Computer Science > EXAM > CDS 348 Final Exam | Questions with Verified Answers (All)
CDS 348 Final Exam | Questions with Verified Answers
Document Content and Description Below
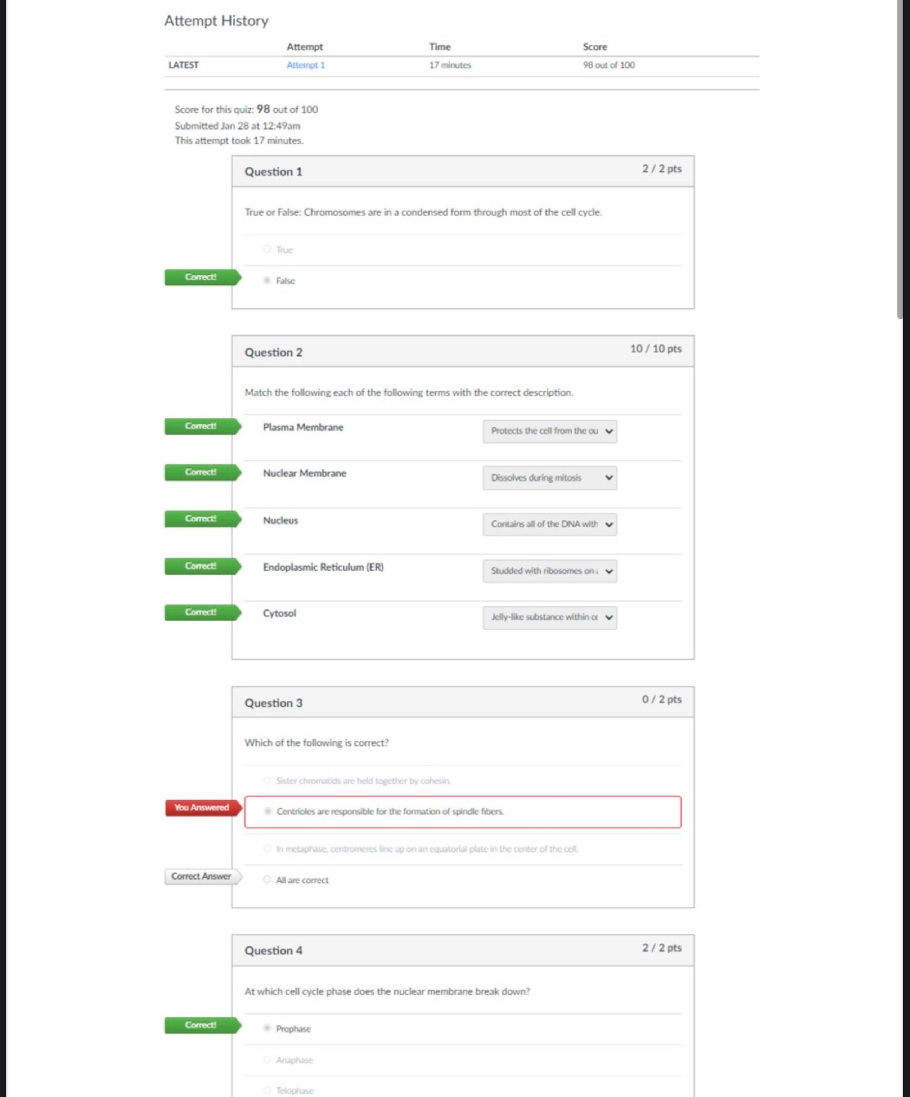
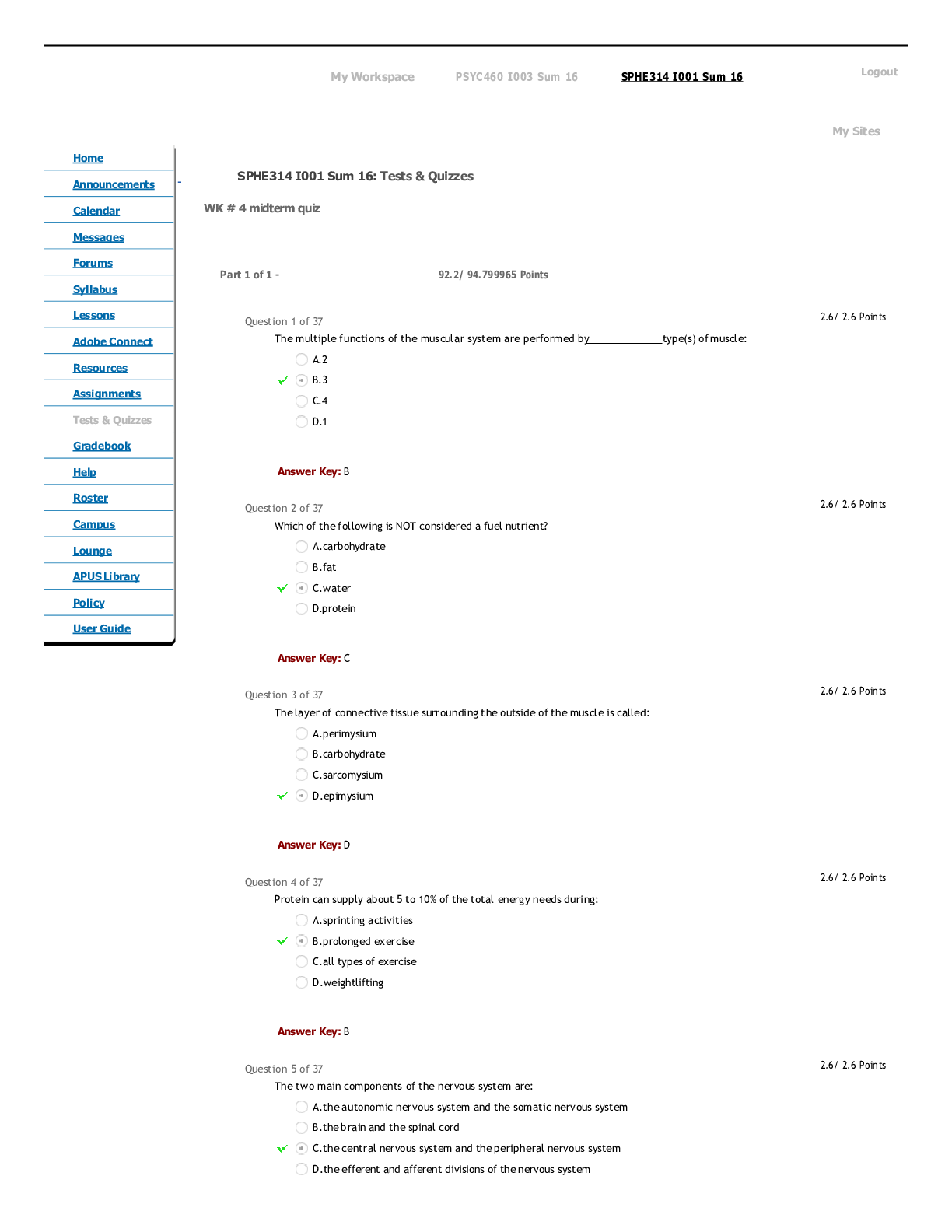
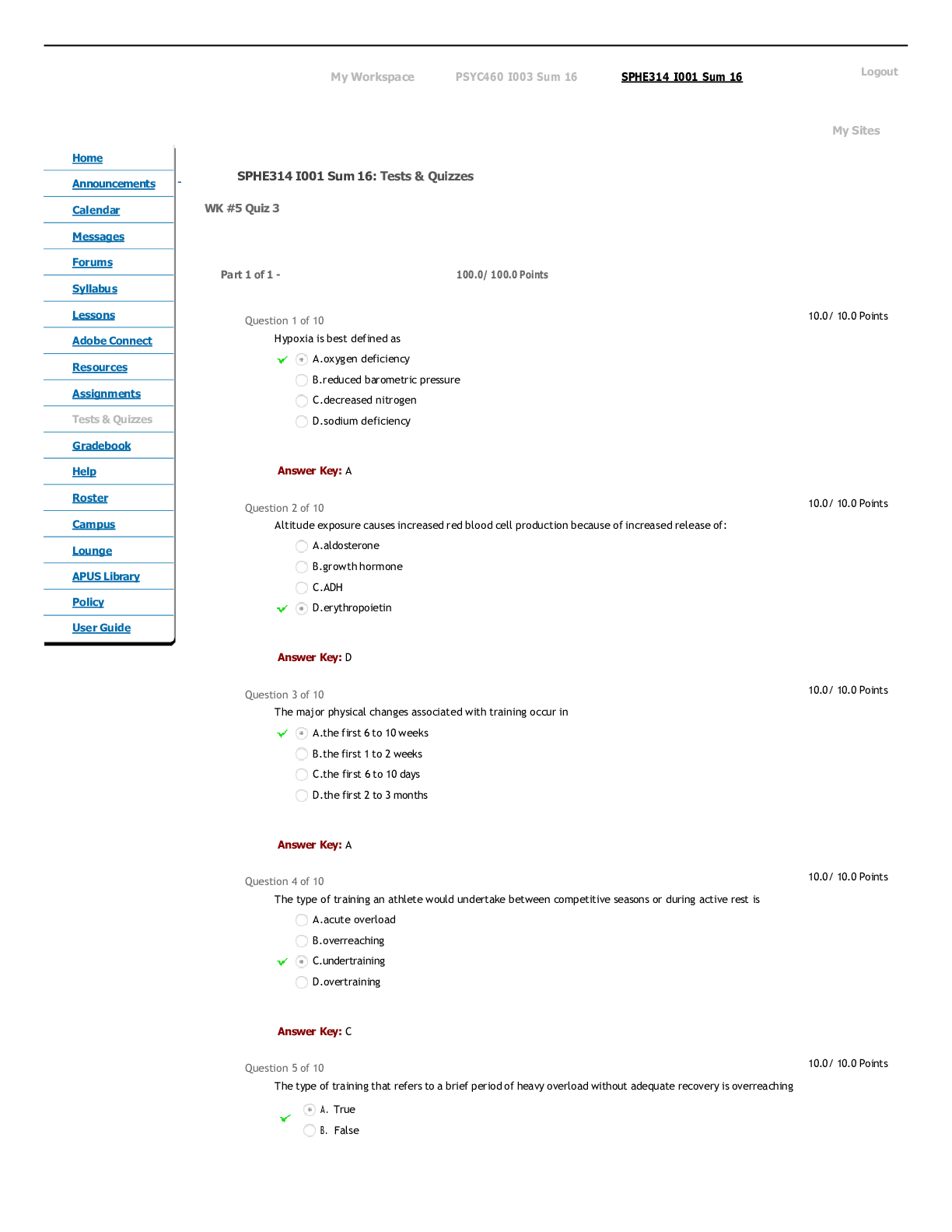
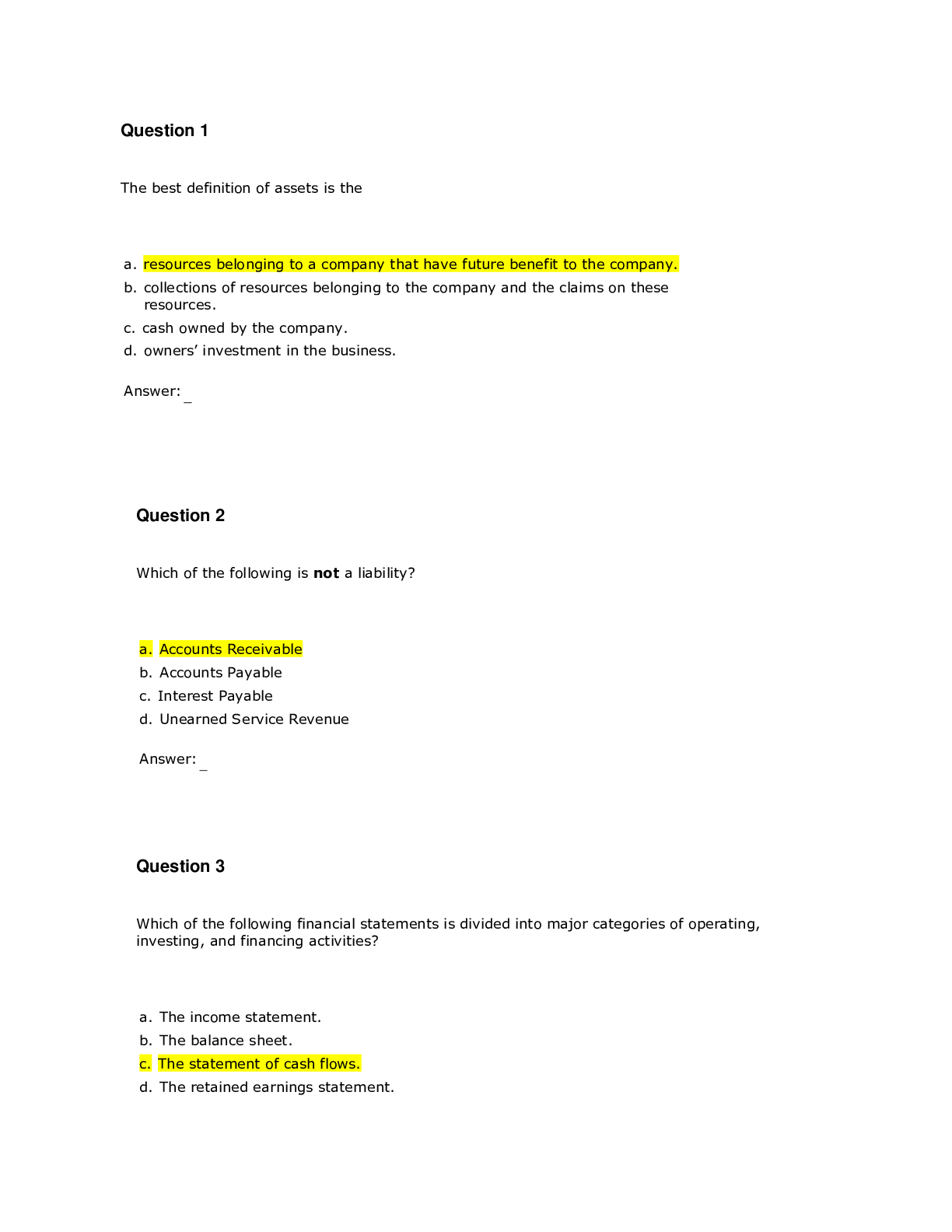
CDS 348 Final Exam | Questions with Verified Answers One of the more commonly seen and most easily avoided incidents is the "blank" attack, where employees are bombarded with numerous attempts to c... onvince them to activate a link embedded in an e-mail or respond to a request for communications with an unknown outside party, often masquerading as a known entity Phishing a staffed control room where key security technologies, networks, and critical systems are monitored for incidents is known as a(n) security operations center if an intruder can blank a device, then no electronic protection can deter the loss of information physical access A(n) blank may signal an adverse event is under way and provide a notification of an incident candidate Indicator blank is the organized research and investigation of Internet addresses owned or controlled by a target organization footprinting a series of steps that follow the stages of a cyberattack from early reconnaissance to the exfiltration of data is known as the blank cyber kill chain A(n) blank may signal an incident that could occur in the future Precursor the theft of organizational data, either physically or by extraction through the owners' networks is called data blank exfiltration NIST SP 800-61, Rev. 1 provides a five category classification scheme for a network-based incidents that includes each of these except all of these are NIST incident classification a set of software functionalities with capabilities that different clients can reuse for different purposes is called a(n) blank service which of the following is not a "probable indicator" of an incident presence or execution of unknown programs or processes the failure of a technical control to react to the intended stimulus so that it goes unreported is called a blank false negative gathering information on and identifying network assets is known as fingerprinting true the most common detection of ransomware is via a message to a user that they have been locked out of their computer system, and that their files and data have been encrypted true the most common detection of denial of service attack is a message to a user that they have been locked out of their computer system, and that their files and data have been encrypted false software designed to penetrate security controls, identify valuable content, and then encrypt files and data in order to extort payment for the key needed to unlock the encryption is known as blackmail false an example of a possible indicator is if a business partner or another connected organization reports an attack from your computing system false an indicator is an activity in progress that may signal an incident could occur in the future false only those with advanced technical skills within a certain set of hardware and software can manually detect signs of a(n) blank through reviews of logs, systems performance, user feedback, and system processes and tasks intrusion the use of IDPS sensors and analysis systems can be quite complex. One very common approach is to use an open source software program called blank running on a UNIX or Linux system that can be managed and queried from a desktop computer using a client interface snort which is the most important factor when selecting a SIEM solution the extent to which the SIEM system provides the required features the organization needs like the Wiretap Act's prohibition on intercepting the contents of communications, the blank creates a general prohibition on the real time monitoring of traffic data relating to communications Pen/Trap statute the SIEM capability of blank enables review of system activity that can identify breaches and reveal insider misuse user monitoring blank are closely monitored network decoys that can distract adversaries from more valuable machines on a network, provide early warning about new attack and exploitation trends; and can allow in-depth examination fo adversaries during and after exploitation honeypots blank system use a combination of resources to detect an intrusion and then track it back to its source; they must be used with caution to avoid illegal actions trap and trace the SIEM capability of blank enables flexible and timely reaction to attacks real time monitoring a blank rootkit is one that becomes a part of the system bootstrap process and is loaded every time the system boots persistent the process of classifying the attack alerts that an IDPS detects in order to distinguish or sort false positives from actual attacks more efficiently is known as alarm blank filtering by guarding against some types of vulnerabilities, an IDPS can become an important part of an organization's blank strategy defense in depth a unique value or pattern of an attack that enables detection is called a(n) signature the ongoing activity from alarm events that are accurate and noteworthy but not necessarily as significant as potentially successful attacks is called blank nosie the problem with a signature based IDPS is that as new attack strategies are identified, the IDPS's database of signatures must be continually updated true alarm condensation is a process based on frequency, similarity in attack signature, similarity in attack target, or other similarities false tweaking is the process of adjusting an IDPS to maximize its efficiency in detecting true positives while min false positives and false negatives false the most important factor in selecting a SIEM system is the extent that it provides the required features the organization needs true blank is a technique for examining and verifying current network traffic for packets that do not conform to TCP/Ip protocol specifications protocol stack verification blank is a process of reducing IDPS events in order to feel more confident in the alerts received filtering blank is/are a common indicator of a DoS attack user reports of system unavailability in a "block" containment strategy, in which the attacker's path into the environment is disrupted, you should use the most precise strategy possible, starting with blank blocking a specific IP address according to NIST, which of the following is an example of an unauthorized access attack modifying web based content without permission the organization will most likely blank to an internal user attempting to escalate privilege than to an external hacker respond differently when an incident includes a breach of physical security, all aspects of physical security should be escalated under a containment strategy known as blank lockdown in the event of a reported password breach, the organization should first plan to blank implement an immediate password change a blank attack is much more substantial than a DoS attack because of the use of multiple systems to simultaneously attack a single target distributed denial of service many malware attacks are blank attacks, which involve more than one type of malware and/or more than one type of transmission method blended there are a number of profession IR agencies, such as blank, that can provide additional resources to help prevent and detect DoS incidents US-CERT the primary preparation and prevention strategy for inappropriate use violations is blank organizational policy blank are procedures for regaining control of systems and restoring operations to normalcy; they are the heart of the IR plan and the CSIRT's operations IR reaction strategies blank is a tactic that deliberately permits an attack to continue while the entire event is observed and additional evidence is collected watchful waiting the CSIRT must document and preserve every action, file, event, and item of potential explanatory value false after the immediacy of incident containment has passed, the organization is still faced with the unavailability that inevitable results after an unauthorized access to a system false the legal term for attempts at unauthorized access is "exceeding enabled access" false once the CSIRT has been notified and arrives "on scene," whether physically or virtually, the first task that must occur is the resolution of the situation false the term unauthorized access refers to attempts by insiders to escalate their privileges, access information, and access other assets to which they do not explicitly have authorization true unauthorized use is a category of incidents that covers a spectrum of violations made by authorized users of a system who nevertheless use it in ways specifically prohibited by management false [Show More]
Last updated: 8 months ago
Preview 4 out of 11 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$15.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 10, 2024
Number of pages
11
Written in
Additional information
This document has been written for:
Uploaded
Oct 10, 2024
Downloads
0
Views
11