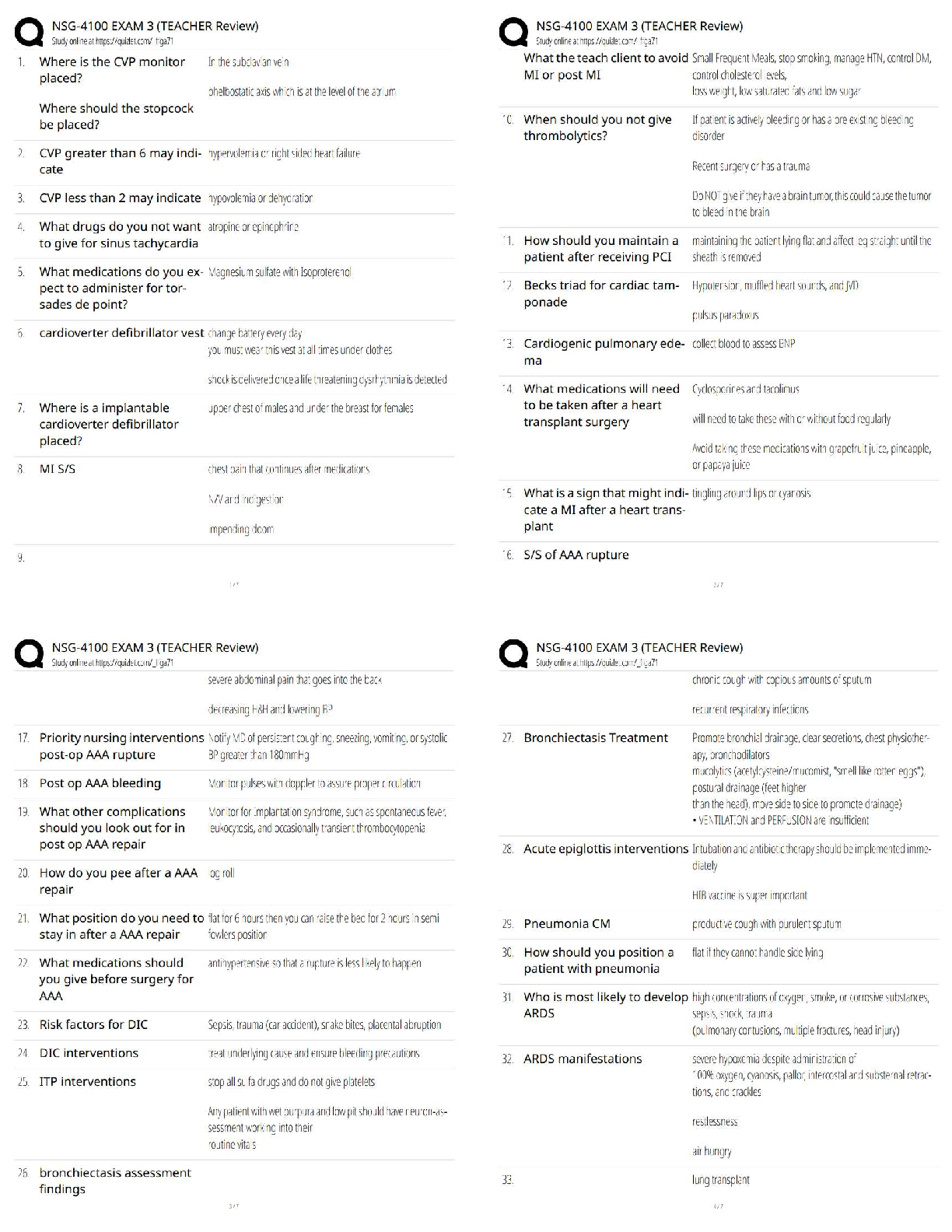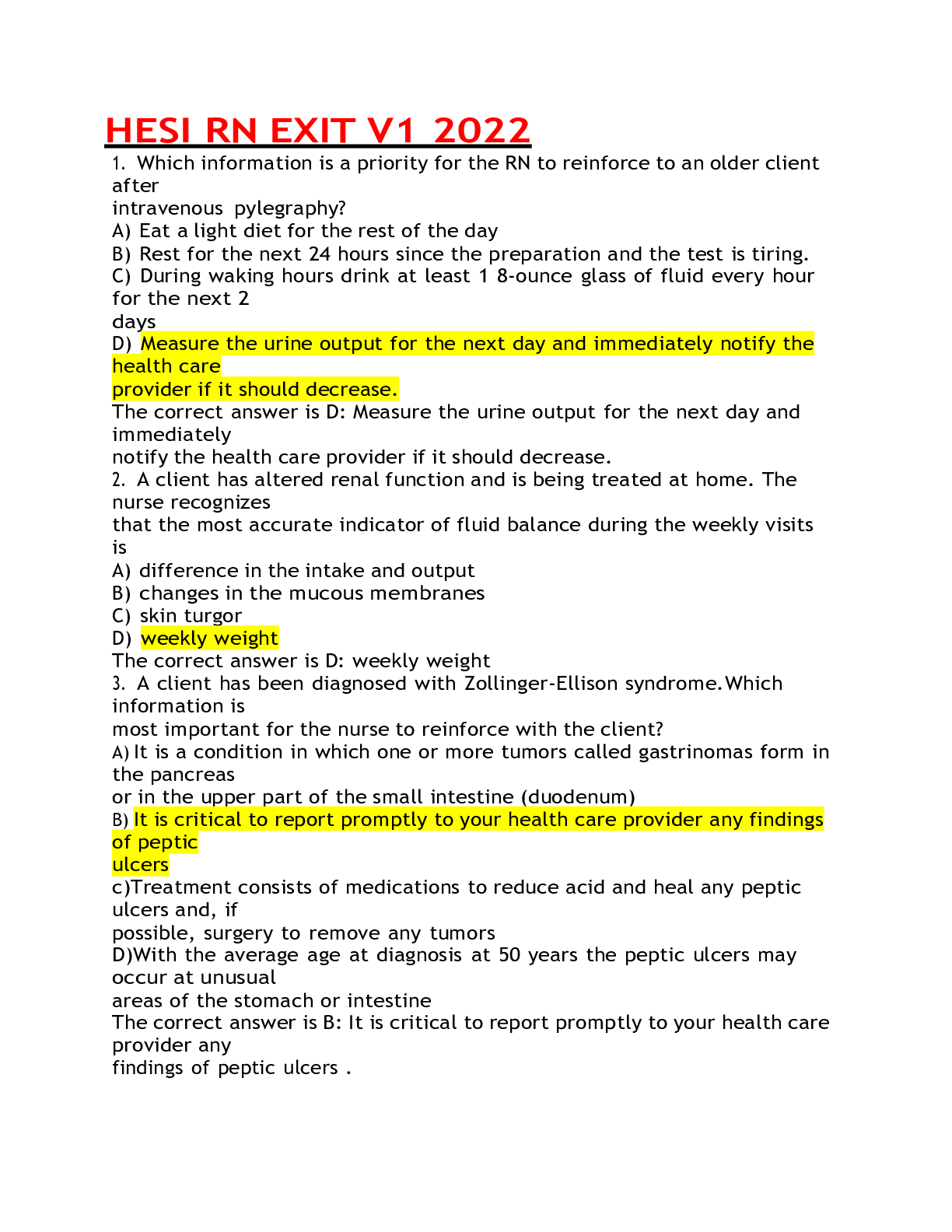
HESI RN EXIT VI 2022
$ 4.5
eBook NMR Multiplet Interpretation An Infographic Walk-Through 1st Edition By Roman A. Valiulin
$ 30
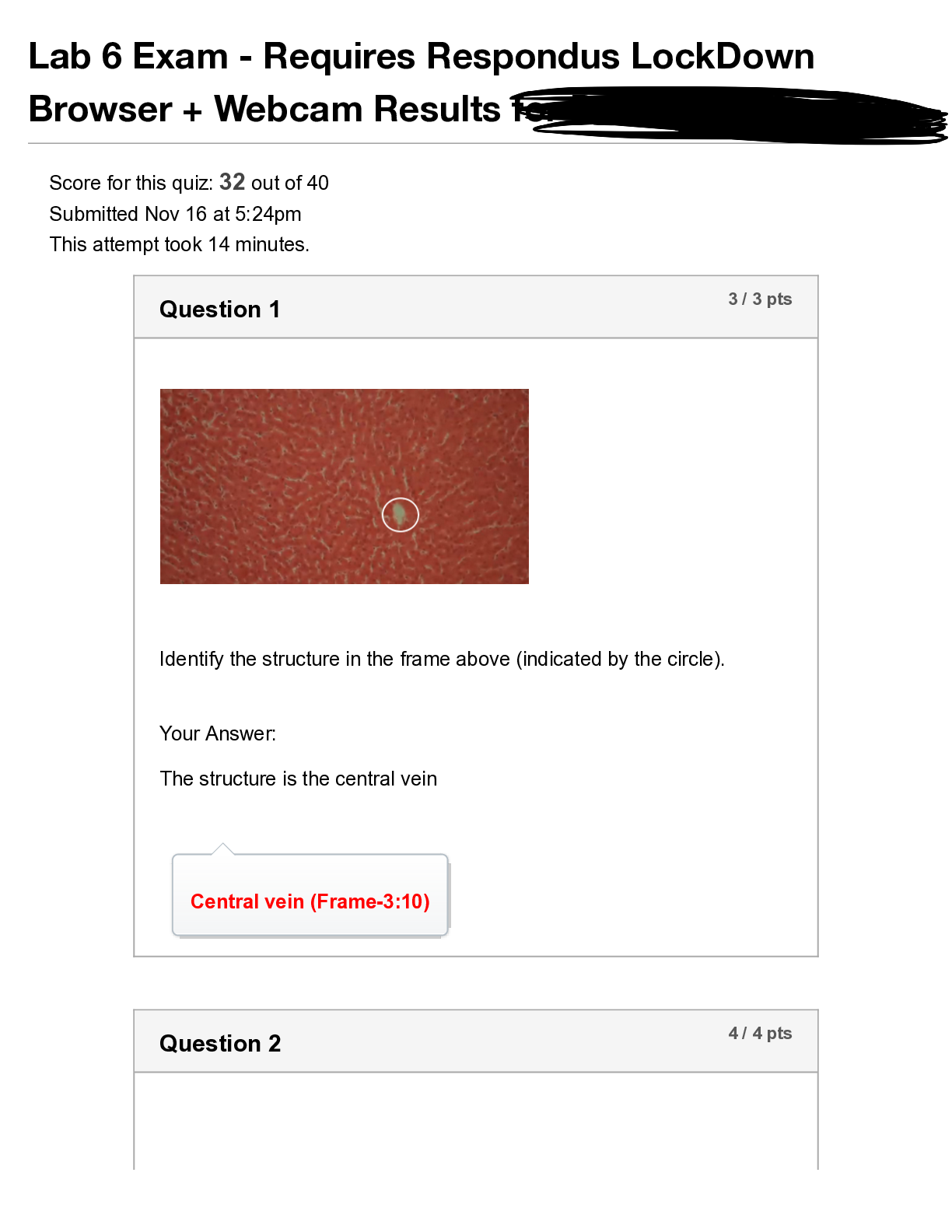
Lab_6_Exam_Essential_Human_Anatomy_and_Physiology_II_with_Lab_|portage learning 2022|All questions examinable
$ 9.5

ATI Medical-Surgical: Oncology: Questions and answers, Rated A+, 2022
$ 6

Florida Atlantic University - EEL 3003HW6F2020.
$ 7

Pearson Edexcel GCE_Further Mathematics_8FM0/21 Mark Scheme_2021 | Further Pure Mathematics 1
$ 6.5
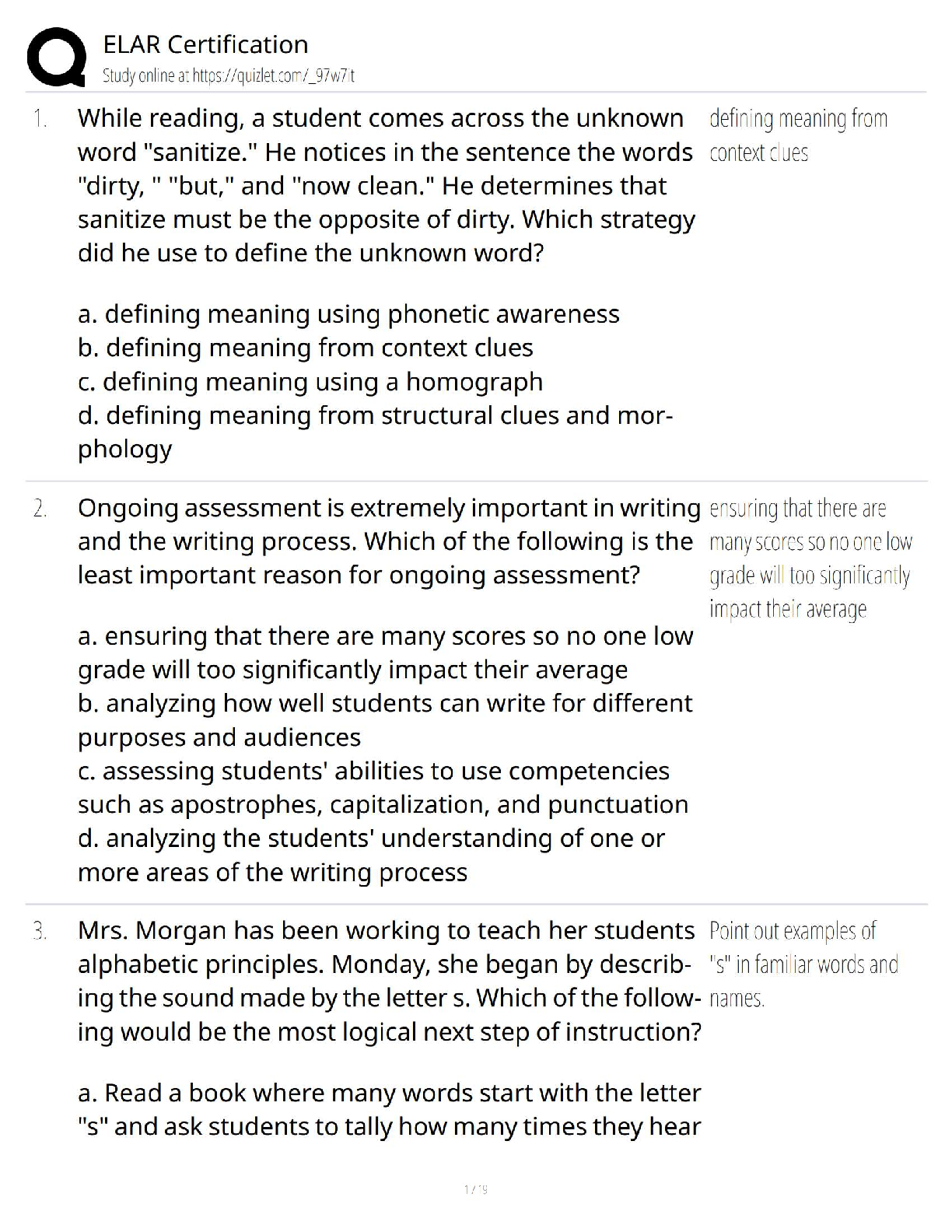
ELAR Certification
$ 21
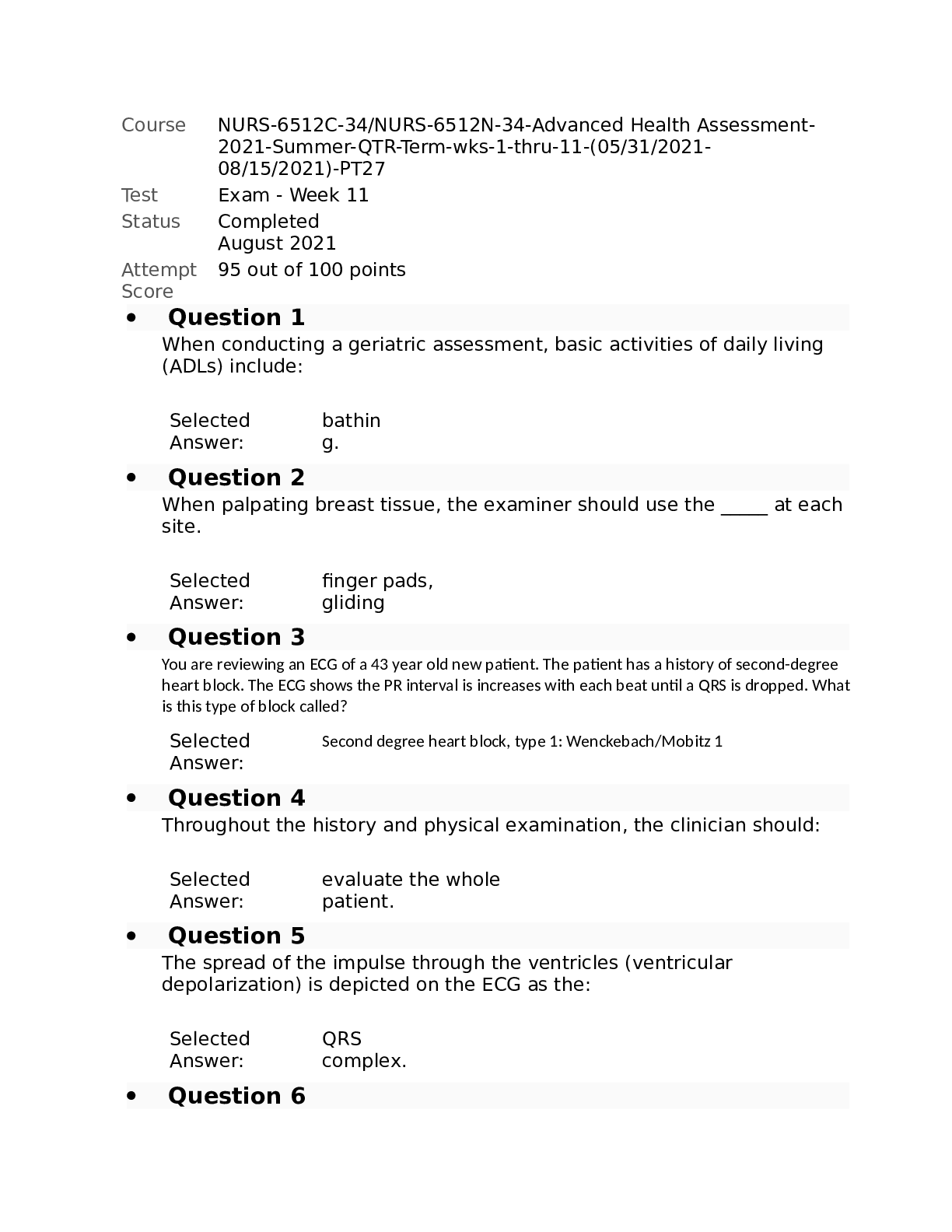
NURS-6512C-34NURS-6512N-34-Advanced Health Assessment Final Week 1 2023 Summer
$ 11

Final Block Study Guide FISDAP Upated
$ 11

GCSE (9-1) Mathematics J560/02 Paper 2 (Foundation Tier) PRACTICE PAPER (SET 3) MARK SCHEME
$ 7.5

2019 HESI EXIT V2
$ 14
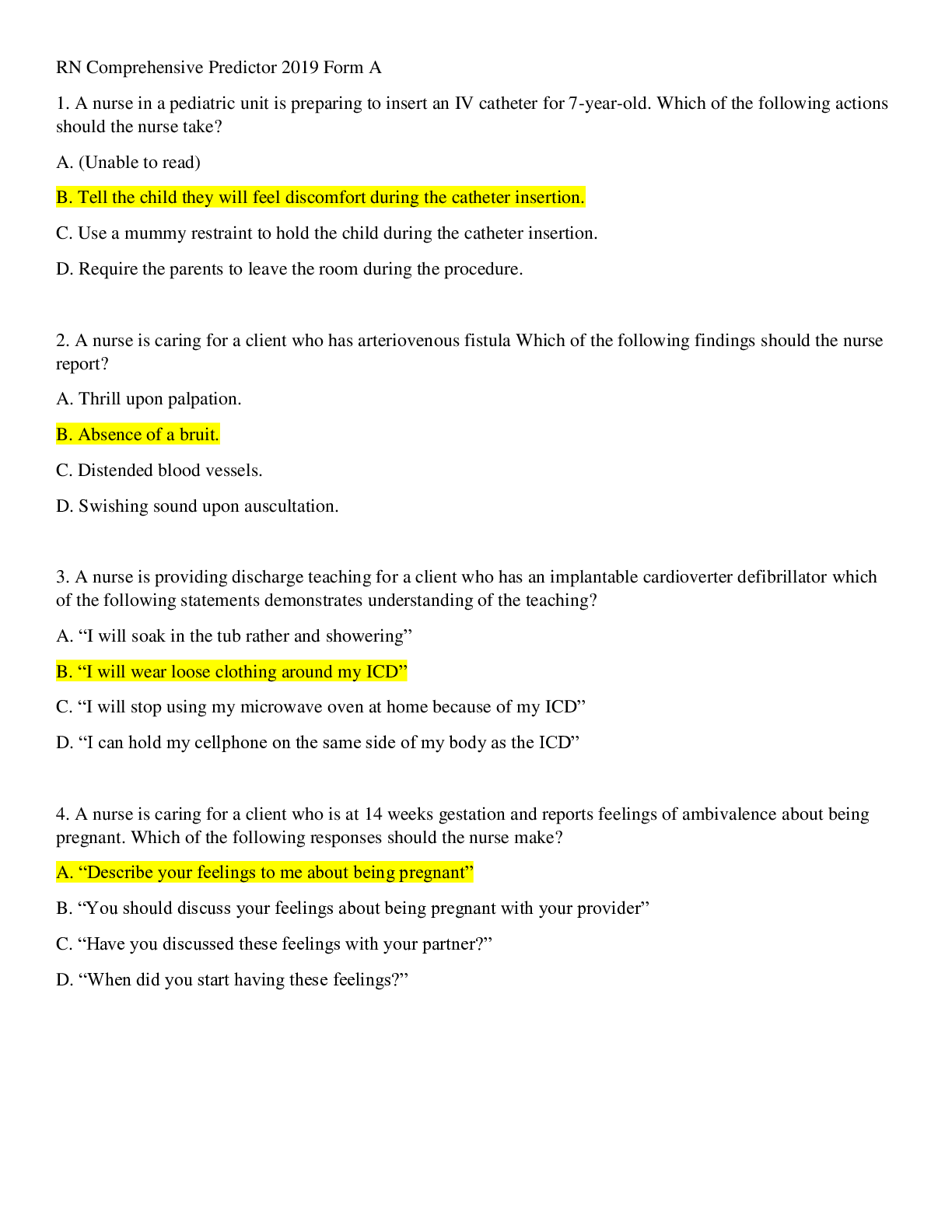
RN Comprehensive Predictor 2019 Form A
$ 9
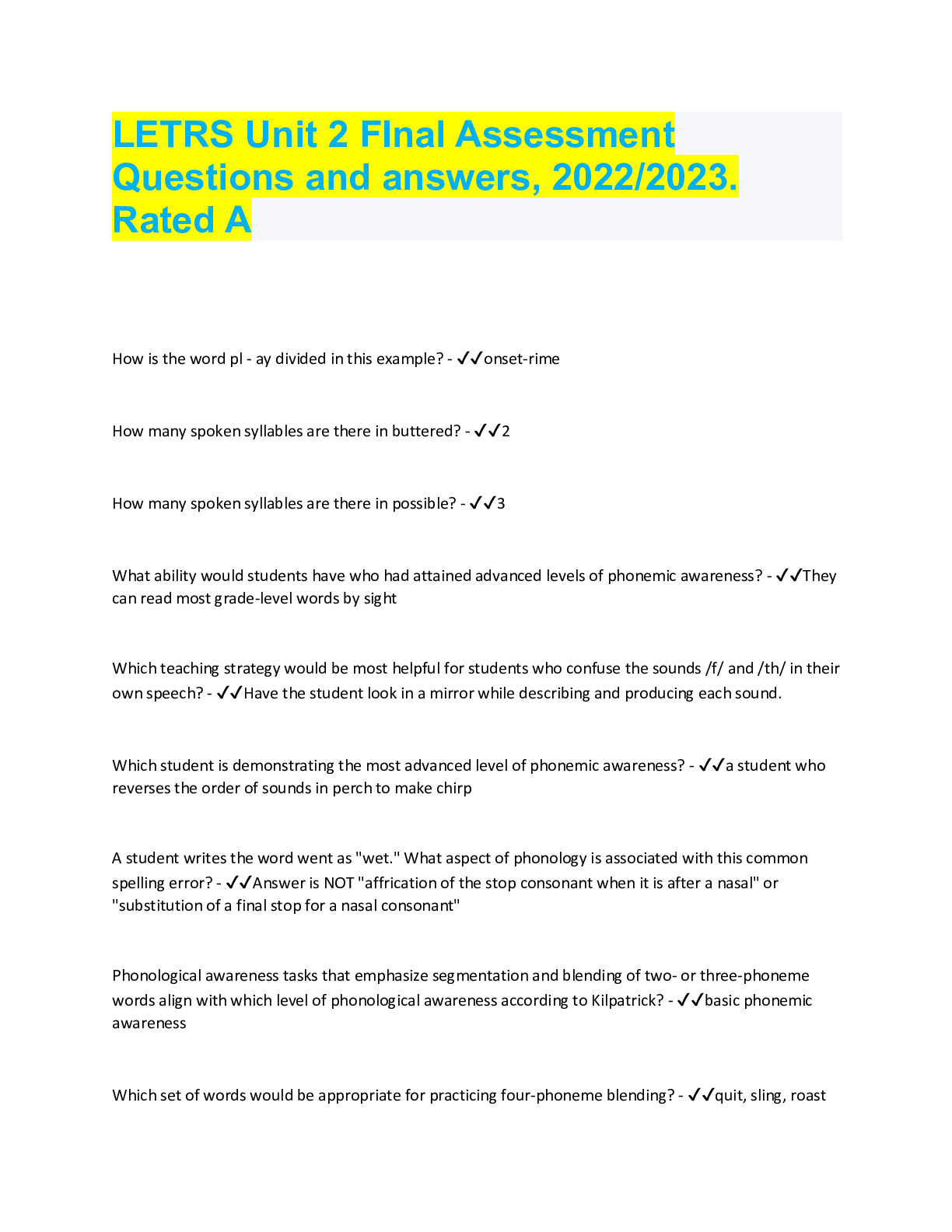
LETRS Unit 2 FInal Assessment Questions and answers, 2022/2023. Rated A
$ 4

SCCJA Cumulative Exam Study Guide 2023 with complete solution
$ 9
DSAC ANNEX E TEST QUESTIONS 2022 (VERIFIED) COMPLETE SOLUTION