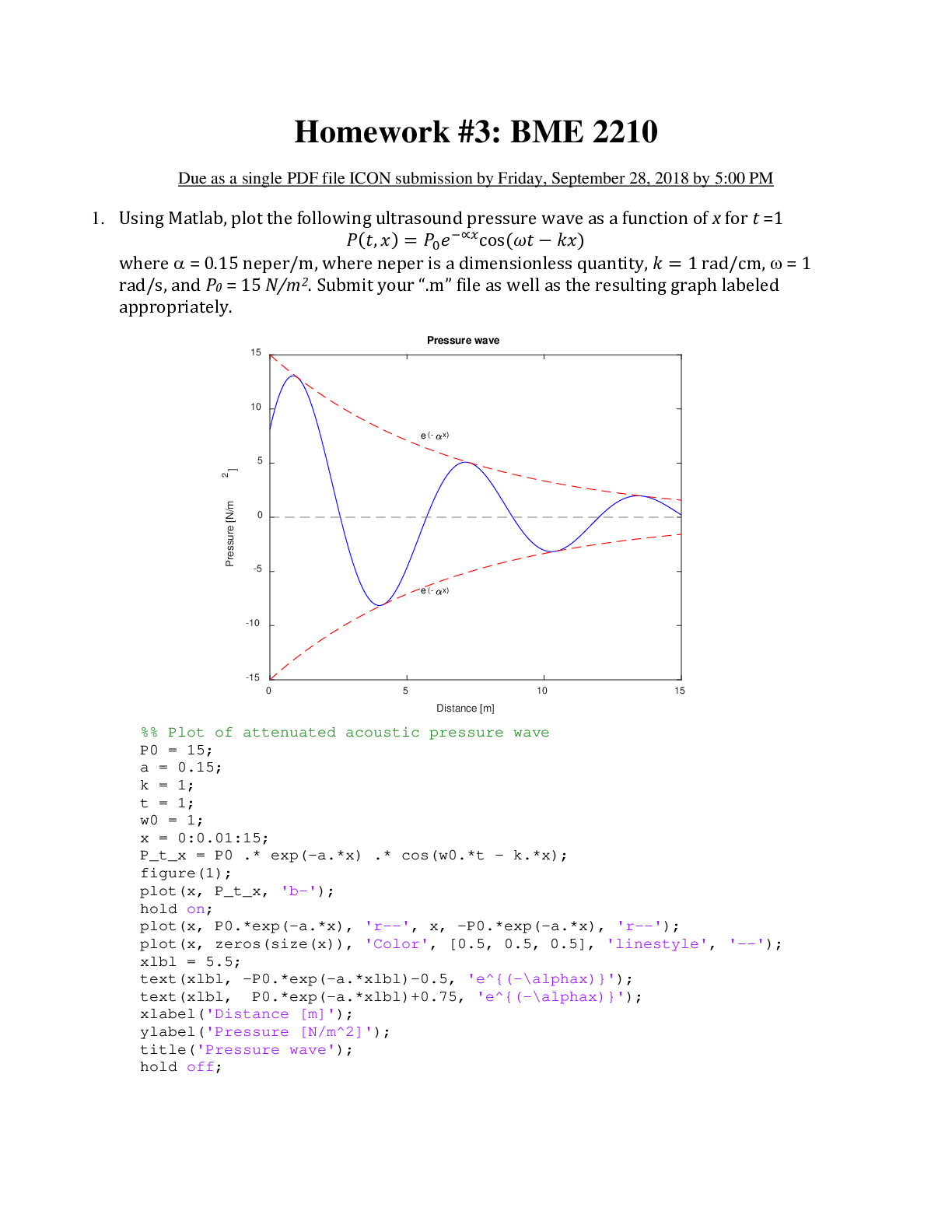
Computer Networking > QUESTIONS & ANSWERS > Questions and Answers > University of Ottawa _ KIN 4516 Q1 Fill the tables with the required fire (All)
Questions and Answers > University of Ottawa _ KIN 4516 Q1 Fill the tables with the required firewall rules for each scenario. You can add more rows if necessary. Use CIDR notation for source and/or destination networks. All rule sets must have an explicit deny all rule at the bottom. Unless otherwise stated, assume:
Document Content and Description Below
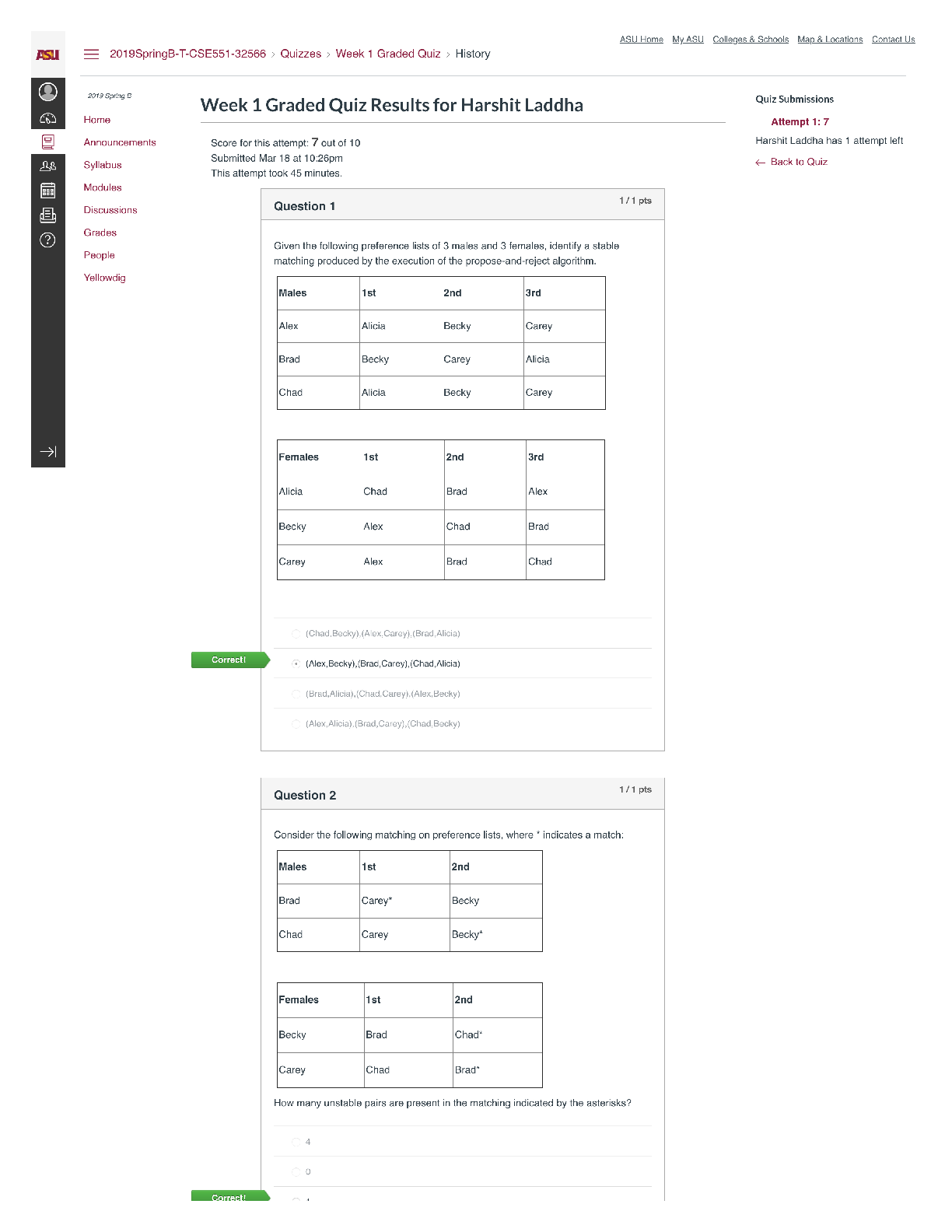
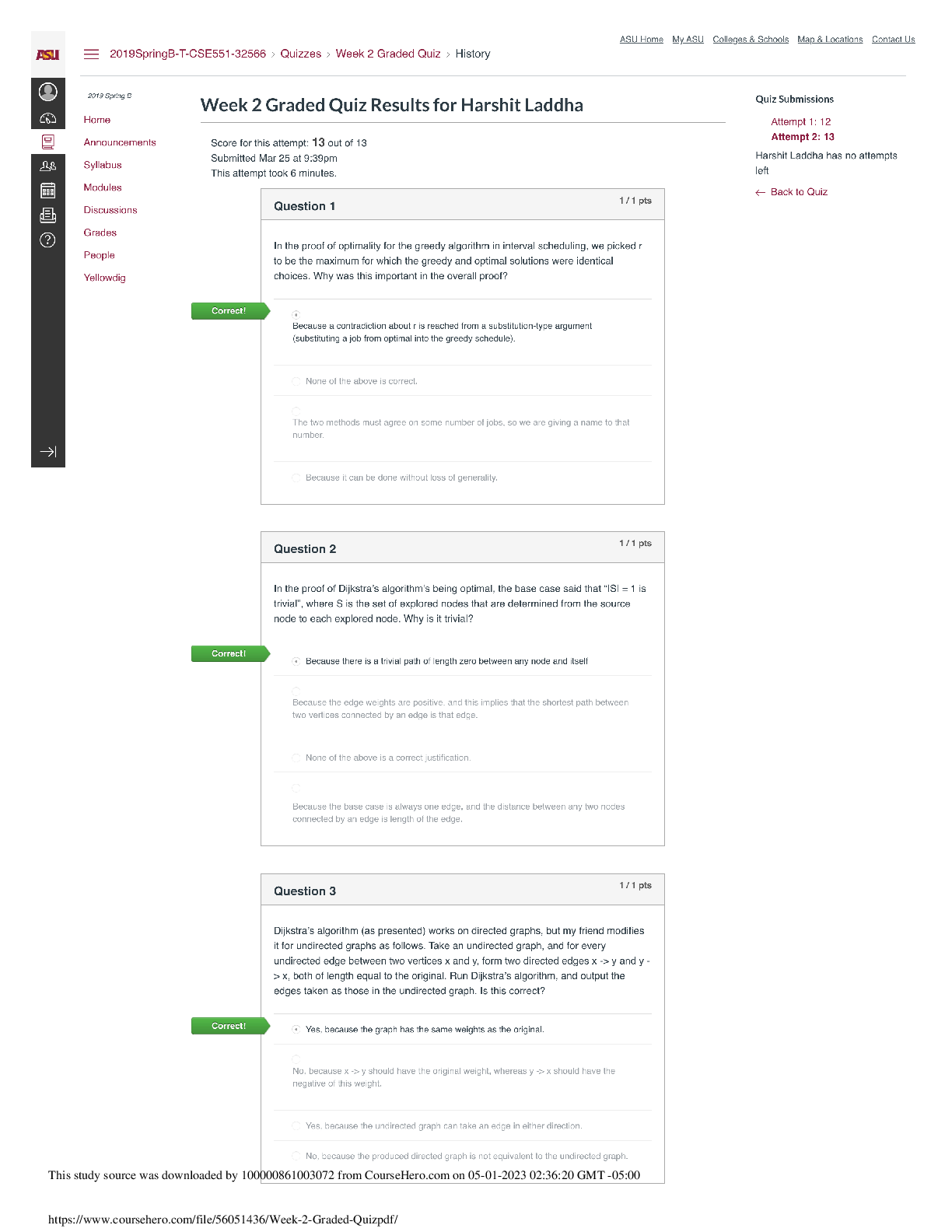
University of Ottawa KIN KIN 4516 Q1 Fill the tables with the required firewall rules for each scenario. You can add more rows if necessary. Use CIDR notation for source and/or des... tination networks. All rule sets must have an explicit deny all rule at the bottom. Unless otherwise stated, assume: Two networks, WAN and LAN Only one port per rule Actions are allow or deny You must create an efficient rule set, which means you reduce the number or rules to the minimum. Users in the internal network 172.16.10.0/24 should browse the Internet by http/s only through the proxy with IP 172.16.10.5, with the exception of the network administrator, who can go directly from their PC with IP 172.16.10.130. The same applies to outbound DNS communication, only the proxy and the network administrator are allowed to query DNS servers on the Internet. Nevertheless, browsing to 15.16.17.18 should be forbidden by everyone, for the network administrator detected some malware might be using it as a C&C. Additionally, the network administrator should be able to access the firewall itself, with IP 172.16.10.1, by https and ssh. Rule # Source IP Destination IP Destination Port Protocol Action A company decided to add a DMZ to the firewall. Thus, a new interface with IP 10.0.0.1 and network mask 255.255.255.240 was added. In the DMZ, there are two web servers with IP addresses 10.0.0.2 and 10.0.0.3, the first to be accessed from anywhere and the second by use only from the Intranet, which is the network 192.168.0.0/24. No other servers in the DMZ, present or future, should be accessed from anywhere unless explicitly allowed. The DMZ should never have access to the Intranet, but for a SQL database server with IP 192.168.0.252 and listening on TCP port 1433. Rule # Source IP Destination IP Destination Port Protocol Action [Show More]
Last updated: 2 years ago
Preview 1 out of 3 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$4.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jan 15, 2023
Number of pages
3
Written in
Additional information
This document has been written for:
Uploaded
Jan 15, 2023
Downloads
0
Views
92