Practice Questions CNA State Exam
$ 10

Lymphatic system Complete notes Handwritten Clear
$ 11

AHIMA CCS EXAM 2023 ACTUAL QUESTIONS WITH VERIFIED COMPLETE SOLUTIONS/A+ SCORE
$ 16.5

eBook Bio-derived Carbon Nanostructures 1st Edition By Bharat Apparao Bhanvase, Divya Prakash Barai
$ 30

Progression: Field Tech V -VI Conventional With Complete Solution
$ 13

My California Permit Practice Test Questions with Answers. 100% Proven pass rate.
$ 6

eBook [PDF] The Communication Playbook 2nd Edition By Teri Kwal Gamble, Michael Gamble
$ 30

eBook Viral, Parasitic, Bacterial, and Fungal Infections 1st Edition By Debasis Bagchi , Amitava Das, Bernard William Downs
$ 30

eBook Urban Resilience to the Climate Emergency Unravelling the transformative potential of institutional and grassroots initiatives (The Urban Book Series) 1st Edition By Isabel Ruiz-Mallén , Hug March , Mar Satorras
$ 29
PSYC 140 MODULE 6 EXAM
$ 14

INSTRUCTOR’S TESTING MANUAL FOR USING & UNDERSTANDING MATHEMATICS, A QUANTITATIVE REASONING APPROACH SEVENTH EDITION
$ 17.5
HESI RN COMPASS EXIT EXAM V2 (NGN) 2025-26 QUESTIONS & 100% CORRECT ANSWERS LATEST UPDATE/A+GRADE
$ 9.5
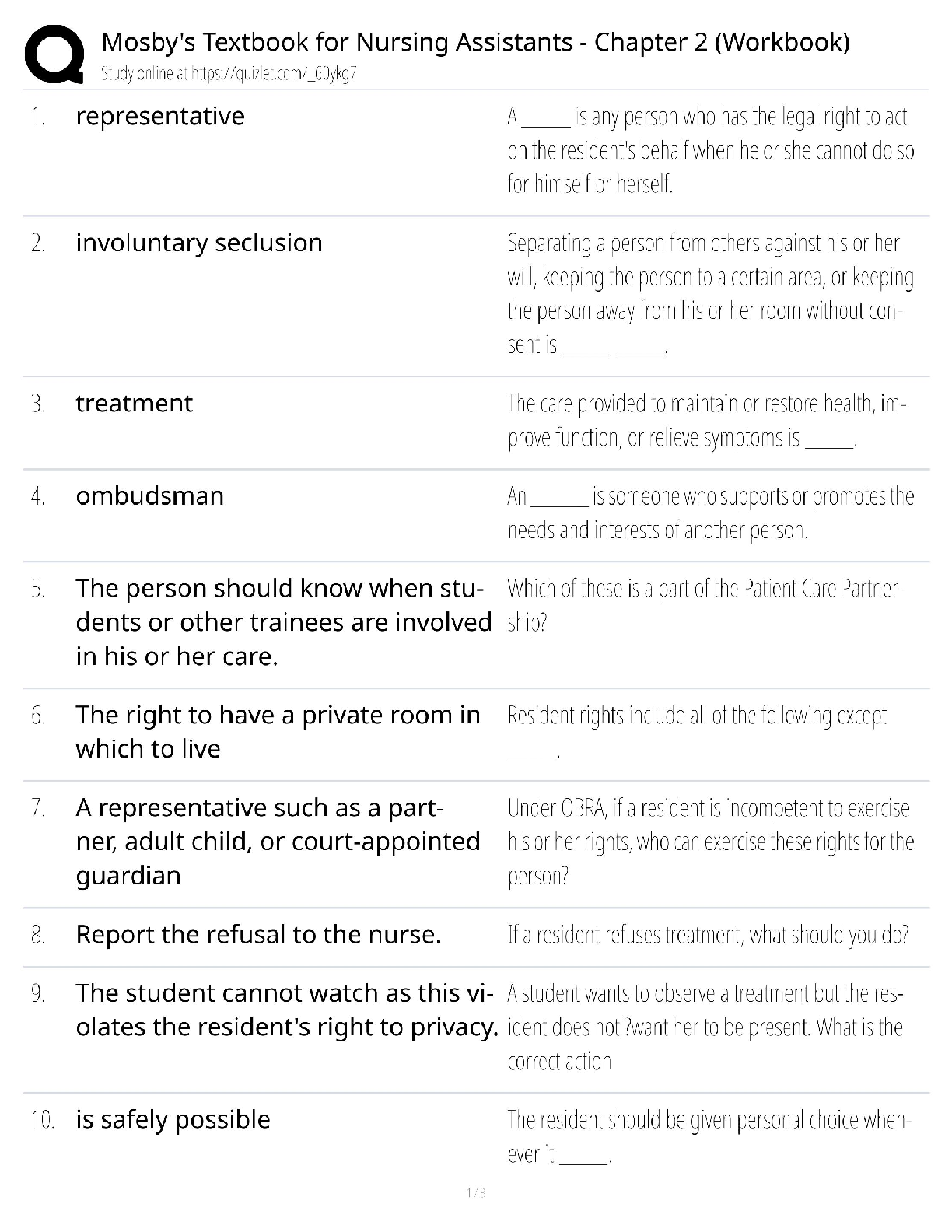
Mosby's Textbook for Nursing Assistants - Chapter 2 Workbook / CNA Study Guide / 2025 Edition / Score 100% / Test Bank
$ 18.5

Corrections Officer Exam Part 1 | 25 Questions with 100% Correct Answers | Updated & Verified
$ 3

eBook Exosomal RNA 1st Edition By Debalina Bhattacharya, Mainak Mukhopadhyay, Kursad Turksen
$ 30
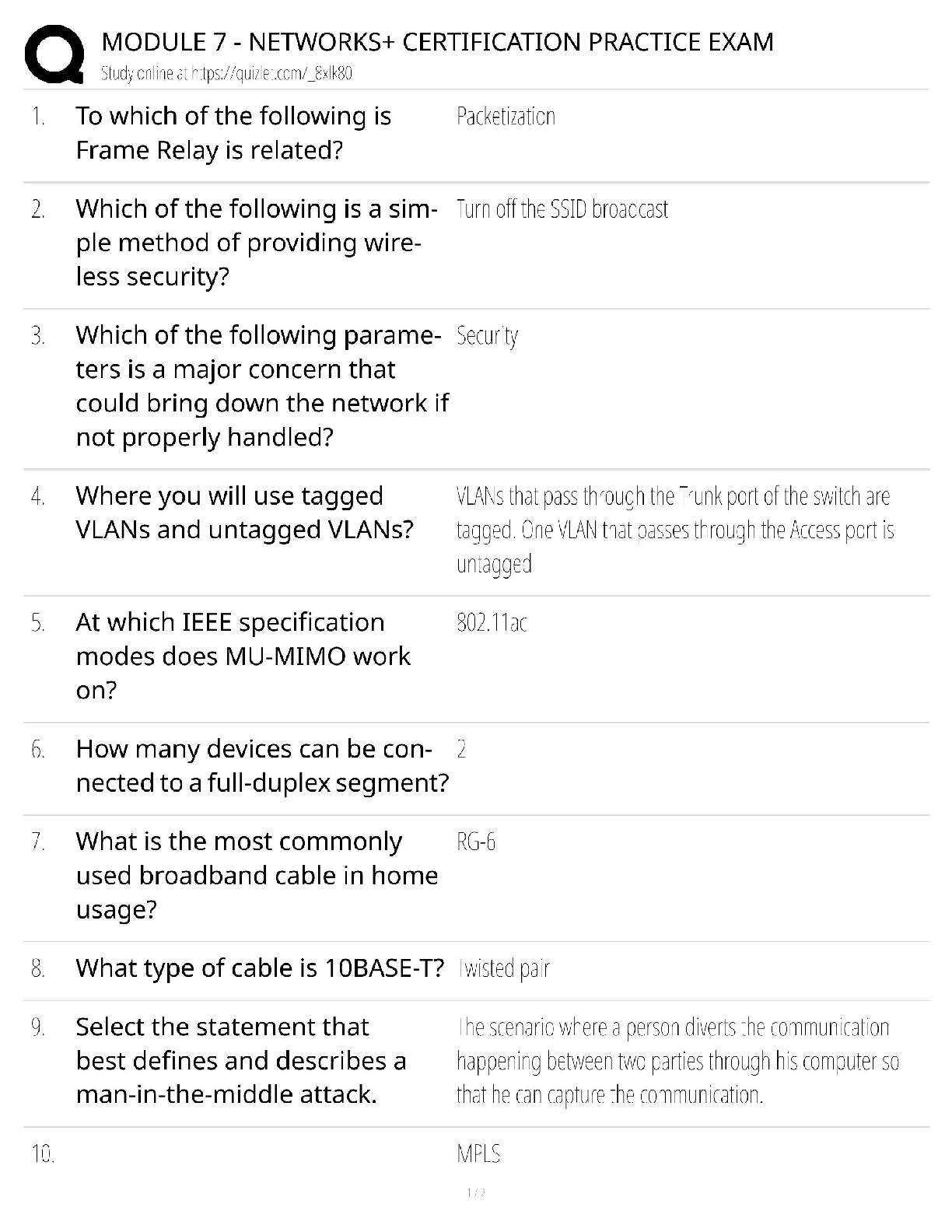
Network+ Module 7 Practice Exam / 2024 Networks+ Prep / N10-008 Test Questions & Simulations
$ 12.5

student exploration dehydration synthesis gizmos answers
$ 8

eBook (Image OCR) Murach's Python Programming 2e Joel Murach, Michael Urban
$ 29

ATI RN COMPREHENSIVE PREDICTOR 2
$ 20.5

Test Bank for Database Systems, 2.0 Edition by Nenad Jukic
$ 39

eBook [PDF] Purchasing & Supply Chain Management 7th Edition By Robert M. Monczka, B. Handfield, Larry C., Jame
$ 27
.png)
> GCE Physics B H557/01: Fundamentals of physics Advanced GCE Mark Scheme for Autumn 2021
$ 10
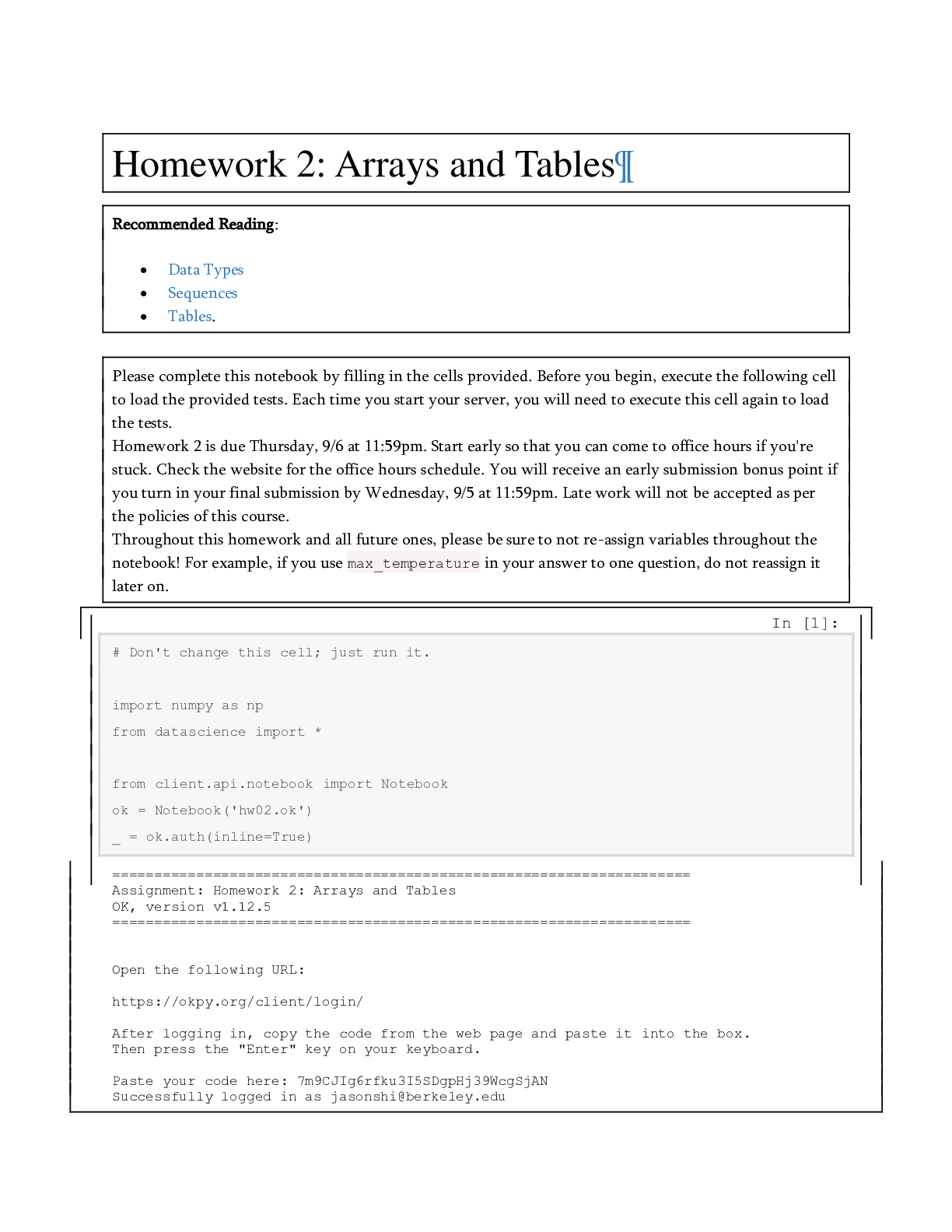
DATA MISC Homework 2: Arrays and Tables | University of California, Berkeley
$ 6

TRAFFIC SUPERVISOR EXAM | QUESTIONS & 100% CORRECT ANSWERS (VERIFIED) | LATEST UPDATE | GRADE A+