ServiceNow VR Course Exam 175 Questions with Verified Answers,100% CORRECT
Document Content and Description Below
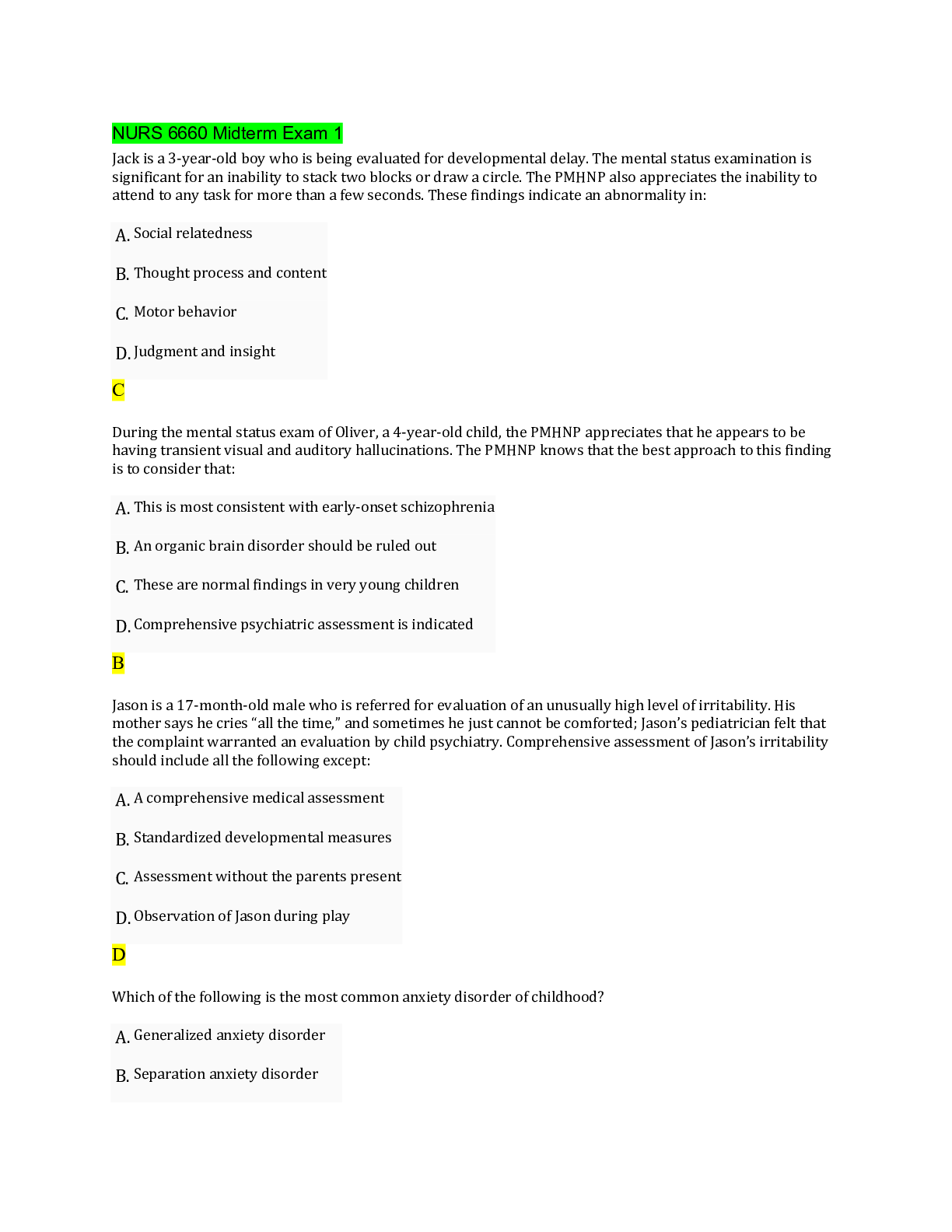
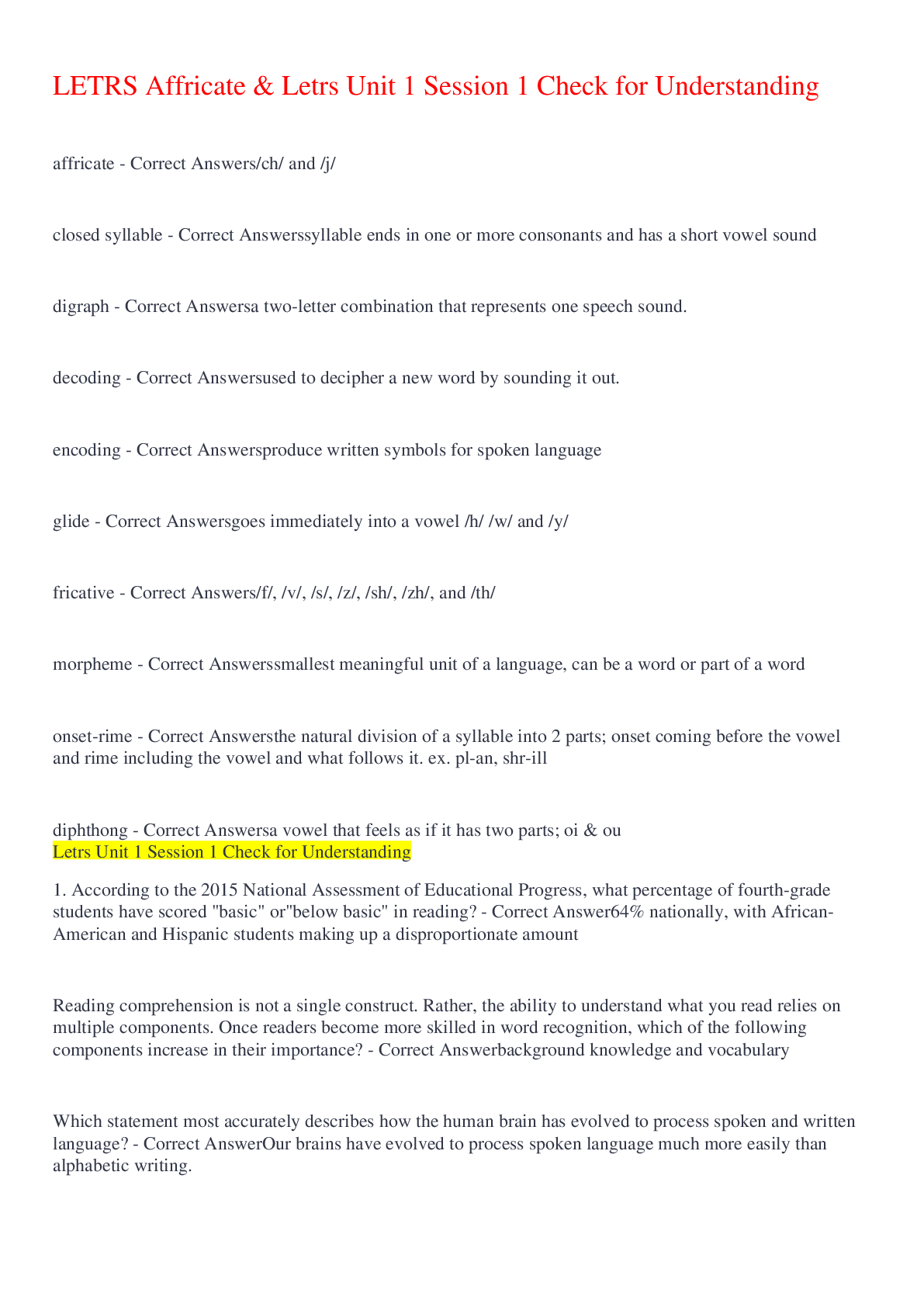
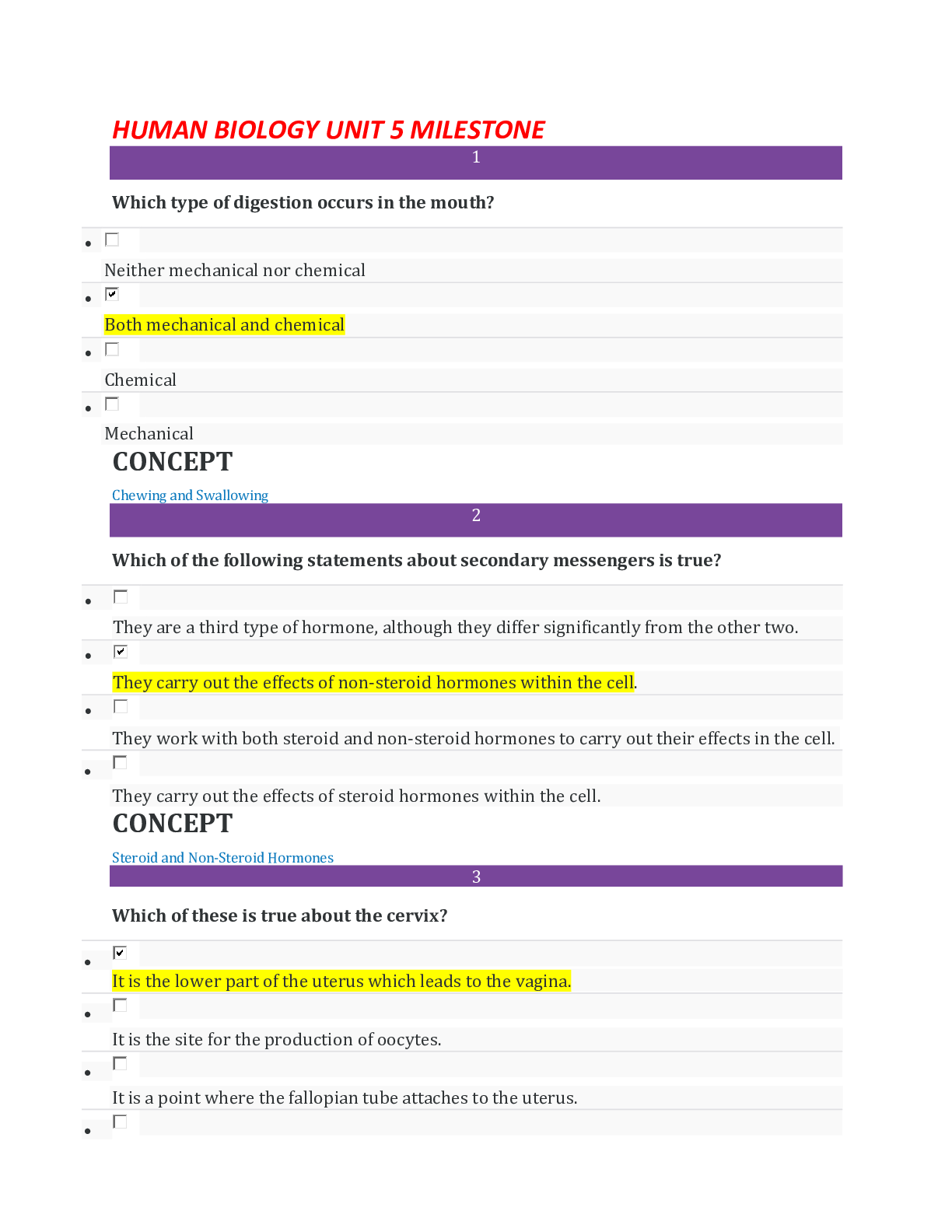
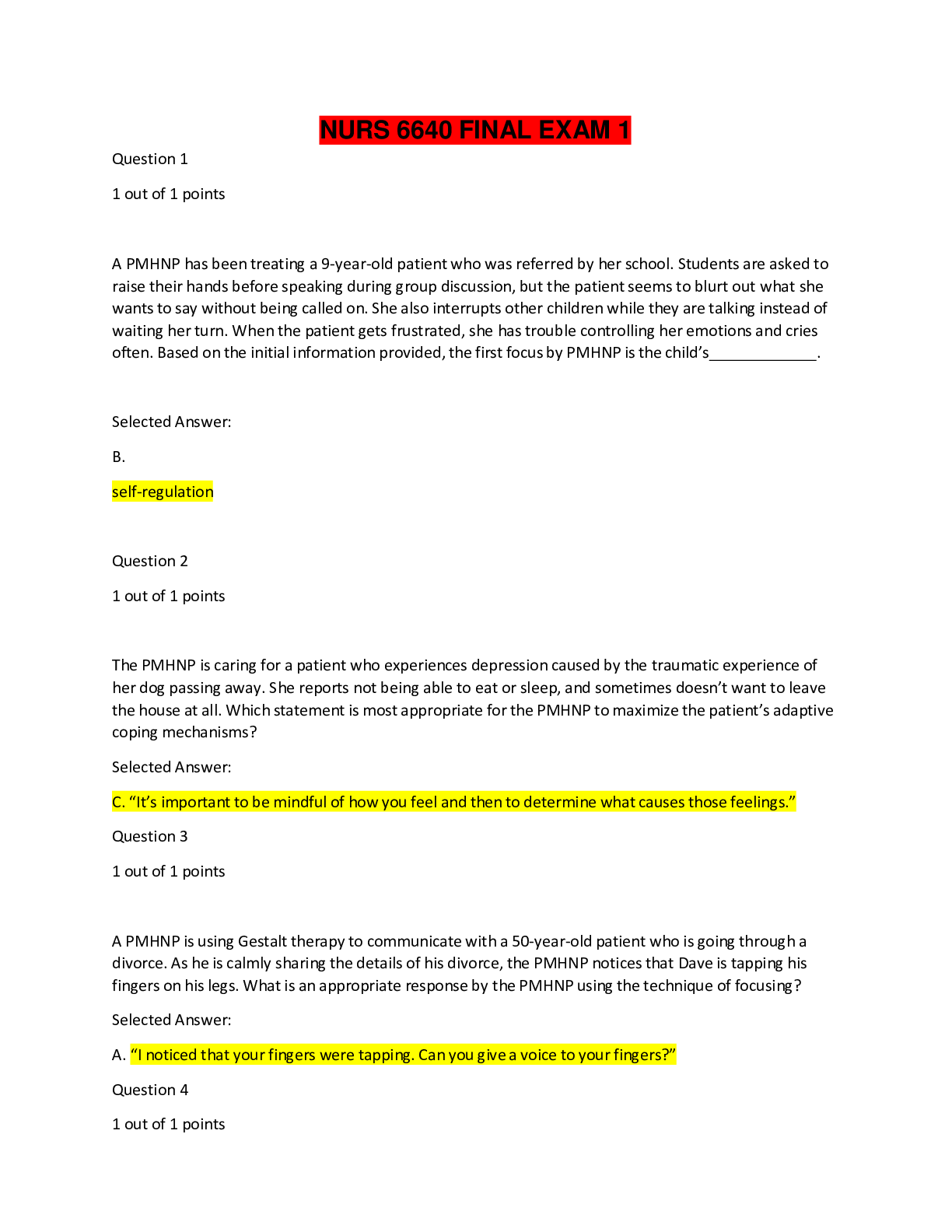
ServiceNow VR Course Exam 175 Questions with Verified Answers What is Security Operations? - CORRECT ANSWER Collection of activities that help maintain the security posture. This consists of th... e monitoring, maintenance and management of processes, products and people that help to provide security posture for an organization. This includes applications, databases, data centers, websites etc. What are the 3 types of security? - CORRECT ANSWER 1. Preventative - measures to prevent an outbreak from occurring 2. Detective - understanding signs that an outbreak has occurred 3. Corrective - containment procedures to limit damage post-breach What are the main issues that leads to inefficient detection and correction of a breach? - CORRECT ANSWER - Little/no detection tool - Not communicating to the right people - Poor decision-making when deciding on a response - No defined process to remediate breaches - No post-incident review process What is the ServiceNow Security Operations process? - CORRECT ANSWER 1. Integrate your security products/tools 2. Automatically prioritize incidents 3. Utilize threat intelligence 4. Determine response action 5. Remediate threats 6. Review post incident reports What are the 5 phases of the SecOps process? - CORRECT ANSWER 1. Identify 2. Protect 3. Detect 4. Respond 5. Recover How many processes are included in the ServiceNow baseline and what are they? - CORRECT ANSWER 4 processes 1. NIST Stateful 2. NIST Open 3. SANS Open 4. Example (for customising) Security Incident Response features? - CORRECT ANSWER - Integrate with 3rd party threat detection systems and Sec Info & Event Management (SIEM) - Prioritizes incidents based on business impact - Enriches incidents with threat intelligence automation and workflows to reduce manual tasks - Improves communication between IT, end users and security teams Vulnerability Response features? - CORRECT ANSWER - Integrates with National Vulnerability Database (NVD) - Integrates with various 3rd party scanners - Identify infrastructure vulnerabilities Provides a proactive opportunity by reducing attack surface by addressing most vulnerable components of the infrastructure. Threat Intelligence features? - CORRECT ANSWER - Integrate with 3rd party threat detection systems and Sec Info & Event Management (SIEM) - Provides information needed to prioritize incidents - Enriches incidents with threat intelligence automation and workflows to reduce manual tasks Maturity Levels for SecOps - CORRECT ANSWER Page 16 Who are the 3 front line responder teams? - CORRECT ANSWER - Computer Emergency Response Team (CERT) - Computer Security Incident Response Team (CSIRT) - Security Incident Response Team (SIRT) Purpose: Dedicated staff that provides analysis, rapid response and recovery of security incidents to limit damage and reduce cost. What are the SecOps product tiers? - CORRECT ANSWER 1. Standard - SIR 2. Standard - VR 3. Professional - SIR 4. Professional - VR 5. Enterprise '1' only contains SIR and 5 custom tables '2' only contains VR and 5 custom tables '3' contains SIR, Event Management, Orchestration, Threat Intelligence, PA and 5 custom tables '4' contains VR, Vulnerability Solution Management, PA and 5 custom tables '5' contains everything and 15 custom tables Is Trusted Security Circles application included in the VR product tiers? - CORRECT ANSWER No. Only included in SIR product tiers and enterprise. Standard - SIR has LIMITED Professional - SIR has UNLIMITED Enterprise has UNLIMITED How does the manual vulnerability response process work? - CORRECT ANSWER 1. Scanner outputs vulnerabilities 2. Output is triaged via a spreadsheet. SLA Opened. 3. User prioritizes vulnerabilities, case by case 4. User has to decide to remediate or defer. 5. User defers case and is put into exceptions list... or... 6. Create change tickets to resolve 7. Close SLA Steps 1 and 2 are automated. Everything else is manual. How does the ServiceNow vulnerability response process work? - CORRECT ANSWER 1. Scanner data is output 2. API used to create vulnerability items (VITs) 3. Automatically prioritize and assign items 4. Group VITs into Vulnerability Groups (VULNs) based on priority and assignment. SLAs opened. 5. User works on VULN with own SLA for each VIT. CMDB automatically sets assignment group on records. 6. Defer VULN... or... 7. Resolve tickets. Close SLAs. Only step 5 is manual. Vulnerability Response Maturity Levels - CORRECT ANSWER Page 22 What is essential to effective security and why? - CORRECT ANSWER - Asset Management - Configuration Management This is because when there are deviations in normal expected behaviour of a CI, this requires business to understand the wider impact on the overall infrastructure in order to correctly categorize and prioritize the response. This is done through the CMDB and CI relationships What can occur with an inaccurate CMDB? - CORRECT ANSWER - Lack of insight into business critical applications aligned to the infrastructure - Business critical systems going offline - Lack of asset ownership - SLAs are missed - Loss of trust internally - Loss of reputation What is Configuration Management? - CORRECT ANSWER Process that tracks all CIs, maintaining the accuracy of the CMDB. What are vulnenrabilites? - CORRECT ANSWER The weaknesses through which security breaches occur What is the National Vulnerability Database (NVD)? - CORRECT ANSWER US Government Repository of vulnerability data, security checklists, products, metrics What is Common Vulnerability and Exposure (CVE)? - CORRECT ANSWER Dictionary of publicly known information security vulnerabilities and exposures. What is Common Weakness Enumeration (CWE)? - CORRECT ANSWER A list of software weaknesses What is Vulnerability Scanner? - CORRECT ANSWER A software system designed to perform automated scans of CIs to discover vulnerabilites What is Vulnerability Response? - CORRECT ANSWER The process of identifying, classifying and prioritizing vulnerabilities. Then deciding the appropriate response (remediate, mitigate, acceptance [defer]). What are the 2 responses after identifying a vulnerability? - CORRECT ANSWER 1. Remediation - fix, change, mend, repair - something to reduce the vulnerability 2. No Remediation - Document the risk to the org - something that accepts the vulnerability Do vulnerabilities act alone? - CORRECT ANSWER No. They need to be exploited by a threat (e.g - Virus). What are 2 examples of when too simply accept a vulnerability? - CORRECT ANSWER 1. Where the likelihood of the threat occurring is low, the vulnerability may simply just be accepted when it arises instead of remediating it. 2. Where the cost of remediating outweighs the business value. When is Vulnerability Response ineffective? - CORRECT ANSWER When it's used in Isolation. To make proper use of it, it needs to be integrated with other platform areas such as: 1. Configuration management 2. Security incident response 3. Change management - ability to plan an prioritize remediation 4. Problem management - allow for root cause analysis 5. SLAs - resolve vulnerabilities 6. Orchestration - Automate responses What is Vulnerable Item record? - CORRECT ANSWER An actual occurence of a vulnerability i.e: an actually affected CI What related data is shown on the record? - CORRECT ANSWER - Tasks - Approvals - Work Notes - Vulnerability - CI What table does Vulnerability Group extend? - CORRECT ANSWER Task What is the difference between Vulnerability Response and Patch Management? - CORRECT ANSWER VR is proactive and is used for mature SecOps teams PM is reactive and is used for IT patching/hot fix teams VR tools used are vulnerability scanners (Qualys) PM tools used are patch deployment tools (SCCM) What are the 2 application scopes that are activated after installing the VR plugin? - CORRECT ANSWER 1. Vulnerability (sn_vul) 2. Security Support Common (sn_sec) How many tables are included in each application scope? - CORRECT ANSWER - 76 in the Vulnerability application scope - 82 in the Security Support Common application scope What tables are used for the Vulnerability Database? - CORRECT ANSWER Vulnerability Entry (sn_vul_entry) Common Weakness Enumeration (sn_vul_cwe) National Vulnerability Database Entry (sn_vul_nvd_entry) Third Party Vulnerability Entry (sn_vul_third_party_entry) What are the key roles? - CORRECT ANSWER - Vulnerability admin (sn_vul.vulnerability_admin) - Remediation owner (sn_vul.remediation_owner) - Vulnerability analyst (sn_vul.vulnerability_analyst) - CI manager (sn_vul.ci_manager) - Exception approver (sn_vul.exception_approver) - Reader (sn_vul.read_all) What does sn_vul.exception_approver allow? - CORRECT ANSWER - Approvers exceptions, deferrals and closure of VIs and VGs What does sn_vul.ci_manager allow? - CORRECT ANSWER - Manages unmatched CIs not found in the CMDB - Updates discovered items What does sn_vul.vulnerability_analyst allow? - CORRECT ANSWER - Can manage VIs and VGs - Assign remediation tasks - Monitor remediation progress What does sn_vul.remediation_owner allow? - CORRECT ANSWER - Can view and update VIs and VGs - Can view all vulnerabilities and solutions - Has write access to internal notes on solution records What does sn_vul.vulnerability_admin allow? - CORRECT ANSWER - Complete access to VR application - Can install third party integrations - Assigns all VR roles What does sn_vul.vulnerability_write allow? - CORRECT ANSWER Deprecated role What is sn_vul.popup do and whats its default value? - CORRECT ANSWER Allow customisation when creating a change, problem or security incident via the Vulnerability Item record. Default = false. It auto inherits values from the Vulnerable item What is sn_vul.vulnerable_item.approval_required do and whats its default value? - CORRECT ANSWER Determines whether an approval is required to move a vulnerable item to a terminal state Default = false. What is sn_vul.email_to do and whats its default value? - CORRECT ANSWER Specifies which inbox will be used by VR Default = true How many properties are provided upon installation of the plugin? - CORRECT ANSWER 35 How do vulnerability scans for single/multiple items work? - CORRECT ANSWER They can be automated using the Vulnerability Response - Scan Vulnerability workflow. Creates a scan record for the vulnerability or group of vulnerabilites. How are approvals against a vulnerability processed? - CORRECT ANSWER Using the workflow: Vulnerable Item State Approval What other Applications can enrich SecOps? - CORRECT ANSWER - Service Mapping... correlate SecOps with key business services - Event Management and Orchestration.. gain efficiency by automating SecOps activities (trigger SIR from a VIT) - Performance Analytics... visualize SecOps data - GRC... align security events with risks and controls - Threat Intelligence... Enrich VIT record with further details What is a Vulnerable Item made of? - CORRECT ANSWER Vulnerability + Configuration Item What is the main source of Vulnerabilities and how is each one identified? - CORRECT ANSWER NVD Data Feed, which is an XML feed, provides CVE data. Each vulnerability on the feed is identified via the first 4 digits which is the 'CVE Identifier' How do NVD Data feeds work? - CORRECT ANSWER There is a Data feed for each year. The data feeds are only updated when the content of the feed changes. e.g 2004 feed will be updated if there is an addition/change to any vulnerability starting with CVE identifier "CVE-2004". Note: Needs to have 'update automatically' set to TRUE. If not, need to use on-demand update module to import new/modified vulnerabilities. How do the data feeds find the new/modified records? - CORRECT ANSWER NVD Integration script runs (default weekly) and finds records which are new/modified. The data feeds then update if new/modified records are found. What is the difference between the "recent" and "modified" feeds and how often are they updated? - CORRECT ANSWER "Recent" is a list of recently published vulnerabilities in the last 8 days "Modified" is a list of recently published and modified vulnerabilities in the last 8 days The feeds are updated every 2 shours What is the CWE Integration? - CORRECT ANSWER Common Weakness Enumeration is a community developed list of common software weaknesses. What is the difference between CVE and CVE-ID - CORRECT ANSWER CVE is the list of common names for publicly known vulnerabilities and exposures CVE-ID is a single record from the list Can CVEs and CWEs be linked together? - CORRECT ANSWER Yes, through related list (m2m table) Where are CVE-ID records downloaded from and what are they compared to? - CORRECT ANSWER NVD They are compared to software/CIs in the customers network What happens if CVE-ID matches a software/CI - CORRECT ANSWER A Vulnerable Item (VIT) is created What is the issue with setting severity on a VIT and how is it solved? - CORRECT ANSWER Different vendors (sources e.g Qualys, NVD) have different severity rankings. Normalized Severity Mapping module is used to solve this by transforming third party severity field values to ServiceNow values. What are Threat Actors? - CORRECT ANSWER Threat Actors pay attention to the scoring of a vulnerability and try exploit lower ranked vulnerabilities What is CVSS Score used for? - CORRECT ANSWER To prioritize vulnerabilities. However it doesn't take into account company business priority and so may miss prioritize vulnerabilities How is Risk Score and Risk Rating calculated? - CORRECT ANSWER Using a Vulnerability Calculator. For each calculator, set a target field (e.g - Risk Score) and then add either a Calculator Rules or Risk Rule which contain info on how the final value is set Can you have multiple calculators for the same target field? - CORRECT ANSWER No Difference between calculator and risk rules? - CORRECT ANSWER Risk rules can have weights added to each parameter that makes up the risk score. Contains sample scenarios which result in different final values based on the weights Calculator rules, you can specify what to set the values too for the target field In a risk rule, what are the parameters that make up the overall score for an IVR Calculator? - CORRECT ANSWER - Vulnerability severity - Exploits exists - Exploit skill level - Exploit attack vector - Business criticality - CI exposure In a risk rule, what are the parameters that make up the overall score for an AVR Calculator? - CORRECT ANSWER - Vulnerability severity - CWE entry SANS Top 25 - CWE entry OWASP Top 10 How are vulnerability groups created? - CORRECT ANSWER Either automatically (1) or manually (2) 1. Use vulnerability group rules 2. Do one of the 3 options - add VIT records to the group - use a condition filter that auto adds VIT records - use a filter group that auto adds VIT records What is Vulnerability Rollup Calculator and how does it run? - CORRECT ANSWER Rolls up the risk scores for all vulnerable items in a vulnerability group by using weights for VIT risk scores, to provide an overall risk score for the entire group of vulnerable items. Runs using a scheduled job which contains a script include (RollupCalculatorUtil). When does the rollup calculator scheduled job run? - CORRECT ANSWER 1. Every 15 mins 2. Change to a VIT (state, target date, membership in a Group). What are Application Vulnerabilities? - CORRECT ANSWER Vulnerabilities on custom software applications, scanned throughout the applications life cycle What are the 2 main problem areas with Application Vulnerability? - CORRECT ANSWER 1. Lack of visibility into application security 2. Lack of collaboration and clarity What are 3 types of testing? - CORRECT ANSWER 1. Development Testing 2. Security Testing 3. Operational Testing How does AVR flow work? - CORRECT ANSWER 1. AVI's are imported into the system... done by Veracode matching Vulnerabilites with Applications (CIs) 2. Vercode passes the data into SNow and uses CI Lookup rules to identify Scanned Applications and Application Release. This info is populated into the record 3. Resolution of the vulnerability will be managed in Veracode. Updates are pushed to SNow which updates the AVI table Components of AVR? - CORRECT ANSWER 1. AVI table doesnt extend or relate to VI table 2. No Remediation Tasks 3. State is managed in the source application (Veracode) Are all fields in the AVI read only? - CORRECT ANSWER Except from Assignment Group, Assigned To and Notes, all others are read only What are Scanned Applications and what table are they stored in? - CORRECT ANSWER They are mapped application services in the CMDB. They populated by scanners such as Veracode and are added to the Application Release field on a AVI. They are stored in Scanned Application Table (sn_vul_app_scanned_application) What additional information needs to be added to a Scanned Application? - CORRECT ANSWER - Department, Business Unit, Support Group - Relationships to Technical Services - Add Security Champions (ownership) What table does sn_vul_app_scanned_application extend? - CORRECT ANSWER cmdb_ci_appl (Application Table) What 3 Groups are created for Application Vulnearbility Response? - CORRECT ANSWER 1. App-Sec Managers 2. Application Security Champions 3. Developers What are the ServiceNow instance sizing guidelines based on vulnerabilities in the environment? - CORRECT ANSWER < 1 million vulnerabilities = XL Instance size 1 - 2.5 million vulnerabilities = XXL Instance size > 2.5 million vulnerabilities = Ultra Instance size What is Qualys? - CORRECT ANSWER A scanner. Plugin exists on ServiceNow to integrate the scanner with the CMDB to keep it updated. When it detects a vulnerability, data (VIT) is imported to Vulnerability Response for tracking and resolution. How does the Qualys plugin work? - CORRECT ANSWER Auto updates the CMDB with any IT assets it discovers with up to date info. What happens if an asset is added to ServiceNow? Will the scanner be able to search for it during a scan? - CORRECT ANSWER Yes. The plugin auto adds it to the QUALYS ASSET INVENTORY What do you need to be using for to enable Qualys integration to detect vulnerabilities? - CORRECT ANSWER Qualys Cloud Platform. The qualys cloud platform sensors collect data and send it to the qualys cloud platform. The integration with SNow SecOps maps vulnerabilities to CI to determine the priority. What is QID and where is it stored? - CORRECT ANSWER Qualys ID which is assigned to a vulnerability. QID information is stored in the third party vulnerability entries [sn_vul_third_party_entry] What table does sn_vul_third_party_entry extend? - CORRECT ANSWER Vulnerability table [sn_vul_entry] What do vulnerability scanner records contain? - CORRECT ANSWER Integration scripts (to interface with the system) Processor scripts (to handle retrieved data) How does Qualys Host Detection Integration work? - CORRECT ANSWER Queries hosts and then runs a Qualys Host Transform to insert/update CIs in the CMDB. The table it targets is cmdb_ci What fields are updated? - CORRECT ANSWER Class Name CI Name DNS Name Fully Qualified Domain Name IP Address When Vulnerability Management plugin is added, what fields are added to the cmdb_ci form - CORRECT ANSWER Qualys ID Qualys host ID Created by Qualys Are CI Look up rules populated once Qualys plugin is installed? - CORRECT ANSWER Yes How are lookup rules evaluated? - CORRECT ANSWER Lowest order first Can classes be ignored when doing a CI Look up? - CORRECT ANSWER Yes, using ignoreCIClass property What happens if a scan doesn't find a matching CI? - CORRECT ANSWER A record is entered into the Discovered item table and a placeholder CI is created and set as an 'Unmatched CI' What is IRE and what does it do to aid in the CI Matching process? - CORRECT ANSWER Identification and Reconciliation Engine. This is used if CI Lookup Rules fail. If there is IP data available, a record is constructed as an "Incomplete IP" record. If there is no IP data, a record is constructed as a "Unclassed Hardware" record. What are the 2 new tables added with IRE? - CORRECT ANSWER - Unclassed Hardware (cmdb_ci_unclassed_hardware) - Incomplete IP (cmdb_ci_incomplete_ci) What is the new property added with IRE? - CORRECT ANSWER sn_sec_cmn.ci_creation_through_IRE Default: True What does SAM provide and what does combining SAM and VR allow? - CORRECT ANSWER SAM provides info on where the most recent vulnerabilities exist in the infrastructure. Combining SAM and VR allows the ability to assess vulnerability exposure using Exposure Assessments. Exposure assessments is a module in the vulnerability scanning section of the VR app. For this to appear, SAM foundation/pro needs to be implemented. Are you able to create a Vulnerable Item via a exposure assessment? - CORRECT ANSWER Yes. Need to define whether you're creating using a new/existing vulnerability. How do VITs work with Exposure Assessment? - CORRECT ANSWER Exposure Assessment identifies a set of items. VIT is created for each identified item. VITs are then grouped into a Vulnerability Group. Can VITs in a group be separated into other groups if need be? - CORRECT ANSWER Yes What are the 3 different methods of grouping Vulnerable Items? - CORRECT ANSWER 1. Manually add items to a group 2. Group by Condition (obvs has to be on VIT table) 3. Group using Filter Groups If you update filter on a Vulnerability Group that has been applied, how do you update the related VITs? - CORRECT ANSWER Using related link on the form What happens when you click 'Reapply' UI action on a vulnerability Group Rule? - CORRECT ANSWER Reapplying this group rule will delete and re-create the vulnerability groups for this rule. Vulnerability groups that are not in the Open state are excluded from deletion. What are the 3 key parts Vulnerability Group Rules? - CORRECT ANSWER 1. Condition to identify which VITs to group 2. Determine how to group them (Group By) 3. Determine the assignment group for the vulnerability group For the Group By part of a Vulnerability group rule, what is the default table for where the options come from? - CORRECT ANSWER Vulnerable Item table For the Assignment section for a vulnerability group rule, what happens if NO group field (e.g 'assignment group') is selected in the 'Group By' section - CORRECT ANSWER The 'Group By Field' option isn't available For the Assignment section for a vulnerability group rule, what happens if None is selected - CORRECT ANSWER Vulnerability group is created without an assignment group What are the 3 options in the Assignment section of a vulnerability group rule? - CORRECT ANSWER 1. Group by Field 2. None 3. Specific User Group What role is required to manually create vulnerability group rules? - CORRECT ANSWER sn_vul.vulnerability_admin What are filter groups and where are they stored? - CORRECT ANSWER Easy way to set up filters to be reused across various SecOps functionalities. Simply set a table and a filter. stored in: sn_sec_cmn_filter_group Can filter groups contain other previously defined filter groups? - CORRECT ANSWER Yes What do Vulnerability Calculators do? - CORRECT ANSWER Built to prioritize and rate impact of vulnerable items based on some criteria. You can create vulnerability calculators to set other field values on a vulnerable item (e.g - risk score, risk rating, active) How are values set using a vulnerability calculator? - CORRECT ANSWER Each calculator contains a list of calculator rules with a condition for each. When the calculator is run, each calculator rule is evaluated in order and the first matching rule is used. Besides calculator rules, what else can vulnerability calculators include:? - CORRECT ANSWER Risk rules. The difference between these and calc rules is that risk rules are used to only set risk score value. Done using weights instead of setting an exact value to set the field too, like calc rules do. What two teams are required for vulnerability solution management? - CORRECT ANSWER - Security Team: identifies the problem - IT Team: manages the solution using patch management What does Vulnerability Solution Management give access to? - CORRECT ANSWER Microsoft Security Response Center, which provides solution information to help manage different types of vulnerabilities What are the 3 benefits of Vulnerability Solution Management? - CORRECT ANSWER 1. Automatically identifies solutions to active vulnerabilities 2. Track solution progress 3. Prioritize remediation efforts Is Vulnerability Solution Management a separate subscription? - CORRECT ANSWER Yes What is included under Remediation Status tab in Vulnerability Groups and Vulnerability Solutions? - CORRECT ANSWER Deployment metrics (e.g - % remediated) What do Assignment Rules do? - CORRECT ANSWER Rule contains a set of conditions on the VIT table. When these conditions are met, this rule automatically assigns vulnerable items to the selected user group. Only the first assignment rule with a matching condition runs against a record. Vulnerable items that are not in the Open state or have been manually assigned are always excluded. What are the 3 options for assignment for an assignment rule? - CORRECT ANSWER 1. Assignment Group - select a specific group 2. Assignment Group Field - select a group from one of the user group fields 3. Script How does Vulnerability Group Assignment Rolldown work? - CORRECT ANSWER If Assignment Group is changed on the group record, all vulnerable item assignment groups will change EXCEPT where the VIT has been manually changed. What happens to the group update if there are over 200 VITs linked to the vulnerable group? - CORRECT ANSWER Done using an a-snyc job Different options when closing a VIT? - CORRECT ANSWER 1. Wait for next scan before closing 2. Close now, reopen if next scan detects it again Whats the procedure for closing a VIT? - CORRECT ANSWER 1. Change request is moved to completion after patch is installed. Status indicated on VIT 2. VIT remains in place until scanner rescans CI 3. VIT is closed AFTER scam successfully reports scan of CI with no vulnerability. What are the table names for Assignment Rules, Remediation Target Rules and Vulnerability Calculators - CORRECT ANSWER - sn_vul_assignment_rule - sn_vul_ttr_rule - sn_vul_calculator_group If you create an assignment rule/target rule/calculator in the AVR section, can it be used for VITs? - CORRECT ANSWER No, it can only be used for AVITs Same if done the other way around, if created in IVR, then it can only be used for VITs. What do SLAs apply too? - CORRECT ANSWER Vulnerability Groups Where do you go to create SLAs? - CORRECT ANSWER Service Level Agreement -> SLA -> SLA Defintion What are Remediation Target Rules? - CORRECT ANSWER Define the expected timeframe for remediating a vulnerable item, much like SLAs define a timeframe to remediate the vulnerability itself Who can create Remediation Target Rules? - CORRECT ANSWER Vulnerability Managers What do Remediation Target Rules apply to? - CORRECT ANSWER Vulnerable Items Can CHG requests be made from Vulnerability Group records? - CORRECT ANSWER Yes. CHG can be made for all vulnerable items in a group What role is required to create a CHG from a group? - CORRECT ANSWER Remediation Owner What are the 2 options for creating CHG records for the linked VITs - CORRECT ANSWER - create for all active VIT in the group - create for all active VIT in the group that match a condition Can you select the change type? - CORRECT ANSWER Yes. Emergency, Normal, Standard Can you define the CHG data (e.g - short description, priority) before creating it? - CORRECT ANSWER Yes Can you add the CI to the CHG record before creating it? - CORRECT ANSWER Yes, using a checkbox to determine whether the CI is added or not What happens to the VG if a Change Request is made with only a subset of the VI's? - CORRECT ANSWER Those VI are moved to a new Vulnerability Group. The new group will have the same name as the original one. Can you associate Vulnerability Group to an EXISTING CHG record? - CORRECT ANSWER Yes, using the related list at the bottom of the group form. Can also decide whether to add the CI to the CHG or not. Can you split a vulnerability group? - CORRECT ANSWER Yes. Need to select which VITs you want to split. What is State Synchronization? - CORRECT ANSWER Sets VG state based on COLLECTIVE STATE of ALL Change records linked to the VG. What happens to VG state when a change is created? - CORRECT ANSWER VG state changes to Awaiting Implementation What happens to VG state when a change moves to Review? - CORRECT ANSWER VG state changes to Resolved Can state synchronisation be changed to work with different states? (page 163) - CORRECT ANSWER Yes. You can modify the BR/SI that controls the execution flow of the state synchronisation MODULE 4 ONWARDS NEEDS TO BE DONE DONT NEED TO DO ANYTHING FOR 6 AND 7 - CORRECT ANSWER .... What is a false positive? - CORRECT ANSWER Scenario where the scanner reports a vulnerability that exists in the system, but in reality, there is nothing What happens when you mark a VIT as 'False Positive'? - CORRECT ANSWER The state updates to Closed and the substate is changed to False Positive Can a false positive be reopened after closed? - CORRECT ANSWER Yes How does Exception Processing work with VR only? - CORRECT ANSWER - Two level approval workflow - Existing VIT state approval workflow is updated in Paris How does Exception Processing work with VR + GRC? - CORRECT ANSWER - Integrates with GRC Policy Exception process - Relates VR Policy to VIT Exception - Leverages the Compliance Approval flow VR Flow - CORRECT ANSWER Check Page 172 VR + GRC Flow? - CORRECT ANSWER Check 173 By default is VR or VR+GRC used? - CORRECT ANSWER VR (two-level process) What are Exception Rules - CORRECT ANSWER Records that allow to automate the VI Deferral process so that VIT are automatically deferred if they match a condition Do Exception Rules work on all data? - CORRECT ANSWER No. Only works on non-GRC Vulnerability Response data. Are Exception Rules defined for a set period? - CORRECT ANSWER Yes. There is a valid from and valid to date. Flow Designer best practices? - CORRECT ANSWER - Discuss with client, internal process that could be automated - Keep the flow simple - Connect to existing flows if necessary - Create sub flows that can be leveraged in different flows How to visualise data for CIO/CISO? - CORRECT ANSWER - Need high level overviews - Single, clear indicators How to visualise data for Managers? - CORRECT ANSWER - Need drill-down to granularity - Need time period views How to visualise data for Analysts? - CORRECT ANSWER - Need up-to-minute views - Need clear prioritizations - Need granularity What does Reporting provide? - CORRECT ANSWER Analysis on data of what HAS happened What does PA provide? - CORRECT ANSWER - Analysis to enable timely decision - Real time information - Insights into the performance of processes... allows to take action on processes as it happens instead of AFTER it happens e.g - P2 incidents not worked on in the last 24 hours Tables commonly used for reports? - CORRECT ANSWER - Vulnerability Item Task (sn_vul_m2m_item_task) - Vulnerability Group (sn_vul_vulnerability) - Vulnerable Item (sn_vul_vulnerable_item) - Vulnerability Entry (sn_vul_entry) - Related Business Services (sn_vul_m2m_ci_services) What are the 2 main types of indicators? - CORRECT ANSWER - Leading Indicators - Lagging Indicators What does a Leading Indicator do? - CORRECT ANSWER focuses on input that is required to achieve an objective What does a Lagging Indicator do? - CORRECT ANSWER Measures the output of your activities Benefits of Lagging and Leading Indicators? - CORRECT ANSWER - Leading indicators are harder to measure than lagging indicators - Leading indicators are easier to influence, compared to lagging indicators Is the full PA suite included in the Vulnerability Response Application? - CORRECT ANSWER No. Just Vulnerability Analytics 3 recommended uses of PA? - CORRECT ANSWER - Systematic analysis - Process Insight - Improved Outcomes What are the states for a VIT record? - CORRECT ANSWER - Open - Under Investigation - Awaiting Implementation - Resolved - Deferred - Closed - In Review What are the states for a Vulnerability Group record? - CORRECT ANSWER - Open - Under Investigation - Awaiting Implementation - Resolved - Deferred - Closed - In Review [Show More]
Last updated: 1 year ago
Preview 1 out of 25 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.50
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 30, 2023
Number of pages
25
Written in
Additional information
This document has been written for:
Uploaded
Aug 30, 2023
Downloads
0
Views
129