SSCP Test Questions and Answers 2022 with complete
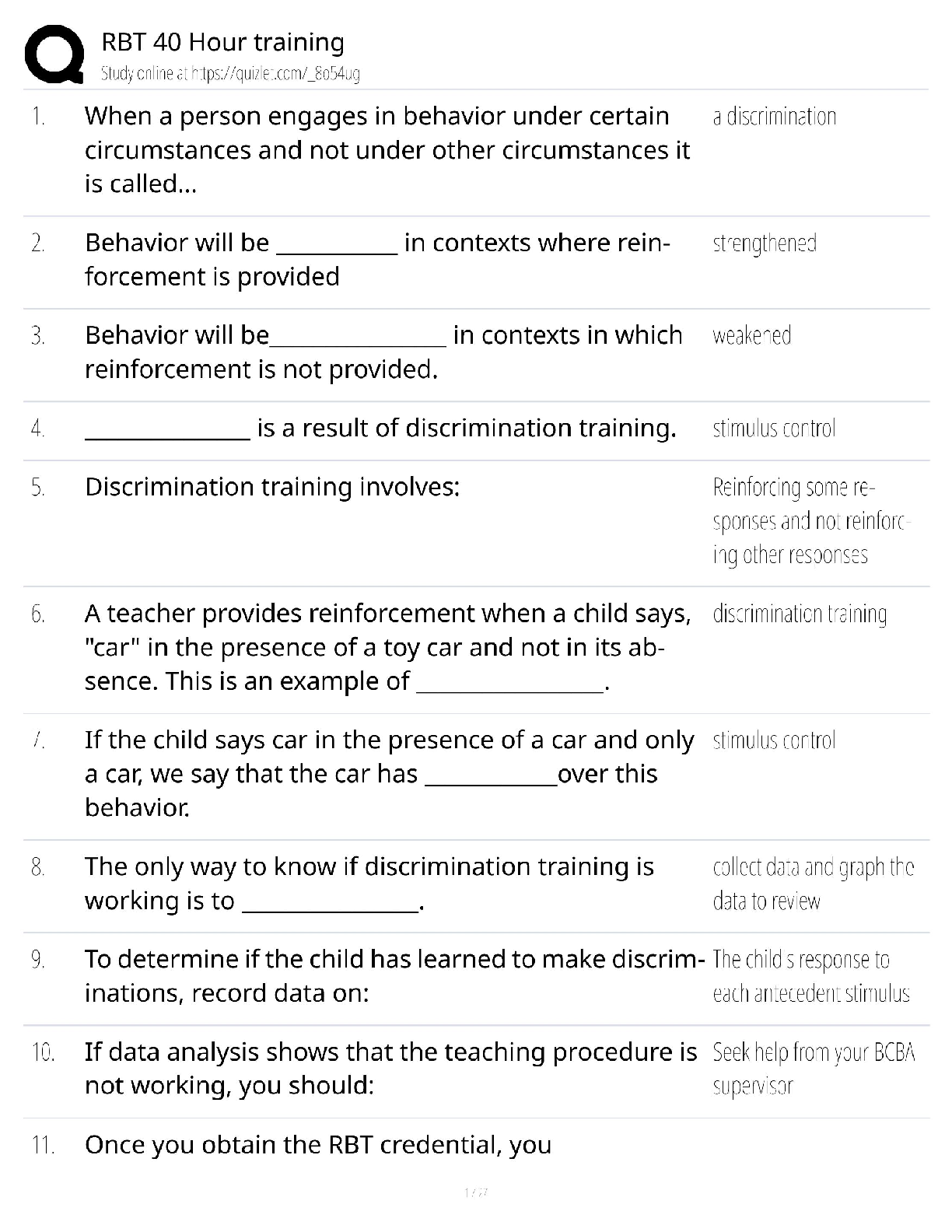
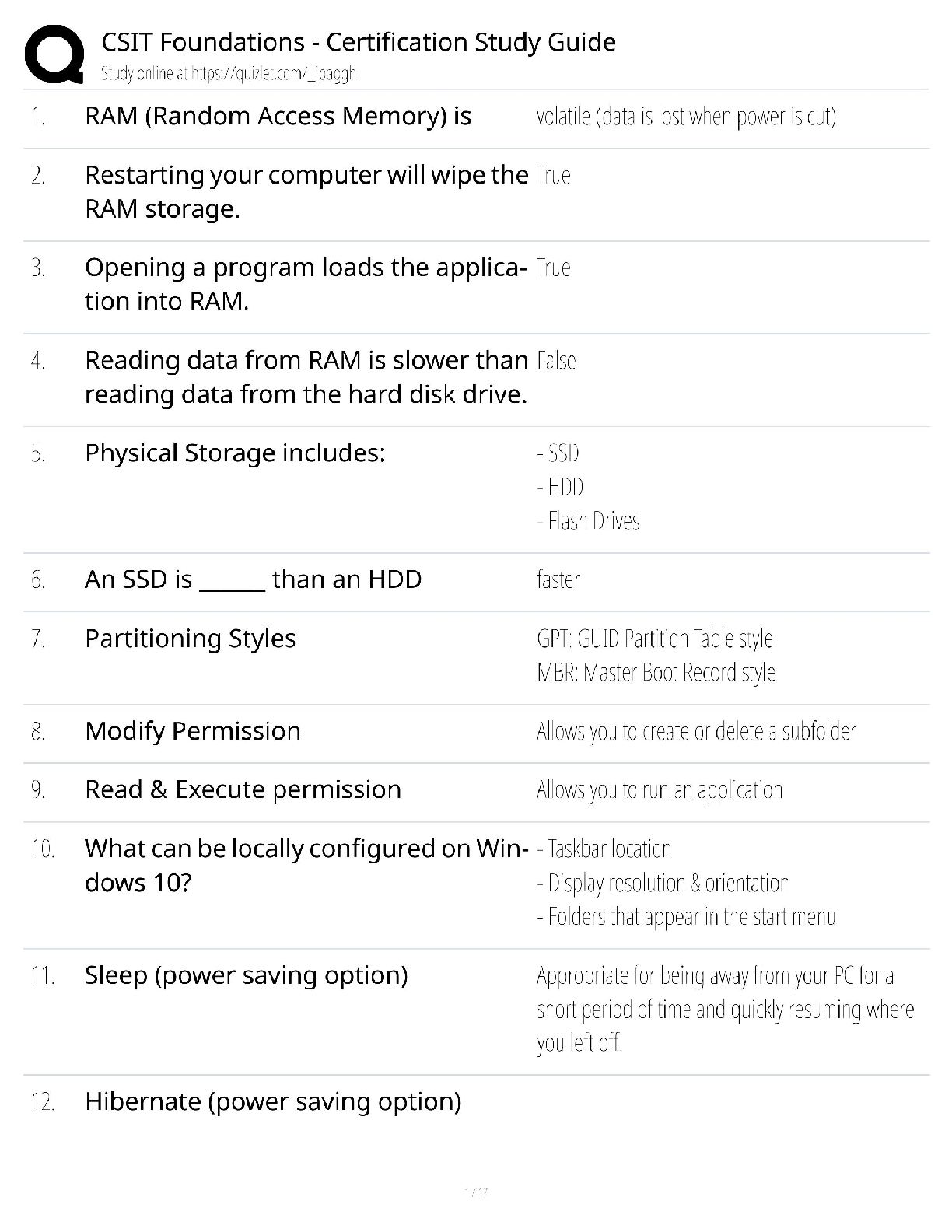
solution
B - DES - Data Encryption standard has a 128 bit key and is very difficult to break.
A. True
B. False
B - What is the main difference between computer abus
...
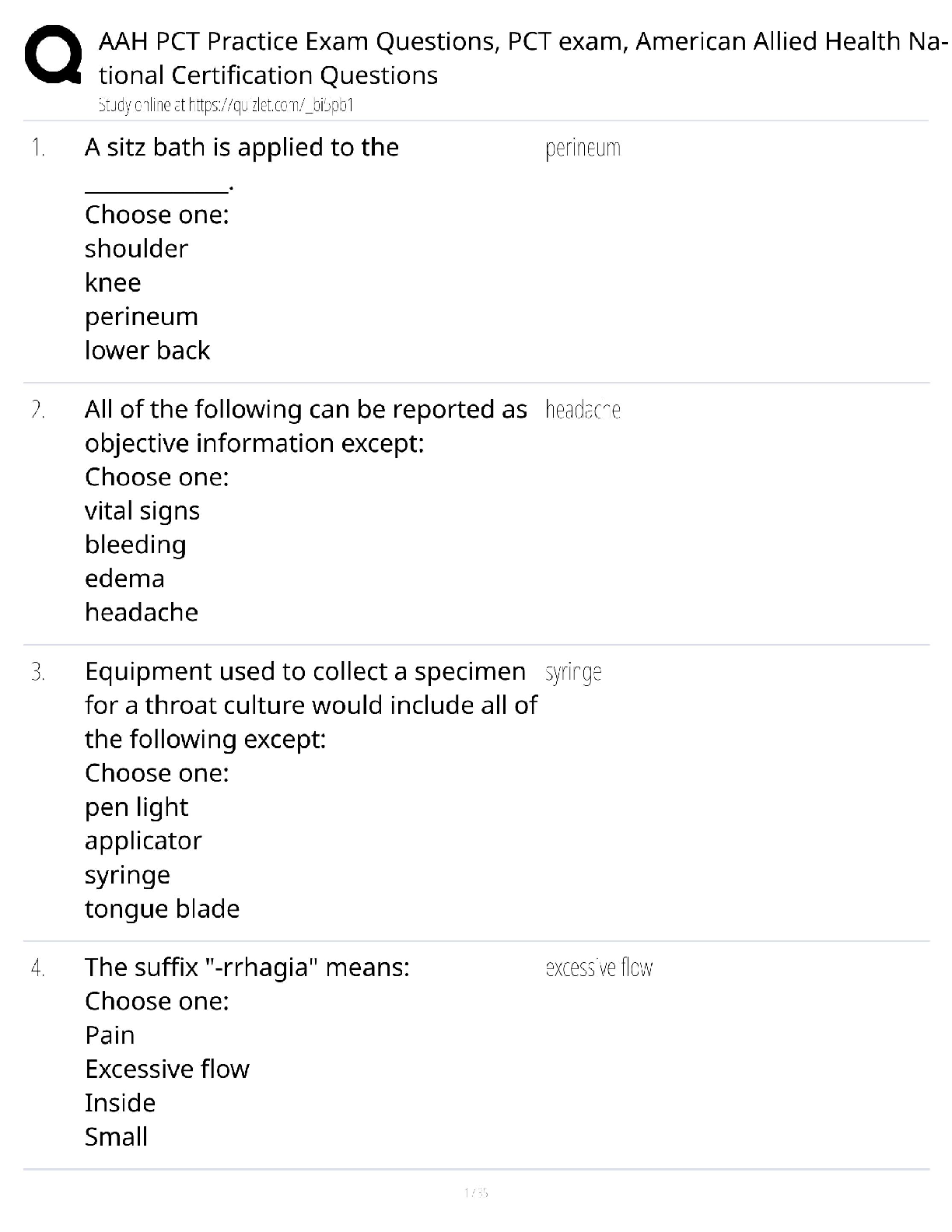
SSCP Test Questions and Answers 2022 with complete
solution
B - DES - Data Encryption standard has a 128 bit key and is very difficult to break.
A. True
B. False
B - What is the main difference between computer abuse and computer crime?
A. Amount of damage
B. Intentions of the perpetrator
C. Method of compromise
D. Abuse = company insider; crime = company outsider
C - A standardized list of the most common security weaknesses and exploits is the
__________.
A. SANS Top 10
B. CSI/FBI Computer Crime Study
C. CVE - Common Vulnerabilities and Exposures
D. CERT Top 10
C - A salami attack refers to what type of activity?
A. Embedding or hiding data inside of a legitimate communication - a picture, etc.
B. Hijacking a session and stealing passwords
C. Committing computer crimes in such small doses that they almost go unnoticed
D. Setting a program to attack a website at11:59 am on New Year's Eve
D - Multi-partite viruses perform which functions?
A. Infect multiple partitions
B. Infect multiple boot sectors
C. Infect numerous workstations
D. Combine both boot and file virus behavior
B - What security principle is based on the division of job responsibilities - designed to
prevent fraud?
A. Mandatory Access Control
B. Separation of Duties
C. Information Systems Auditing
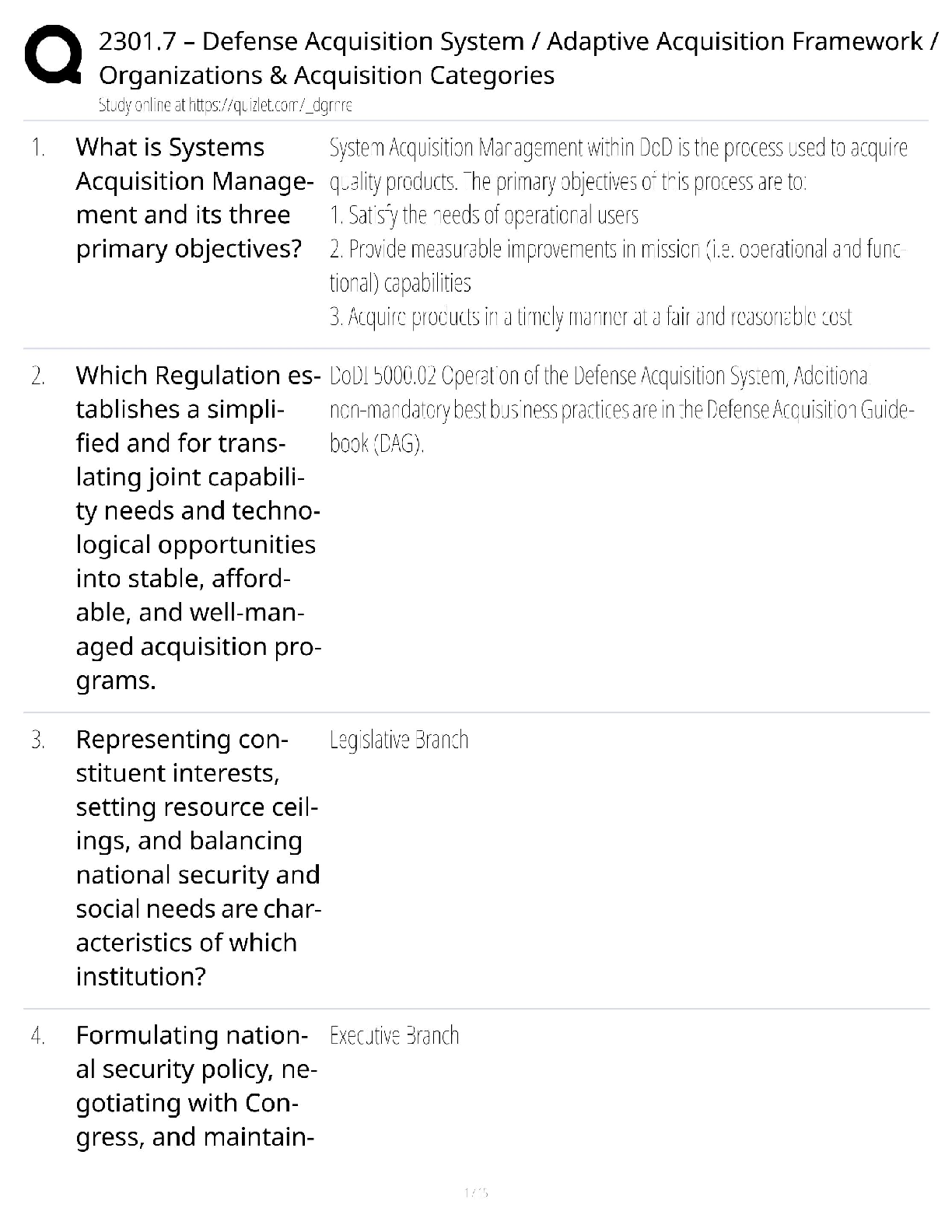
D. Concept of Least PrivilegeA - ________ is the authoritative entity which lists port assignments
A. IANA
B. ISSA
C. Network Solutions
D. Register.com
E. InterNIC
B - Cable modems are less secure than DSL connections because cable modems are
shared with
other subscribers?
A. True
B. False
D - ____________ is a file system that was poorly designed and has numerous security
flaws.
A. NTS
B. RPC
C. TCP
D. NFS
E. None of the above
Log files - Trend Analysis involves analyzing historical ___________ files in order to
look for patterns of
abuse or misuse.
D - HTTP, FTP, SMTP reside at which layer of the OSI model?
A. Layer 1 - Physical
B. Layer 3 - Network
C. Layer 4 - Transport
D. Layer 7 - Application
E. Layer 2 - Data Link
D - Layer 4 in the DoD model overlaps with which layer(s) of the OSI model?
A. Layer 7 - Application Layer
B. Layers 2, 3, & 4 - Data Link, Network, and Transport Layers
C. Layer 3 - Network Layer
D. Layers 5, 6, & 7 - Session, Presentation, and Application Layers
B - A Security Reference Monitor relates to which DoD security standard?
A. LC3B. C2
C. D1
D. L2TP
E. None of the items listed
D - The ability to identify and audit a user and his / her actions is known as
____________.
A. Journaling
B. Auditing
C. Accessibility
D. Accountability
E. Forensics
A,B,C - There are 5 classes of IP addresses available, but only 3 classes are in
common use today,
identify the three: (Choose three)
A. Class A: 1-126
B. Class B: 128-191
C. Class C: 192-223
D. Class D: 224-255
E. Class E: 0.0.0.0 - 127.0.0.1
B - The ultimate goal of a computer forensics specialist is to ___________________.
A. Testify in court as an expert witness
B. Preserve electronic evidence and protect it from any alteration
C. Protect the company's reputation
D. Investigate the computer crime
[Show More]