Computer Science > QUESTIONS & ANSWERS > Official CompTIA Security/ Exam SY0-601 Latest 2022 with complete solution (All)
Official CompTIA Security/ Exam SY0-601 Latest 2022 with complete solution
Document Content and Description Below
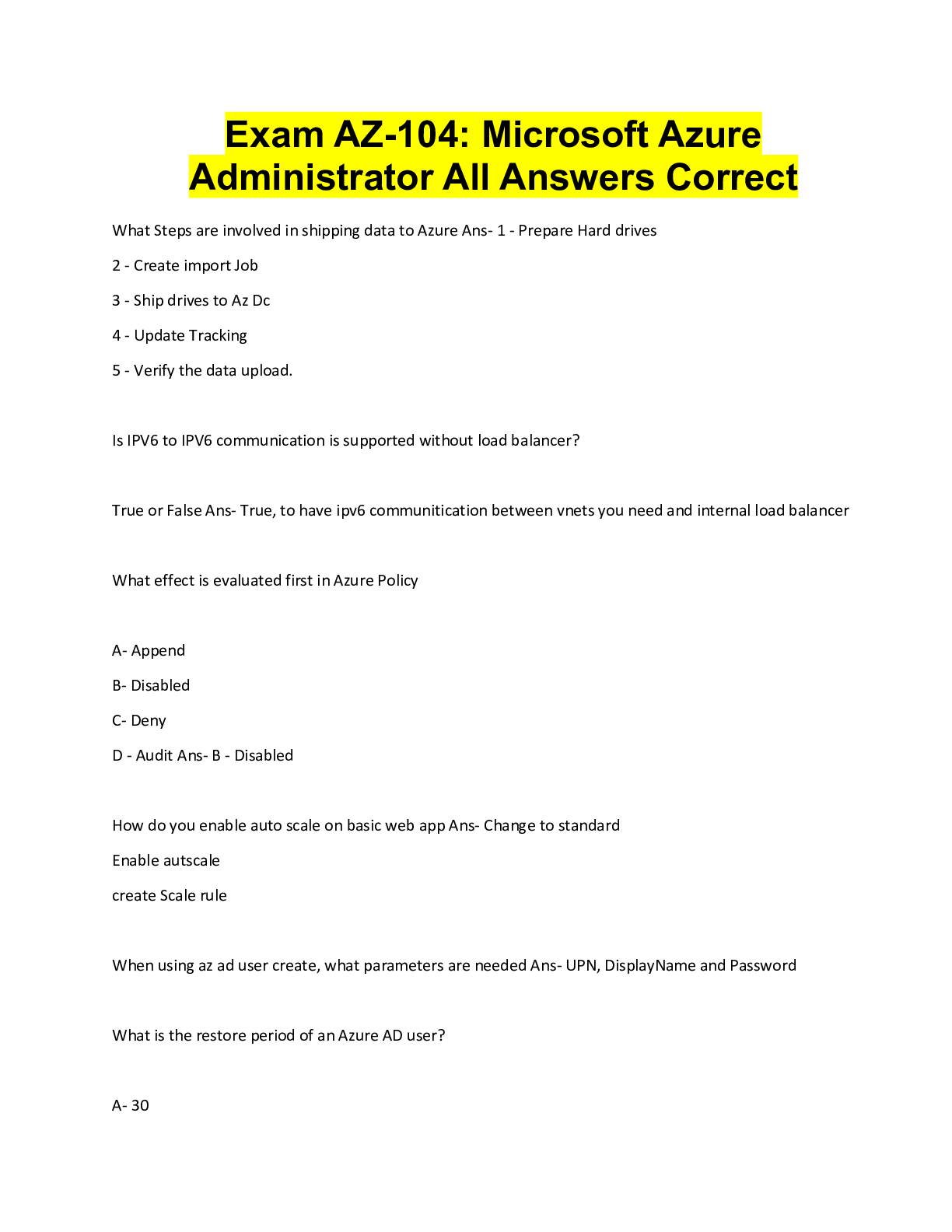
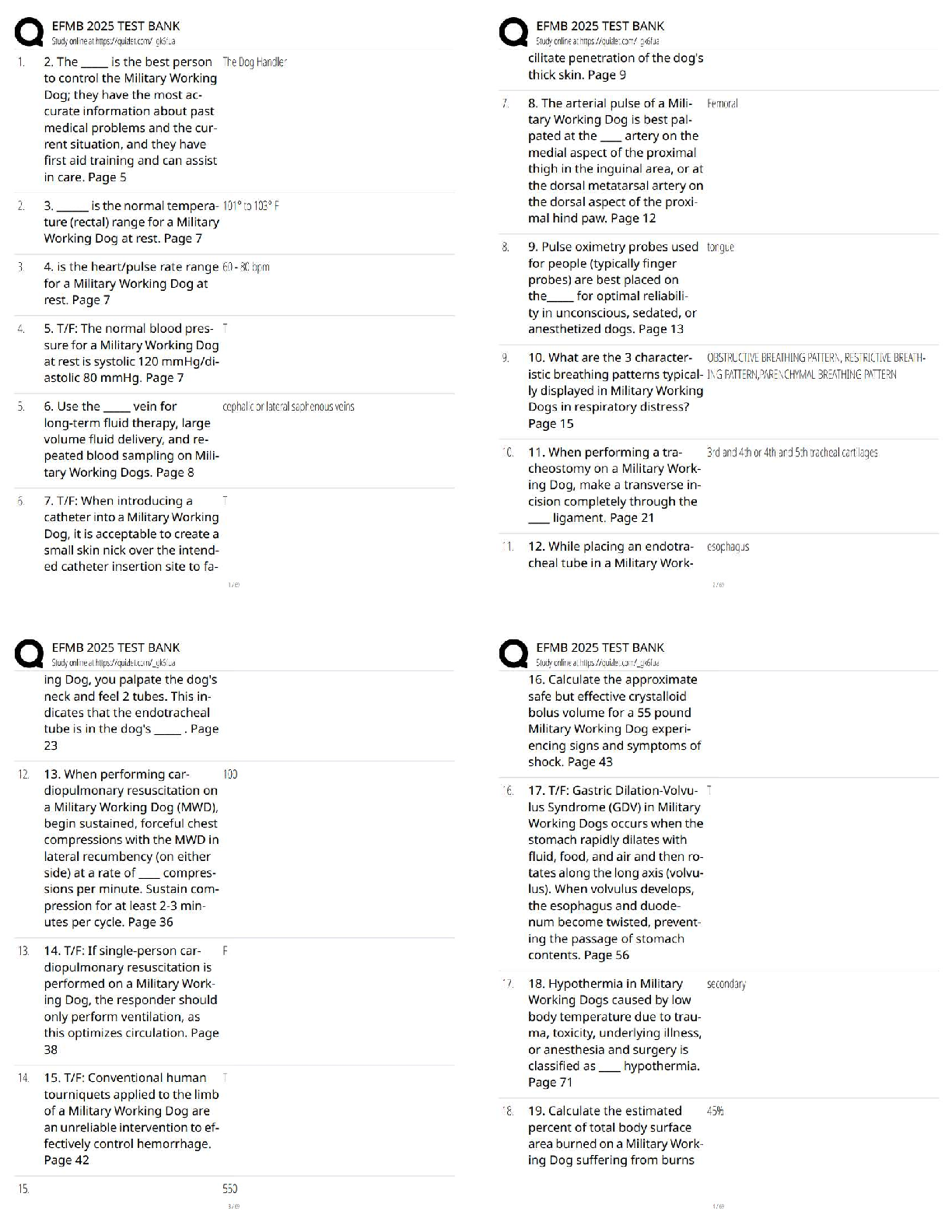
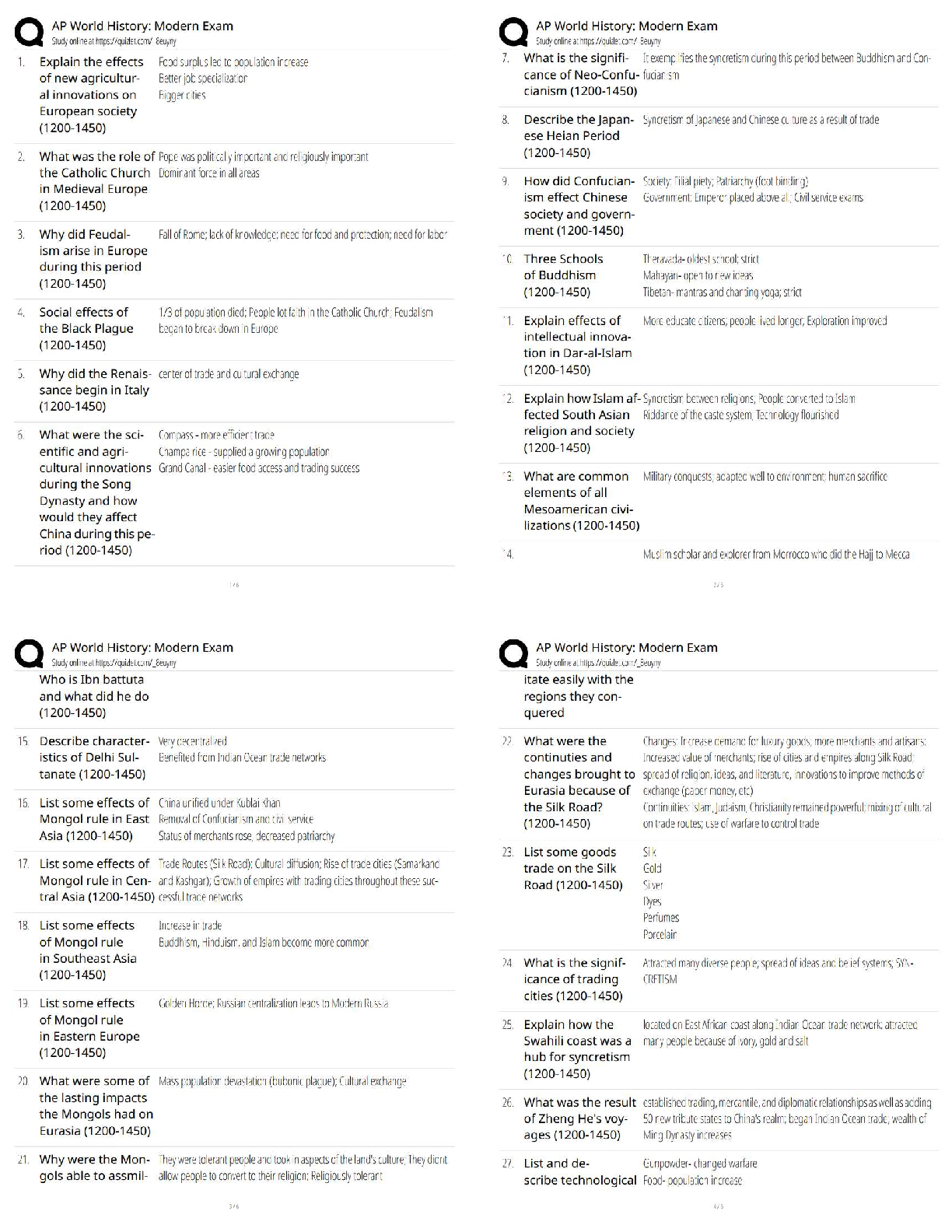
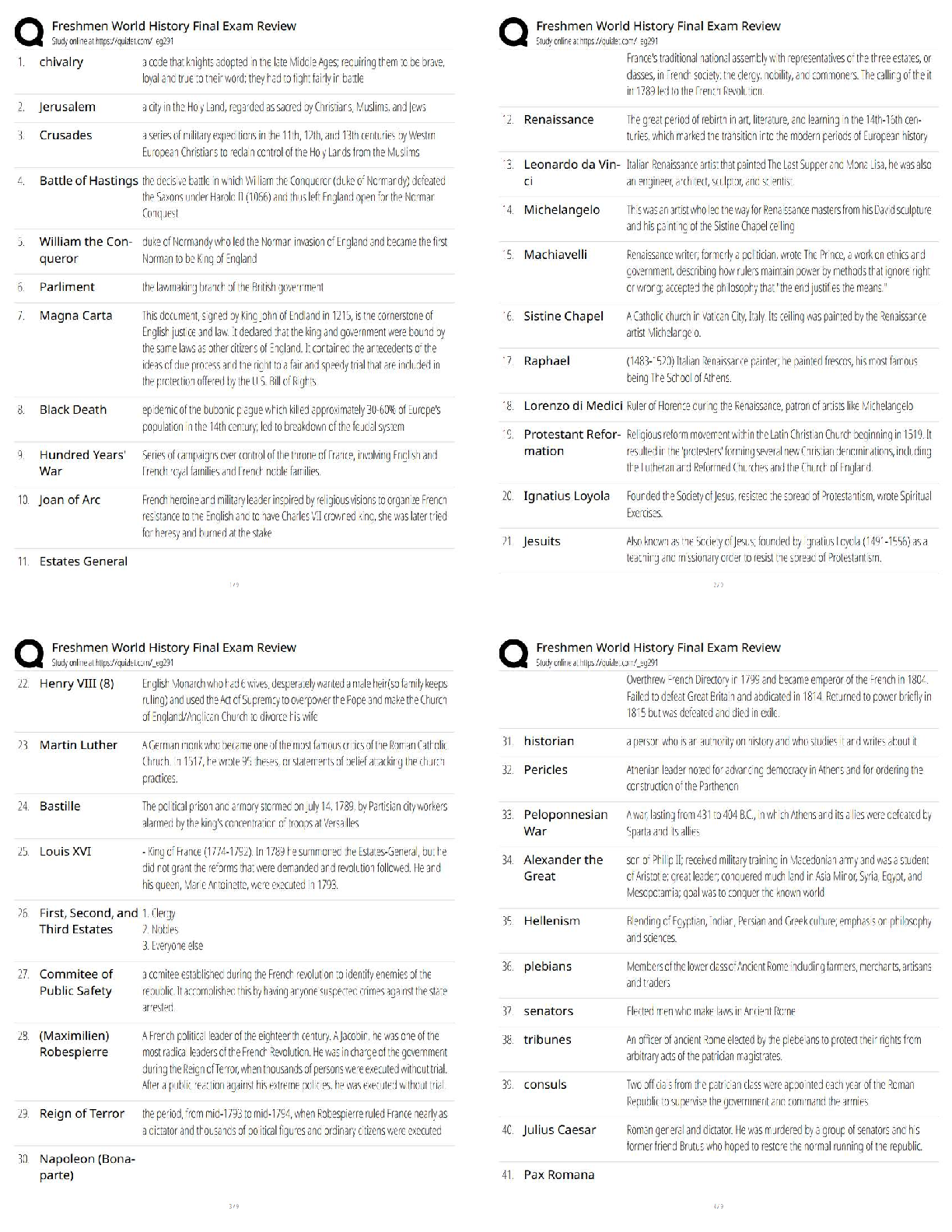
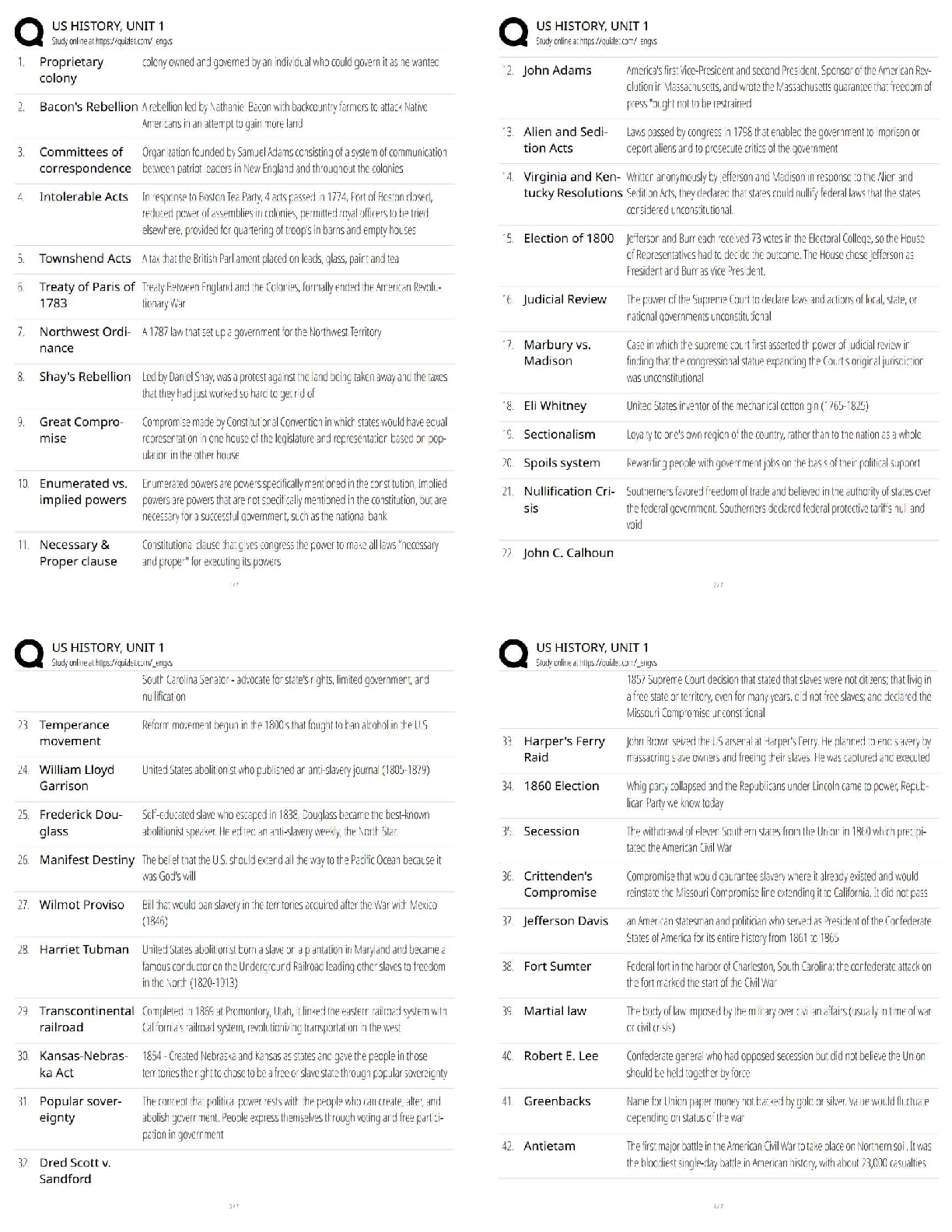
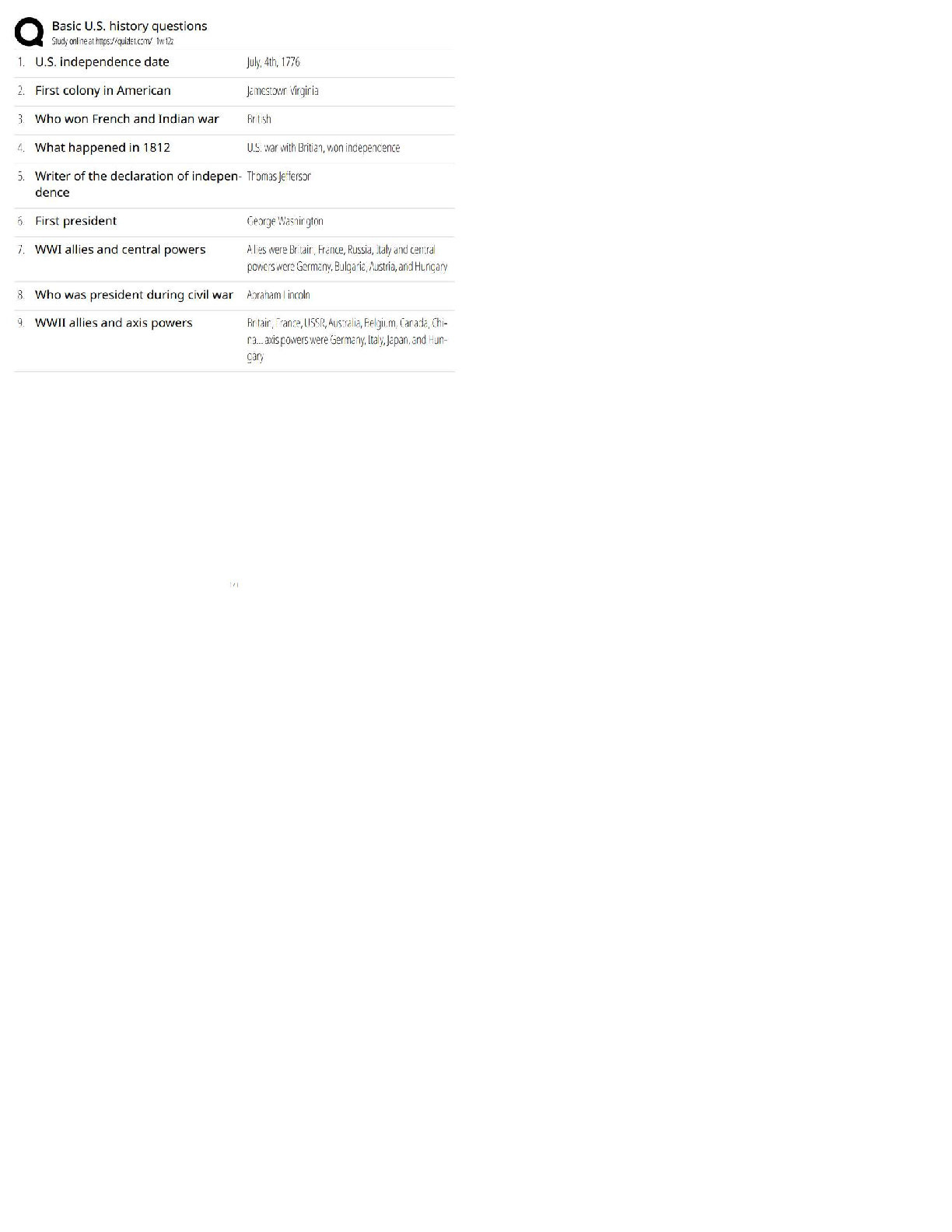
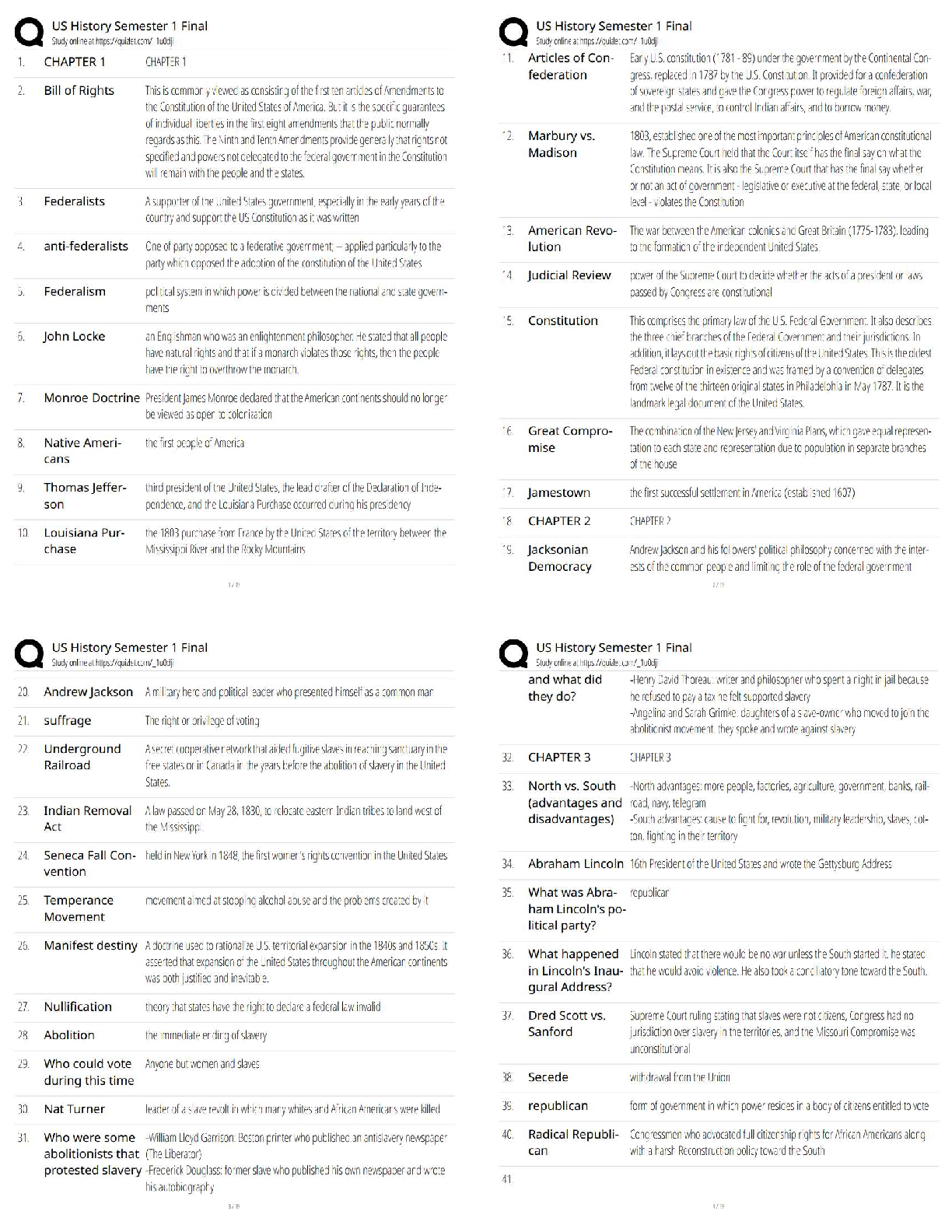
Official CompTIA Security/ Exam SY0-601 Latest 2022 with complete solution A large enterprise has moved all its data to the cloud behind strong authentication and encryption. A sales director recen ... tly had a laptop stolen, and later enterprise data was found to have been compromised from a local database. Which of the following was the MOST likely cause? A. Shadow IT B. Credential stuffing C. SQL injection D. Man-in-the-browser E. Bluejacking -Answer- A An enterprise has hired an outside security firm to conduct penetration testing on its network and applications. The firm has only been given the documentation available to the customers of the applications. Which of the following BEST represents the type of testing that will occur? A. Bug bounty B. Black-box C. Gray-box D. White-box -Answer- A A security analyst sees the following log output while reviewing web logs: [02/Feb2019:03:39:21 -0000] 23.35.212.99 12.59.34.88 - "GET /uri/input.action?query=%f.. %2f.. %2f..%2fetc%2fpasswrd HTTP/1.0" 80 200 200 [02/Feb2019:03:39:85 -0000] 23.35.212.99 12.59.34.88 - "GET /uri/input.action?query=/../../../etc/password HTTP/1.0" 80 200 200 Which of the following mitigation strategies would be BEST to prevent this attack from being successful? A. Secure cookies B. Input validation C. Code signing D. Stored procedures -Answer- B A technician needs to prevent data loss in a laboratory. The laboratory is not connected to any external networks. Which of the following methods would BEST prevent data? (Select TWO) A. VPN B. Drive encryption C. Network firewall D. File-level encryption E. USB blocker F. MFA -Answer- BE Company engineers regularly participate in a public Internet forum with other engineers throughout the industry. Which of the following tactics would an attacker MOST likely use in this scenario? A. Watering-hole attack B. Credential harvesting C. Hybrid warfare D. Pharming -Answer- A An organization just experienced a major cyberattack modem. The attack was well coordinated sophisticated and highly skilled. Which of the following targeted the organization? A. Shadow IT B. An insider threat C. A hacktivist D. An advanced persistent threat -Answer- D A company processes highly sensitive data and senior management wants to protect the sensitive data by utilizing classification labels. Which of the following access control schemes would be BEST for the company to implement? A. Discretionary B. Rule-based C. Role-based D. Mandatory -Answer- D An organization hired a consultant to assist with an active attack, and the consultant was able to identify the compromised accounts and computers. Which of the following is the consultant MOST likely to recommend to prepare for eradication? A. Quarantining the compromised accounts and computers, only providing them with network access B. Segmenting the compromised accounts and computers into a honeynet so as to not alert the attackers. C. Isolating the compromised accounts and computers, cutting off all network and internet access. D. Logging off and deleting the compromised accounts and computers to eliminate attacker access. -Answer- B A Chief Executive Officer's (CEO) personal information was stolen in a social engineering attack. Which of the following sources would reveal if the CEO's personal information is for sale? A. Automated information sharing B. Open-source intelligence C. The dark web D. Vulnerability databases -Answer- C The following is an administrative control that would be MOST effective to reduce the occurrence of malware execution? A. Security awareness training B. Frequency of NIDS updates C. Change control procedures D. EDR reporting cycle -Answer- A An attacker is attempting to exploit users by creating a fake website with the URL users. Which of the following social-engineering attacks does this describe? A. Information elicitation B. Typo squatting C. Impersonation D. Watering-hole attack -Answer- D The manager who is responsible for a data set has asked a security engineer to apply encryption to the data on a hard disk. The security engineer is an example of a: A. data controller. B. data owner C. data custodian. D. data processor -Answer- D A security administrator needs to create a RAIS configuration that is focused on high read speeds and fault tolerance. It is unlikely that multiple drivers will fail simultaneously. Which of the following RAID configurations should the administration use? A. RAID 0 B. RAID 1 C. RAID 5 D. RAID 10 -Answer- D A company recently set up an e-commerce portal to sell its product online. The company wants to start accepting credit cards for payment, which requires compliance with a security standard. Which of the following standards must the company comply with before accepting credit cards on its e-commerce platform? A. PCI DSS B. ISO 22301 C. ISO 27001 D. NIST CSF -Answer- A [Show More]
Last updated: 3 years ago
Preview 1 out of 56 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

CompTIA Security+ SY0-601 Practice, Study Guide, Exam Review and Exam Questions with Answers Combined Bundle Solution
COMPTIA SECURITY+ SY0-601 BEST EXAM STUDY GUIDE SOLUTION 2022/2023 BEST Security+ SY0-601 EXAM STUDY with Complete Solutions SY0-501 - CompTIA Security+ Certification Exam Questions with Answers...
By Excel 3 years ago
$14
12
Reviews( 0 )
$11.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 26, 2022
Number of pages
56
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 26, 2022
Downloads
0
Views
210