you will seize a Linux server, which according to your source of information contains the database records for the company under investigation for fraud. What is the best practice for "taking down" the server for collection? A. Photograph the screen and note any running programs or messages, and so on, and use the normal shutdown procedure. B. Photograph the screen and note any running programs or messages, and so on, and pull the plug from the wall. C. Photograph the screen and note any running programs or messages, and so on, and pull the plug from the rear of the computer. D. Photograph the screen and note any running programs or messages, and so on, and ask the user at the scene to shut down the server. You are a computer forensic examiner at a scene and are authorized to seize only media that can be determined to have evidence related to the investigation. What options do you have to determine whether evidence is present before seizure and a full forensic examination? (Choose all that apply.) A. Use a DOS boot floppy or CD to boot the machine, and browse through the directory for evidence. B. Use an EnCase boot floppy or CD to boot the machine into Linux, and use LinEn to preview the hard drive through a crossover cable with EnCase for Windows. C. Remove the subject hard drive from the machine, and preview the hard drive in EnCase for Windows with a hardware write blocker such as FastBloc. D. Use an EnCase boot floppy or CD to boot the machine into DOS, and use EnCase for DOS to preview the hard drive through a crossover cable with EnCase for Windows. You are a computer forensic examiner at a scene and have determined you will need to image a hard drive in a workstation while on-site. What are your options for creating a forensically sound image of the hard drive? (Choose all that apply.) A. Use a DOS boot floppy or CD to boot the machine, and use EnCase for DOS to image the subject hard drive to a second hard drive attached to the machine. B. Use a forensically sound Linux boot CD to boot the machine into Linux, and use LinEn to image the subject hard drive to a second hard drive attached to the machine. C. Remove the subject hard drive from the machine, and image the hard drive in EnCase for Windows with a hardware write blocker such as FastBloc. D. Use an EnCase boot floppy or CD to boot the machine into DOS, and use EnCase for DOS to image the hard drive through a crossover cable with EnCase for Windows. You are a computer forensic examiner and have imaged a hard drive on site. Before you leave the scene, you want to ensure the image completely verifies as an exact forensic duplicate of the original. To verify the EnCase evidence file containing the image, you should do which of the following? A. Use a hex editor to compare a sample of sectors in the EnCase evidence file with that of the original. B. Load the EnCase evidence files into EnCase for Windows, and after the verification is more than halfway completed, cancel the verification and spot-check the results for errors. C. Load the EnCase evidence files into EnCase for DOS, and verify the hash of those files. D. Load the EnCase evidence files into EnCase for Windows, allow the verification process to finish, and then check the results for complete verification. You are a computer forensic examiner and need to verify the integrity of an EnCase evidence file. To completely verify the file's integrity, which of the following must be true? A. The MD5 hash value must verify. B. The CRC values and the MD5 hash value both must verify. C. Either the CRC or MD5 hash values must verify. D. The CRC values must verify. You are a computer forensic examiner and need to determine what files are contained within a folder called Business documents. What EnCase pane will you use to view the names of the files in the folder? A. Tree pane B. Table pane C. View pane D. Filter pane You are a computer forensic examiner and need to view the contents of a file contained within a folder called Business documents. What EnCase pane will you use to view the contents of the file? A. Tree pane B. Table pane C. View pane D. Filter pane You are a computer forensic examiner and are viewing a file in an EnCase evidence file. With your cursor, you have selected one character in the file. What binary term is used for the amount of data that represents a single character? A. A byte B. A nibble C. A bit D. A word You are a computer forensic examiner and need to search for the name of a suspect in an EnCase evidence file. You enter the name of the suspect into the EnCase keyword interface as John Doe. What search hits will be found with this search term with the default settings? (Choose all that apply.) A. john doe B. John D. C. John Doe D. John.Doe You are a computer forensic examiner and need to determine whether any Microsoft Office documents have been renamed with image extensions to obscure their presence. What EnCase process would you use to find such files? A. File signature analysis B. Recover Folders feature C. File content search D. File hash analysis You are a computer forensic examiner and want to reduce the number of files required for examination by identifying and filtering out known good or system files. What EnCase process would you use to identify such files? A. File signature analysis B. Recover Folders feature C. File content search D. File hash analysis You are a computer forensic examiner and want to determine whether a user has opened or double-clicked a file. What folder would you look in for an operating system artifact for this user activity? A. Temp B. Recent C. Cookies D. Desktop You are a computer forensic examiner and want to determine when a user deleted a file contained in a Windows XP Recycle Bin. In what file is the date and time information about the file deletion contained? A. index.dat B. Link file C. INFO2 D. deleted.ini You are a computer forensic examiner and want to determine how many times a program was executed. Where would you find information? A. Temp folder B. Registry C. Recycle Bin D. Program Files You are a computer forensic examiner and want to examine any email sent and received by the user of the computer system under investigation. What email formats are supported by EnCase? (Choose all that apply.) A. Outlook B. Outlook Express C. America Online D. Hotmail E. Yahoo! F. Mozilla Thunderbird G. All above What is the definition of a CPU? A. The physical computer case that contains all its internal components B. The computer's internal hard drive C. A part of the computer whose function is to perform data processing D. A part of the computer that stores and manages memory What is the BIOS? A. BIOS stands for Basic Input Output System and is a combination of low-level software and drivers that function as the interface, intermediary, or layer between a computer's hardware and its operating system. B. BIOS stands for Bootstrap Initialization Operating System and is a combination of lowlevel software and drivers that function as the interface, intermediary, or layer between a computer's hardware and its operating system. C. BIOS stands for Boot-level Input Output System and is a combination of low-level software and drivers that function as the interface, intermediary, or layer between a computer's hardware and its operating system. D. BIOS stands for Boot Initialization Operating System and is a combination of low-level software and drivers that function as the interface, intermediary, or layer between a computer's hardware and its operating system. Is the information stored on a computer's ROM chip lost during a proper shutdown? A. Yes B. No Is the information contained on a computer's RAM chip accessible after a proper shutdown? A. Yes B. No Can information stored in the BIOS ever change? A. Yes B. No What is the purpose or function of a computer's ROM chip? A. Long-term or permanent storage of information and instructions B. Temporary storage area to run applications C. Permanent storage area for programs and files D. A portable storage device Information contained in RAM memory (system's main memory), which is located on the motherboard, is _________. A. volatile B. nonvolatile What is the maximum number of drive letters assigned to hard drive(s) partitions on a system? A. 4 B. 16 [Show More]
Last updated: 1 year ago
Preview 1 out of 40 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$18.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jul 21, 2024
Number of pages
40
Written in
All
Additional information
This document has been written for:
Uploaded
Jul 21, 2024
Downloads
0
Views
50