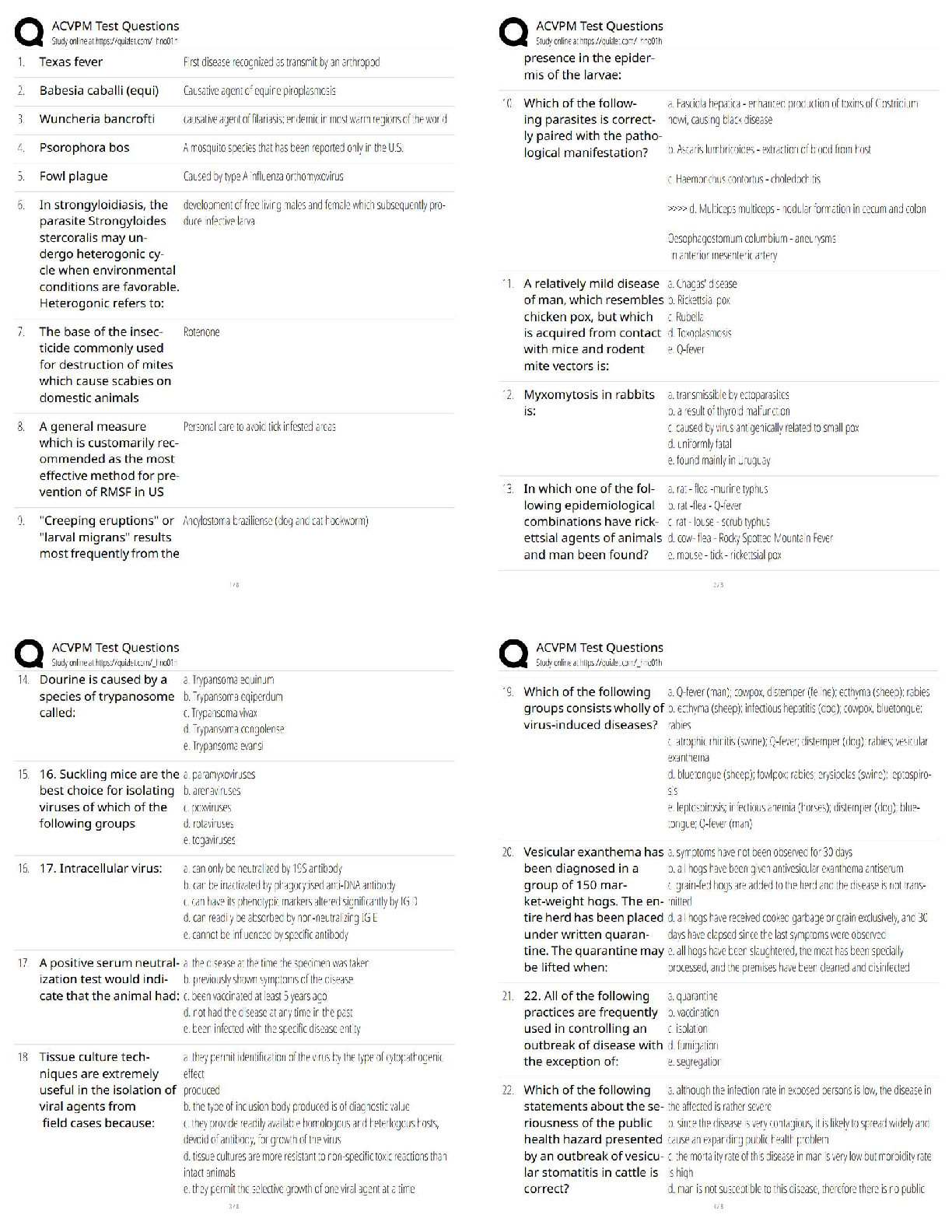
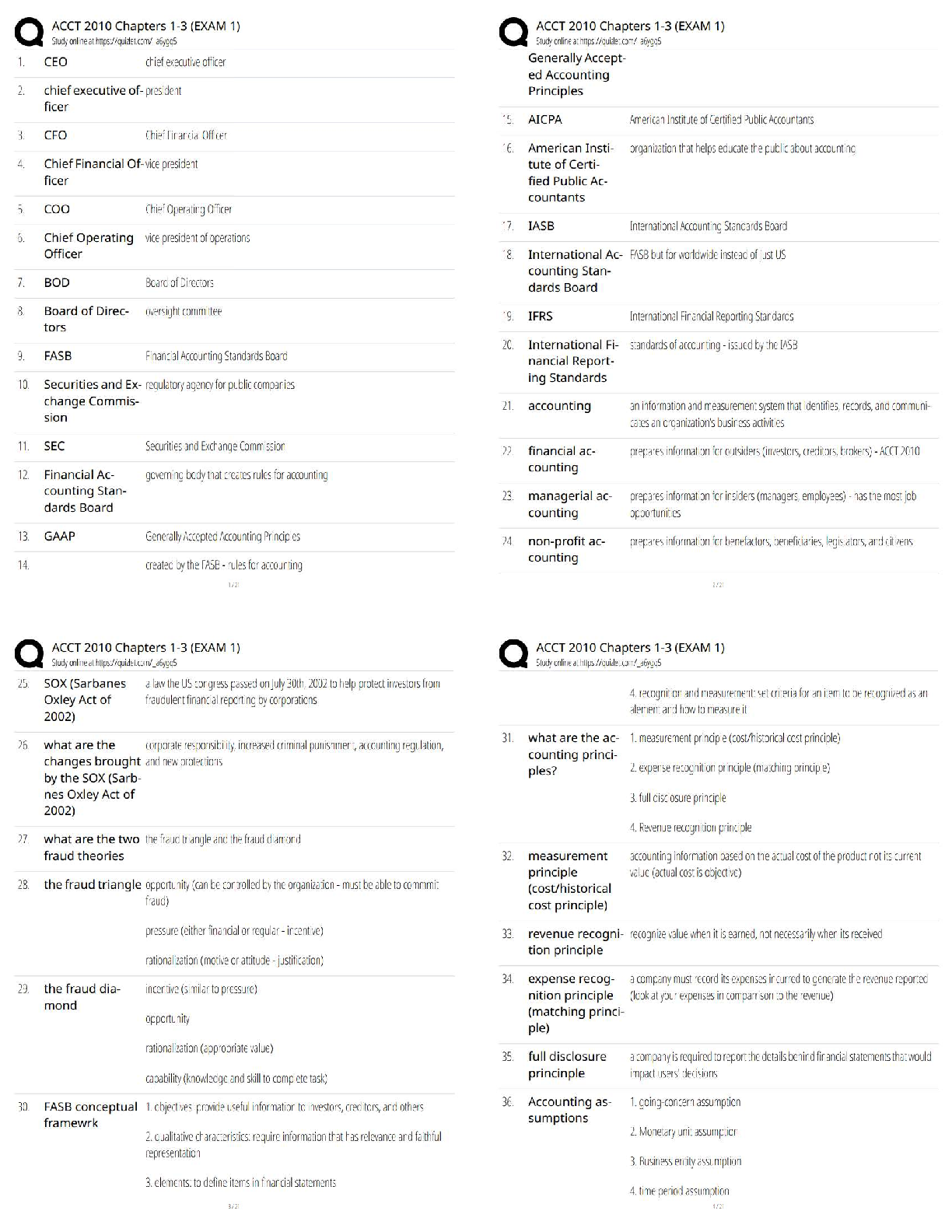
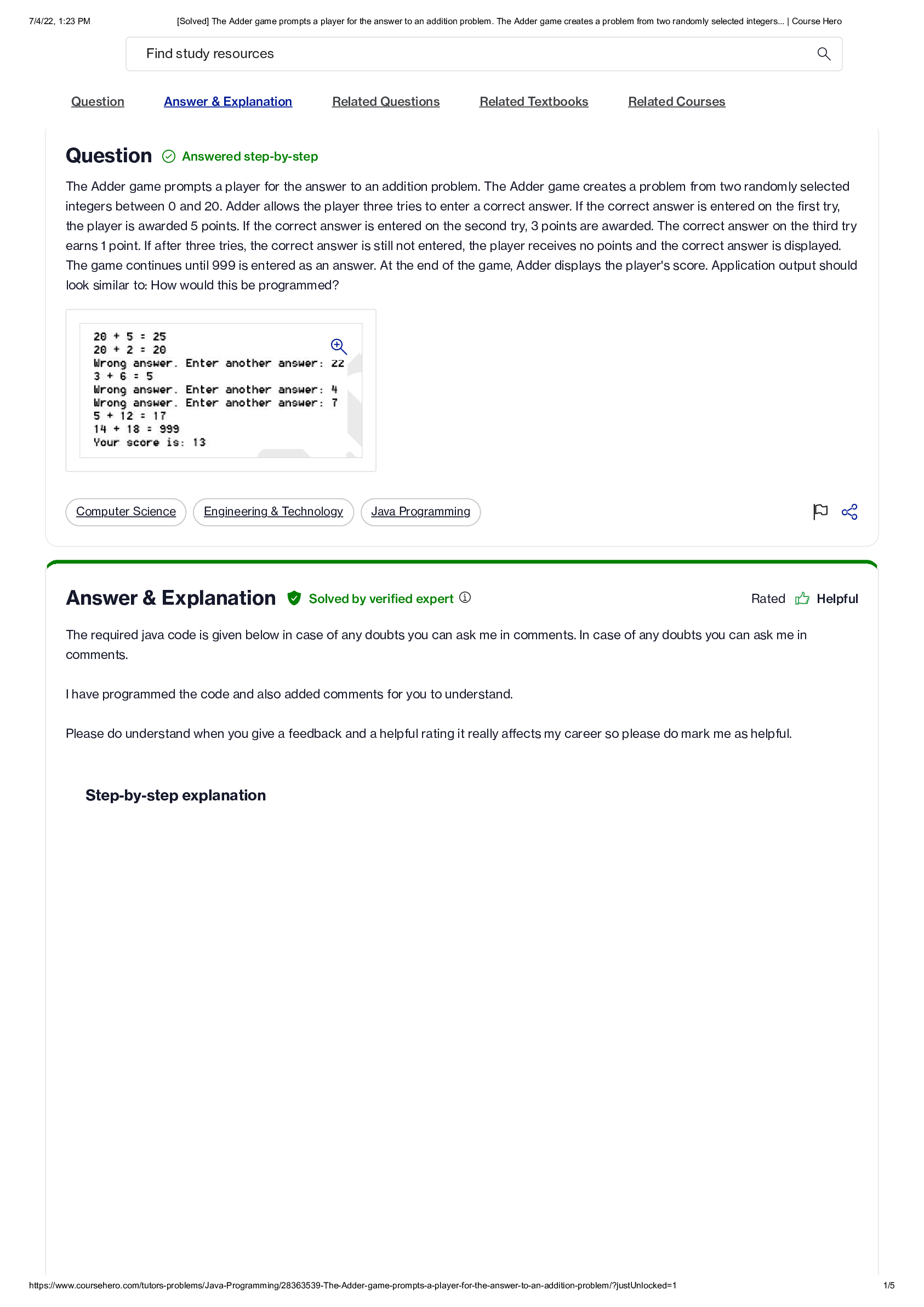
PAEA Surgery Study Guide | PAEA Surgery Blueprint Gastrointestinal/Nutritional ; ABDOMINAL PAIN.
$ 14.5

eBook Spatial Futures Difference and the Post-Anthropocene 1st Edition By LaToya E. Eaves , Heidi J. Nast , Alex G. Papadopoulos
$ 20

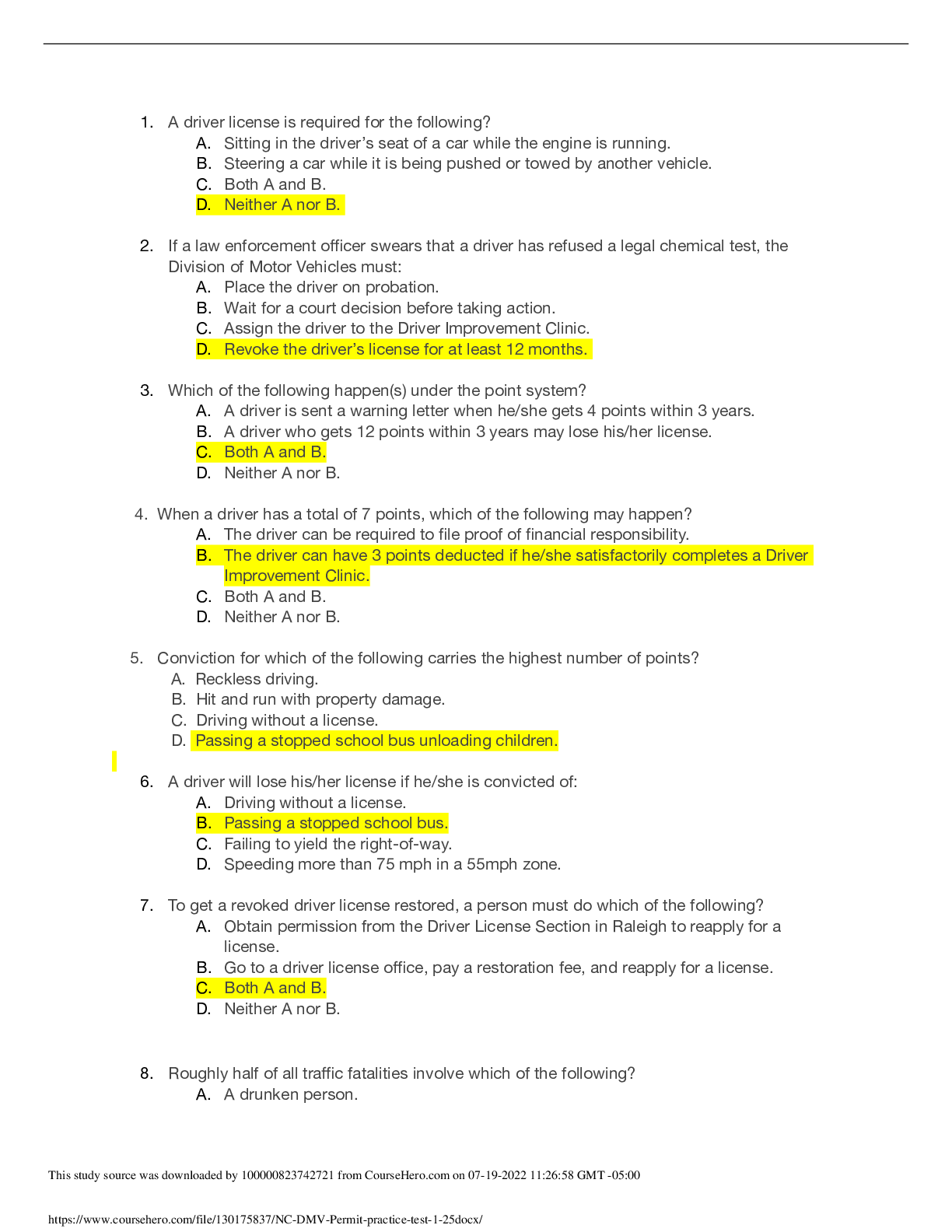
DMV Learners Permit Test 100% Correct
$ 11

Grand Canyon University_PSY 520 Topic 6 Exercise:Chapter 16, 17, 18 COMPLETE SOLUTION
$ 13

WGU BioChem OA Review with complete solution (Graded A)
$ 10
.png)
AQA A-level RELIGIOUS STUDIES 7062/2B Paper 2B Study of Religion and Dialogues: Christianity Mark scheme June 2021 Version: 1.0 Final
$ 10

OCR AS Level Religious Studies H173/04 Developments in Islamic thought QUESTION PAPER Tuesday 14 June 2022 – Morning
$ 9
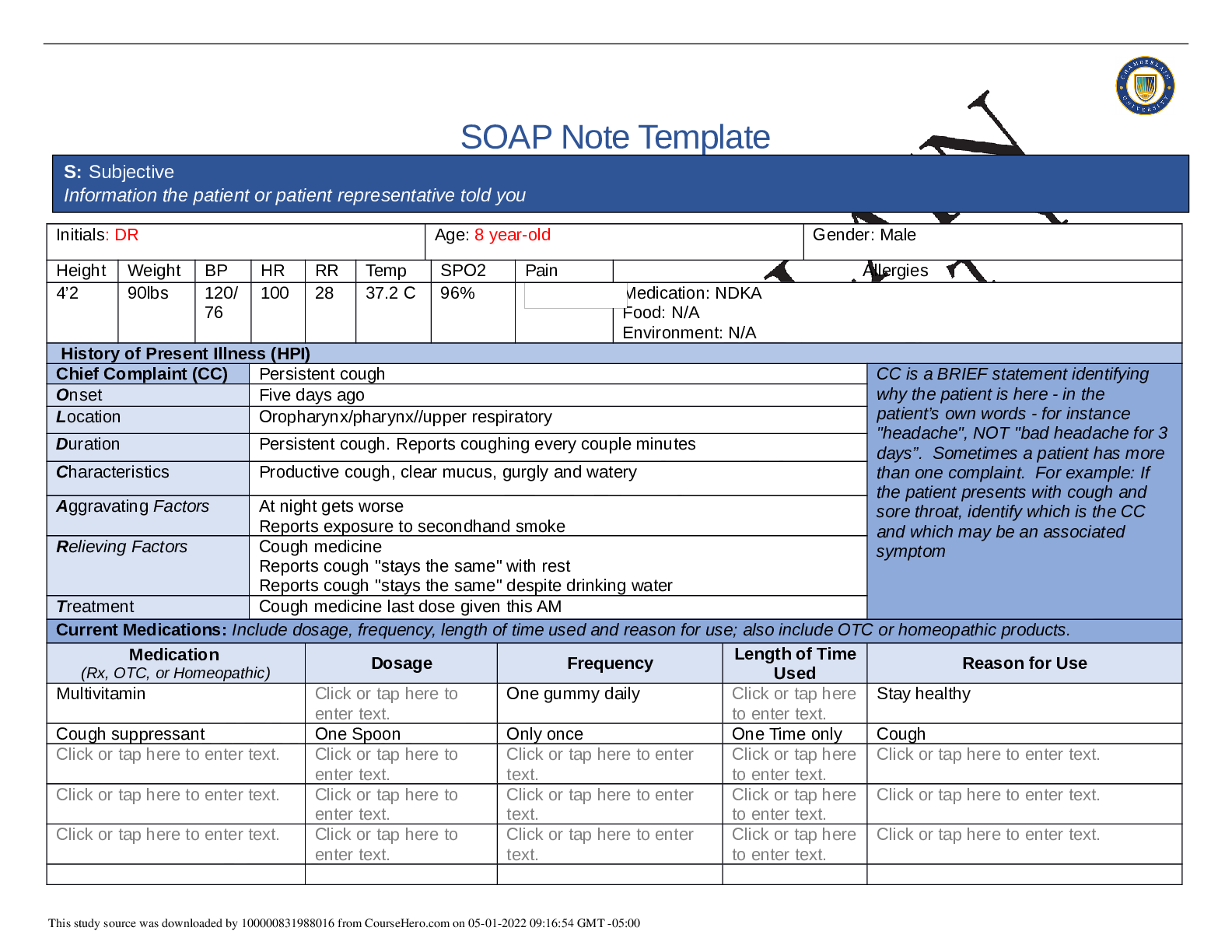
NR-509 Week 7 Comprehensive Health History SOAP Note
$ 9
C170 - Performance Assessment
$ 10

BIOD 151 PORTAGE LEARNING ESSENTIAL HUMAN A & P MODULE 3 LATEST REVIEW EXAM Q & A 2024
$ 14

Nancy Caroline’s Emergency Care in the Streets 6th Edition - Chapter 5 Ethical Issues
$ 8

PRACTICE QUESTIONS FOR THE MIDTERM EXAM | Download for quality grades
$ 25

VSIM RED YODER part 1 Guided Reflection 6.16( Best Solution) Score A+
$ 15.5

A Solution Manual and Notes for: The Elements of Statistical Learning by Jerome Friedman, Trevor Hastie, and Robert Tibshirani
$ 25

ISYE 6501x Midterm Quiz 1 - GT Students ( with Correct top Questions And Answers)
$ 11.5

TCOLE State exam review with Correct Answers
$ 11

Module 09 Assignment Develop a Presentation about a Medication
$ 3.5

eBook [PDF] Traffic and Highway Engineering 5th Edition By Nicholas Garber, Lester Hoel
$ 30

MARK KLIMEK NCLEX REVIEW 2 STUDY GUIDE A+ Grade
$ 13
CFE-103-FINAL-EXAM (1) - Saint Louis University, Baguio City Main Campus - Bonifacio St., Baguio City CFED 104
$ 6

Nancy Caroline’s Emergency Care in the Streets 6th Edition - Chapter 3 Illness and Injury Prevention
$ 8

AP STATS 2022 EXAM DEFINITIONS/CONCEPTS; WITH EXPLANATIONS)
$ 13.5

Portage Learning MATH 110 Introduction to Statistics _ Combination of Exam Answers - Complete Solutions (Graded A)
$ 17

Questions and Answers > University of British Columbia - EOSC 114; Volcano Homework.