Computer Science > QUESTIONS & ANSWERS > CySA+ 2022 Questions and Answers with complete solution (All)
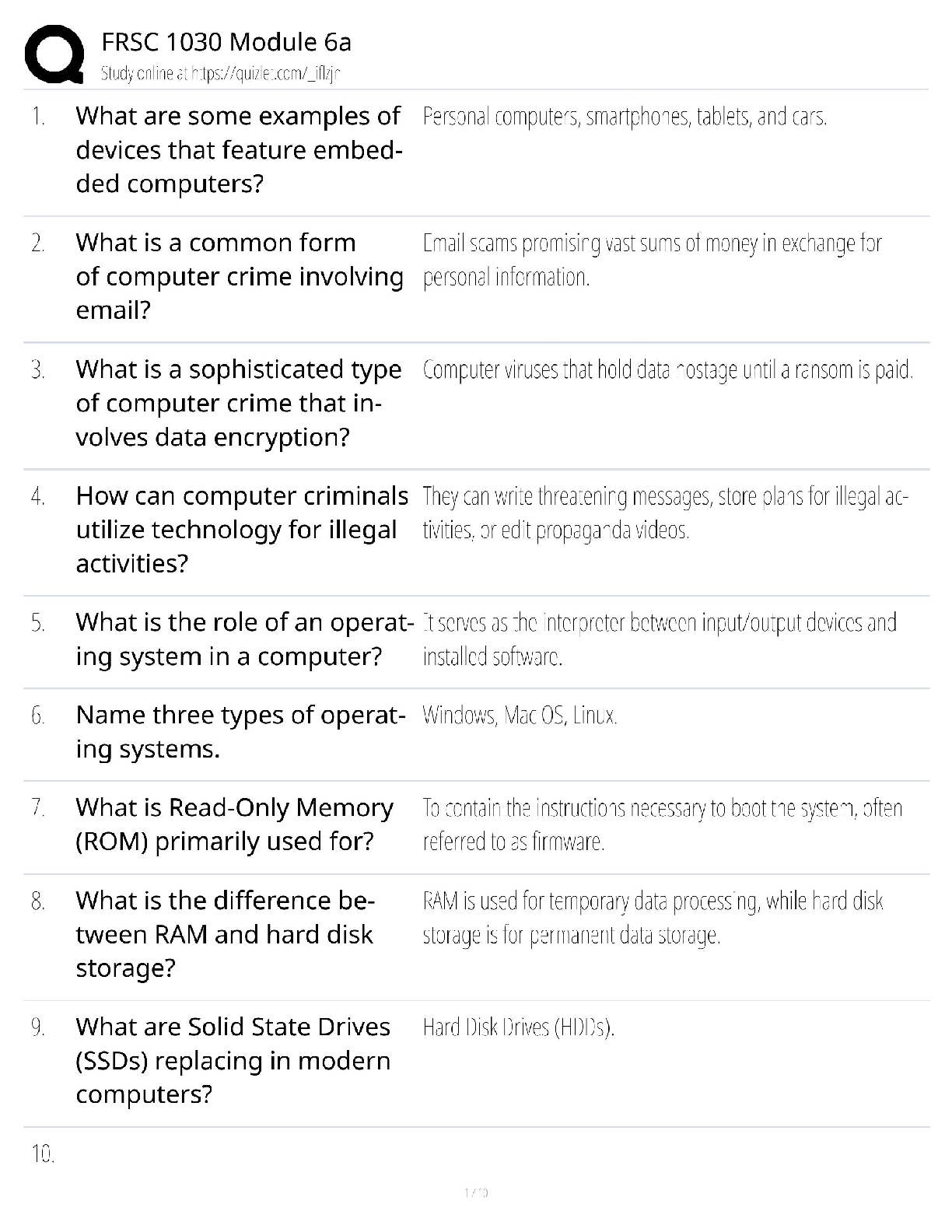
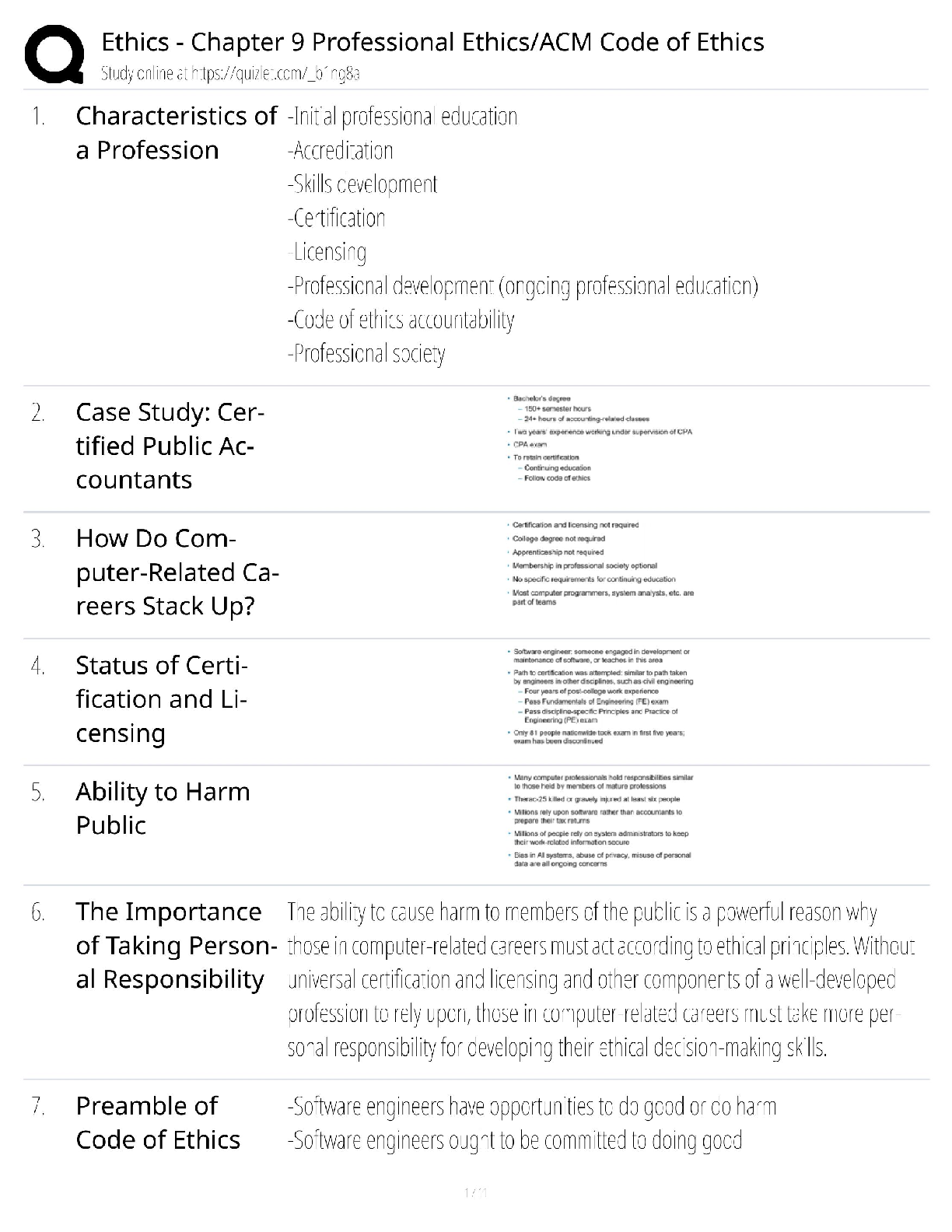
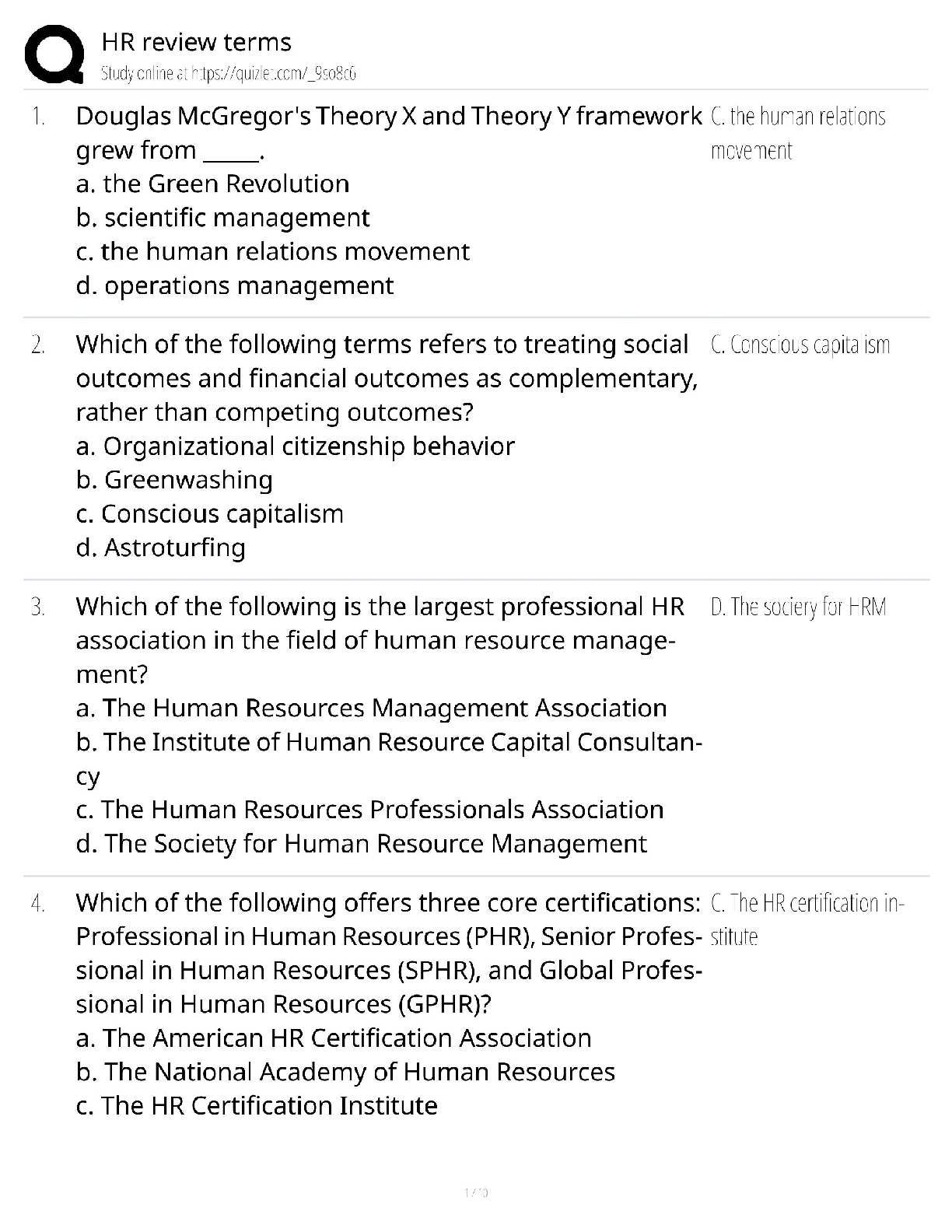
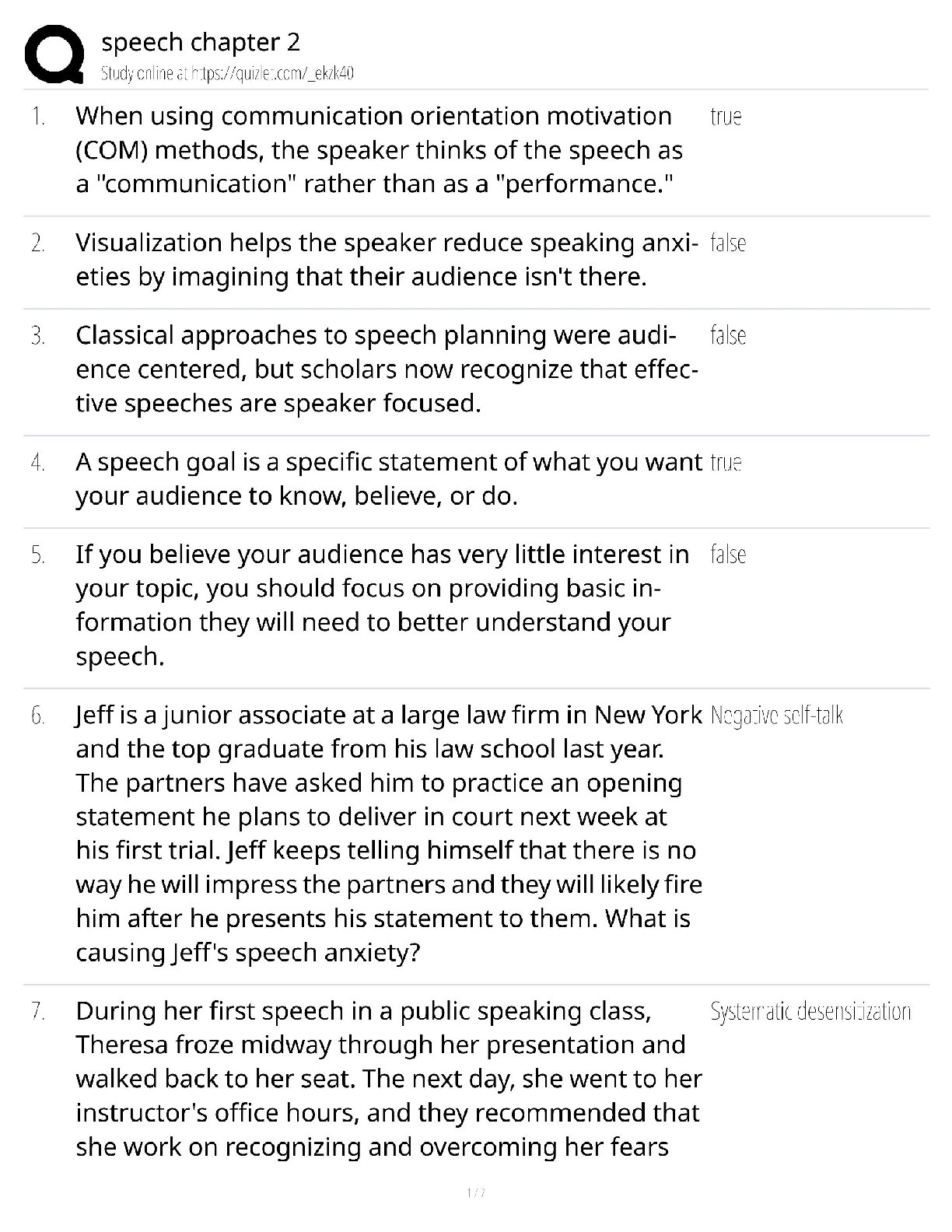
CySA+ 2022 Questions and Answers with complete solution
Document Content and Description Below
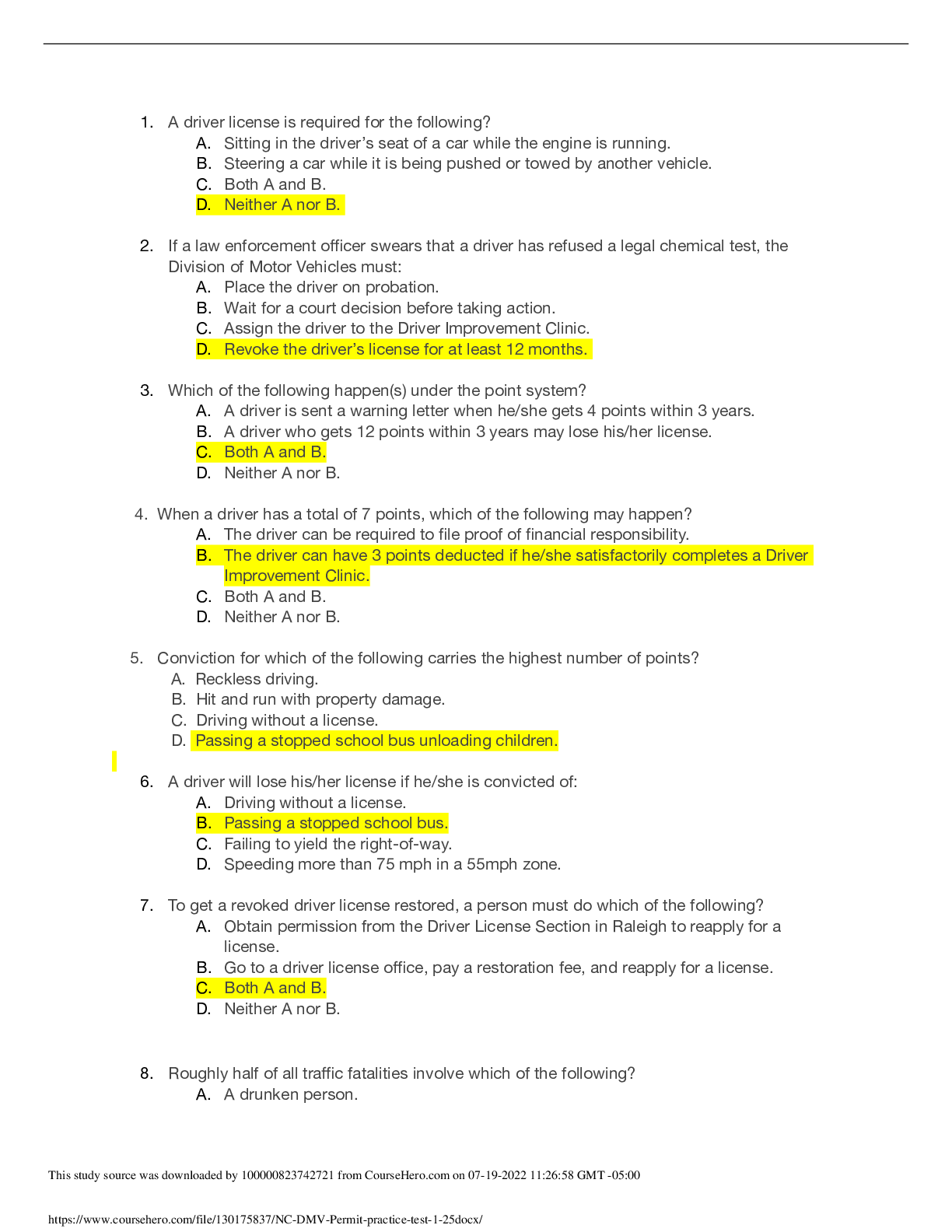
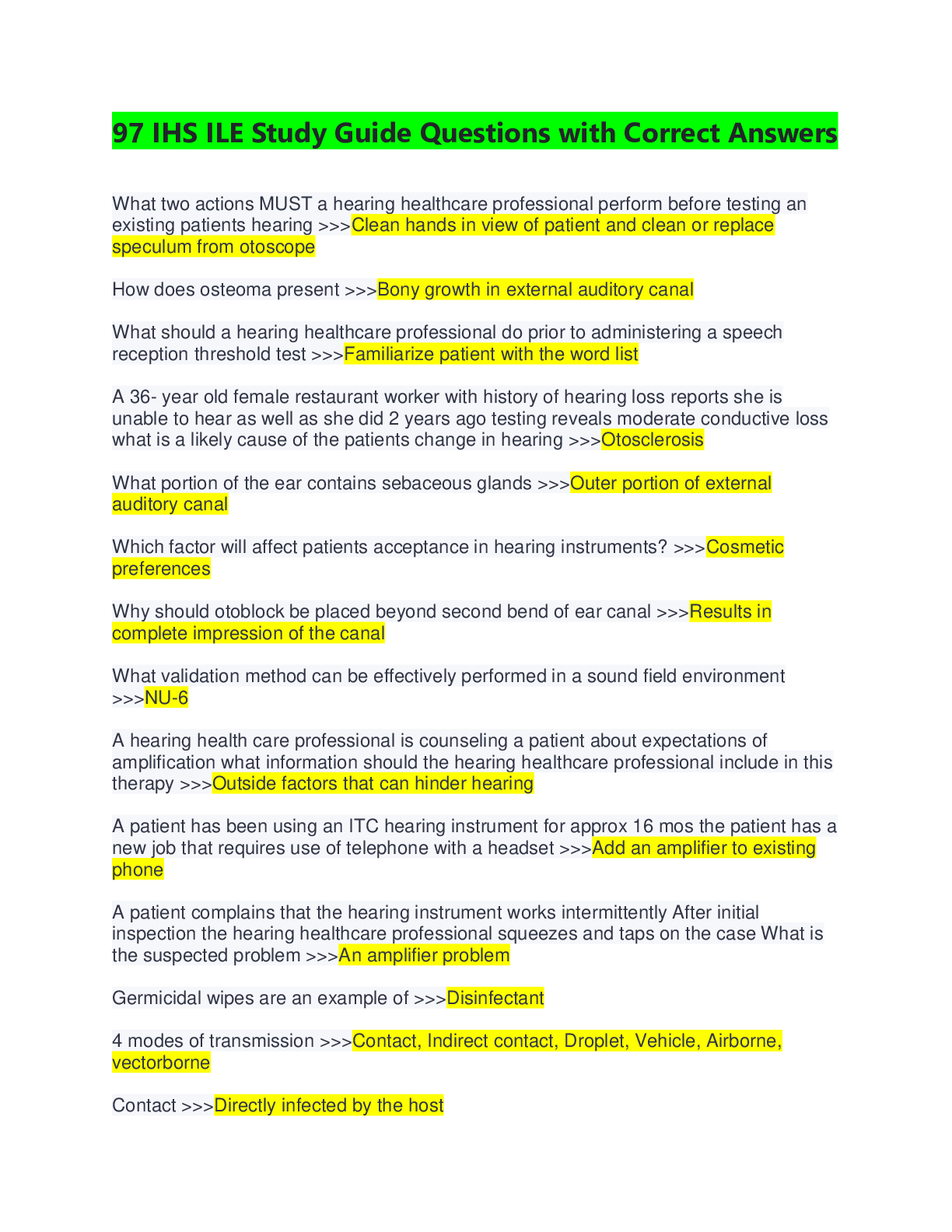
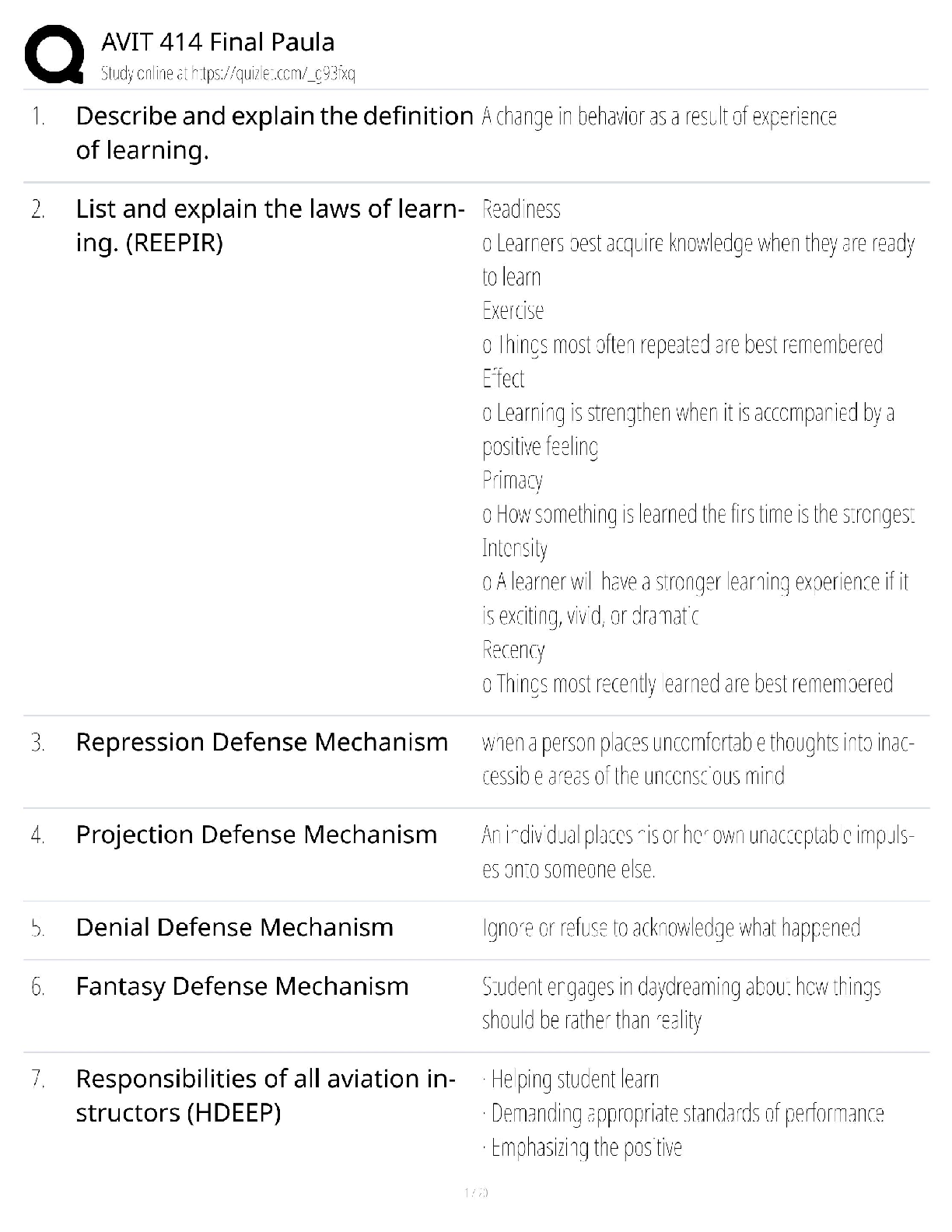
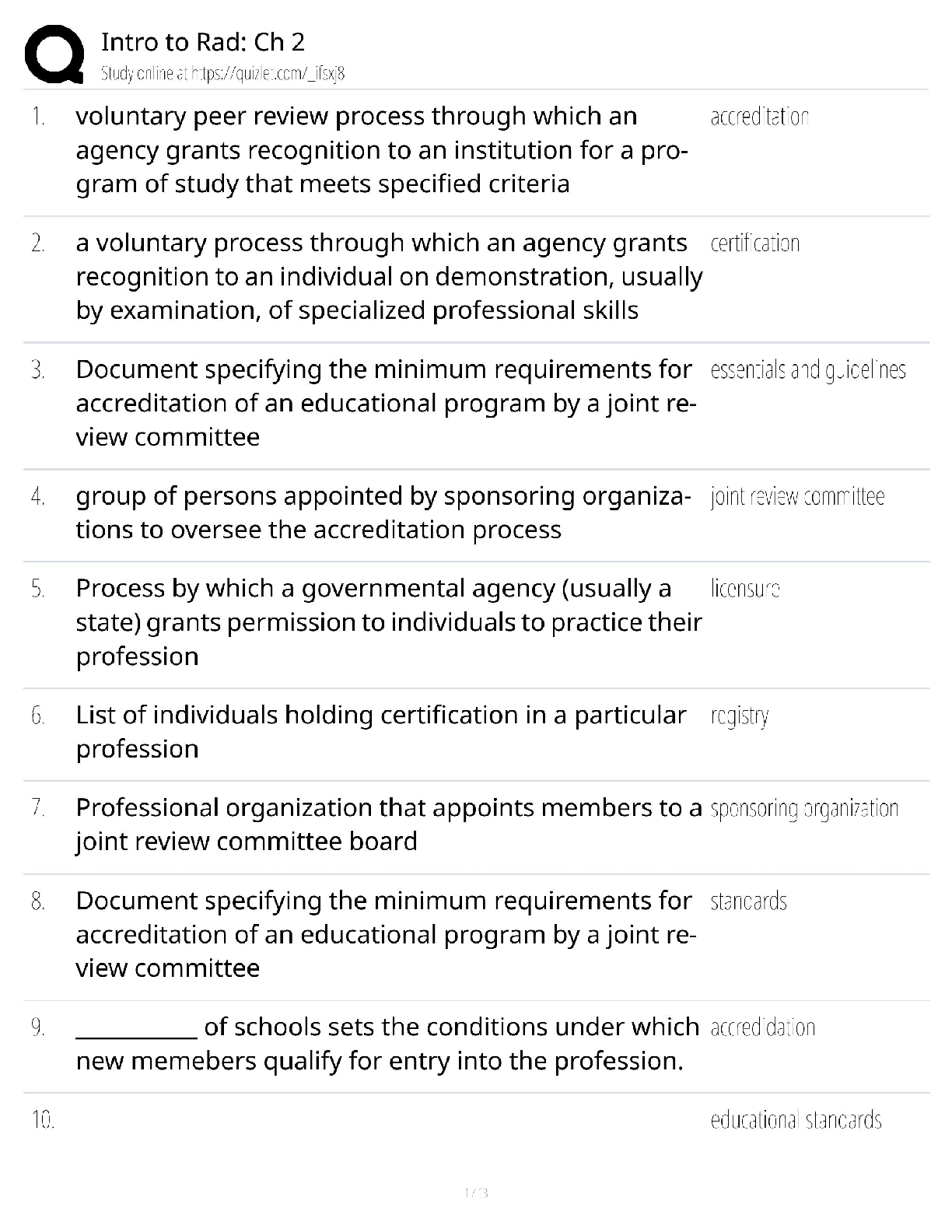
CySA+ 2022 Questions and Answers with complete solution B. >>>1. The help desk informed a security analyst of a trend that is beginning to develop regarding a suspicious email that has been reporte ... d by multiple users. The analyst has determined the email includes an attachment named invoice.zip that contains the following files: Locky.js xerty.ini xerty.lib Further analysis indicates that when the .zip file is opened, it is installing a new version of ransomware on the devices. Which of the following should be done FIRST to prevent data on the company NAS from being encrypted by infected devices? A. Disable access to the company VPN B. Email employees instructing them not to open the invoice attachment C. Set permissions on file shares to read-only D. Add the URL included in the .js file to the company's web proxy filter B. >>>2. A security analyst is reviewing the following log after enabling key-based authentication. Dec 21 11:00:57 comptia sshd[5657]: Failed password for root from 95.58.255.62 port 38980 ssh2 Dec 21 20:08:26 comptia sshd[5768]: Failed password for root from 91.205.189.15 port 38156 ssh2 Dec 21 20:08:30 comptia sshd[5770]: Failed password for nobody from 91.205.189.15 port 38556 ssh2 Dec 21 20:08:34 comptia sshd[5772]: Failed password for invalid user asterisk from 91.205.189.15 port 38864 ssh2 Dec 21 20:08:38 comptia sshd[5774]: Failed password for invalid user sjobeck from 91.205.18.15 port 39157 ssh2 Dec 21 20:08:42 comptia sshd[5776]: Failed password for root from 91.205.189.15 port 39467 ssh2 Given the above information, which of the following steps should be performed NEXT to secure the system? A. Disable anonymous SSH logins B. Disable password authentication for SSH C. Disable SSHv1 D. Disable remote root SSH logins C. >>>3. A security analyst has noticed that a particular server has consumed over 1TB of bandwidth over the course of the month. It has port 3333 open; however, there have not been any alerts or notices regarding the server or its activities. Which of the following did the analyst discover? A. APT B. DDoS C. Zero Day D. False Positive C. >>>4. A company has recently launched a new billing invoice website for a few key vendors. The cybersecurity analyst is receiving calls that the website is performing slowly and the pages sometimes time out. The analyst notices the website is receiving millions of requests, causing the service to become unavailable. Which of the following can be implemented to maintain the availability of the website? A. VPN B. Honeypot C. Whitelisting D. DMZ E. MAC filtering A. >>>5. An executive tasked a security analyst to aggregate past logs, traffic, and alerts on a particular attack vector. The analyst was then tasked with analyzing the data and making predictions on future complications regarding this attack vector. Which of the following types of analysis is the security analyst MOST likely conducting? A. Trend analysis B. Behavior analysis C. Availability analysis D. Business analysis C. >>>6. An incident response report indicates a virus was introduced through a remote host that was connected to corporate resources. A cybersecurity analyst has been asked for a recommendation to solve this issue. Which of the following should be applied? A. MAC B. TAP C. NAC D. ACL A. >>>7. A reverse engineer was analyzing malware found on a retailer's network and found code extracting track data in memory. Which of the following threats did the engineers MOST likely uncover? A. POS malware B. Rootkit C. Key logger D. Ransomware D. E. >>>8. Based on the above information, which of the following should the system administrator do? (Select TWO). A. Verify the vulnerability using penetration testing tools or proof-of-concept exploits. B. Review the references to determine if the vulnerability can be remotely exploited. C. Mark the result as a false positive so it will show in subsequent scans D. Configure a network-based ACL at the perimeter firewall to protect the MS SOL port E. Implement the proposed solution by installing Microsoft patch 0316333. D. E. >>>A cybersecurity consultant is reviewing the following output from a vulnerability scan against a newly installed MS SOL Server 2012 that is slated to go into production in one week: summary The remote MS SQL server is vulnerable to the Hello overflow Solution Install Microsoft Patch Q316333 or disable the Microsoft SQL Server service or use a firewall to protect the MS SQL port References MSB: MS02-043, MS02-056, MS02-061 CVE: CVE-2002-1123 BID: 5411 Other: IAVA 2002-B-0007 Based on the above information, which of the following should the system administrator do? (Select TWO) A. Verify the vulnerability using penetration testing tools or proof-of-concept exploits B. Review the references to determine if the vulnerability can be remotely exploited C. Mark the result as a false positive so it will show in subsequent scans D. Configure a network-based ACL at the perimeter firewall to protect the MS SQL port E. Implement the proposed solution by installing Microsoft patch Q316333 D. >>>9. Datacenter access is controlled with proximity badges that record all entries and exits from the datacenter. The access records are used to identify which staff members accessed the data center in the event of equipment theft. Which of the following MUST be prevented in order for this policy to be effective? A. Password reuse B. Phishing C. Social engineering D. Tailgating A. >>>10. A security professional is analyzing the results of a network utilization report. The report includes the following information: IP Address Server Name Server Uptime Historical Current 172.20.20.58 web.srvr.03 30D 12H 52M 009S 41.3GB 37.2GB 172.20.1.215 dev.web.srvr.01 30D 12H 52M 009S 1.81GB 2.2GB 172.20.1.22 hr.dbprod.01 30D 12H 17M 009S 2.24GB 29.97GB 172.20.1.26 mrktg.file.srvr.02 30D 12H 41M 009S 1.23GB 0.34GB 172.20.1.28 accnt.file.srvr.01 30D 12H 52M 009S 3.62GB 3.57GB 172.20.1.30 R&D.file.srvr.01 1D 4H 22M 01S 1.24GB 0.764GB Which of the following servers needs further investigation? A. hr.dbprod.01 B. R&D.file.srvr.01 C. mrktg.file.srvr.02 D. web.srvr.03 A. >>>11. Several users have reported that when attempting to save documents in team folders, the following message is received: The File Cannot Be Copied or Moved - Service Unavailable Upon further investigation, it is found that the syslog server is not obtaining log events from the file server to which the users are attempting to copy files. Which of the following is the MOST likely scenario causing these issues? A. The network is saturated, causing network congestion B. The file server is experiencing high CPU and memory utilization C. Malicious processes are running on the file server D. All the available space on the file server is consumed C. >>>12. A security analyst has created an image of a drive from an incident. Which of the following describes what the analyst should do NEXT? A. The analyst should create a backup of the drive and then hash the drive. B. The analyst should begin analyzing the image and begin to report findings C. The analyst should create a hash of the image and compare it to the original drive's hash D. The analyst should create a chain of custody document and notify stakeholders C. >>>13. After completing a vulnerability scan, the following output was noted: CVE-2011-3389 QID 42366 - SSLv3.- / TLSv1.0 Protocol weak CBC mode Server side vulnerability Check with: openssl s_client -connect qualys.jive.mobile.com:443 - tlsl -cipher "AES:CAMELLA:SEED:3DES:DES" Which of the following vulnerabilities has been identified? A. PKI transfer vulnerability B. Active Directory encryption vulnerability C. Web application cryptography vulnerability D. VPN tunnel vulnerability C. >>>14. A cybersecurity analyst traced the source of an attack to compromised user credentials. Log analysis revealed that the attacker successfully authenticated from an unauthorized foreign country. Management asked the security analyst to research and implement a solution to help mitigate attacks based on compromised passwords. Which of the following should the analyst implement? A. Self-service password reset B. Single sign-on C. Context-based authentication D. Password complexity [Show More]
Last updated: 3 years ago
Preview 1 out of 42 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

CySA Bundled Exams with complete solution; Everything you need is here.
CySA+ 231 More Questions with 100% Correct Answers CySA+ 2022 Questions and Answers with complete solution CySA+ Final - Study Guide 2022 with complete solution Final SAS study guide Question...
By Professor Lynne 3 years ago
$18
17
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 05, 2022
Number of pages
42
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 05, 2022
Downloads
0
Views
163