Programming > EXAM > CS6823 Network Security_CSCI-SHU MISC . Introduction to Programming and Problem Solving, Sample Fina (All)
CS6823 Network Security_CSCI-SHU MISC . Introduction to Programming and Problem Solving, Sample Final _4_New York University
Document Content and Description Below
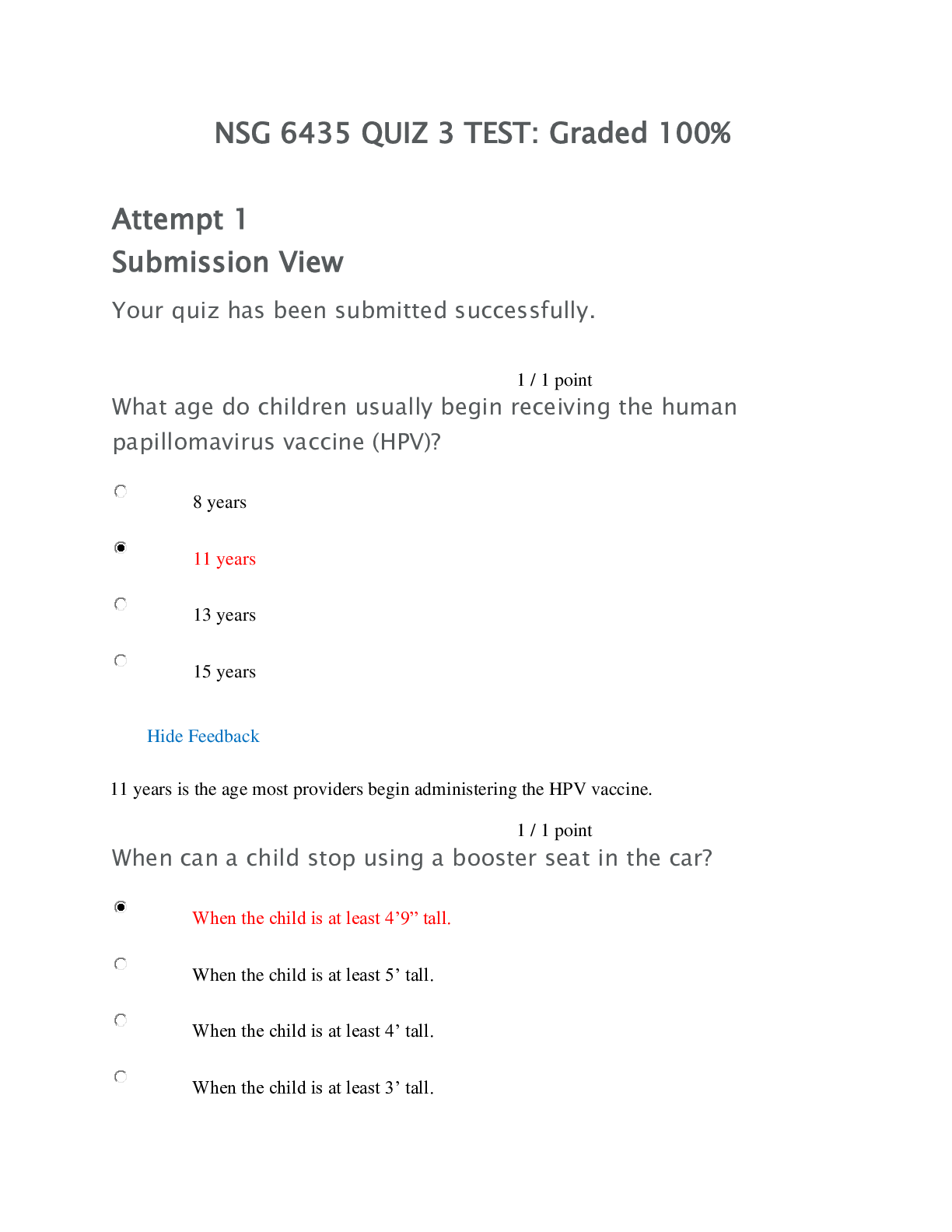
CS6823 Network Security – Final Sample Final _4 • Read each question carefully and answer all parts of the question. • Each answer must be explained. A correct answer without explanation on ... how the conclusion was obtained will receive no credit. • If you do not understand a question or are confused, do the best you can. • If you have the correct solution and also the incorrect solution in your answer, you will lose points. 1. PKI Alice, Bob, and Trudy are employees of ACME Corporation. Alice's PKI private certificate is generated on her laptop and never leaves the laptop. ACME Corporation has the ACME CA that digitally signs all the certificates. a. [3 pts] Explain how Alice would mutually authenticate an ACME server using her PKI certificates. b. [3 pts] How does ACME and Alice know that each other’s certificate is valid? c. [3 pts] If Alice used her PKI certificates for encrypted communications to Bob, would ACME be able to read the encrypted conversation? Explain. d. [3 pts] Trudy (who is evil) also worked at ACME corporation and has valid PKI certificates to authenticate into the ACME network. In what instances would Trudy be able to read the encrypted communication between Alice and Bob? Explain. 2. SSL/TLS 2a. [6 pts] The above diagram shows the SSL Record Layer Operations. Describe what each number (1) to (6) is referring to. 2b. [6 pts] Select the ciphersuites that should not be support anymore today and explain why. Explanation required for credit. (1) TLS_RSA_WITH_RC4_128_SHA (2) TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (3) TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (4) TLS_ECDHE_ECDSA_WITH_RC4_128_SHA (5) TLS_DH_RSA_WITH_AES_128_CBC_SHA Page 2 of 3 3. [10 pts] Kerberos. Suppose Joe wants to authenticate to the Kerberos File Server (FS). Joe has already authenticated to the Kerberos Key Distribution Center (KDC), and has KJ-KDC (symmetric key between Joe and KDC). Additionally, the FS has already authentication to KDC and has KFS-KDC (symmetric key between FS and KDC). Explain in detail what happens in order for Joe to begin communicating with the File Sever using Kerberos. 4. iptables The diagram shows two networks: 10.10.111.0/24 is the Internal network, which is protected from the Internet by an Exterior Firewall. The Interior Firewall separates the wireless clients from the wired clients, which are both on the same subnet 10.10.111.0/24. The Internal network has a DHCP Server with a DHCP address pool of .100 to .200. The DHCP Server provides DHCP addresses to all users on the Internal Network as marked. Implement the following policies using iptables on the Interior Firewall and Exterior Firewall only. Clearly show which rules are for which Firewall. Stateful rules required. 4a. [3 pts] Both Firewalls shall drop all other packets not specified. 4b. [10 pts] The DHCP Server provides DHCP addresses to the Interior Firewall and to the clients on the Wireless Network. Note: DHCP Discovery and Requests are from UDP source port 68 to destination port 67, and Offers and ACKs are the opposite. Note 2: Assume iptables works with DHCP. 4c. [4 pts] All HTTP (80) and HTTPS (443) traffic initiated from the Internal Network 10.10.111.0/24 must go through the HTTP Proxy Gateway (10.20.111.20) in order to access the Internet. Only the HTTP Proxy Gateway is allowed access the Internet. 4d. [5 pts] The administrator (10.10.111.3) can initiate pings to anywhere on the network. Page 3 of 3 5. Layer 2 Security A, B, C, D, and R are all locally connected to a switch. The switch is connected to a Router that can access the Internet. The Switch and Router both have a CAM and ARP table, while the hosts only have an ARP table. 5a. [4 pts] If the Attacker can only send one ARP packet and nothing else, what is the single ARP packet that will allow the Attacker to eavesdrop on as much traffic as possible? Describe the ARP packet in detail and explain why. 5b. [4 pts] Suppose that the Attacker knows that the Client with MAC B, which already has a DHCP IP address, will be renewing its lease soon. How can the Attacker be the MITM between Client B and the Router R using only the DHCP protocol? 5c. [6 pts] Describe in detail three ways to mitigate these two attacks. 6. Wireless ACME Corporation has upgraded their WiFi network to WPA2-AES network for employees only. The WPA2 AP is configured with a Pre-Shared Key. Suppose Trudy is parked outside ACME. 6a. [4 pts] What information can Trudy obtain from just sniffing the wireless traffic of ACME corporation? 6b. [4 pts] Suppose Trudy wants to perform a Denial-of-Service attack on the ACME WiFi network. What are two different ways that she can do that? Why does it work? 6d. [4 pts] What are two different ways that Trudy can try to break into the WiFi network that does not involve brute forcing the WPA2 password? 6e. [8 pts] Describe the WEP Plaintext attack in detail. 7. [5 pts] Scapy. What does the following scapy command do? dst = 10.10.10.0/24 send( IP(dst=dst)/ICMP()/("X"*65535) ) 8. [5 pts] TRUE/FALSE. No explanations needed. 8a. The MAC addresses in WEP are encrypted. 8b. In TLS, the server chooses the ciphersuite to use. 8c. Web servers (e.g., amazon.com) is only allowed to have one TLS certificate at a time. 8d. Passwords stored in the linux /etc/passwd file is the reason that “pass-the-hash” attack works. 8e. A DHCP Server only looks at the MAC address in the Ethernet header. [Show More]
Last updated: 1 year ago
Preview 1 out of 10 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 16, 2022
Number of pages
10
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 16, 2022
Downloads
0
Views
140