Computer Science > EXAMs > IAP 301 Final Exam | Verified with 100% Correct Answers (All)
IAP 301 Final Exam | Verified with 100% Correct Answers
Document Content and Description Below
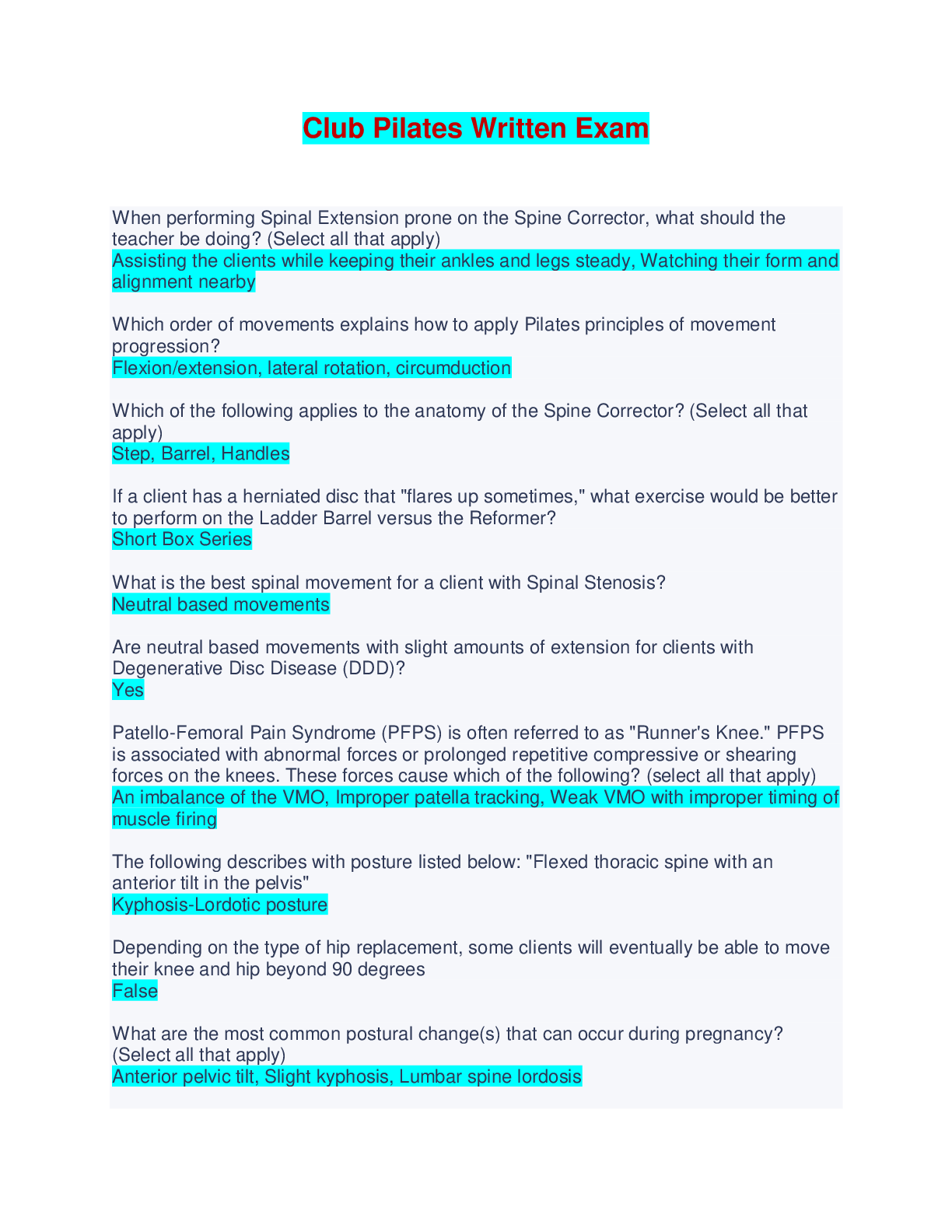
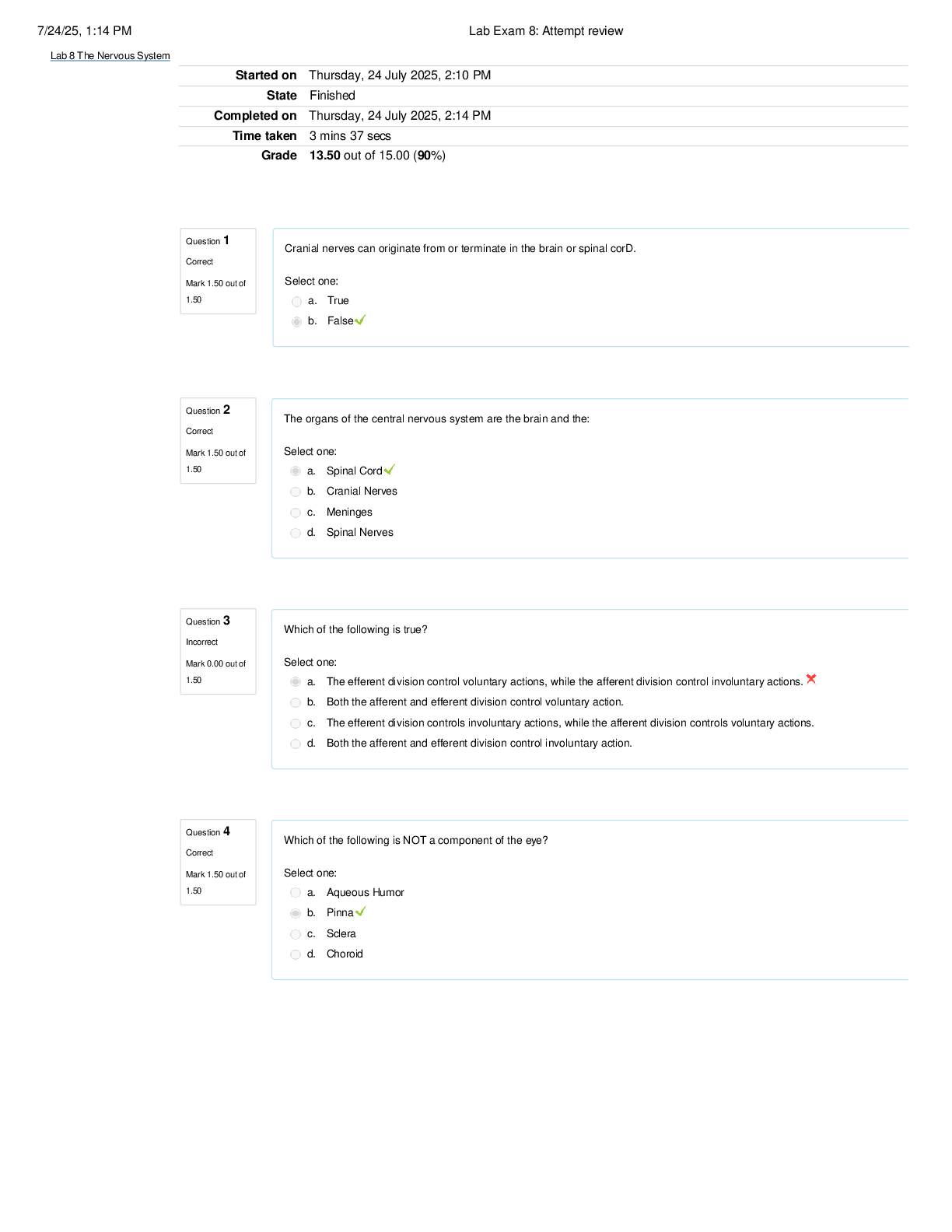
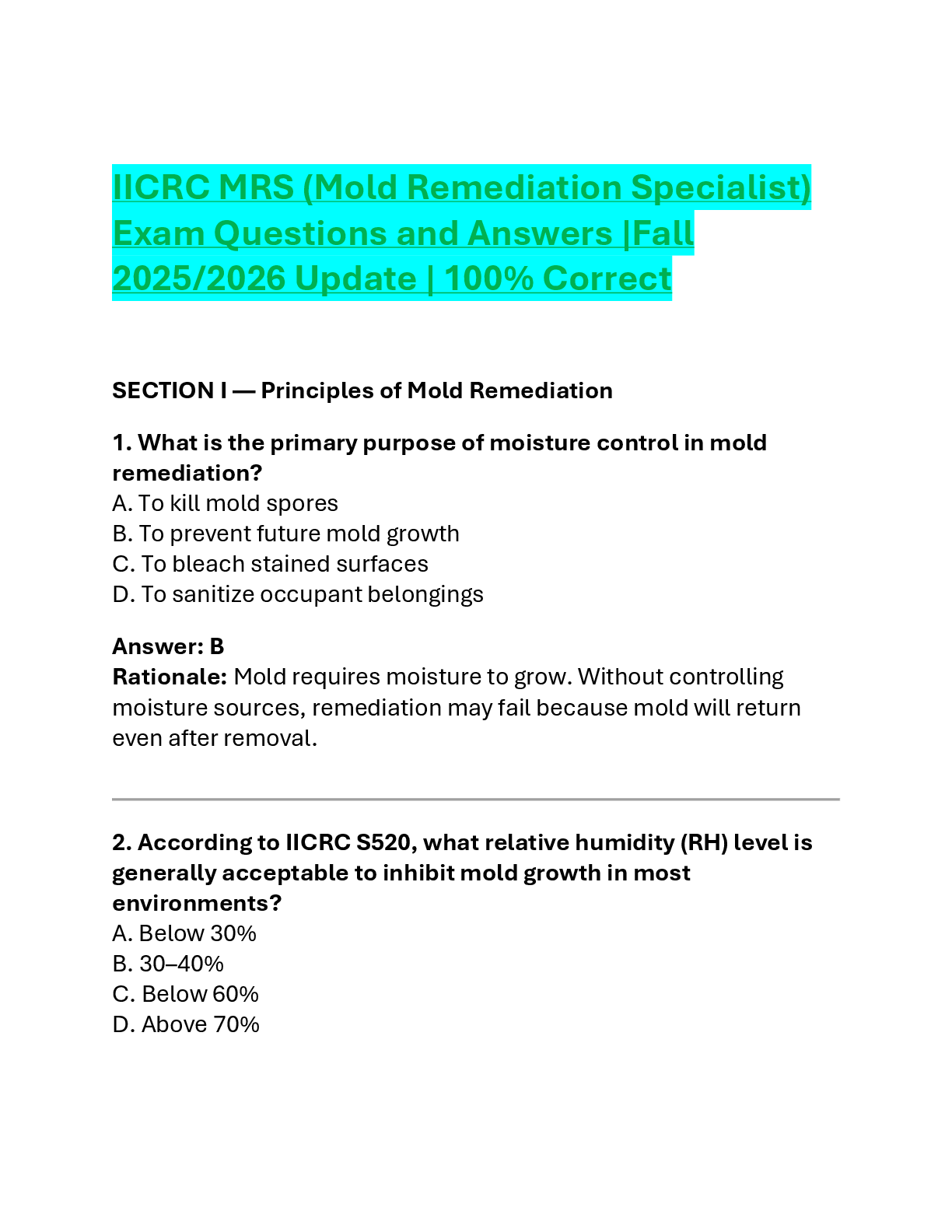
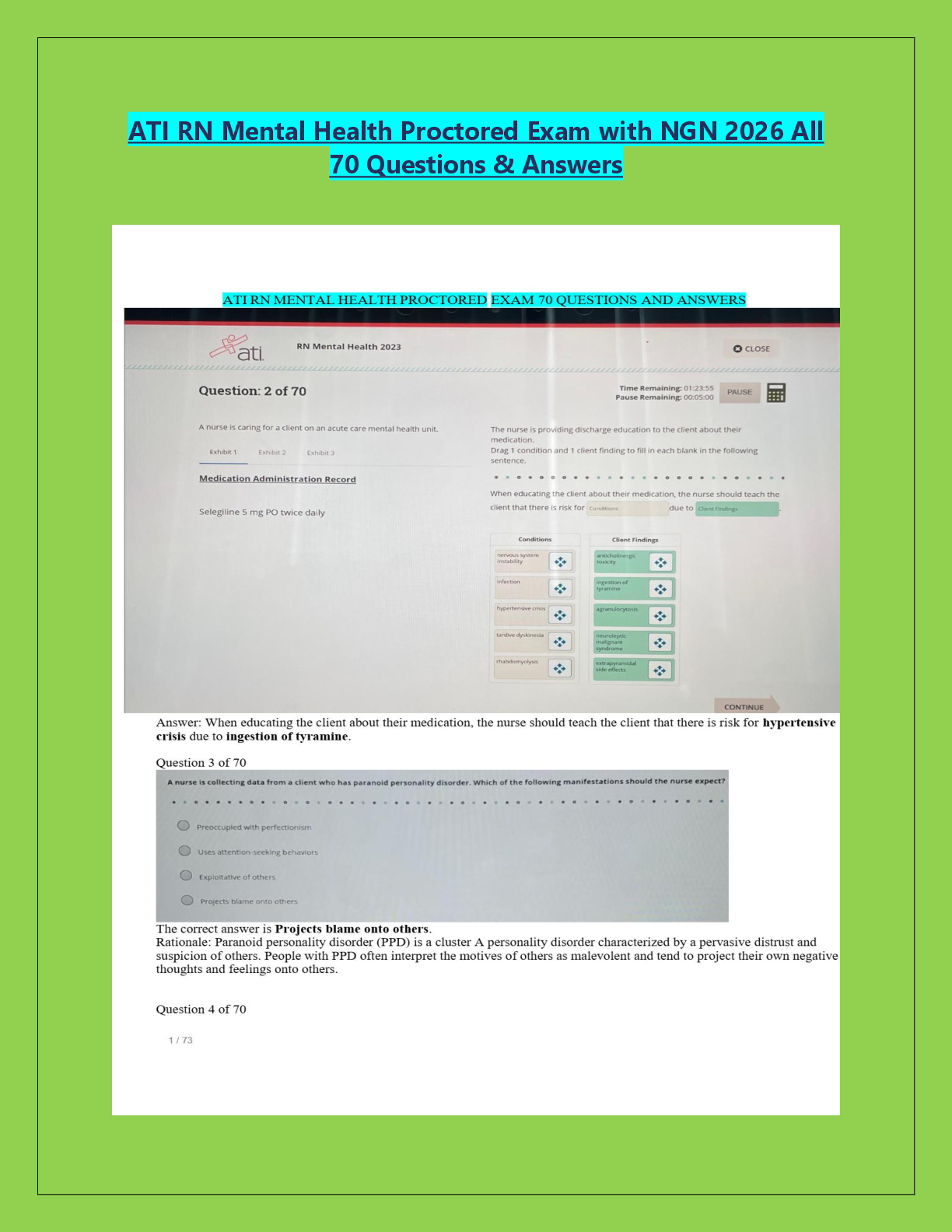
IAP 301 Final Exam | Verified with 100% Correct Answers John works in the accounting department but travels to other company locations. He must present the past quarter's figures to the chief execut ... ive officer (CEO) in the morning. He forgot to update the PowerPoint presentation on his desktop computer at the main office. What is at issue here? A. Unauthorized access to the system B. Integrity of the data C. Availability of the data D. Nonrepudiation of the data E. Unauthorized use of the system Governance is the practice of ensuring an entity is in conformance to policies, regulations, ________, and procedures. Standards COBIT is a widely accepted international best practices policy framework. a. True b. False Which of the following are generally accepted as IA tenets but not ISS tenets? (Select two.) A. Confidentiality B. Integrity C. Availability D. Authentication E. Nonrepudiation Greg has developed a document on how to operate and back up the new financial sections storage area network. In it, he lists the steps required for powering up and down the system as well as configuring the backup tape unit. Greg has written a ________. Procedure When should a wireless security policy be initially written? A. When the industry publishes new wireless standards B. When a vendor presents wireless solutions to the business C. When the next generation of wireless technology is launched D. After a company decides to implement wireless and before it is installed A toy company is giving its Web site a much-needed facelift. The new Web site is ready to be deployed. It's late October, and the company wants to have the site ready for the holiday rush. The year-end holiday season accounts for 80 percent of its annual revenue. What process would be of particular importance to the toy company at this time? A. Continuous improvement B. Business process reengineering C. Change management D. Information security system life cycle Implementation and enforcement of policies is a challenge. The biggest hindrance to implementation of policies is the ________ factor. Human Information systems security policies should support business operations. These policies focus on providing consistent protection of information in the system. This happens by controlling multiple aspects of the information system that directly or indirectly affect normal operations at some point. While there are many different benefits to supporting operations, some are more prevalent than others. Which of the following are aspects of ISS policies that extend to support business operations? A. Controlling change to the IT infrastructure B. Protecting data at rest and in transit C. Protecting systems from the insider threat D. B and C only E. All the above Ted is an administrator in the server backup area. He is reviewing the contract for the offsite storage facility for validity. This contract includes topics such as the amount of storage space required, the pickup and delivery of media, response times during an outage, and security of media within the facility. This contract is an example of information security. a. True b. False A weakness is found in a system's configuration which could expose client data to unauthorized users. Which of the following best describes the problem? A. A new threat was discovered. B. A new vulnerability was discovered. C. A new risk was discovered. D. A and B E. B and C F. A, B, and C What is policy compliance? A. The effort to follow an organization's policy B. When customers read a Web site policy statement C. Adherence to an organization's policy D. Failure to follow to an organization's policy What is an automated control? A. A control that stops behavior immediately and does not rely on human decisions B. A control that does not stop behavior immediately and relies on human decisions C. A control that does not stop behavior immediately but automates notification of incident D. A control that stops behavior immediately and relies on human decisions Which of the following is not a business driver? A. Ability to acquire the newest technology B. Cost of maintaining controls C. Ability to legally defend D. Customer satisfaction A firewall is generally considered an example of a ________ control Preventive What is an information security policy? A. A policy that defines acceptable behavior of a customer B. A policy that defines what hardware to purchase C. A policy that defines how to protect information in any form D. A policy that defines the type of uniforms guards should wear Which of the following is not a type of security control? A. Preventative B. Correlative C. Detective D. Corrective Tone at the top refers to: A. A company's leaders making sure every employee knows the priorities B. Senior leaders implementing and enforcing policies C. Senior managers building trust with the public and with regulators D. All of the above Privacy regulations involve two important principles: full disclosure and data encryption. a. True b False What are the benefits to having a security awareness program emphasize the business risk? A. Risk becomes more relevant to employees B. Security policies are more likely to be followed C. Provides employees a foundation to deal with unexpected risk D. All of the above Which of the following is not a guideline to be considered when developing policy to secure PII date? A. Align—Coordinate privacy policies with data classification policies B. Retain—Ensure proper controls around data retention and destruction C. Disclose—Fully disclose to the individual what data is being collected and how it will be used D. Resiliency—Policies provide guidelines for the unexpected Information used to open or access a bank account is generally considered PII data. a. True b. False Which of the following is not a benefit of having an acceptable use policy? A. Outlines disciplinary action for improper behavior B. Prevents employees from misusing the Internet C. Reduces business liability D. Defines proper behavior while using the Internet Mitigating controls always meet the full intent of the policy. A. True B. False Which of the following do you need to measure to achieve operational consistency? A. Consistency B. Quality C. Results D. All of the above Well-defined and properly implemented security policies help the business in which of the following ways? A. Maximize profit B. Reduce risk C. Produce consistent and reliable products D. All of the above When creating laws and regulations, the government's sole concern is the privacy of the individual. A. True B. False Which of the following are pressures on creating security policies? A. Shareholder value B. Regulations C. Technology vulnerabilities and limitations D. B and C only E. All of the above Which of the following laws require proper security controls for handling privacy data? A. HIPAA B. GLBA C. FERPA D. B and C Only E. All of the above Which of the following are control objectives for PCI DSS? A. Maintain an information security policy B. Protect cardholder data C. Alert when credit cards are illegally used D. A and B only E. None of the above Nation-state attacks that try to disrupt the country's critical infrastructure are sometimes referred to as ________. Cyberterrorism or cyberwarfare Health care providers are those that process and facilitate billing. A. True B. False The law that attempts to limit children's exposure to sexually explicit material is ________. CIPA The only consideration in protecting personal customer information is legal requirements. A. True B. False You should always write new security policies each time a new regulation is issued. A. True B. False What should you ask for to gain confidence that a vendor's security controls are adequate? A. An SSAE16 Type I audit B. An SSAE16 Type II audit C. A list of all internal audits D. All of the above Why is it important to map regulatory requirements to policies and controls? A. To demonstrate compliance to regulators B. To ensure regulatory requirements are covered C. To demonstrate the importance of a security control D. All of the above Who typically writes a report to the board of directors on the current state of information security within a company? A. Chief risk officer B. Chief information officer C. Chief information security officer D. A and B E. B and C F. All of the above Private WANs must be encrypted at all times. A. True B. False Which of the following attempts to identify where sensitive data is currently stored? A. Data Leakage Protection Inventory B. DLP Encryption Key C. Data Loss Protection Perimeter D. DLP Trojans Voice over Internet Protocol (VoIP) can be used over which of the following? A. LAN B. WAN C. Both D. Neither Which of the following is not one of the seven domains of typical IT infrastructure? A. Remote Access Domain B. LAN Domain C. World Area Network Domain D. System/Application Domain Which of the seven domains refers to the technical infrastructure that connects the organization's LAN to a WAN and allows end users to surf the Internet? LAN-to-WAN Domain One key difference between RBAC and ABAC is which of the following? A. ABAC is dynamic and RBAC is static. B. ABAC is static and RBAC is dynamic. C. No difference; these are just different terms to mean the same thing. A ________ is a term that refers to a network that limits what and how computers are able to talk to each other. Segmented network A LAN is efficient for connecting computers within an office or groups of buildings. A. True B. False What policy generally requires that employees lock up all documents and digital media at the end of a workday and when not in use? A. Acceptable use policy B. Clean desk policy C. Privacy policy D. Walk out policy What employees learn in awareness training influences them more than what they see within their department. A. True B. False What kind of workstation management refers to knowing what software is installed? A. Inventory management B. Patch management C. Security management D. Discovery management Always applying the most strict authentication method is the best way to protect the business and ensure achievement of goals. A. True B. False Generally, remote authentication provides which of the following? A. Fewer controls than if you were in the office B. The same controls than if you were in the office C. More controls than if you were in the office D. Less need for controls than in the office Remote access does not have to be encrypted if strong authentication is used. A. True B. False Where is a DMZ usually located? A, Inside the private LAN B, Within the WAN C, Between the private LAN and public WAN D, Within the mail server Dedicated network devices whose only function is to create and manage VPN traffic are called VPN _______ Concentrators What is a botnet? A. A piece of software the end user loads onto a device to prevent intrusion B. A piece of software a company loads onto a device to monitor its employees C. A piece of software a hacker loads onto a device without user knowledge D. A piece of software used to communicate between peers The minimum standard in authentication for businesses is the use of ________. IDs and Passwords Which of the following is a basic element of motivation? A. Pride B. Self-interest C. Success D. B and C E. All of the above Which personality type often breaks through barriers that previously prevented success? A. Attackers B. Commanders C. Analyticals D. Pleasers Avoiders like to ________ and will do _______ but not much more. Be in the background; precisely what is asked of them As the number of specialties increases so does ________. The cost of business In hierarchical organizations, the leaders are close to the workers that deliver products and services. a. True b. False User apathy often results in an employee just going through the motions. a. True b. False Which of the following is a method for overcoming apathy? A. Avoiding redundancy B. Issuing company directives C. Engaging in communication D. Requiring obedience to policies Why is HR policy language often intentionally vague? A. To avoid being interpreted as an unintended promise B. To start lawsuits C. To avoid being too severe for new hires In the case of policies, it is important to demonstrate to business how polices will reduce risk and will be derived in a way that keeps costs low. a. True b. False Kotter's Eight-Step Change Model can help an organization gain support for _______ changes. Security policy An ideal time to refresh security policies is during a reduction in force. a. True b. False When a catastrophic security breach occurs, who is ultimately held accountable by regulators and the public? A. Company officers B. The CIO C. The ISO D. The data owner Which of the following are attributes of entrepreneurs? Innovators A. Well educated in business management B. More likely to take risks C. A and C D. B and C A control partner's role includes analysis of proposed policy changes and providing an opinion on their viability. a. True b. False Which of the following is the best measure of success for a security policy? A. Number of security controls developed as a result B. The number of people aware of the policy C. Reduction in risk D. The rank of the highest executive who approved it A change agent typically will a. Ensure current processes are working b. Ensure application code changes are well understood c. Challenge whether a company's existing processes represent the best approach An IT policy framework charter includes which of the following? A. The program's purpose and mission B. The program's scope within the organization C. Assignment of responsibilities for program implementation [Show More]
Last updated: 1 year ago
Preview 5 out of 29 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$18.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jul 21, 2024
Number of pages
29
Written in
All
Additional information
This document has been written for:
Uploaded
Jul 21, 2024
Downloads
0
Views
107