Information Technology > QUESTIONS & ANSWERS > C844 Task 1Revised.docx.pdf (All)
C844 Task 1Revised.docx.pdf
Document Content and Description Below
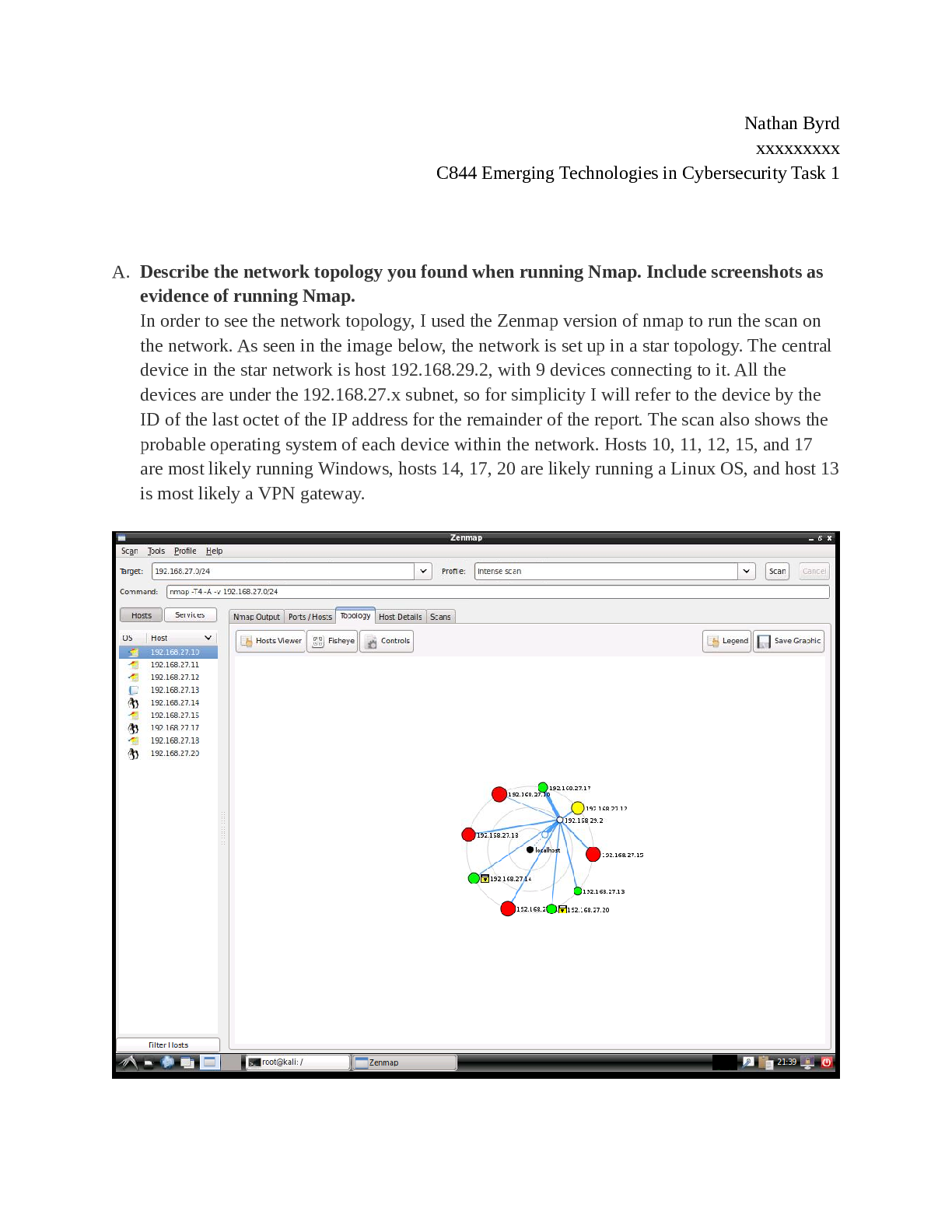
C844 Emerging Technologies in Cybersecurity Task 1 A. Describe the network topology you found when running Nmap. Include screenshots as evidence of running Nmap. In order to see the network topolog ... y, I used the Zenmap version of Nmap to run the scan on the network. As seen in the image below, the network is set up in a star topology. The central device in the star network is host 192.168.29.2, with 9 devices connecting to it. All the devices are under 192.168.27.x subnet, so for simplicity I will refer to the device by the The ID of the last octet of the IP address for the remainder of the report. The scan also shows the probable operating system of each device within the network. Hosts 10, 11, 12, 15, and 17 are most likely running Windows, hosts 14, 17, and 20 are likely running a Linux OS, and host 13 is most likely a VPN gateway.B. Summarize the vulnerabilities on the network and their potential implications based on your Nmap results. Some of the hosts scanned showed potential vulnerabilities based on open ports and operating systems. I will highlight them below, including images of the Zenmap scan results Host 192.168.27.12 - The scan for host 12 shows ports 21, 80, 135, 139, and 445 open. Port 21 is potentially vulnerable as the FTP service that runs on it uses cleartext transmissions. This means that usernames and passwords used for authentication are not encrypted and can be seen by anyone. Any data or files transmitted using this protocol are also vulnerable. This protocol is very susceptible to password sniffing and man-in-the-middle attacks. Ports 135, 139, and 445 are all ports used by the WannaCry Ransomware to infect Windows systems. The WannaCry Ransomware can infect every version of Windows from XP to 10. Ransomware is particularly nasty as it encrypts all the files on your computer, and demands payment, usually in Bitcoin, to receive the key to decrypt the files. Sometimes, the key isn’t even delivered. The only way to recover from a ransomware attack is to restore the system from the most recent backup, which can lead to loss of data going back hours or even days (Shaw, 2018). [Show More]
Last updated: 3 years ago
Preview 1 out of 10 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$7.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 24, 2022
Number of pages
10
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 24, 2022
Downloads
0
Views
50