Social Sciences > QUESTIONS & ANSWERS > Digital Forensics in Cybersecurity - C840 Study guide 2022 with complete solution (All)
Digital Forensics in Cybersecurity - C840 Study guide 2022 with complete solution
Document Content and Description Below
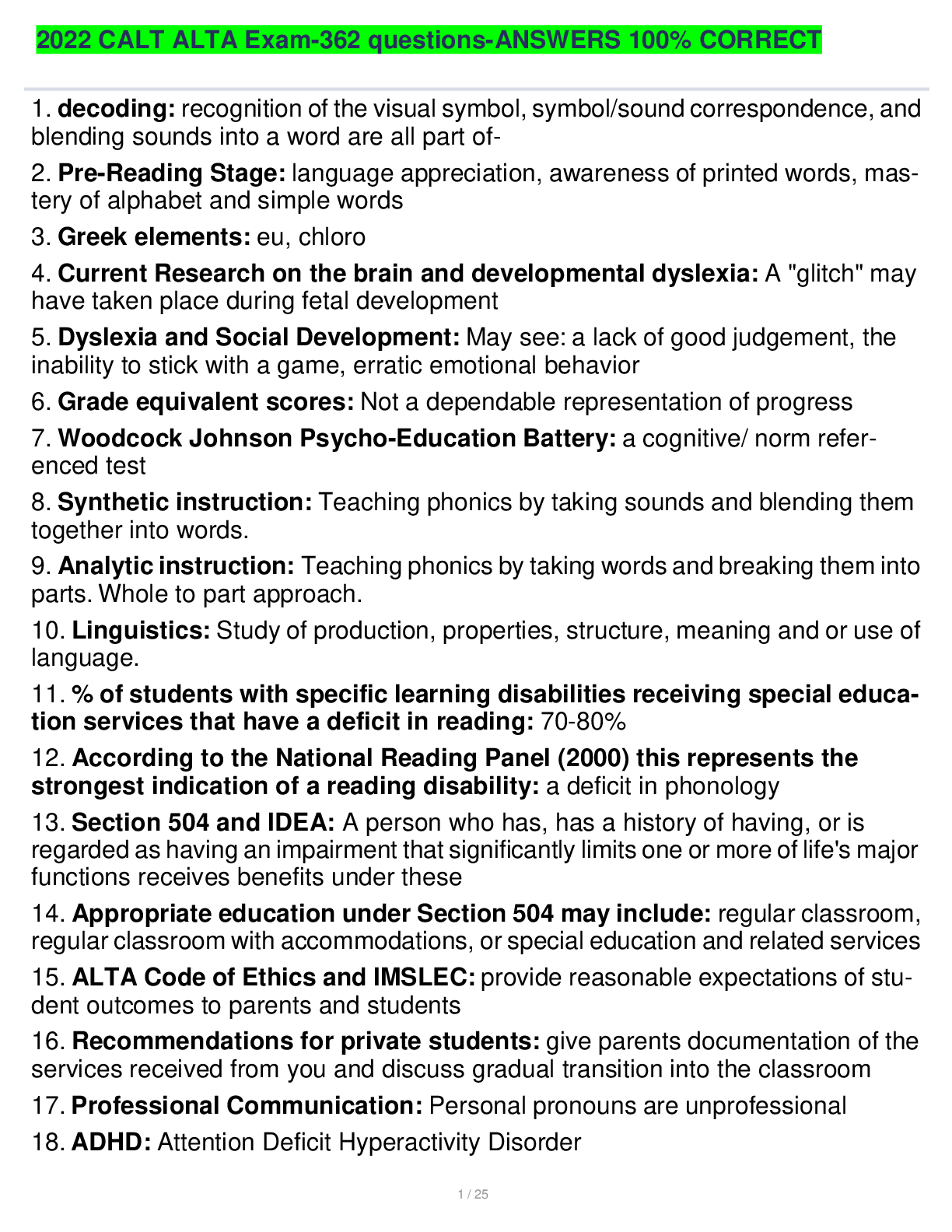
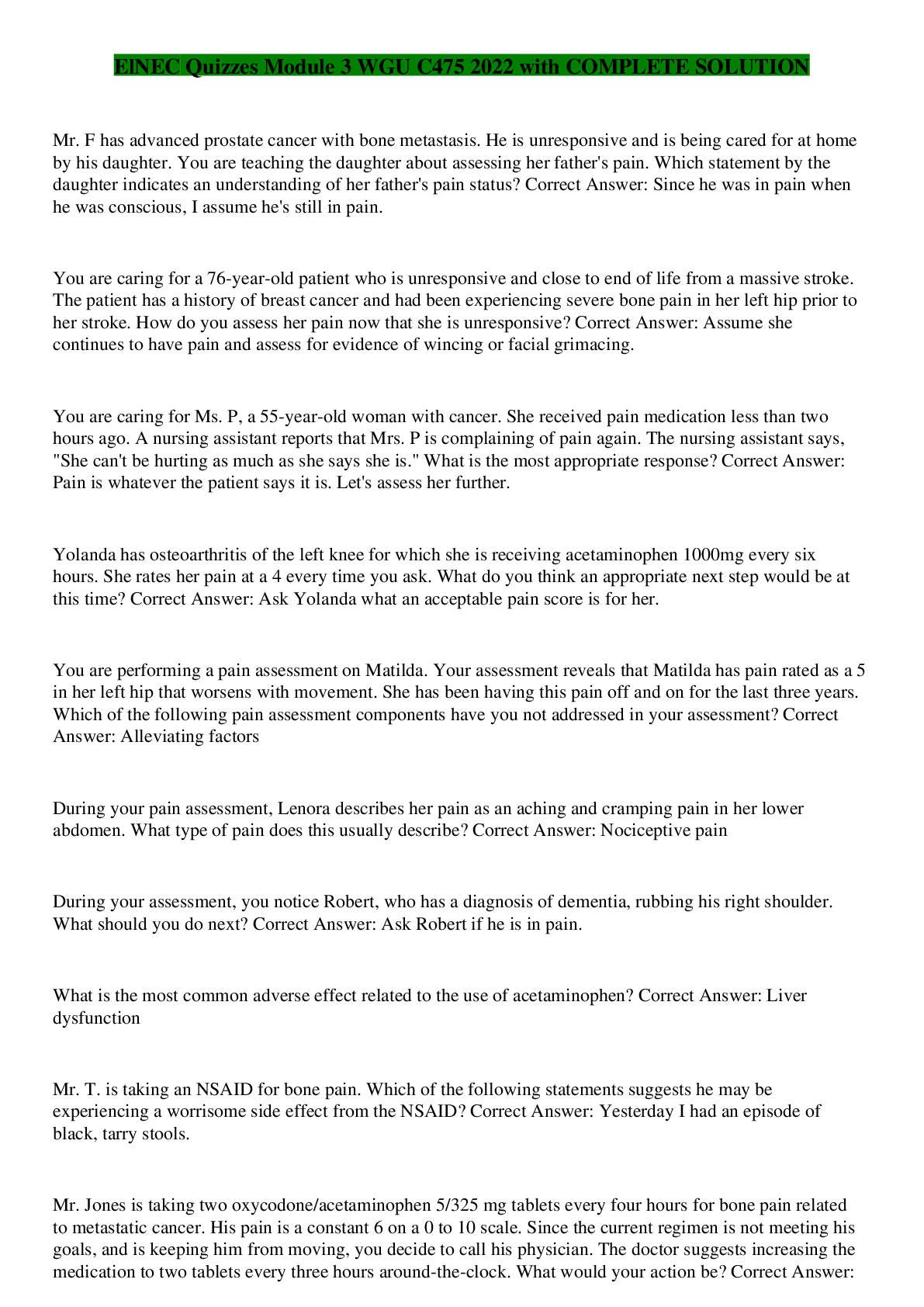
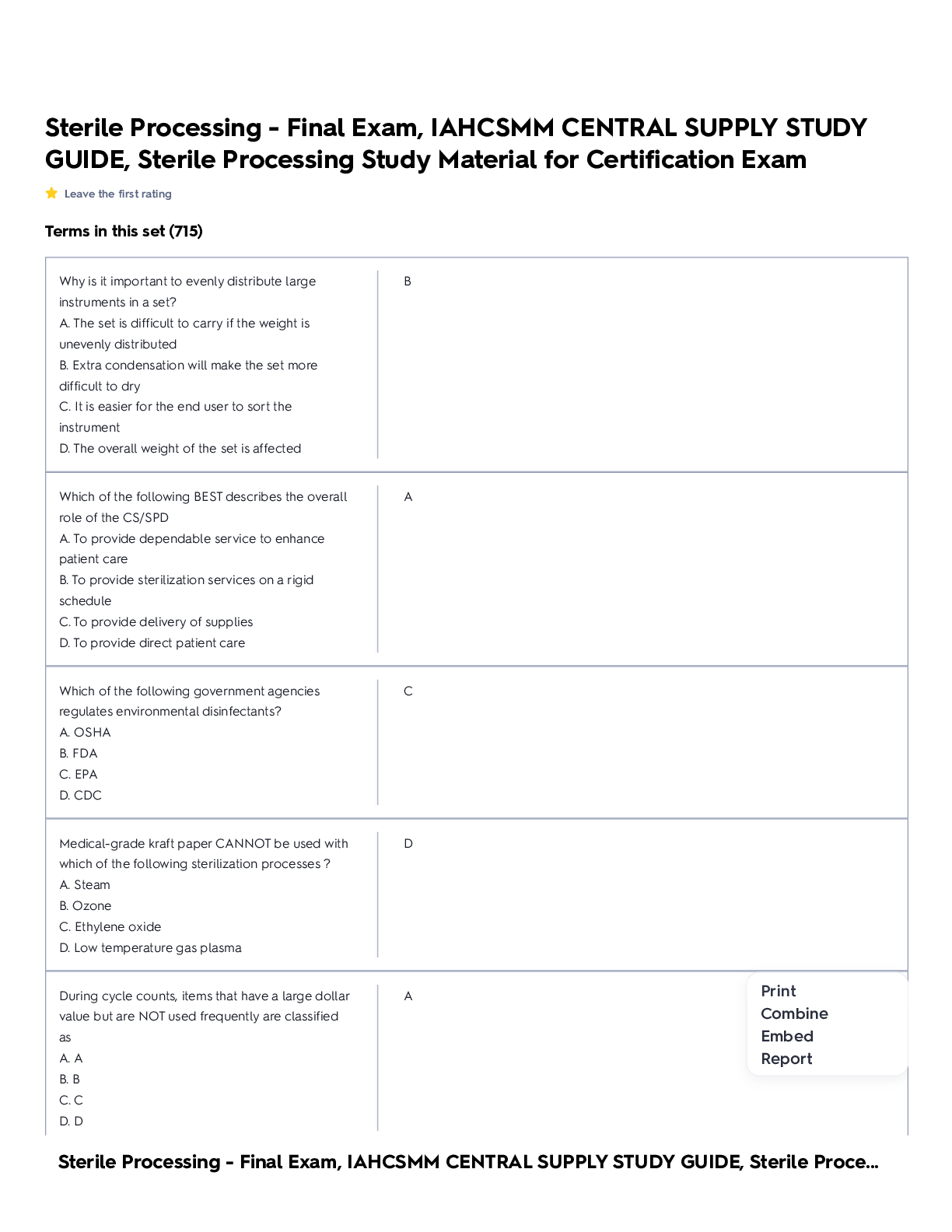
1. FAT: Stores file locations by sector in a file called the file allocation table. This table contains information about which clusters are being used by which particular files and which clusters are... free to be used. 2. NTFS (New Technology File System): File system used by Windows NT 4, 2000, XP, Vista, 7, Server 2003, and Server 2008. One major improvement of this system was the increased volume sizes. 3. Extended file system: System created specifically for Linux. There have been many versions; the current version is 4. 4. ReiserFS: Popular journaling file system, used primarily with Linux. It was the first file system to be included with the standard Linux kernel, and first appeared in kernel version 2.4.1. 5. The Berkeley Fast File System: This is also known as the UNIX file system. Uses a bitmap to track free clusters, indicating which clusters are available and which are not. 6. Data hiding: Storage of data where an investigator is unlikely to find it. 7. Data transformation: Disguising the meaning of information. 8. Data contraception: Storage of data where a forensic specialist cannot analyze it. 9. Data fabrication: Uses false positives and false leads extensively. 10. File system alteration: Corruption of data structures and files that organize data. 11. Daubert standard: Any scientific evidence presented in a trial has to have been reviewed and tested by the relevant scientific community. For a computer forensics investigator, that means that any tools, techniques, or processes you utilize in your investigation should be ones that are widely accepted in the computer forensics community. You cannot simply make up new tests or procedures. (1) whether the theory or technique in question can be and has been tested; (2) whether it has been subjected to peer review and publication; (3) its known or potential error rate; (4) the existence and maintenance of standards controlling its operation; and (5) whether it has attracted widespread acceptance within a relevant scientific community. 12. The Federal Privacy Act of 1974: Prohibits unauthorized disclosures of records( about people, citizens, individuals) maintained by Federal Agencies. Also allows individuals the ability to request to review their record. [Show More]
Last updated: 2 years ago
Preview 1 out of 43 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$7.50
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 24, 2022
Number of pages
43
Written in
Additional information
This document has been written for:
Uploaded
Oct 24, 2022
Downloads
0
Views
109



 with Complete Solution.png)
 Career Information with Complete Solution.png)


 for E-6 Career Information_watermark.png)