Computer Science > STUDY GUIDE > Case Project 1-2: Personal Information Security Terminology Introduction to Network Security (All)
Case Project 1-2: Personal Information Security Terminology Introduction to Network Security
Document Content and Description Below
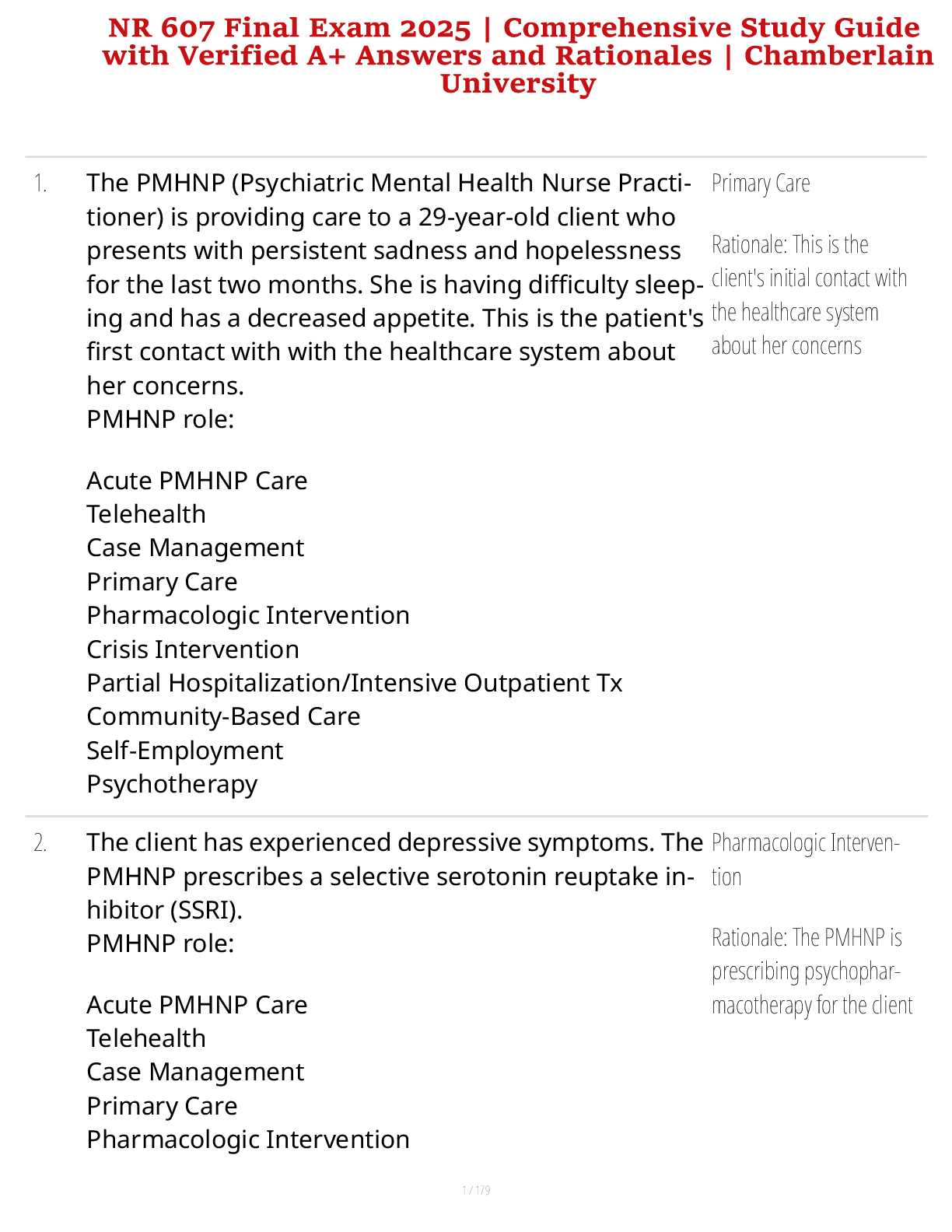
Case Project 1-2: Personal Information Security Terminology The scenario of Ellie protecting her scooter was used in this chapter to introduce important key terms used in information security: asset ... , threat, threat actor, vulnerability, attack vector, attack surface, likelihood, and risk. Create you own one-paragraph scenario with those key terms using a situation with which you are familiar. Also, create a table similar to Table 1-5 that lists these terms and how they are used in your scenario. George, an IT employee was just fired from ABC company due to unsatisfactory performance within the company. Disgruntled, he decides to use his old credentials to log into ABC’s databases to delete important files that can disrupt service within the company. He decides to go to a coffee shop that offers free Wi-Fi and tries to log into the company’s database remotely using their VPN. He finds out that his credentials are still working. Knowing this, he then deletes and alters a few files that are important. Additionally, he installs a backdoor, so that if his credentials no longer work, he can access the database later. In this scenario, the disgruntled employee George would be considered the threat attacker in this scenario. The asset would be ABC’s company files within their database. The threat would be the manipulation and depletion of the company files. The vulnerability in this scenario would be the log-in credentials of George and the fact it is still active for him to access ABC’s database. The attack vector would be using the backdoor, should George want to access the database in the future. The likelihood that George would do this would be because he felt that his dismal from ABC company is unfair to him. The risk of this scenario is the lost of data of ABC company. [Show More]
Last updated: 3 years ago
Preview 1 out of 4 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$7.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
May 15, 2021
Number of pages
4
Written in
All
Additional information
This document has been written for:
Uploaded
May 15, 2021
Downloads
0
Views
65


.png)
.png)