Computer Science > EXAM > ITN 276 Midterm Exam | Verified with 100% Correct Answers (All)
ITN 276 Midterm Exam | Verified with 100% Correct Answers
Document Content and Description Below
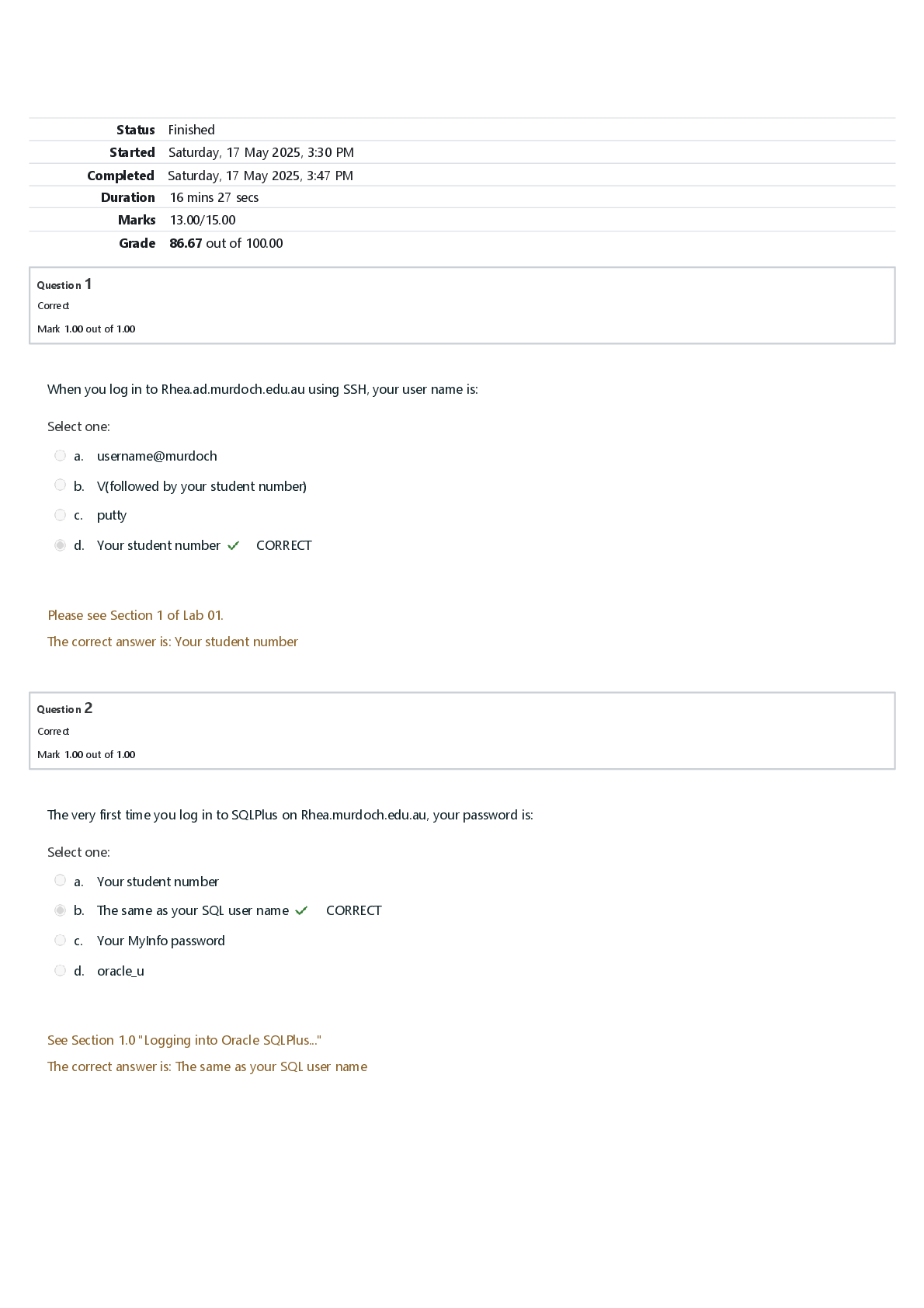
ITN 276 Midterm Exam | Verified with 100% Correct Answers Which of the following options is a common standard file format for executables, object code, and shared libraries for UNIX-based systems? ... ELF Documentary evidence is Written contracts, sales slips, letters, or affidavits (sworn statements) What term is used to describe a broad category of crime that can encompass many different activities, but essentially, any attempt to gain financial reward through deception? Fraud What name is given to any use of another person's identity? identity theft Which of the following is the definition of the Daubert Standard? TheDaubert Standard dictates that only methods and tools widely accepted in the scientific community can be used in court. The most common protocol used at OSI Layer 3 is IP The most common computer hard drives today are SATA Which of the following is the definition of anti-forensics? The actions that perpetrators take to conceal their locations, activities, or identities The __________ contains many provisions about recordkeeping and destruction of electronic records relating to the management and operation of publicly held companies. Sarbanes-Oxley Act of 2002 Data about information, such as disk partition structures, and file tables, is called what? Metadata China Eagle Union is a Chinese cyberterrorism group The __________ was passed to improve the security and privacy of sensitive information in federal computer systems. The law requires the establishment of minimum acceptable security practices, creation of computer security plans, and training of system users or owners of facilities that house sensitive information Computer Security Act of 1987 Recent years have seen the growth of more targeted phishing attacks, rather than those aimed at the general public. These targeted attacks are known as spear phishing is information that helps explain other evidence Demonstrative evidence The real difference between a mediocre investigator and a star investigator is the evidence analysis __________is/are the cyber-equivalent of vandalism. DoS attacks What is meant by three-way handshake The process of connecting to a server that involves three packets being exchanged A SYN flood is an example of what? DoS attack Before you can do any forensic analysis or examination, you have to do what? collect the evidence What is meant by distributed denial of service (DDoS) attack? an attack in which the attacker seeks to infect several machines, and use those machines to overwhelm the target system to achieve a denial of service Suspects often overwhelm forensic analysts with false positives and false leads. This is referred to as__________. data fabrication What name is given to the process of searching memory in real time, typically for working with compromised hosts or to identify system abuse? live system forensics The use of electronic communications to harass or threaten another person is the definition of Cyberstalking A(n) __________attack is designed to render the target unreachable by legitimate users, not to provide the attacker access to the site denial of service Computer forensics begins with a thorough understanding of what? computer hardware Which of the following was the first file system created specifically for Linux? EFS The __________is the continuity of control of evidence that makes it possible to account for all that has happened to evidence between its original collection and its appearance in court, preferably unaltered. chain of custody Verity, ICU, and WorkTime are all examples of spyware software A(n) __________ is the concatenation of the IP address and the TCP or UDP port number, and should be unique to a connection at any single moment in time. socket number The American Heritage Dictionary defines __________as "the use of science and technology to investigate and establish facts in criminal or civil courts of law." Forensics What is meant by chain of custody? The continuity of control of evidence that makes it possible to account for all that has happened to evidence between its original collection and its appearance in court, preferably unaltered. __________ refers to phishing with a specific, high-value target in mind. For example, the attacker may target the CIO of a bank. Whaling The __________ protects journalists from being required to turn over to law enforcement any work product and documentary material, including sources, before it is disseminated to the public Privacy Protection Act of 1980 If the crime being investigated is identity theft, then the first thing the investigator should be looking for is Spyware on the victim's machine The__________ is a federal wiretap law for traditional wired telephony that was expanded to include wireless, voice over packet, and other forms of electronic communications, including signaling traffic and metadata. Communications Assistance to Law Enforcement Act of 1994 The process of connecting to a server that involves three packets being exchanged is the definition of: Three-way handshake What term is used to describe the process of acquiring and analyzing information stored on physical storage media, such as computer hard drives or smartphones? disk forensics What term is used to describe an attack designed to overwhelm the target system so it can no longer reply to legitimate requests for connection? denial of service (DoS) attack __________is information that has been processed and assembled to be relevant to an investigation, and that supports a specific finding or determination Digital evidence One must be able to show the whereabouts and custody of the evidence, how it was handled and stored and by whom, from the time the evidence is first seized by a law enforcement officer or civilian investigator until the moment it is shown in court. This is referred to as what? Chain of custody The unused space between the logical end of file and the physical end of file is known as File lack This forensic certification is open to both the public and private sectors and is specific to the use and mastery of FTK. Requirements for taking the exam include completing the boot camp and Windows forensic courses AccessData Certified Examiner What term is used to describe a formal document prepared by a forensics specialist to document an investigation, including a list of all tests conducted? expert report What is meant by file slack? the unused space between the logical end of file and the physical end of file Use of __________ tools enables an investigator to reconstruct file fragments if files have been deleted or overwritten bit-level If someone has a certification regarding knowledge of PC hardware, that certification would be CompTIA A+ certification is a Linux Live CD that you use to boot a system and then use the tools. It is a free Linux distribution, making it extremely attractive to schools teaching forensics or laboratories on a strict budget BackTrack is a term that refers to how long data will last, related to volatility Life span The 1s and 0s that make up data can be hidden and vanish instantly with the push of a button. As a result, forensic examiners should assume that every computer has been rigged to destroy evidence. Therefore, one of the three basic tasks of a forensics specialist is to preserve evidence Identification, preservation, collection, examination, analysis, and presentation are six classes in the matrix of the DFRWS framework govern whether, when, how, and why proof of a legal case can be placed before a judge or jury Rules of evidence Failing to document where evidence comes from and/or ensure that it has not been changed can ruin a case. Judges have dismissed cases because of such failures. Therefore, one of the three basic tasks of a forensics specialist is to prepare evidence Basically, __________ is information at the level of actual 1s and 0s stored in memory or on the storage device, as opposed to going through the file system's interpretation bit-level information What name is given to the unused space between the logical end of file and the physical end of file? slack space Which of the following is the definition of digital evidence? information that has been processed and assembled so that it is relevant to an investigation and supports a specific finding or determination Which starting-point forensic certification covers the general principles and techniques of forensics, but not specific tools such as EnCase or FTK? EC Council Certified Hacking Forensic Investigator Authentication of evidence on the basis of scientific or technical knowledge relevant to a case is the definition of: expert testimony [Show More]
Last updated: 9 months ago
Preview 3 out of 10 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$12.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Mar 13, 2025
Number of pages
10
Written in
All
Additional information
This document has been written for:
Uploaded
Mar 13, 2025
Downloads
0
Views
34