NEW TEAS 7 MATH V4
$ 50
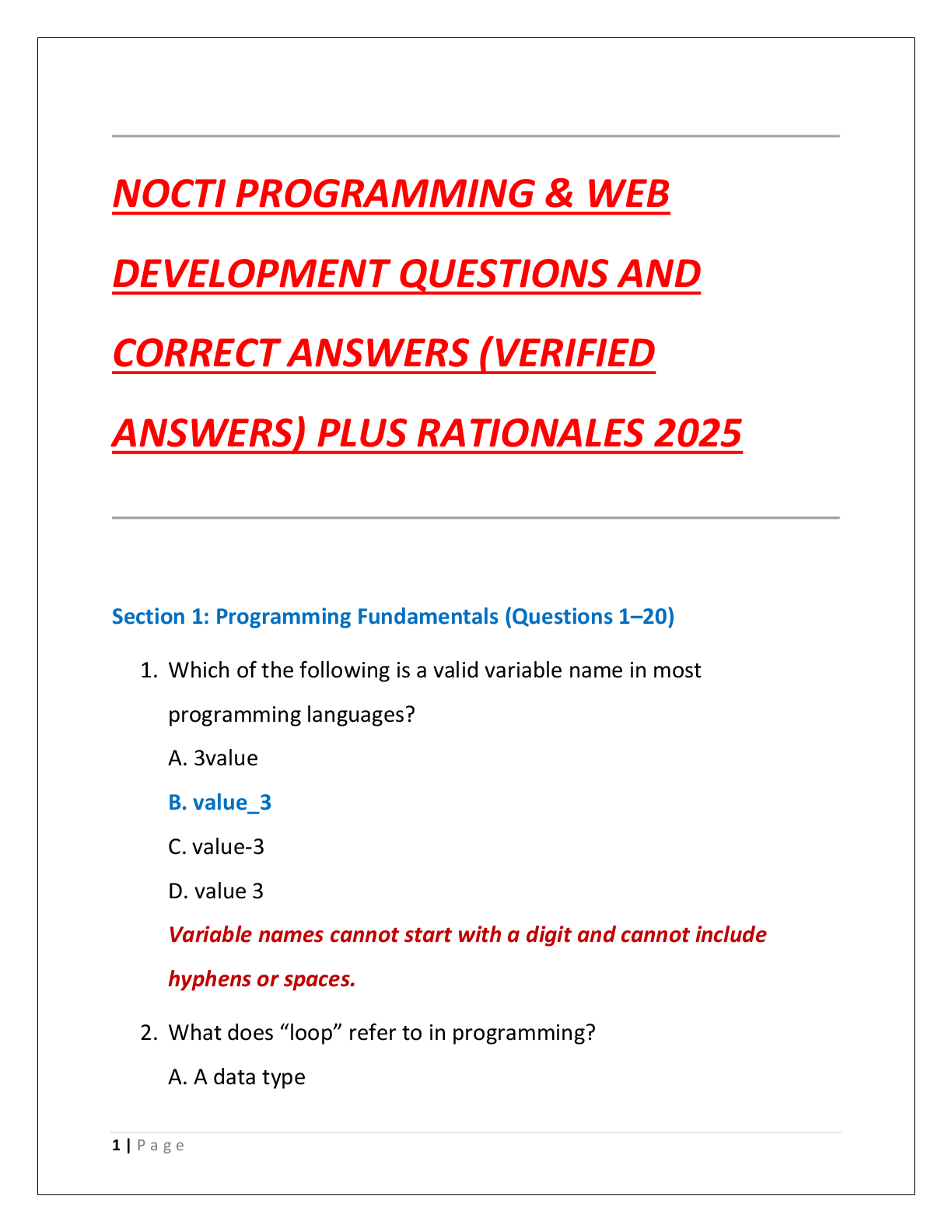
NOCTI PROGRAMMING & WEB DEVELOPMENT QUESTIONS AND CORRECT ANSWERS (VERIFIED ANSWERS) PLUS RATIONALES 2025
$ 15

2024 HESI Cardiovascular Disorders Exam Guaranteed A+ Actual Questions and Answers, Complete 100%
$ 14

ASVAB Study Guide-2022-2023
$ 11

data and data management study guide
$ 8

eBook ioremediation and Phytoremediation Technologies in Sustainable Soil Management, Volume 4,1st Edition By Junaid Ahmad Malik, Megh R.Goyal, Khursheed Ahmad Wani
$ 30

eBook Urinalysis in the Dog and Cat Primera 1st Edition By Dennis J. Chew,Patricia A. Schenck
$ 30

Dalisay Edwards OBGYN
$ 12.5

INDR 372 Production Planning and Control _INDR 372 Review Exercises for the Midterm Exam.
$ 6.5

nur 150 test 3 guide
$ 15

Sampling Design and Analysis 2nd Edition Solution Manual
$ 24
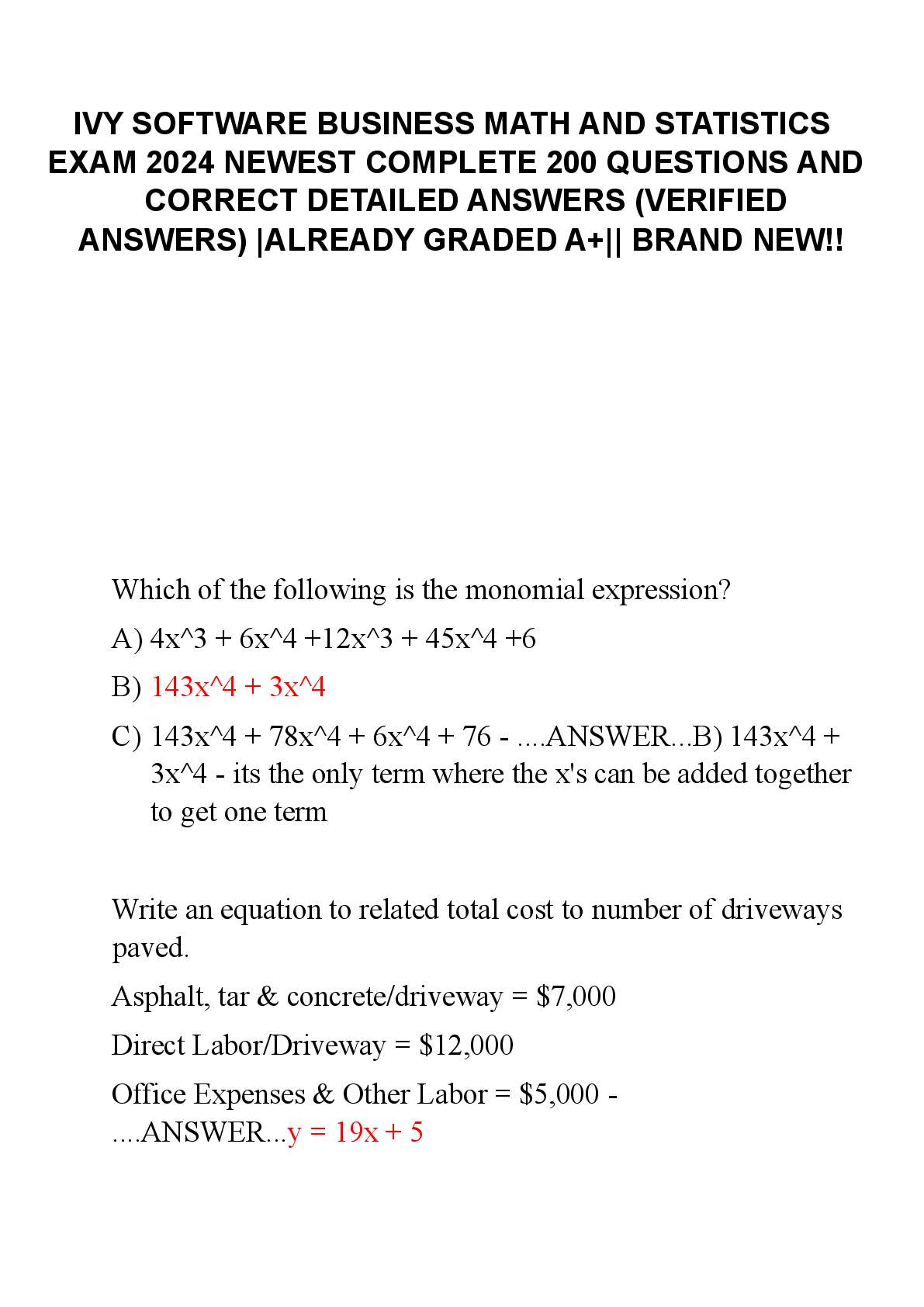
IVY SOFTWARE BUSINESS MATH AND STATISTICS EXAM 2024 NEWEST COMPLETE 200 QUESTIONS AND CORRECT DETAILED ANSWERS (VERIFIED ANSWERS) ALREADY GRADED A+ BRAND NEW!!
$ 18

eBook Formal Methods, 26th International Symposium, FM 2024, Milan, Italy, September Proceedings, Part I: 14933, 1st edition by André Platzer, Kristin Yvonne Rozier, Matteo Pradella
$ 30
BIOD 171 EXAM MODULE 4
$ 11

[eBook][PDF] Modern Database Management, 12th Edition By Jeffrey Hoffer, Ramesh Venkataraman, Heikki Topi
$ 14.5

NURS 6501N MIDTERM EXAM
$ 15
ISBAR_Gestational Diabetes
$ 9.5

E book Bioelectronics and Medical Devices Applications and Technology 1st Edition by Garima Srivastava Manju Khari









.png)

.png)