Running Head: ICT287 COMPUTER SECURITY 1
Ict287 Computer Security
Name
Murdoch University
Course
ICT287 COMPUTER SECURITY 2
Question 1 Attack Surface Modelling
With three stores in operation, the organization is
...
Running Head: ICT287 COMPUTER SECURITY 1
Ict287 Computer Security
Name
Murdoch University
Course
ICT287 COMPUTER SECURITY 2
Question 1 Attack Surface Modelling
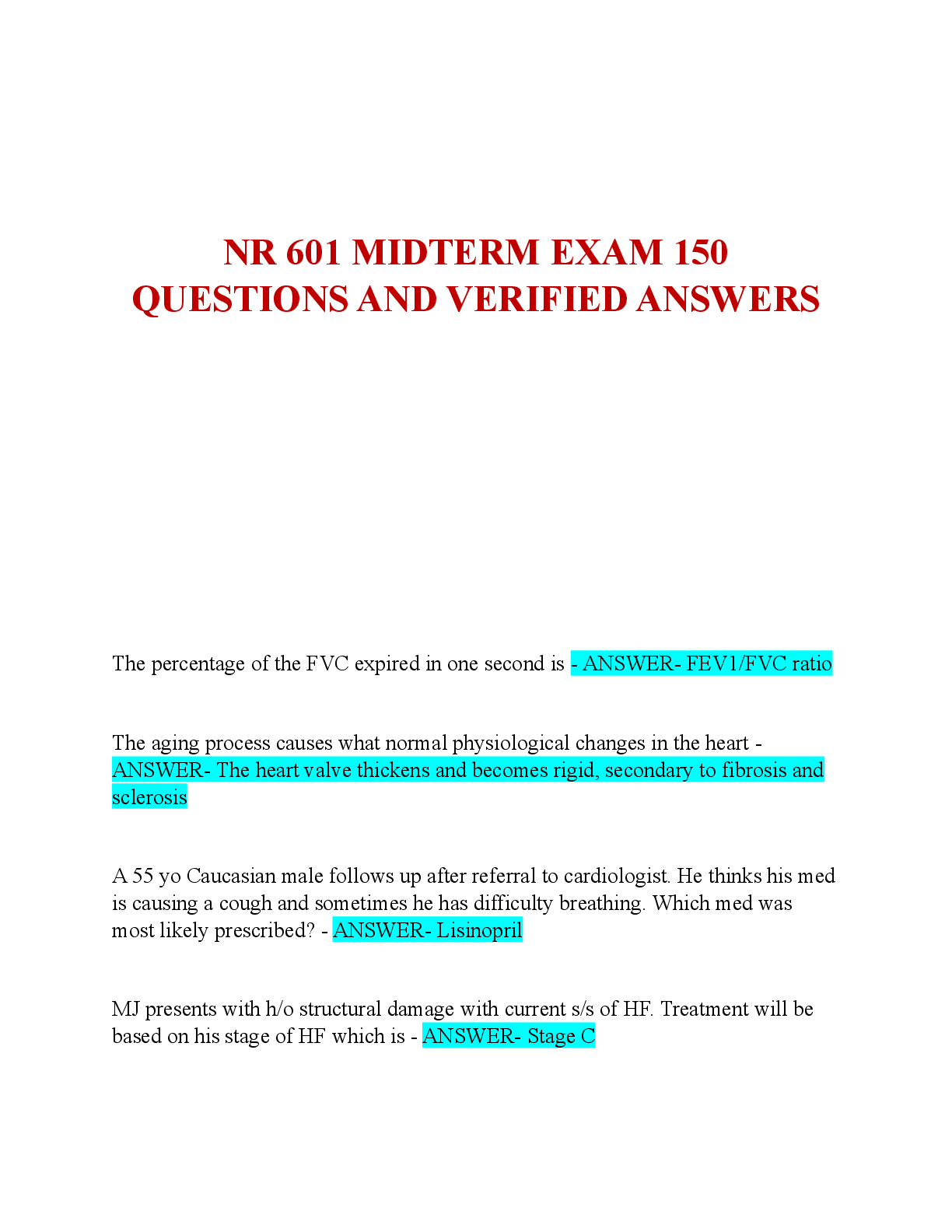
With three stores in operation, the organization is facing numerous threats, risks, and
vulnerabilities that will expose its computer network system to external entry and attack, thus
interfering with the privacy, confidentiality, accuracy, and integrity of its data and information in
the computer network. The fact that the different stores share data as a by-product means that
there is a high risk of such data landing on the wrong user. The CVE Items to be used in this case
are the description of the system vulnerability and the references to the system vulnerabilities.
With its expansion into an online platform, the data and the computer network will be accessible
to numerous users and external parties who may gain unauthorized entry into the network and
use the data for the wrong reason (Gibson, 2015).
The data entry created during the sharing of the data and moving to the online platform
will also be considered. These are the security threats, risks, and vulnerability that the computer
network of the organization faces currently. The vulnerabilities and risk of security threat to the
organization network are magnified by the fact that the organization has never engaged in any
system audit and have relied on their own knowledge and skills to set up their computer systems.
Numerous security breaches and loopholes must have been created during this process, thus
making it possible to have issues with the security of the computer network.
The Possible Weaknesses and Vulnerabilities in These Systems (Gibson, 2015).
The system of this organization is facing vulnerability that is making it susceptible to
external attacks who may gain aces into the da
[Show More]





.png)






.png)
.png)