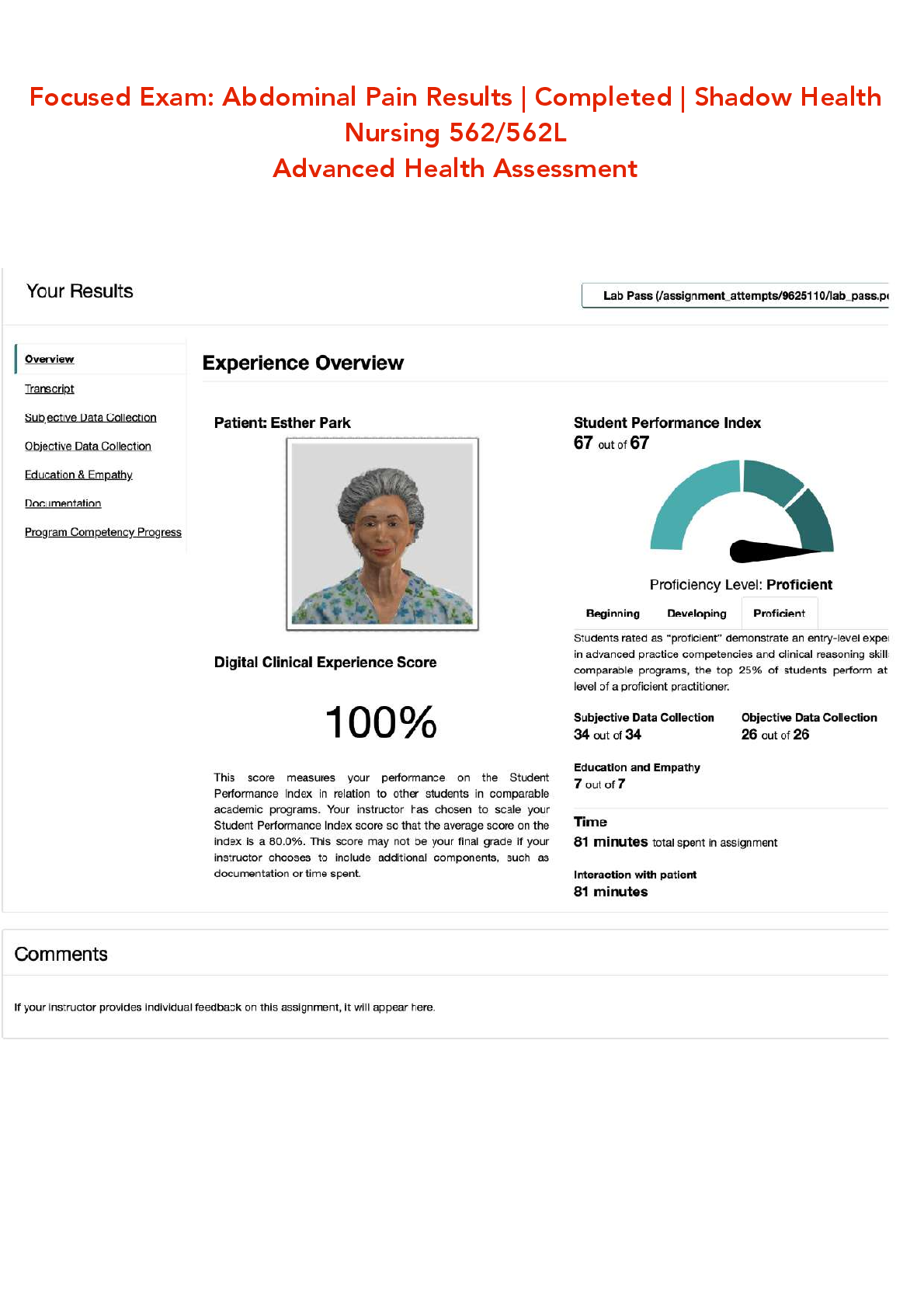
Which Event Correlation Approach checks and compares all the fields systematically and intentionally for positive and negative correlation with each other to determine the correlation across one or multiple fields?
gr
...
Which Event Correlation Approach checks and compares all the fields systematically and intentionally for positive and negative correlation with each other to determine the correlation across one or multiple fields?
graph-based approach
rule-based approach
field-based approach
automated field correlation
Minimizing the tangible and intangible losses to the organization or an individual is considered an essential computer forensics use.
A. True
B. False
Which field type refers to the volume descriptor as a primary?
A. Number 2
B. Number 0
C. Number 1
D. Number 3
This phase of EFI consists of initialization code that the system executes after powering the EFI system on. It manages platform reset events and sets the system so that it can find, validate, install, and run the PEI.
A. SEC
B. PEI
C. DXE
D. BDS
E. RT
Most of the initialization happens in this phase. Using the Hand-Off Block List (HOBL), it initializes the entire system physical memory, I/O, and MIMO (Memory Mapped Input Output) resources and finally begins dispatching DXE Drivers present in the system Firmware Volumes (given in the HOBL). The DXE core produces a set of EFI Boot Services and EFI Runtime Services. The EFI Boot Services provided are allocating memory and loading executable images. The EFI Runtime services provided are converting memory addresses from physical to virtual while handing over to the kernel, and resetting the CPU, to code running within the EFI environment or within the OS kernel once the CPU takes the control of the system.
A. SEC
B. PEI
C. DXE
D. BDS
E. RT
This phase initializes the CPU, temporary memory, and boot firmware volume (BFV). It locates and executes the Pre Initialization chapters (PEIMs) present in the BFV so as to initialize all the found hardware in the system. Finally, it creates a Hand-Off Block List with all found resources interface descriptors and passes it to the next phase i.e. the DXE phase.
A. SEC
B. PEI
C. DXE
D. BDS
E. RT
In this phase, the BDS interprets the boot configuration data and selects the Boot Policy for later implementation. This phase works with the DXE to check if the device drivers require signature verification.In this phase, the system loads MBR boot code into memory for Legacy BIOS Boot or loads the Bootloader program from the EFI partition for UEFI Boot. It also provides an option for the user to choose EFI Shell or an UEFI application as the Boot Device from the Setup.
A. SEC
B. PEI
C. DXE
D. BDS
E. RT
At this point, the system clears the UEFI program from memory and transfers it to the OS. During UEFI BIOS update the OS calls the run time service using a small part of the memory.
A. SEC
B. PEI
C. DXE
D. BDS
E. RT
Which of the following basic partitioning tools displays details about GPT partition tables in Windows OS?
A. DiskPart
B. Gparted
C. Disk Utility
D. Fdisk
[Show More]
















.png)

.png)