Information Technology > EXAM > ITSS 4370 Final Exam | Questions and Answers (All)
ITSS 4370 Final Exam | Questions and Answers
Document Content and Description Below
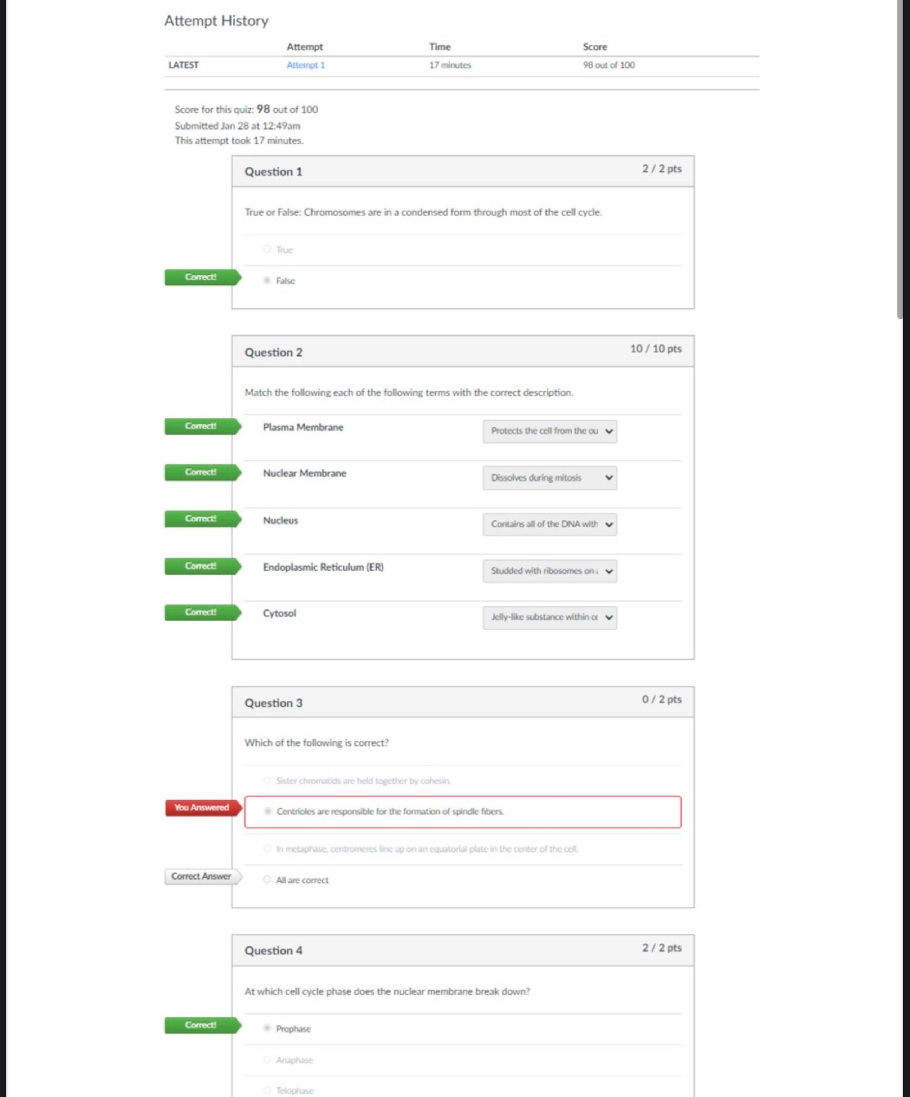
ITSS 4370 Final Exam | Questions and Answers Which of the following functions is NOT a key component in an organization's disaster recovery efforts? Disaster reaction Network equipment is usually n ... ot included as part of the configuration management because there is little need to document network hardware and network configurations False IT controls are the BEST detection method to limit fraud duration and loss TRUE What should the relationship be between business continuity policies and corporate policies? They should be strategically aligned One justification for choosing a hybrid cloud deployment model is the ability to support cloud bursting. What is cloud bursting? Spilling over to the public cloud to deal with spikes in demand Matching: Weakness that may be exploited Vulnerability Matching: Preventative measure Control Matching: Potential for exposure Threat Matching: An occurrence that actually or potentially results in adverse consequences to an information system or the information that the system stores, processes, or transmits, and that may require a response action to mitigate the consequences Incident Matching: Human originated penetration or penetration attempt Attack Matching: Actual harm or possible harm Exposure Which of these are methods for measuring availability? Percent uptime = (Actual uptime) / (Scheduled uptime) Measure uptime in terms meaningful to users Quantify amount of downtime Redundancy as a method for maximizing availability deals with ______ Eliminating, as much as possible, any single point of failure that could disrupt service availability Which of the following is NOT one of the three common service models in cloud computing? Broadband as a Service (BaaS) Defense in depth refers to _________ Establishing sufficient security controls and safeguards so that an intruder faces multiple layers of controls There are several approaches that can be taken to maximize availability - the seven R's of high availability. Which of the following is NOT one of these seven approaches? Recognition The rule of nines refers to Measurement of availability as a percentage of uptime Matching: It should be clear who accessed or changed information and when they did Accountability Matching: Information should only be provided to those who need access to it Confidentiality Matching: Information should be provided to users when they need it Availability Matching: Information should not be altered or changed unexpectedly Integrity The principal purpose of Business Impact Analysis is to ______________ Assess the impact that various risks or attacks can have on the organization's Data tiering determines where and how data is stored. Which of the following criteria may be used in determining data tiering needs? Performance Cost Availability Recovery or retrieval requirements Which of the following are key functions of the NIST Cybersecurity Framework? [Show More]
Last updated: 1 year ago
Preview 2 out of 4 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

ITSS 4370 EXAM 2 AND FINAL EXAM BUNDLE
ITSS 4370 EXAM 2 AND FINAL EXAM BUNDLE
By Nurse Henny 1 year ago
$12
2
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Dec 05, 2024
Number of pages
4
Written in
All
Additional information
This document has been written for:
Uploaded
Dec 05, 2024
Downloads
0
Views
25