
Sophia Learning College Algebra Unit 5, challenge 1, challenge 2: Challenge 3 - All answers
$ 13
.png)
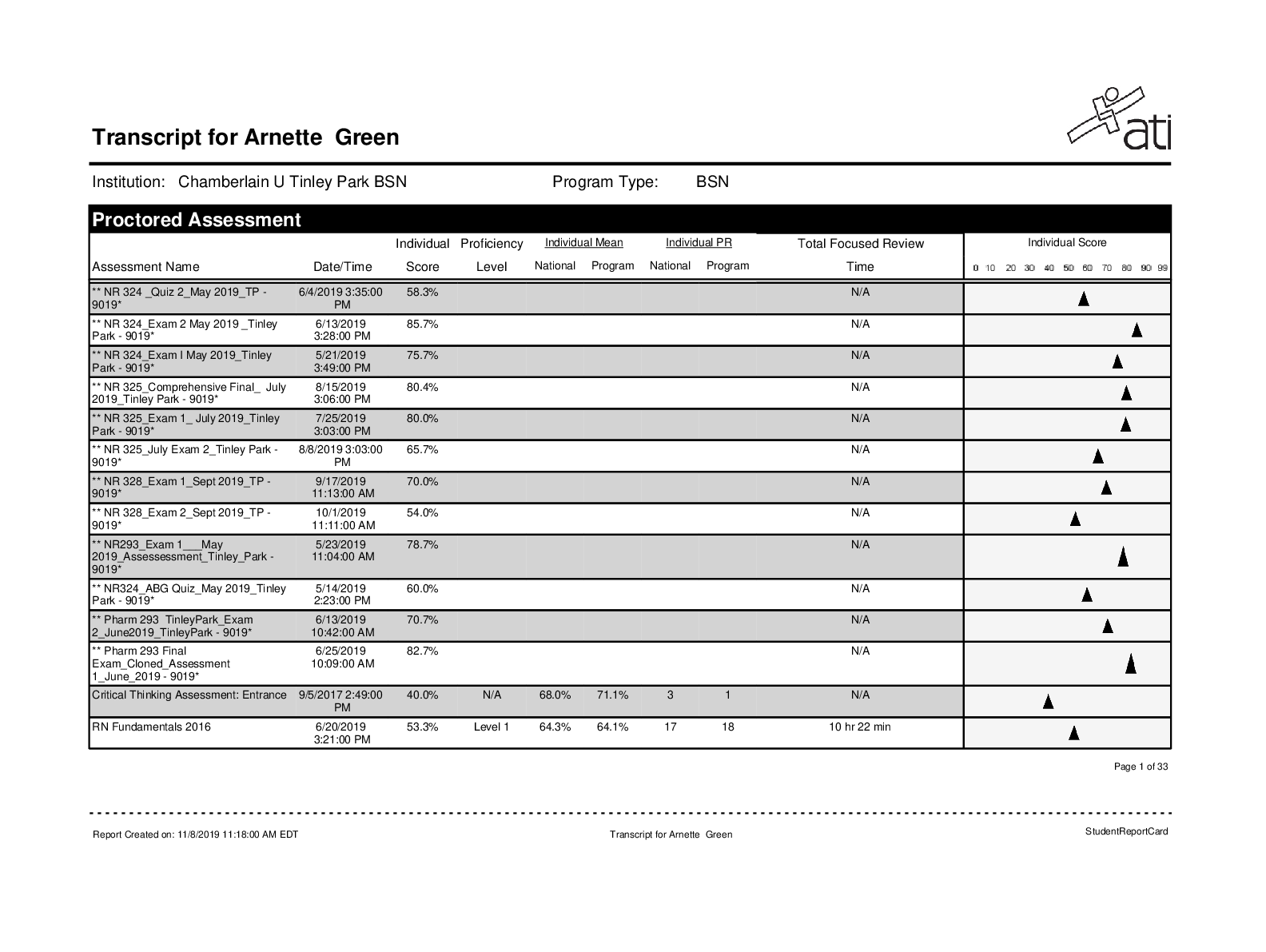
ATI Mental Health - Chapters 1-32 questions with 100% accuarate answers. Highly Rated
$ 10
 (1).png)
MAT 510 Week 11 Final Exam study Questions and Answers
$ 15

Hesi Fundamentals 2019 Exam Questions And Answers( Complete Solution Rated A)
$ 16

Test Bank for Using Basic Statistics in the Behavioral and Social Sciences 5th Edition By Annabel Evans.
$ 19

Counselor Preparation Comprehensive Examination CPCE, Exam Questions and answers. Graded A+
$ 11

NR 509 Week 3 Neurology SOAP Note (version 1) 2019/2020, complete template solutions.
$ 11

Test Bank For Statistics Informed Decisions Using Data 6th Edition (Global Edition) By Michael Sullivan
$ 25

NGR 6172 Pharm Midterm Exam- Questions and Answers (Graded A)


















.png)





