Information Technology > QUESTIONS & ANSWERS > Nicolas Moy 844 Emerging Technologies in Cybersecurity Task 2 (All)
Nicolas Moy 844 Emerging Technologies in Cybersecurity Task 2
Document Content and Description Below
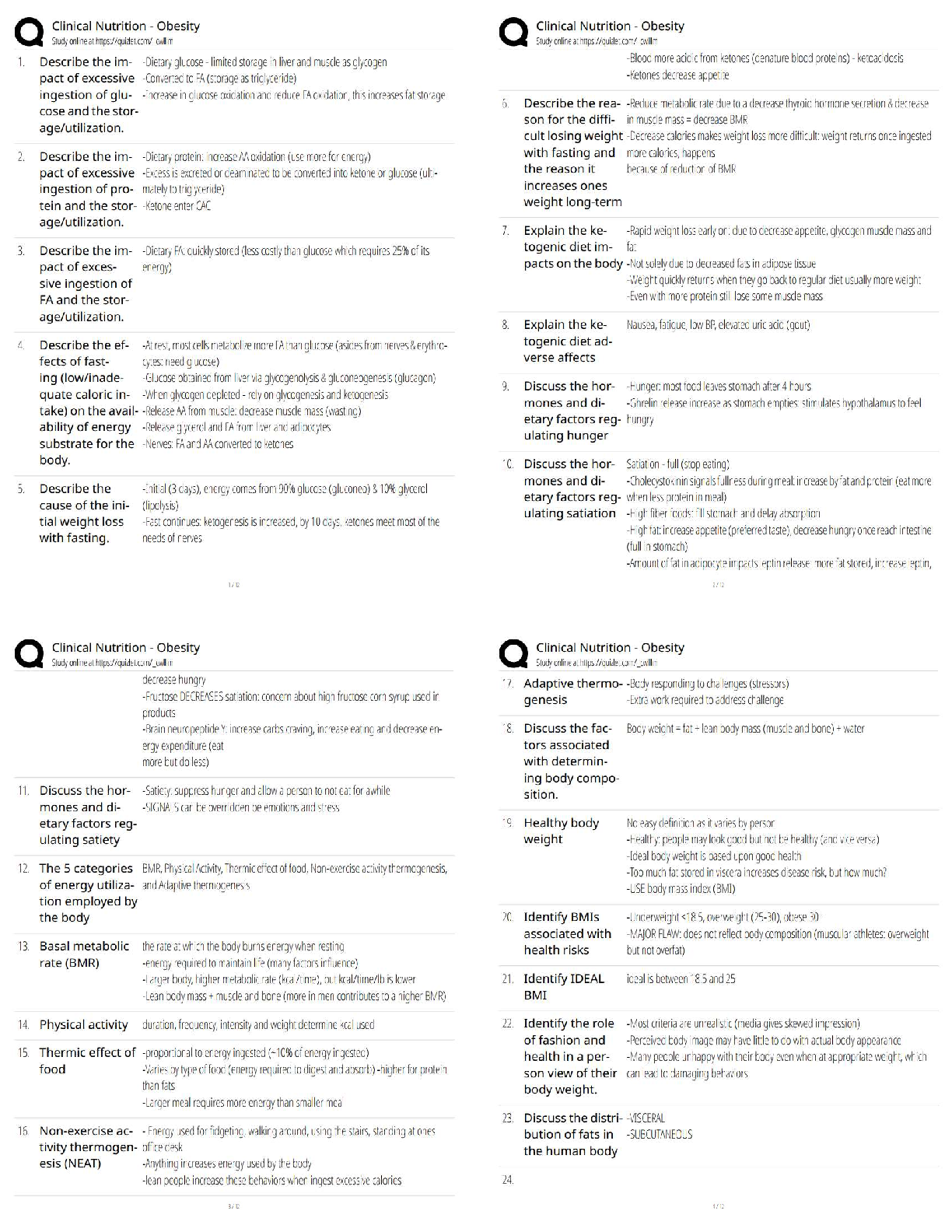
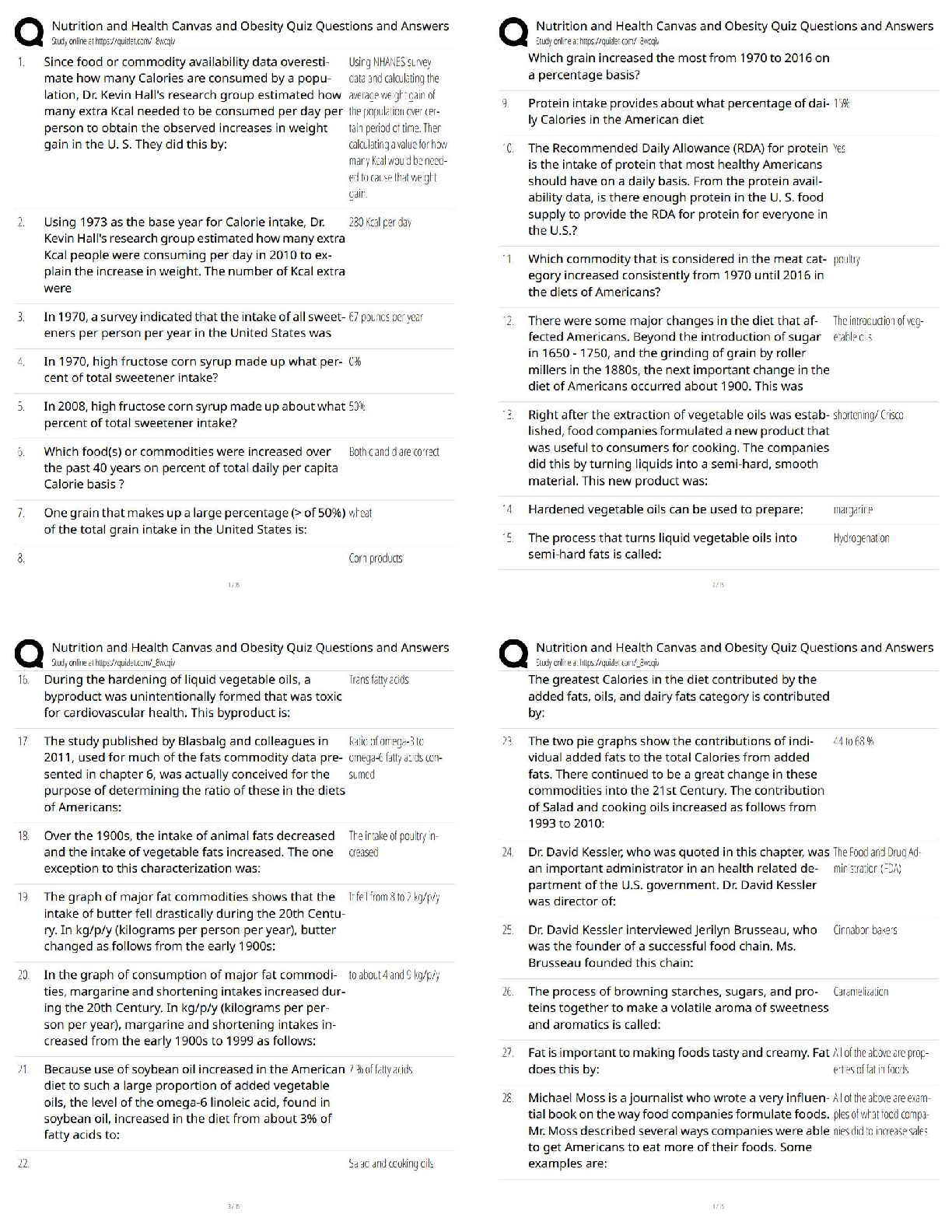
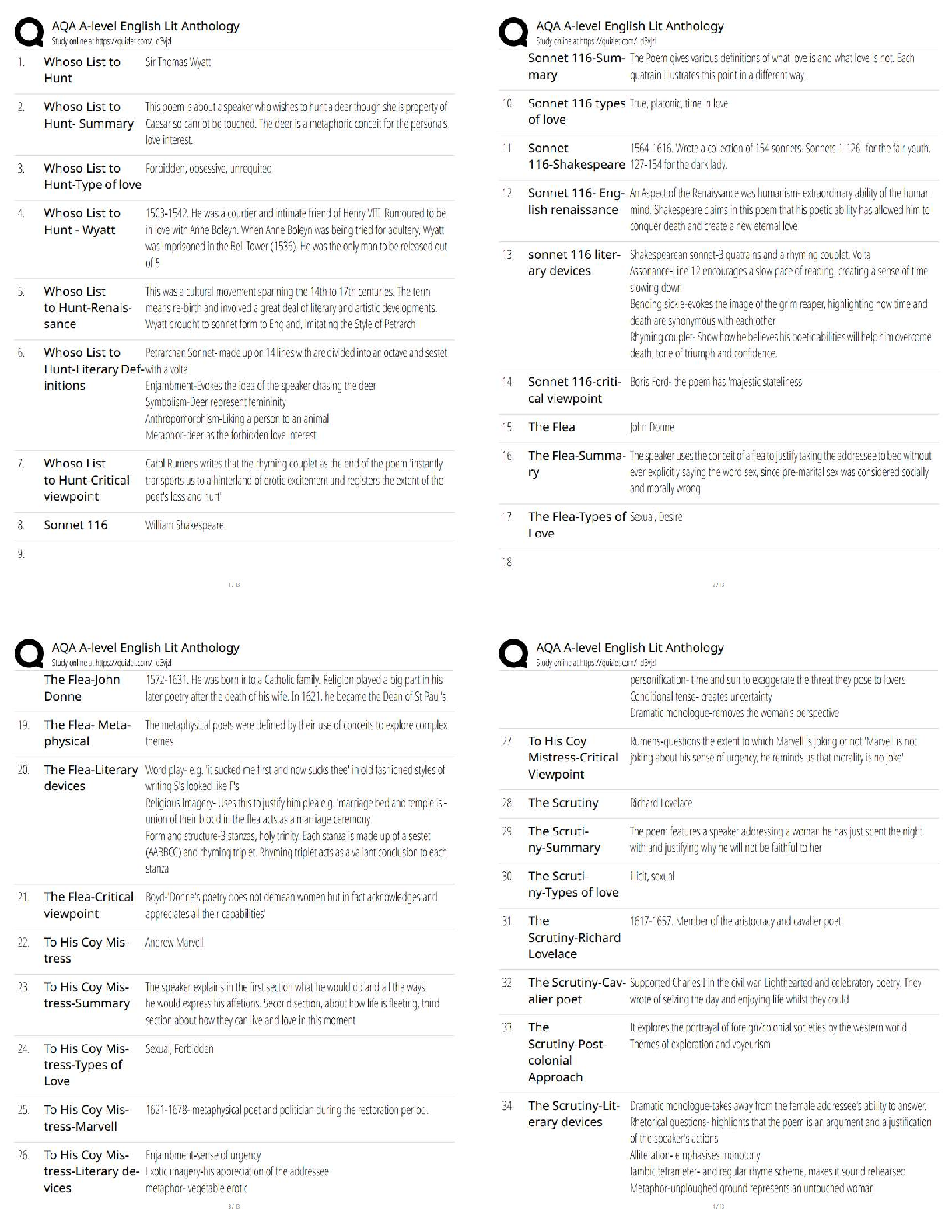
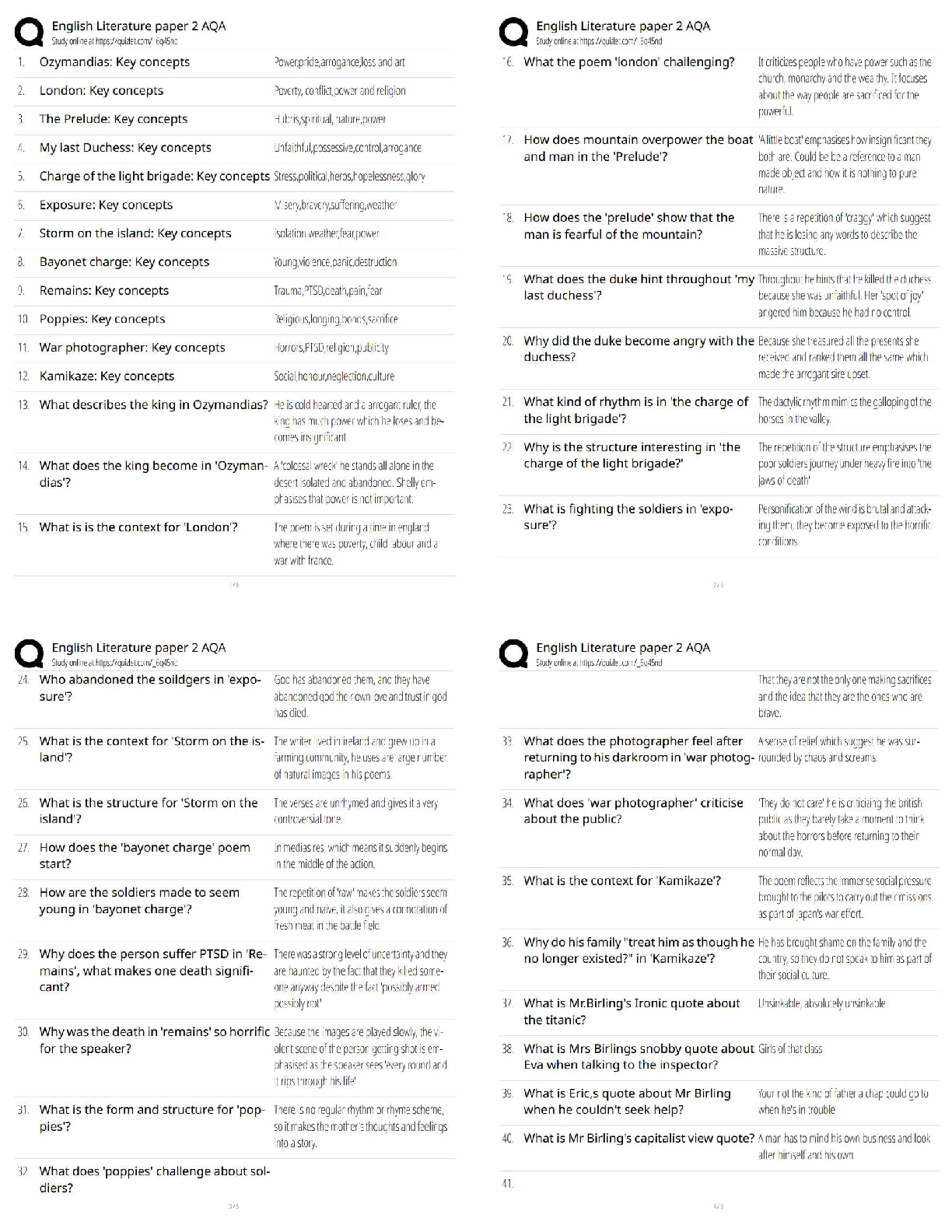
Describe two WLAN vulnerabilities that present risks for Alliah, based on the details in the scenario. Rogue Access Point - A rogue access point is placed in a network by an attacker to trick users ... into accessing the rogue access point instead of the primary/intended access point. Usually, this is done by creating an open network with similar SSID naming schemes that draw users into thinking it’s part of the corporate network. In the scenario of Alliah Company, a rogue access point could easily be placed within the perimeter of the building offering access to the internet. The motive behind the attacker using the rogue AP is to inspect traffic being transmitted through the access point and used for further exploitation. This is called an “Evil Twin” attack. Packet Sniffing - Given that Alliah Company has its workspace operating on a wireless network, there is certainly room for outside intruders to sniff out and intercept packets being broadcast in the air via 802.11 wireless signals. Describe two mobile vulnerabilities that present risks for Alliah, based on the details in the scenario. Data leaks - Data leaks are the second most common threat to employees using company-issued mobile devices. Employees on the go are likely to be focused on the tasks at hand day-to-day between traveling and meeting with numerous people. This has the potential to leave access to their mobile devices vulnerable to unforeseen attackers who have the desire to steal company private data for their personal or competitive game. In the example with Alliah Company, 5 employees are on the road 80% of the time working with leads to close sales on behalf of the company. Instilling hard drive encryption, VPN access to corporate resources, and strict password policies on mobile devices are all good ways to prevent data leakage. Malware - Granted that these remote account representatives were issued laptops, tablets, and smartphones, it is imperative to protect the span of devices from malware. Hackers have found intelligent methods to penetrating mobile devices using malware and man-in-the-middle attacks to intercept information being transmitted. [Show More]
Last updated: 3 years ago
Preview 1 out of 3 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$7.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 24, 2022
Number of pages
3
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 24, 2022
Downloads
0
Views
44