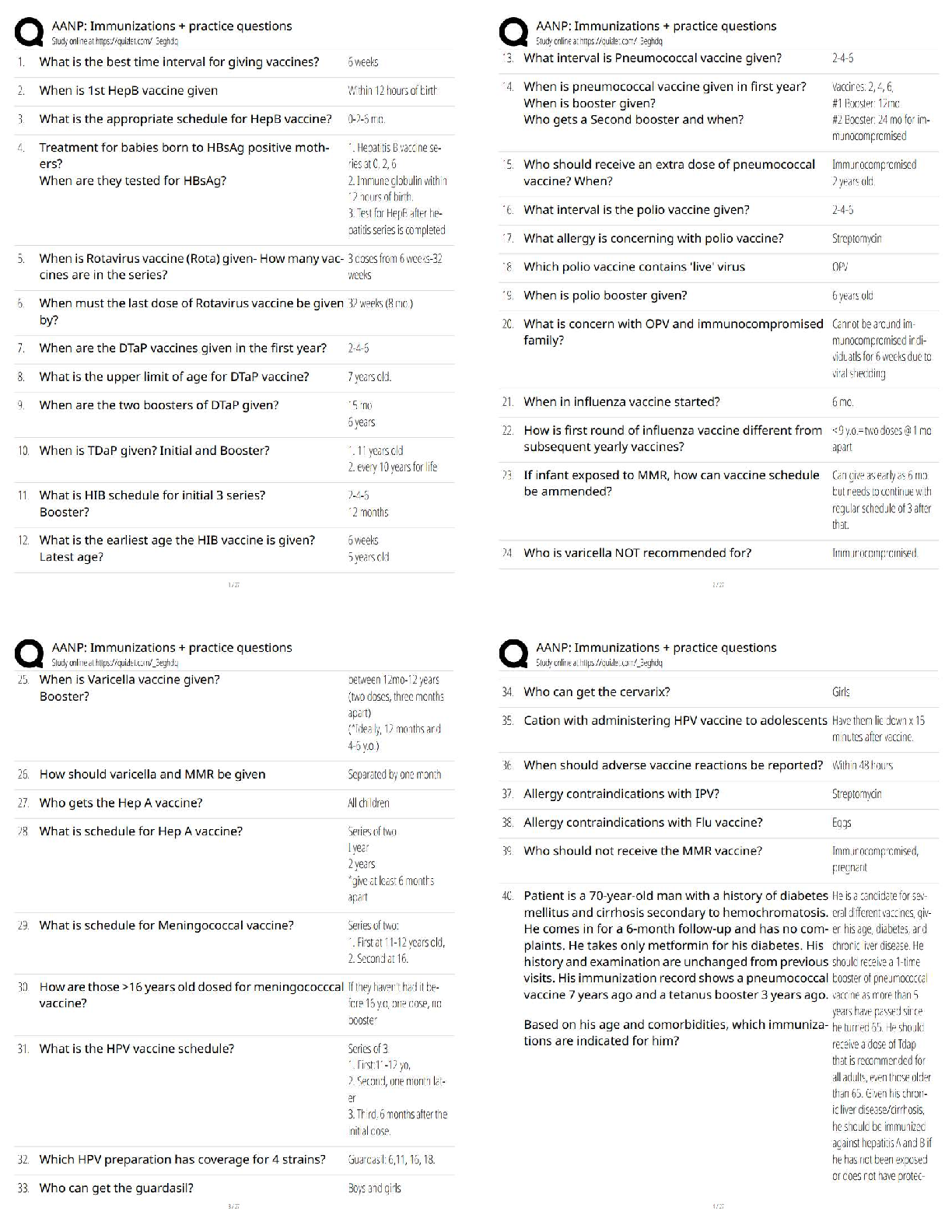
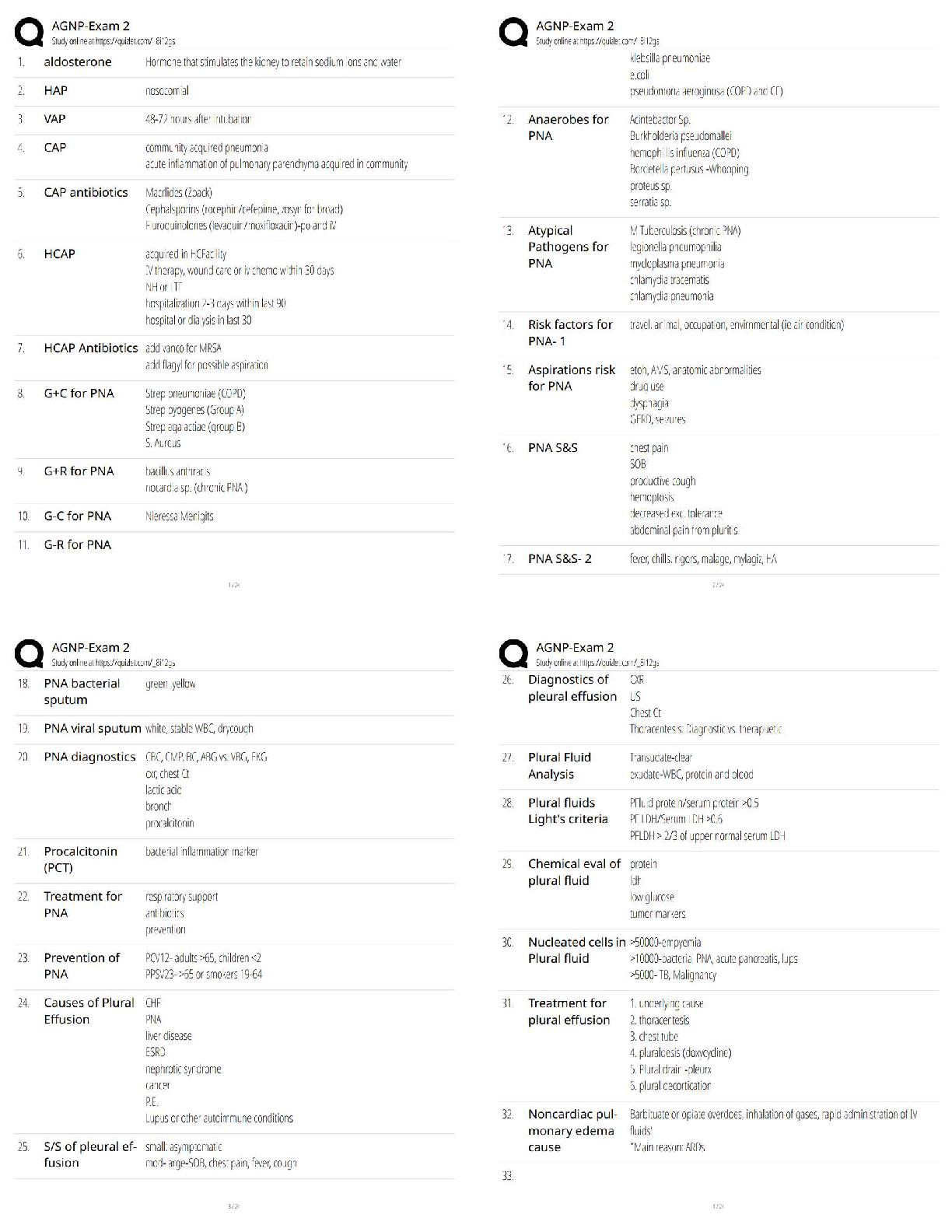
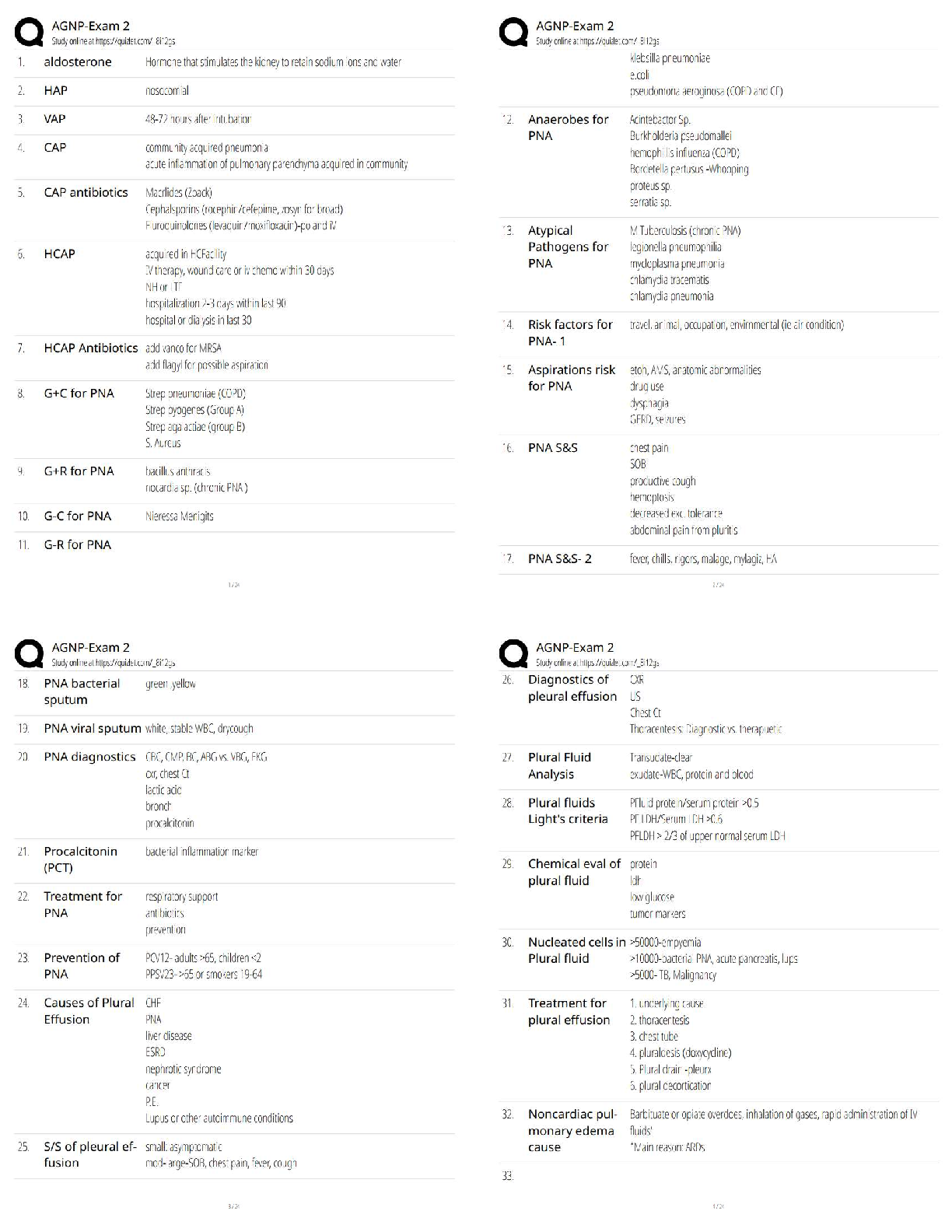
A network infrastructure supervisor is designing a firewall placement strategy that will protect the organization's Internet-facing web and email servers and the internal network. Which design will best protect both? - A
...
A network infrastructure supervisor is designing a firewall placement strategy that will protect the organization's Internet-facing web and email servers and the internal network. Which design will best protect both? - ANSWER Using two firewalls to create a demilitarized zone (DMZ); one firewall is placed between the Internet and the servers, the other firewall is located behind the first firewall and the servers protecting the internal network
Demetrice is a network consultant. She has been hired to design security for a network that hosts 25 employees, many of whom need remote access. The client recently opened another small office in a neighboring community and wants to be able to routinely establish secure network connections between the two locations. The client often deals with customer bank information and requires a particularly secure solution. What is her response to these requirements? - ANSWER Small office/home office (SOHO) virtual private network (VPN)
Tonya is redesigning her company's network infrastructure to accommodate rapid growth. Several departments are highly specialized. Tonya needs to allow Network News Transfer Protocol (NNTP) on some, but not all, subnets. Her budget is limited. Which of the following is the best solution? - ANSWER Place existing routers capable of packet filtering at each subnet.
Israel is a network technician who has just deployed a new firewall. Before putting it in production, he wants to test the firewall's ability to filter traffic according to its rule set, without risking the internal network. What is the best solution? - ANSWER Place the firewall outside the demilitarized zone (DMZ) with a production firewall behind it protecting the internal network.
Which of the following records every connection outside the network on the Internet by IP address and URL requested? - ANSWER Proxy server
A web server between two firewalls is considered to be in a demilitarized zone (DMZ). - ANSWER True
All firewalls provide network perimeter security. - ANSWER False
A bastion host is a ____
server
host
router
none of the above - ANSWER none of the above
Which of the following is true about DMZ?
The DMZ is located between an Internal Network and an external network.
Communications from the internal and the external network to the DMZ are permitted
Communication from the DMZ to connect to the internal network is not permitted
All of the above - ANSWER All of the above
What is an example of security through obscurity? - ANSWER Using a nonstandard operating system for workstations such as FreeBSD
Jacob is a network technician who works for a publishing company. He is setting up a new hire's access permissions. The new hire, Latisha, is an editor. She needs access to books that have been accepted for publication but are in the review stage. Jacob gives her access to the network drive containing only books in review, but not access to administrative or human resources network drives. What principle is Jacob applying? - ANSWER The principle of least privilege
Which of the following is described as an approach to network security in which each administrator is given sufficient privileges only within a limited scope of responsibility? - ANSWER Separation of duties
Landon is a network contractor. He has been hired to design security for the network of a small company. The company has a limited budget. Landon is asked to create a system that will protect the company's workstations and servers without undo expense. Landon decides to deploy one hardware firewall between the Internet and the local area network (LAN). What is this solution called? - ANSWER Single defense
Which of the following can be described as putting each resource on a dedicated subnet behind a demilitarized zone (DMZ) and separating it from the internal local area network (LAN)? - ANSWER N-tier deployment
Alejandro is a cybersecurity contractor. He was hired by a Fortune 500 company to redesign its network security system, which was originally implemented when the company was a much smaller organization. The company's current solution is to use multiple firewall platforms from different vendors to protect internal resources. Alejandro proposes an infrastructure security method that, in addition to firewalls, adds tools such as an intrusion detection system (IDS), antivirus, strong authentication, virtual private network (VPN) support, and granular access control. What is this solution called? - ANSWER Diversity of defense
Joaquin is a senior network technician for a mid-sized company who has been assigned the task of improving security for the IT infrastructure. He has been given a limited budget and must increase security without redesigning the network or replacing all internetworking security devices. He focuses on an approach that will identify a single vulnerability. What does he recommend? - ANSWER Weakest link
Which of the following is an authentication method that supports smart cards, biometrics, and credit cards, and is a fully scalable architecture? - ANSWER 802.1x
Which of the following is unlikely to support at-firewall authentication? - ANSWER Demilitarized zone (DMZ) firewall
What is the basic service of a reverse proxy? - ANSWER Hides the identity of a web server accessed by a client over the Internet
Which of the following is a type of fallback attack?
eavesdropping
social engineering
session hijacking
all of the above - ANSWER all of the above
Which of the following is a type of malware?
virus
Trojan
keylogger
all of the above - ANSWER all of the above
__________are malicious camouflage that function as invisibility shields for anything a hacker wants to hide on a computer. - ANSWER Rootkits
A ____________is an electronic land mine. Once a hacker embeds a logic bomb in a system, it remains dormant until a triggering event takes place. - ANSWER logic bomb
Trapdoor and backdoor malware are two terms for the same type of malware. - ANSWER True
Replay attacks are also known as playback attacks and is a retransmission pf the captured communication - ANSWER True
Buffer Overflow attacks can include e-mails to victims with falsified hyperlinks that point the script injection to a target site when the victim clicks on the e-mail's embedded links. - ANSWER False
Spoofing attack usually involves fooling or tricking the client into initiating the session with the hacker's computer instead of with the intended server. This form of attack is also called an interception attack, a proxy attack, or a monkey-in-the-middle attack. - ANSWER False
Isabella is a network administrator. She is researching virtual private network (VPN) options for company employees who work from home. The solution must provide encryption over public networks, including the Internet; not rely upon pathways the company owns; be reliable; and not be subject to eavesdropping. It must also be cost-effective. Which solution does she choose? - ANSWER Secured VPN
Consuela is a business analyst for her company. She is working from home and on a video conference with several other team members. Her video-conferencing client displays a message indicating that the quality of her connection is unstable. What is the most likely problem? - ANSWER VPNs over the Internet can easily suffer from latency, fragmentation, traffic congestion, and dropped packets.
Virtual private networks (VPNs) allow external entities to connect to and interact with a private network. What does identity verification require? - ANSWER Authentication
which of the following is a category of VPN?
Trusted VPN
Secured VPN
Hybrid VPN
all of the above - ANSWER all of the above
Diego is a network consultant. He is explaining the benefits of virtual private network (VPN) connections for remote clients to the owner of a company who wants to allow most staff to work remotely. He says that a VPN is both private and secure. What does he say is the rationale? - ANSWER Authentication provides privacy and encryption provides security
Carl is a network technician who has been assigned to select a dedicated hardware device to act as the company's termination point for the secured virtual private network (VPN) tunnel. He chooses a device that allows the firewall to filter traffic that is exiting the VPN and moving into the local area network (LAN). It is the choice that is best suited for controlled access into the demilitarized zone (DMZ). What is the solution that he recommends? - ANSWER Edge router
Mazie is a network engineer designing a virtual private network (VPN) architecture. The architecture must have the ability to establish and maintain a secure link between the company's main office and a branch office over the Internet, effectively creating a single distributed LAN. What solution does she recommend be applied? - ANSWER Site-to-site
Which of the following is a virtual private network (VPN) encryption encapsulation method best suited for linking individual computers together, even though it does not encrypt the original IP header? - ANSWER Transport
Which of the following establishes what a user can and cannot do relative to a virtual private network (VPN)? - ANSWER Authorization
A virtual private network (VPN) can operate securely over the Internet and still provide high levels of security through encryption. - ANSWER True
Chad is a network engineer. He is tasked with selecting a virtual private network (VPN) platform for his company. He chooses a solution that is inexpensive and runs on UNIX, although it is less scalable and less stable than other solutions. What has he chosen? - ANSWER Operating system-based VPN
Which of the following can perform authentication to provide integrity protection, although not for the outermost IP header? - ANSWER Encapsulating Security Payload (ESP)
Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? - ANSWER Authentication Header (AH)
Maria is a new network engineer for a company that was established more than 30 years ago. She is examining the IT infrastructure and discovers that the virtual private network (VPN) solution employs an older encryption protocol for backward compatibility. This protocol has largely been replaced, but it used to be popular in early VPN solutions. What is this protocol? - ANSWER Layer 2 Tunneling Protocol (L2TP)
Which of the following is a protocol that supports Advanced Encryption Standard (AES) with 128, 192, and 256 keys? - ANSWER Transport Layer Security (TLS)
Chris is a network engineer deploying a virtual private network (VPN) solution. He needs an implementation of Secure Sockets Layer/Transport Layer Security (SSL/TLS) that adds a layer of authentication to the access. What feature does he require? - ANSWER Bidirectional authentication
Which of the following statements is TRUE of an Internet Protocol Security (IPSec) virtual private network (VPN) when compared to a Secure Sockets Layer/Transport Layer Security (SSL/TLS) VPN? - ANSWER It requires client software.
Which of the following is a protocol that replaces the use of telnet and rlogin to log in to a shell on a remote host? - ANSWER Secure Shell (SSH)
Virtual private networks (VPNs) and which standard have historically suffered from conflicts when used together? - ANSWER Network address translation (NAT)
Which of the following is a core Internet Protocol Security (IPSec) protocol that provides encryption only, both encryption and integrity protection, or integrity protection only in all but the oldest IPSec implementations? - ANSWER Encapsulating Security Payload (ESP)
Oscar is deploying a virtual private network (VPN) solution for his company. The VPN needs to connect to remote servers by their Internet Protocol (IP) addresses rather than using network address translation (NAT). What type of VPN is Oscar deploying? - ANSWER Operating system (OS)
Tonya is an accountant working from home. She connects to her office each day over a virtual private network (VPN). The IT department for her company has deployed a VPN appliance to assist employees such as Tonya in performing their tasks remotely. What solution does Tonya use to access her files on the company's accounting server? - ANSWER Host-to-gateway
Remote Desktop Connection (RDC) is a built-in application that uses what proprietary protocol? - ANSWER Remote Desktop Protocol (RDP)
Alice is a network engineer who has been tasked with researching a virtual private network (VPN) tunneling protocol to be used by her company. It must be able to pass traffic through a network address translation (NAT) server and be compatible with a number of well-known proprietary and open source platforms. What solution does she select? - ANSWER Internet Key Exchange v2 (IKEv2)
Various virtual private network (VPN) encryption technologies offer access to almost any network application or resource. Which one offers additional features, such as easy connectivity from non-company-managed desktops, little or no desktop software maintenance, and user-customized web portals upon login? - ANSWER Secure Sockets Layer/Transport Layer Security (SSL/TLS)
Jacob is a remote employee. He clicks the Start menu button in Windows and selects an application to run. Most of the time, he is unaware that he is really accessing the application on a server at his company's main office several miles away. What solution is he using? - ANSWER RD RemoteApp
Bill's work-issued Windows laptop has been configured so he can remotely connect to his office from home without having to initiate a virtual private network (VPN) connection. What technology is he using? - ANSWER DirectAccess
Isabelle is a network engineer deploying an IT infrastructure in one of her company's new branch offices. Currently, she is designing a local subnetwork that contains and exposes the office's external services to a larger, untrusted network, specifically the Internet. What is this called? - ANSWER Demilitarized zone (DMZ)
James is a network engineer. He has been assigned the responsibility of designing a virtual private network (VPN) solution that will allow customers, suppliers, and business partners access to network resources without exposing the secure private LAN. The parties accessing these resources must use digital certificates issues by a certification authority (CA). What form of VPN is he setting up? - ANSWER Extranet
Which of the following BEST describes a technology with inherent security risks and that can reveal information a user did NOT intend to share? - ANSWER Peer-to-peer (P2P)
Nimi has deployed a new virtual private network (VPN) solution in her company's IT infrastructure. She is testing the connection to the server from a client. Which tool is the best choice for her to use? - ANSWER Ping
Carl is a student in a computer networking class who is studying virtual private network (VPN) implementations. He is learning the basics about VPNs. Which of the following statements does he find is TRUE? - ANSWER VPNs are both hardware and software solutions.
Arturo is a new network technician. He wants to use Remote Desktop Protocol (RDP) to connect to a server from his computer. The server is on the other side of the building. His computer is running Windows 10. Will he be able to make the connection? - ANSWER Yes, because the RDP protocol has clients that work on most common operating systems.
What is a virtual private network (VPN) protocol that requires public key infrastructure (PKI) support to obtain and use a certificate? - ANSWER Secure Sockets Layer/Transport Layer Security (SSL/TLS)
A customer premise equipment (CPE)-based virtual private network (VPN) is a VPN appliance. - ANSWER True
A virtual private network (VPN) replaces a firewall. - ANSWER False
Whereas a virtual private network (VPN) encrypts pieces of data, a firewall protects the internal network from outside threats. - ANSWER True
In a gateway-to-gateway virtual private network (VPN), the mobile user takes specific actions to connect to the VPN. - ANSWER False
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft. - ANSWER True
Remote Desktop Connection (RDC) is a built-in application that uses Remote Desktop Protocol (RDP). - ANSWER True
[Show More]