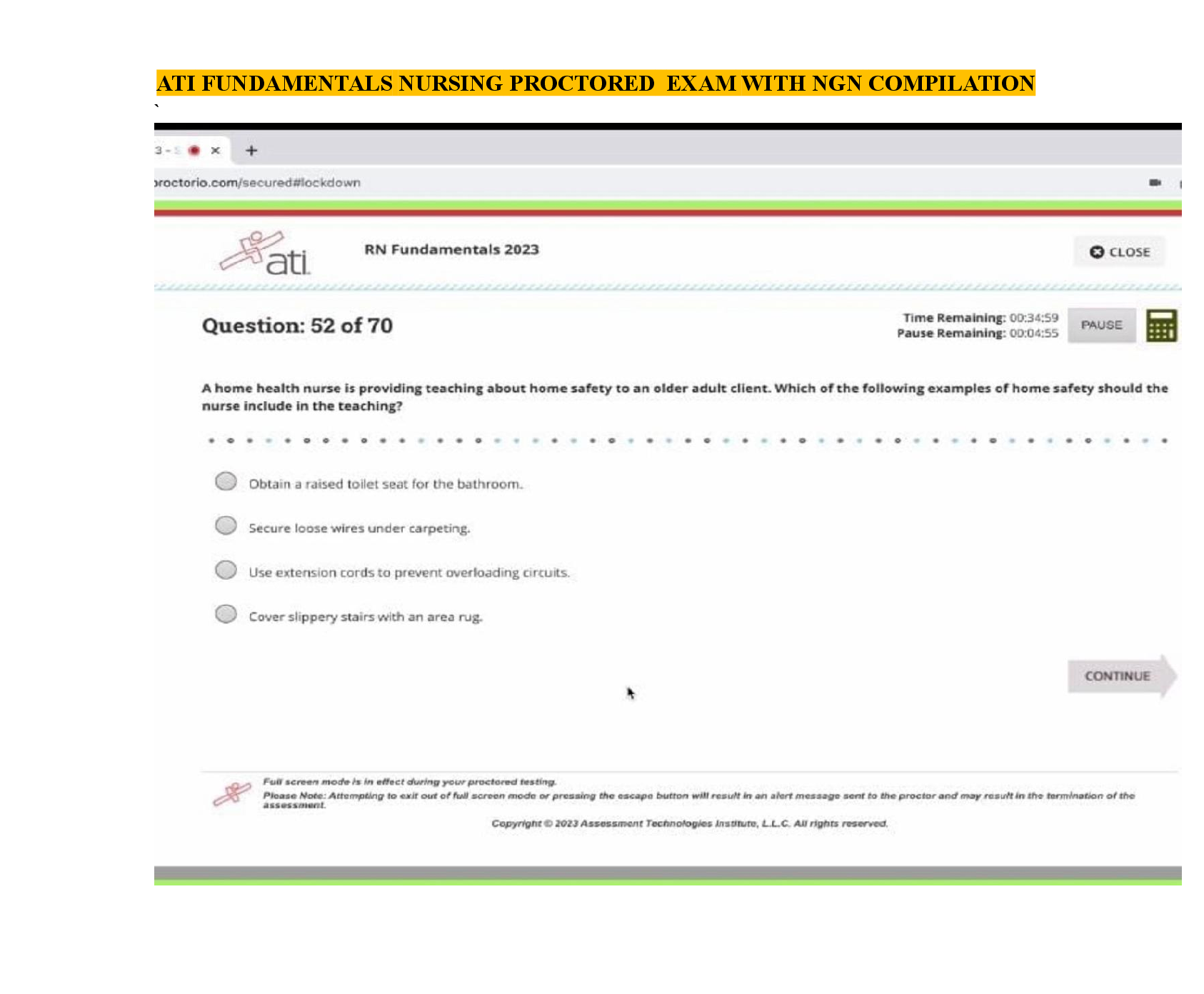
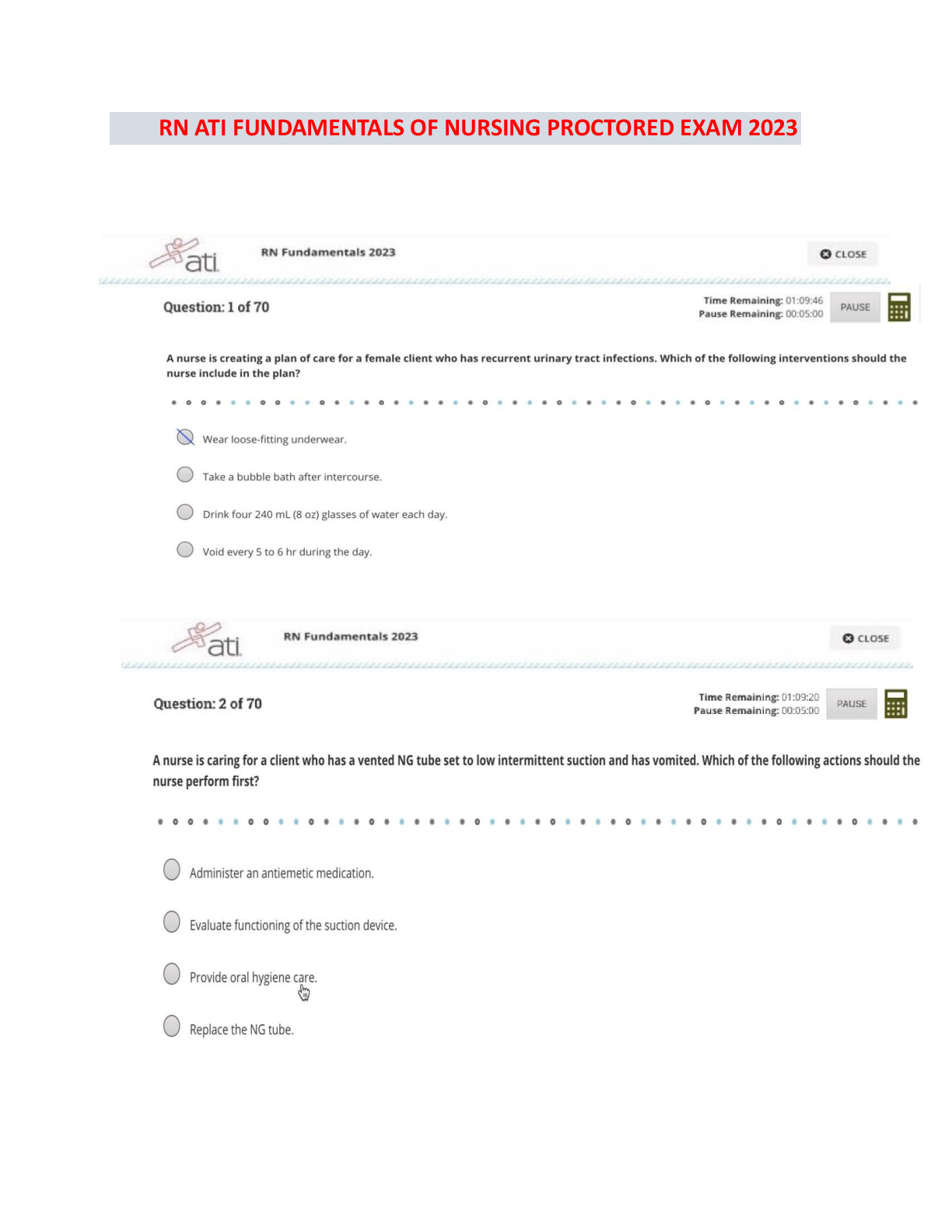
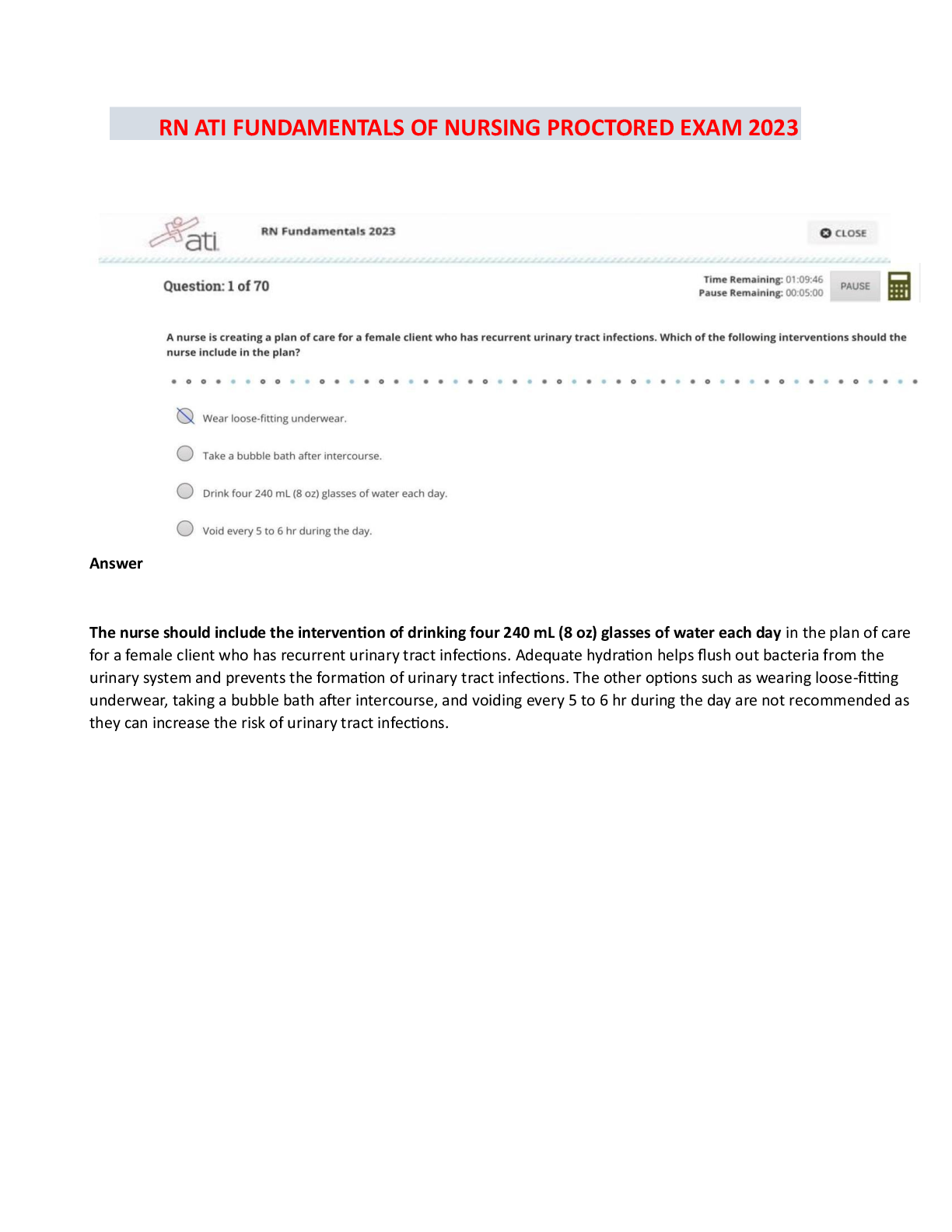
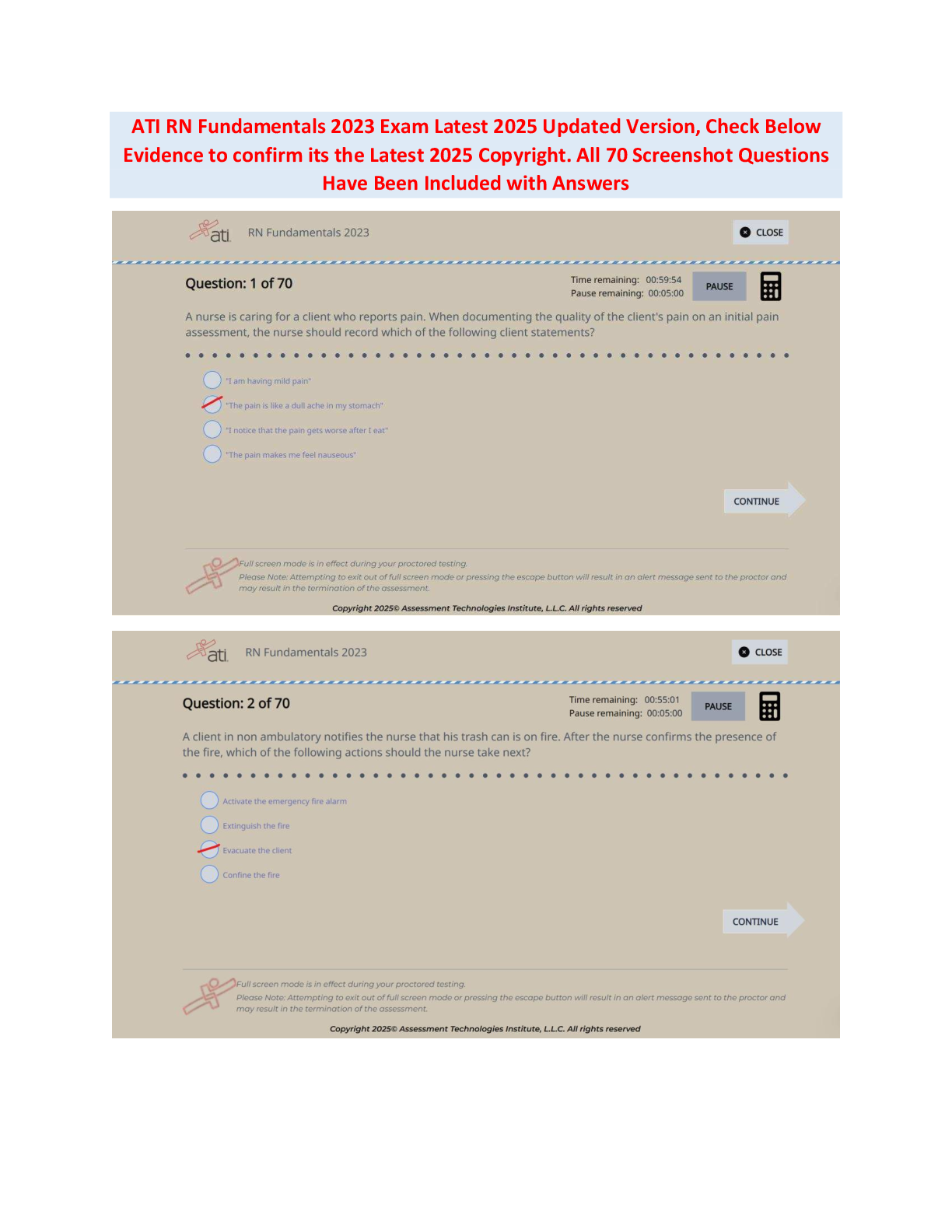
Computer Architecture > EXAM > FedVTE - Windows Operating System Security Questions and Answers Rated A (All)
FedVTE - Windows Operating System Security Questions and Answers Rated A
Document Content and Description Below
Which value in the PowerShell "execution policy" allows loading of all configuration files and scripts? ✔✔Unrestricted Which Active Directory Certificate Service (AD CS) server role allows route ... rs and other network devices that do not have a domain account to obtain certificates? ✔✔B. Online Responder D. Network Device Enrollment Service Which key command in PowerShell shows an objects methods and properties? ✔✔All of the above Which one of the following steps is not part of securing the Microsoft patch process? ✔✔Apply patches while on the road Of the following methods which one is a tool that centrally manages and configures Windows operating systems and applications and user settings? ✔✔Group Policy In which one of the Social Engineering stages would you establish credibility? ✔✔Relationship DevelopmentMicrosoft Security Configuration Wizard is a management tool that is based upon machine roles such as a file server a print server a domain controller etc. ✔✔True Which option is best for a server to connect to a network? ✔✔Wired Authenticode is a means of code signing that allows users to verify the source and author of the signed software. ✔✔False Which type of permissions are created by default on non child objects or based by user assignment? ✔✔Explicit Which one of the following could be categorized as a misconfiguration? ✔✔All of the above Which one of the following is a Windows Firewall advantage? ✔✔B. Provides a very granular customization of applications C. Can be configured with Netsh or PowerShell What are the four service startup types? ✔✔Manual; Automatic; Automatic (Delayed); Disabled Which method can start PowerShell in Windows 8? ✔✔Charm > Search > type PowerShell > click Windows PowerShellThe Windows Security Configuration Wizard can be used to configure the Windows Firewall with advanced security support. ✔✔True Many current network security tools such as Firewalls and Intrusion Detection Systems and Intrusion Prevention Systems are not 100% compatible with IPv6. ✔✔True Which one of the following creates and manages and exports (for deployment) security policies across multiple Windows operating systems roles and Microsoft applications? ✔✔Microsoft Security Compliance Manager In a Hardening Process which method uses plaintext files containing software and driver installation configuration settings? ✔✔A. Security Templates D. Group Policy Security Templates provide a standardized way to organize and express and measure security related information. ✔✔False Network Access Protection (NAP) is a Windows feature that provides which one of the following? ✔✔Automatic Remediation Which two of the following categories of monitoring are in the Action Center formerly known as the Windows Security Center? ✔✔Security and MaintenanceIn a Kerberos Authentication process which one of the following sends a Ticket Granting Ticket secret key and a session key as a function? ✔✔AS_RESPONSE User Account Control (UAC) was introduced in Windows XP and Server 2003. ✔✔False Which Internet Protocol Security (IPsec) protocol provides confidentiality by encrypting data? ✔✔Encapsulating Security Payload (ESP) CVE is short for Critical Vulnerabilities and Exploits. ✔✔False During which step of Microsofts recommended Update Management Process would an update be tested? ✔✔Evaluate and Plan Which description best defines a Hotfix? ✔✔An update to fix a very specific issue In which multi tasking mode can an operating system take control of the processor without consent from the task? ✔✔Preemptive multi-tasking A Virtual Private Network allows two systems to connect over a public network and have the assurance of which of the following? ✔✔All of the above Which one of the following default rights can be performed by a member of the Windows User Group? ✔✔Increase a process working setWhich vulnerability allows remote attackers to execute arbitrary code via a crafted TrueType Font (TTF) file? ✔✔Kernel Mode Driver - CVE-2012-4786 An API is a set of functions that an application can call to allow the application to operate within Windows. ✔✔True Which one of the following is a benefit of Dynamic Access Control? ✔✔All of the above Which built-in Windows security feature prevents users from loading unauthorized and unapproved applications? ✔✔Windows AppLocker Which Dynamic Access Control capability allows for "safety net" policies? ✔✔Centralize Access Policies PowerShell is built on top of the .Net CRL and .Net Framework. ✔✔True Which method scans systems to identify common security misconfigurations and missing security updates? ✔✔Microsoft Baseline Security Analyzer In the Windows Registry what is a collection of discrete files called? ✔✔HivesA logical Patch Management process is a one-time process that businesses should establish to ensure success. ✔✔False Which Network Access Protection (NAP) client collects and maintains a system health status? ✔✔NAP Agent Which solution is best to avoid downloading an untrusted patch? ✔✔All of the above Which one of the following can be audited using the Windows Security Auditing feature? ✔✔All of the above Which one of the following can be managed through group policies (GPO)? ✔✔All of the above Which one of the following DLL file handles the memory management? ✔✔Kernel32.dll Which one of the following is required for Windows BitLocker configuration? ✔✔Trusted Platform Module (TPM) Which type of attacker has actions that are considered noble by the attacker but could cause more harm than good? ✔✔Gray Hat In a PowerShell environment the WhatIf parameter allows PowerShell users to test the command before actually executing. ✔✔TrueWhich one of the following is a cmdlet that is used to gather computer information? ✔✔GetWmiObject Which execution mode has unrestricted access to the underlying [Show More]
Last updated: 1 year ago
Preview 3 out of 7 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$7.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 03, 2024
Number of pages
7
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 03, 2024
Downloads
0
Views
49