Computer Architecture > EXAM > FedVTE Cyber Risk Management for Technicians Questions and Answers 100% Pass (All)
FedVTE Cyber Risk Management for Technicians Questions and Answers 100% Pass
Document Content and Description Below
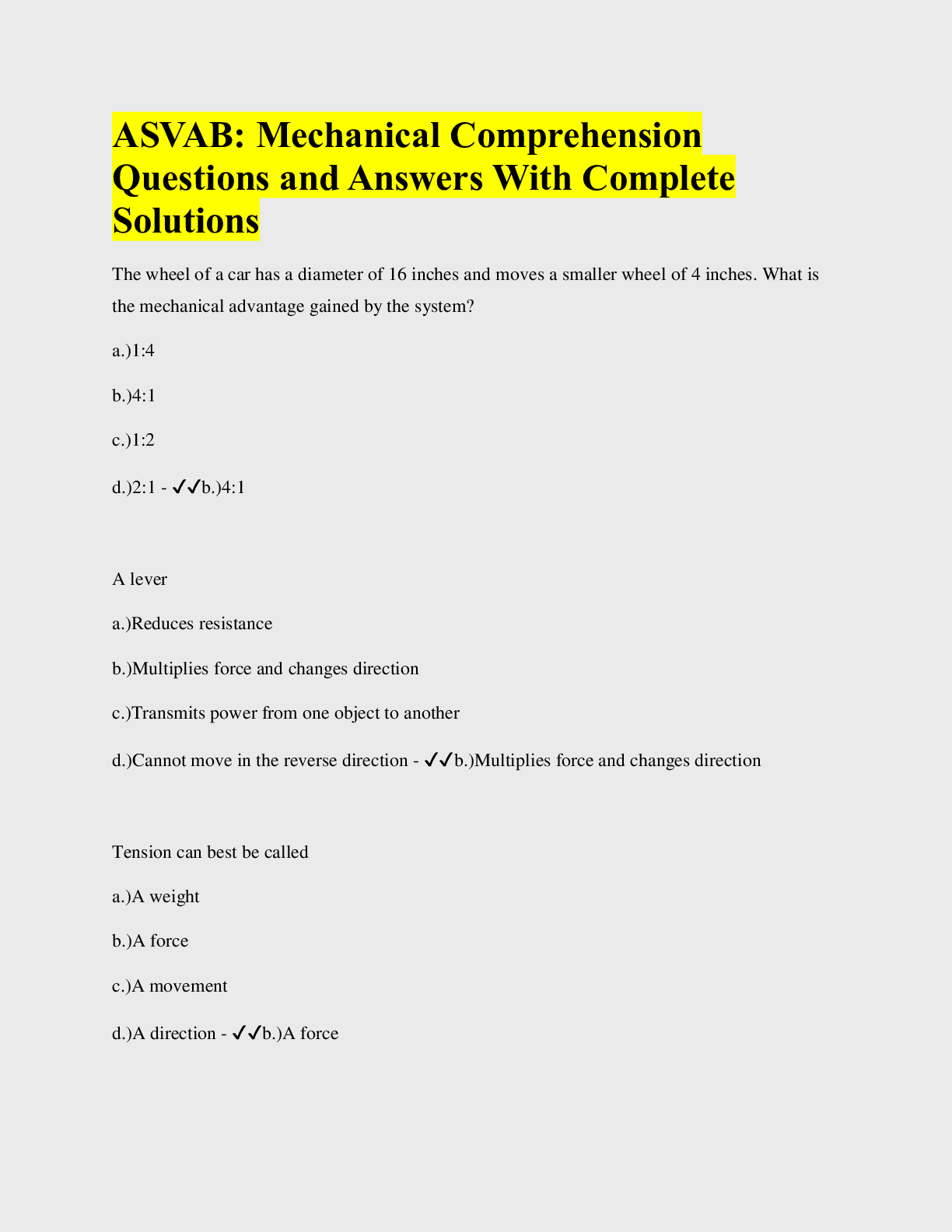
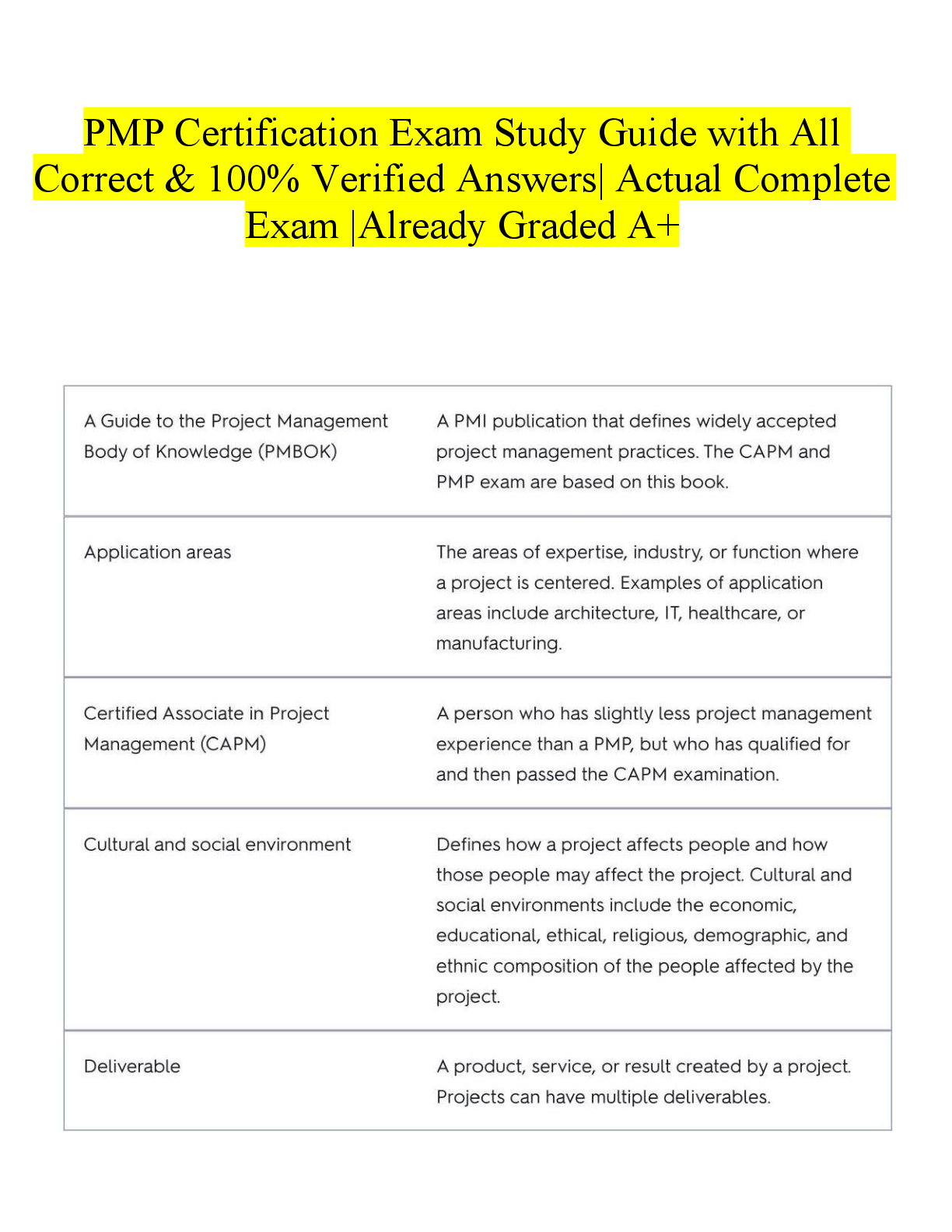
In order to automate host characteristic monitoring you can compare baselines and snapshots with syslog. ✔✔False The following should be taken into account when accepting the residual risk inher ... ent in the project. ✔✔All of the above What is the high water mark for an information system? ✔✔Highest Potential Impact value assigned to each Security Objective (AIC) for all Security Categories resident on the system and the overall classification of the system. Which of the following describes NetScan Tools Pro? ✔✔B. A powerful command line packet analyzer C. A tool that provides advanced network trace routing D. A collection of Internet information gathering and network troubleshooting utilities FIPS 200 is: ✔✔A short document that describes the minimum security requirements for information and information systemsWhich risk comes from a failure of the controls to properly mitigate risk? ✔✔A. Inherent risk C. Control Risk D. All of the above Open Source Security (OSSEC) is what? ✔✔A host based security system that monitors for changes What tool would be best to automatically detect your network and construct a complete and easy to view network map? ✔✔LANsurveyor Which NIST special publication is a guide for Applying the Risk Management Framework to Federal Information Systems: A Security Life Cycle Approach? ✔✔NIST SP 800 37 Which of the following is a part of the Examine Method? ✔✔Inspecting the physical security measures If the cost of controls exceeds the benefit the organization may choose to accept the risk instead. ✔✔True Which of the following families of controls belongs to the technical class of controls? ✔✔Identification and AuthenticationWhich tier of Risk Management is associated with Enterprise Architecture? ✔✔Tier 2 Mission (Business Process) In NIST SP 800 53 the security control structure consists of all the following components except for: ✔✔All of these are in the security control structure: - Priority and baseline allocation - Supplemental guidance - Control enhancements Kismet is different from a normal network sniffer such as Wireshark or tcpdump because it separates and identifies different wireless networks in the area. ✔✔True What is the order of the Change Control Process? ✔✔A. Request : Approval : Build : Impact Assessment : If successful Implement B. Request : Impact Assessment : Approval : Build and or Test : Implement D. Request : Impact Assessment : Build and or Test : Approval : Implement The threat source is highly motivated and sufficiently capable and controls to prevent the vulnerability from being exercised are ineffective. Which likelihood rating does this describe? ✔✔HighWhich of the following is not part of the process for assessing security controls according to NIST SP 800 53A 1? ✔✔A. Study C. Conduct D. Analyze Which step of a risk assessment uses the history of system attacks? ✔✔Step 2: Threat Identification In risk management people and information and technology are examples of? ✔✔Assets What type of analysis involves using scales to suit circumstances and allows for quick identification of potential risks as well as vulnerable assets and resources? ✔✔B. Audit Analysis C. Qualitative Analysis D. Cost/benefit analysis NIST SP 800 30 defines risk as a function of the likelihood of a given threat source exercising a particular potential vulnerability and the resulting impact of that adverse event on the organization. ✔✔True [Show More]
Last updated: 1 year ago
Preview 3 out of 5 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$6.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 03, 2024
Number of pages
5
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 03, 2024
Downloads
0
Views
64