Computer Networking > STUDY GUIDE > Thomas Nelson Community College ITN 26 0Entire Unit 2. (All)
Thomas Nelson Community College ITN 26 0Entire Unit 2.
Document Content and Description Below
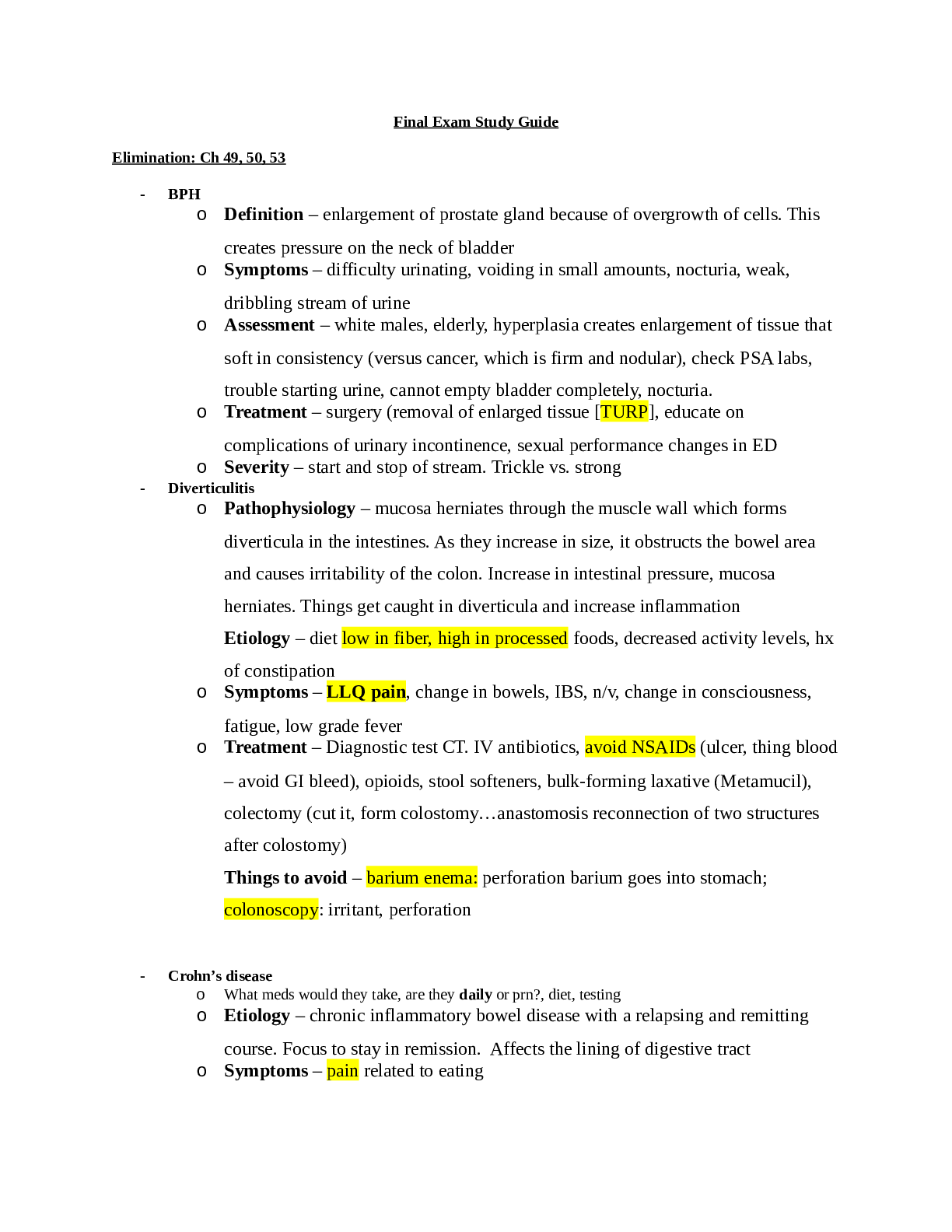
Unit 2 Malware (malicious sofware) is sofware that enters a computer system without the user’s knowledge or consent and then performs an unwanted and harmful action. Malware is most ofen used as ... the general term that refers to a wide variety of damaging sofware programs. NOTE: Many jurisdictions use the legal term computer contaminant instead of malware to be as encompassing and precise as possible so that offenders cannot find a loophole to escape prosecution. A typical definition is: “Computer contaminant means any data, information, image, program, signal or sound that is designed or has the capability to: 1. Contaminate, corrupt, consume, damage, destroy, disrupt, modify, record or transmit; or 2. Cause to be contaminated, corrupted, consumed, damaged, destroyed, disrupted, modified, recorded or transmitted, any other data, information, image, program, signal or sound contained in a computer, system or network without the knowledge or consent of the person who owns the other data, information, image, program, signal or sound or the computer, system or network.” As security defenses have continued to evolve in order to repel malware, so too has malware continued to become more complex, with new malware being written and distributed. This has resulted in an enormous number of different instances of malware that have emerged (an example is the malware ZeuS). Yet there has been no standard established for the classification of these different instances of malware; many malware classifications are simply lists of different types of malware (virus) instead of broader categories in which like instances can be grouped together. As a result, the attempts to classify malware can be confusing. NOTE: Because threat actors ofen tweak their malware so that it evades the latest security defenses, many instances of malware are similar. These similar instances of malware are sometimes referred to as malware families.One method of classifying the various instances of malware is by using the primary trait that the malware possesses. These traits are circulation, infection, concealment, and payload capabilities. Circulation. Some malware has as its primary trait spreading rapidly to other systems to impact a large number of users. Malware can circulate through a variety of means: by using the network to which all the devices are connected, through USB flash drives that are shared among users, or by sending the malware as an email attachment. Malware can be circulated automatically or it may require an action by the user. Infection. Once the malware reaches a system through circulation, then it must “infect” or embed itself into that system. The malware might run only one time, or it might remain on the system and be launched an infinite number of times. Some malware attaches itself to a benign program while other malware functions as a stand-alone process. Concealment. Some malware has as its primary trait avoiding detection by concealing its presence from sofware scanners that are looking for malware. Some malware attempts to avoid detection by changing itself, while other malware can embed itself within existing processes or modify the underlying host operating system. Payload capabilities. When payload capabilities are the primary trait of malware, the goal is the nefarious actions the malware performs. Does it steal passwords and other valuable data from the user’s system? Does it delete programs so the computer can no longer function properly? Does the malware modify the system’s security settings? In some cases, the purpose of the malware is to use the infected system to launch attacks against other computers. The sections that follow give more details and examples of malware classified by circulation, infection, concealment, and payload capabilities. (NOTE: Some types of malware have more than one of these traits: that is, the malware both circulates and carries a payload. However, in terms of classification the primary trait of the malware is used here)Two types of malware have the primary trait of circulation. These are viruses and worms.A biological virus is an agent that reproduces inside a cell. When a cell is infected by a virus, the virus takes over the operation of that cell, converting it into a virtual factory to make more copies of it. The cell is forced to produce thousands or hundreds of thousands of identical copies of the original virus very rapidly (the polio virus can make more than one million copies of itself inside one single infected human cell). Biologists ofen say that viruses exist only to make more viruses. A computer virus is malicious computer code that, like its biological counterpart, reproduces itself on the same computer. Strictly speaking a computer virus replicates itself (or an evolved copy of itself) without any human intervention. (NOTE: Strictly speaking, virus and malware are not interchangeable terms. A virus is only one type of malware.) Almost all viruses infect by inserting themselves into a computer file, either an executable program file or a user-created data file. A virus that infects an executable program file is called a program virus. When the program is launched, the virus is activated. A virus can also be part of a data file. One of the most common is a macro virus. A macro is a series of instructions that can be grouped together as a single command. Ofen macros are used to automate a complex set of tasks or a repeated series of tasks. Macros can be written by using a macro scripting language, such as Visual Basic for Applications (VBA), and are stored within the user document (such as in an Excel .xlsx worksheet or Word .docx file). Once the document is opened, the macro instructions execute, whether those instructions are benign or a macro virus. NOTE: The first macro virus appeared in 1995. Macro viruses infecting Microsof Word documents became the dominant type of virus until 2000 when Microsof disabled macros by default in its Office products. However, a macro virus is not a relic of the past; it has recently made a resurgence as threat actors have discovered new ways to trick their victims into enabling macros that will then allow the macro virus to run. A very large number of different file types can contain a virus. Table 2-1 lists some of the 50 different Microsof Windows file types that can be infected with a virus. NOTE: One of the first viruses found on a microcomputer was written for the Apple II in 1982. Rich Skrenta, a ninth-grade student in Pittsburgh, wrote “Elk Cloner, [Show More]
Last updated: 3 years ago
Preview 1 out of 23 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$13.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jun 16, 2021
Number of pages
23
Written in
All
Additional information
This document has been written for:
Uploaded
Jun 16, 2021
Downloads
0
Views
90