CompTIA Cybersecurity Analyst (CySA+) - Module 1: Threat Management
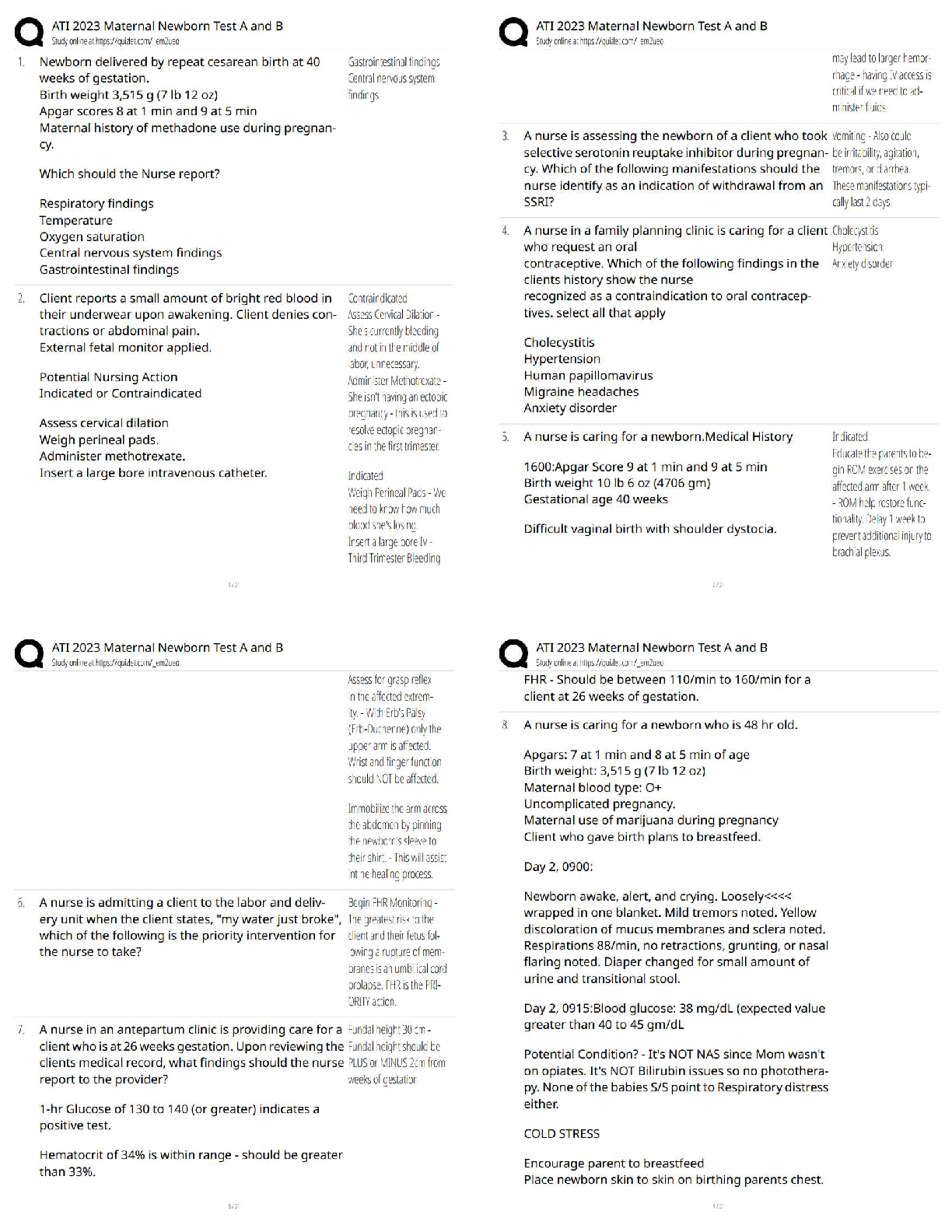
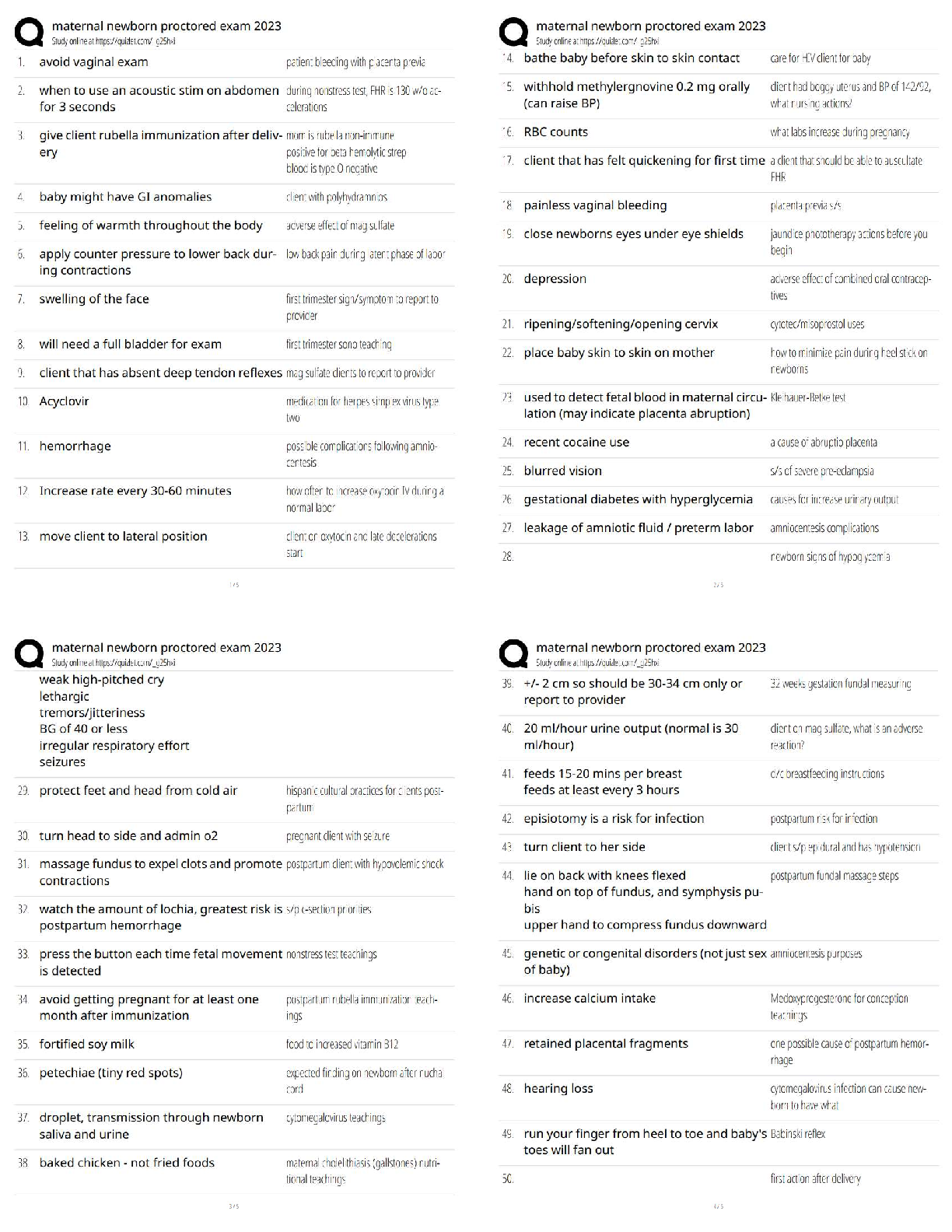
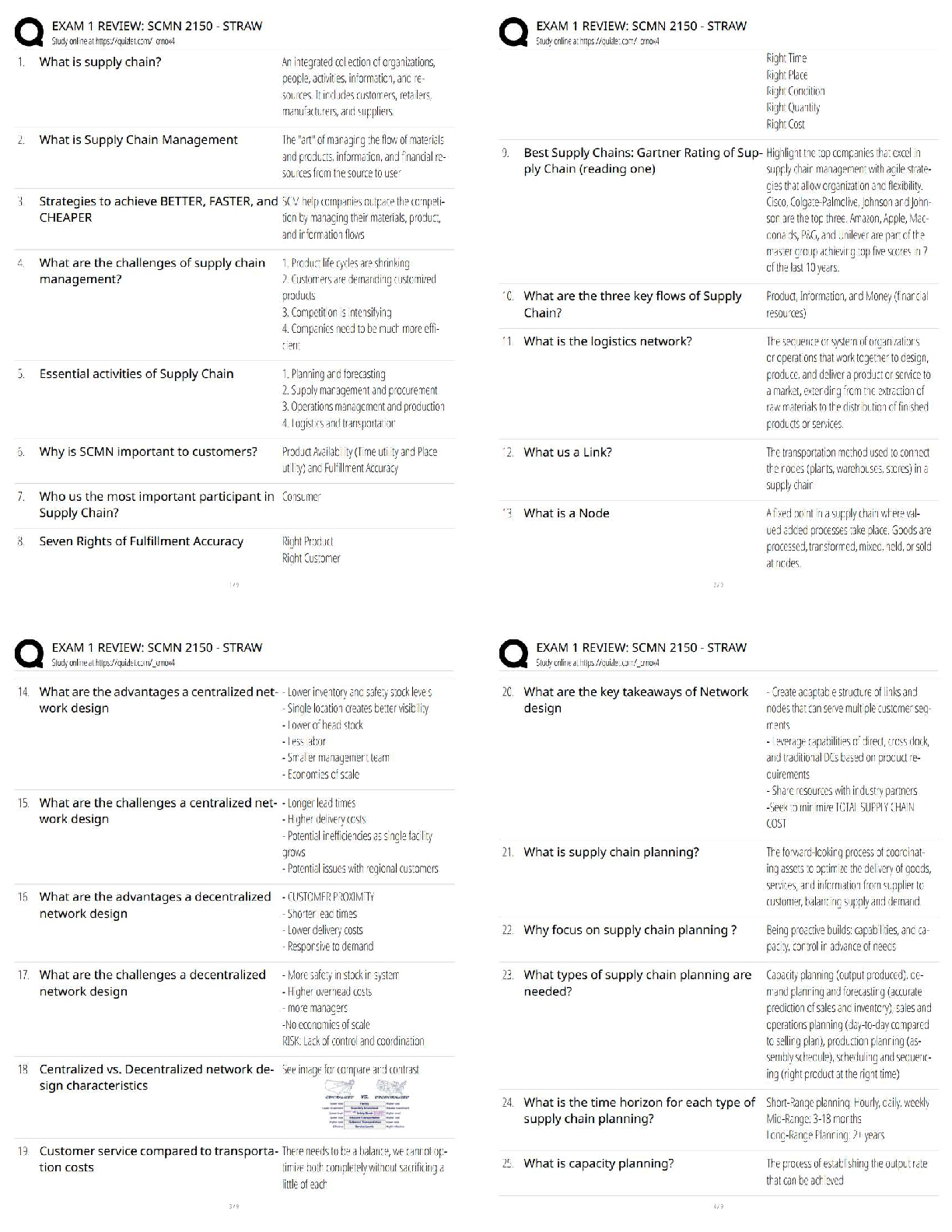
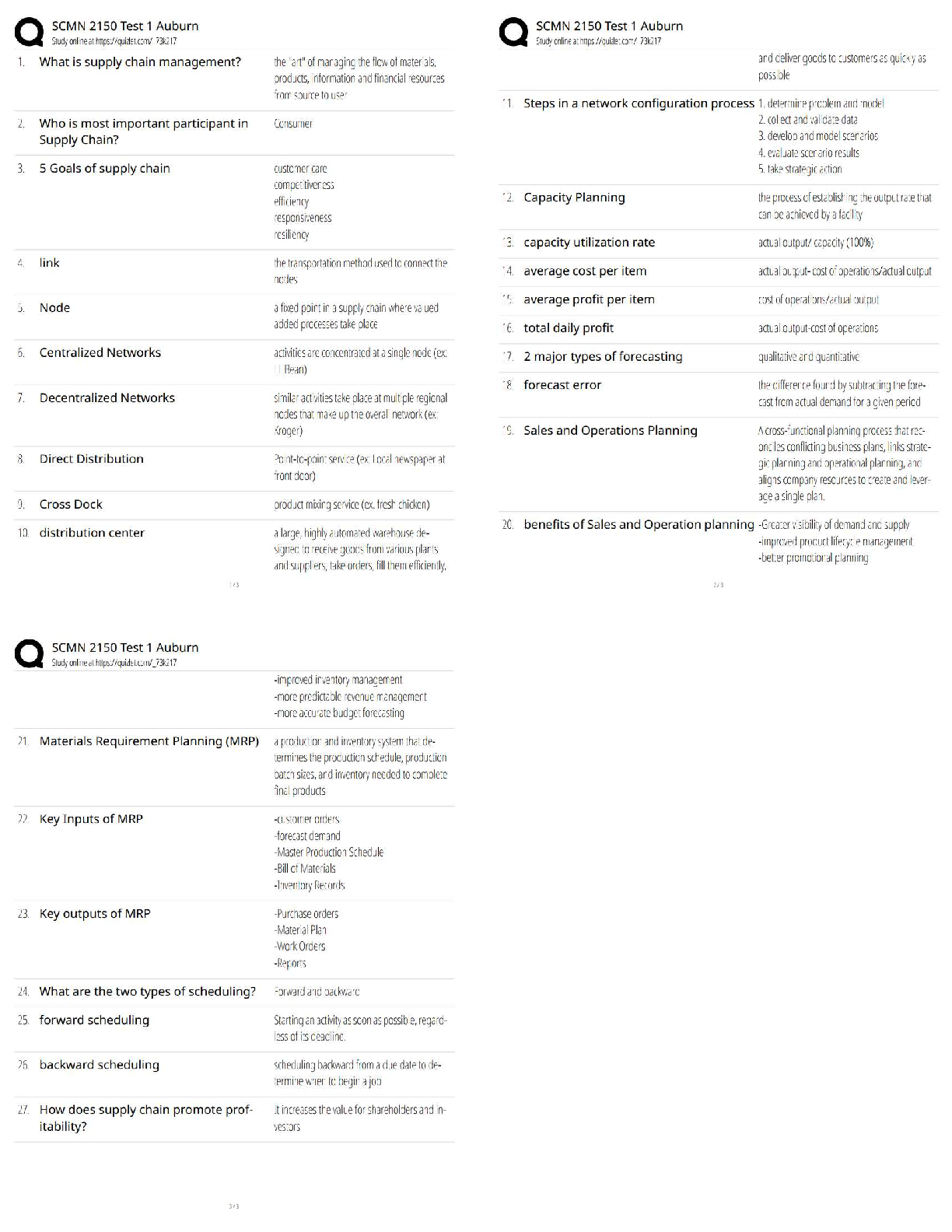
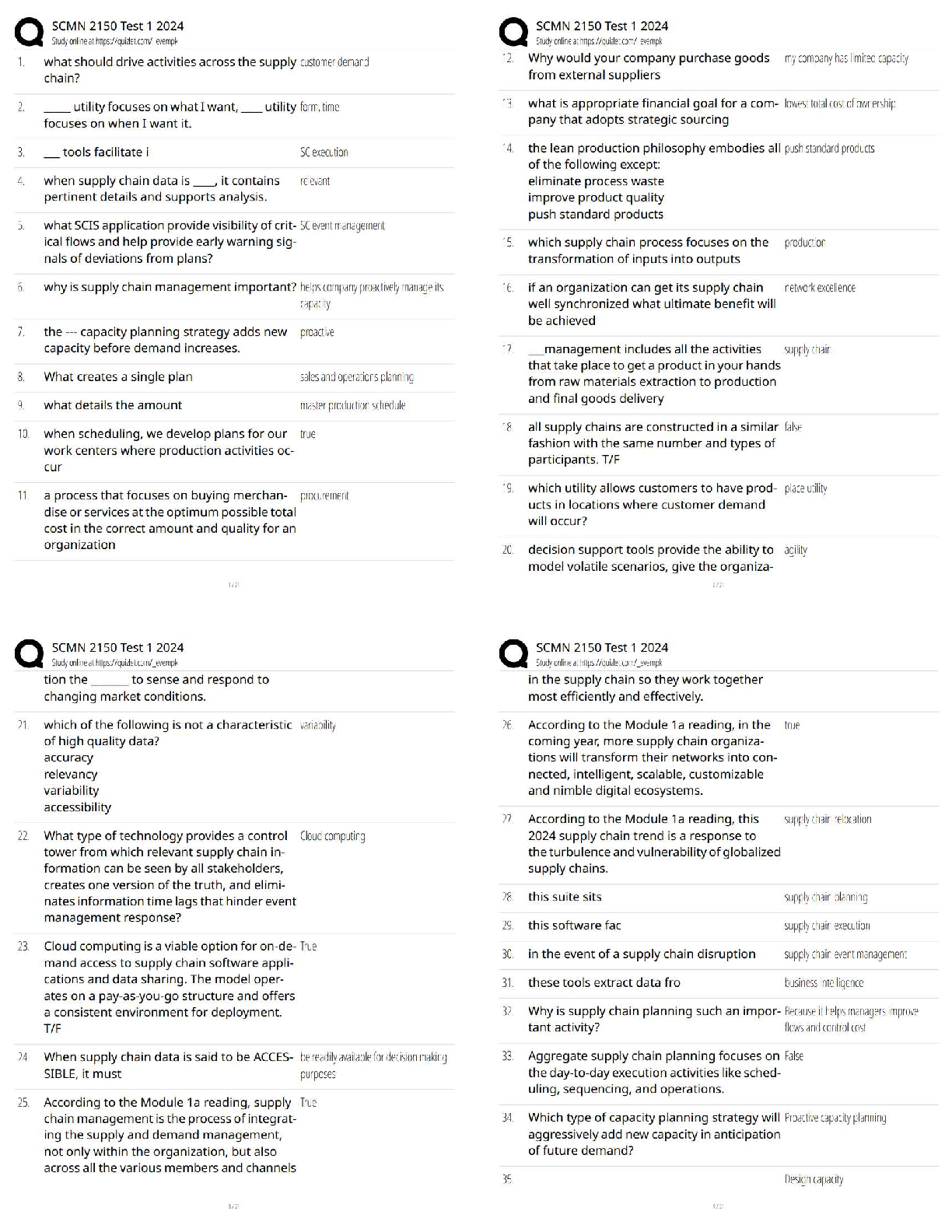
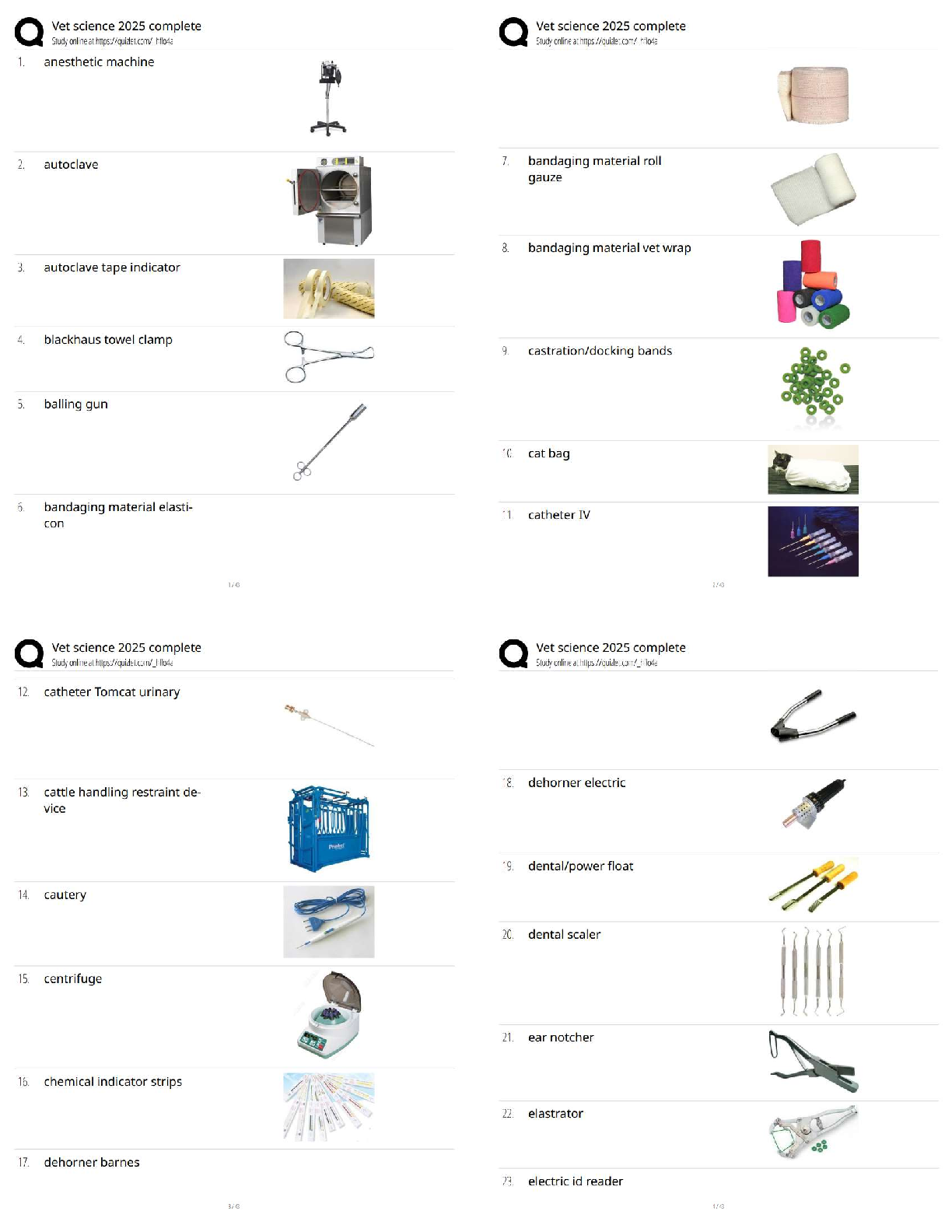
Which of the following is an alternate name for topology Discovery?
Fingerprinting
Footprinting
Pivotprinting
Sniffing -Answer- Footprinting
...
CompTIA Cybersecurity Analyst (CySA+) - Module 1: Threat Management
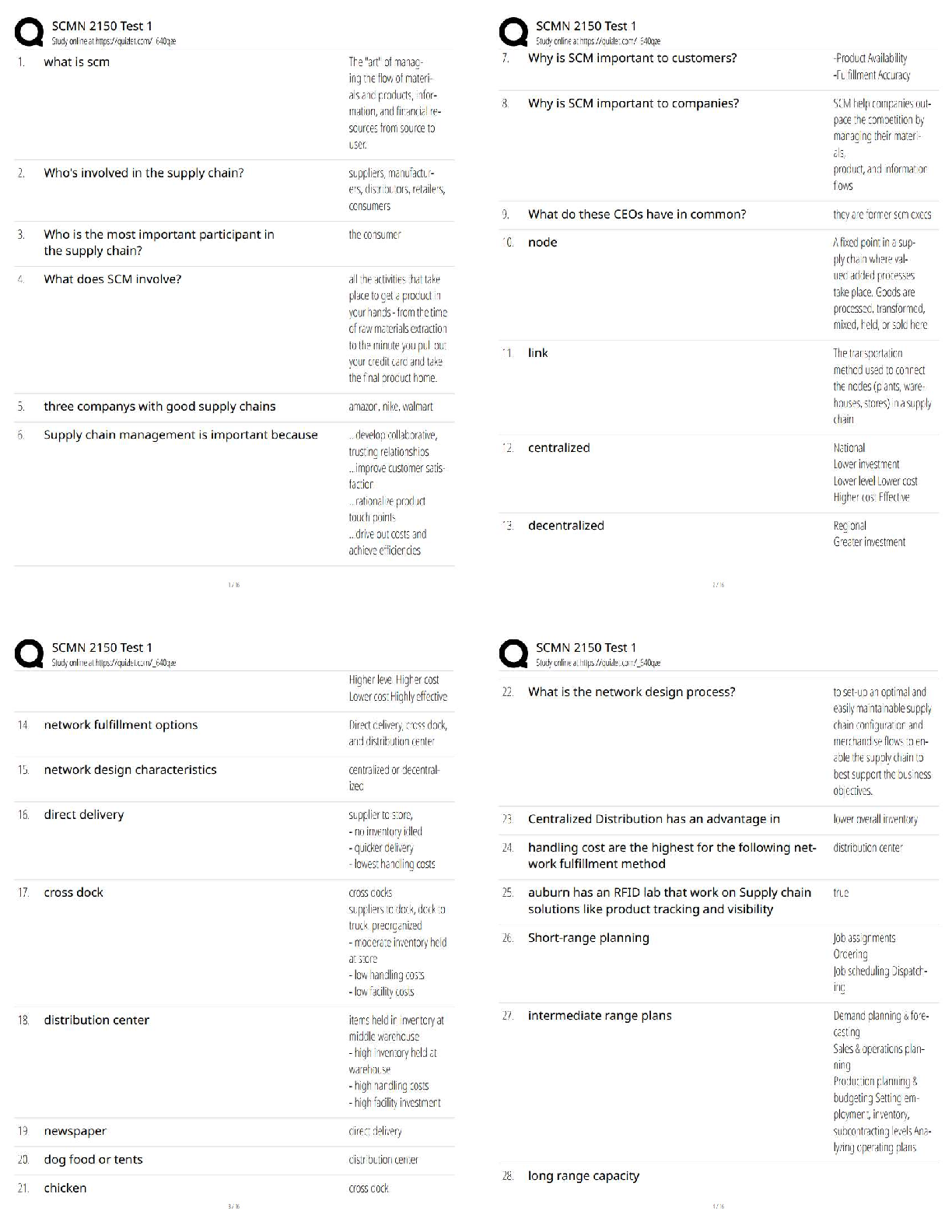
Which of the following is an alternate name for topology Discovery?
Fingerprinting
Footprinting
Pivotprinting
Sniffing -Answer- Footprinting
What process allows an analyst to discover the operating system and version of a system?
Service Discovery
Topology Discovery
Log Review
OS Fingerprinting -Answer- OS Fingerprinting
In what order is an ACL processed?
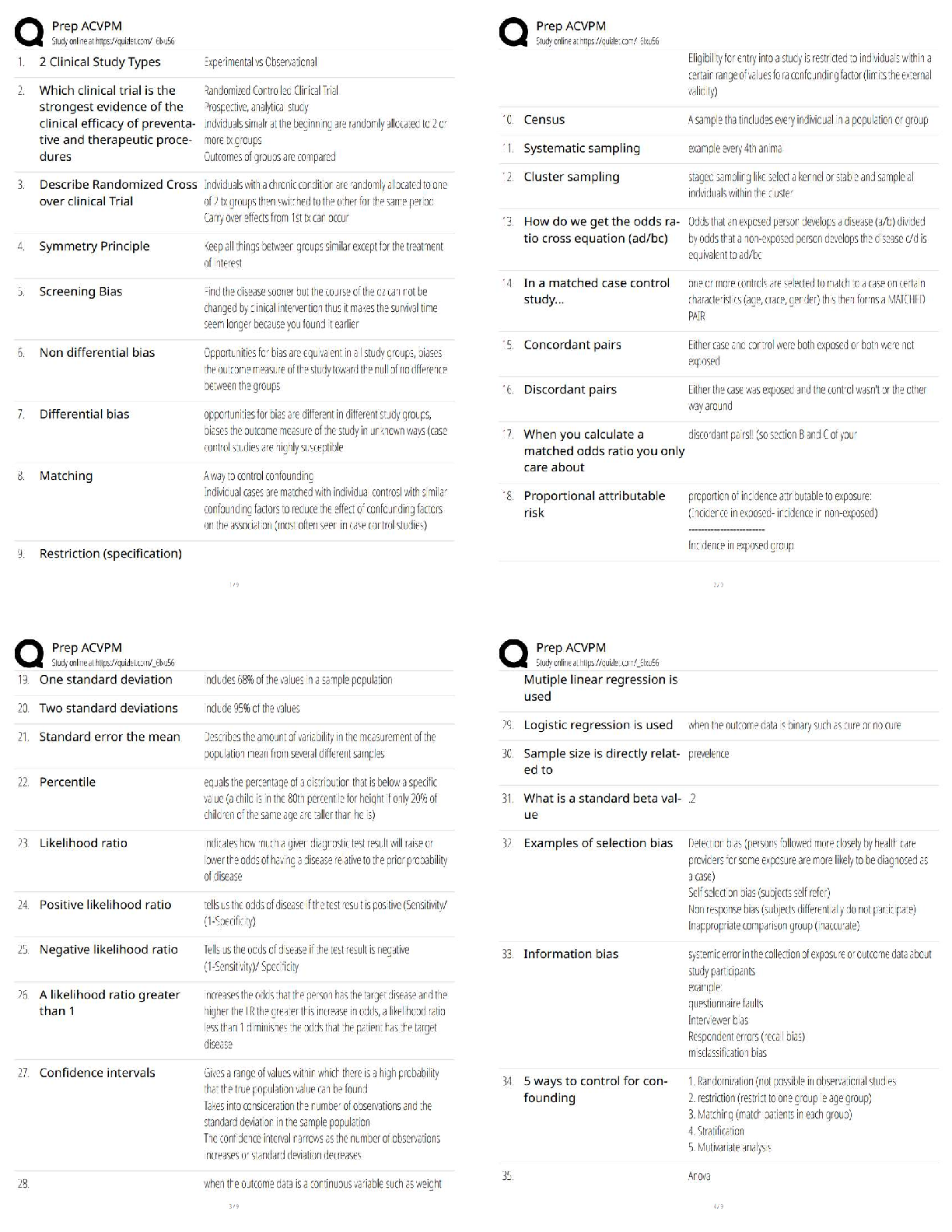
From top to bottom
From bottom to top
Most specific entry first
Least specific entry first -Answer- From top to bottom
What is the unwritten rule at the bottom of a firewall's ACL?
Implicit Allow
Implicit Deny
Explicit Deny
Explicit Allow -Answer- Implicit Deny
Attackers may potentially collect company emails by searching Google.
True
False -Answer- True
Which process would an attacker use to determine who in a company is most likely to be tricked into giving up company information?
Social Engineering
Phishing
Social Media Profiling
Email Harvesting -Answer- Social Media Profiling
What type of Phishing is sent over a text message specifically?
Vishing
Spear Phishing
SMiShing
Whaling -Answer- SMiShing
Internal DNS servers need to be protected from an attacker to prevent the leakage of email records within a company.
True
False -Answer- False
Due to the amount of a network that is physically wired it is more difficult to prevent access to a physical network than a wireless one.
True
False -Answer- False
Which of the following wireless protocols can be used to best supply security for a wireless network?
WEP
TKIP
WPA2
WPA -Answer- WPA2
A virtual network is more secure network for which of the following reasons?
They are easier to patch
They can't spread viruses
Virtual machines can't compromise their host
They're easier to isolate -Answer- They're easier to isolate
In which way can an IDS protect a network? (Choose all that apply)
Reactively
Proactively
Actively
Passively -Answer- Reactively & Passively
Which of the following methods can be used to delay a scan to avoid detection?
Sparse scanning
Traceroute scan
half-open scan
Randomized scan -Answer- Sparse scanning
Which tool can be used to test many different port states on a Linux or Windows device?
Firewall
Packet Analyze
Netstat
Syslog -Answer- Netstat
Of the IDS/ IPS systems which will have the best ability to prevent an attack on a network scale?
HIDS
HIPS
NIDS
NIPS -Answer- NIPS
Of the IDS/ IPS systems which will be best at protecting a system while minimizing service interruptions?
HIDS
HIPS
NIDS
NIPS -Answer- HIDS
When reviewing a Syslog report which of the following severities would have the highest priority?
0
4
7
10 -Answer- 0
Which of the following Windows commands would allow the user to determine the path that traffic takes through the network.
Traceroute
Netstat
NMAP
Tracert -Answer- Tracert
Spear phishing is when an attacker goes after corporate data by calling up the CEO or other upper-level employees.
True
False -Answer- False
Employees need not be trained in current social engineering attacks as plenty of other countermeasures exist to prevent somebody from falling victim to one of these attacks such as email filters.
True
False -Answer- False
[Show More]














.png)