Business > EXAM > Vulnerability Response Exam 118 Questions with Verified Answers,100% CORRECT (All)
Vulnerability Response Exam 118 Questions with Verified Answers,100% CORRECT
Document Content and Description Below
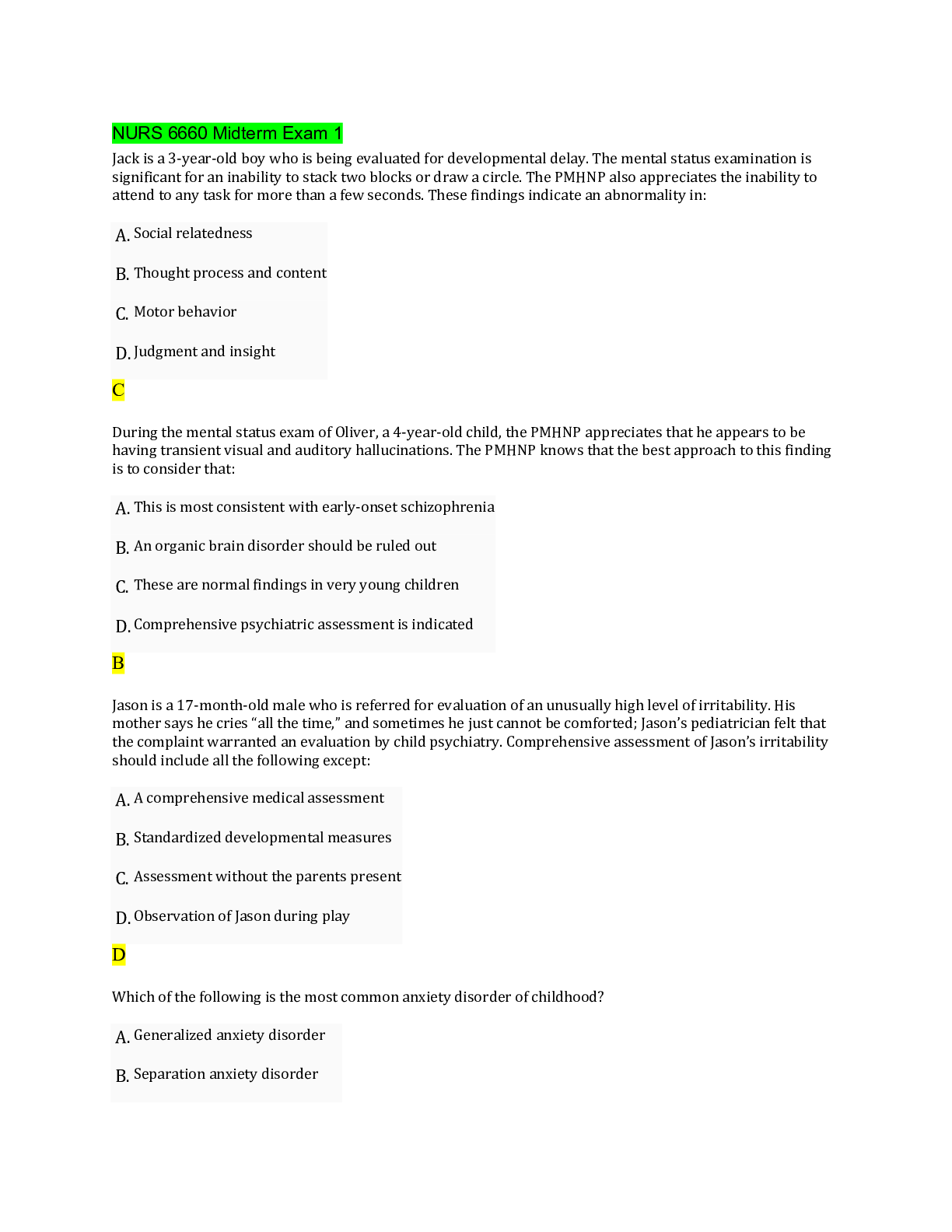
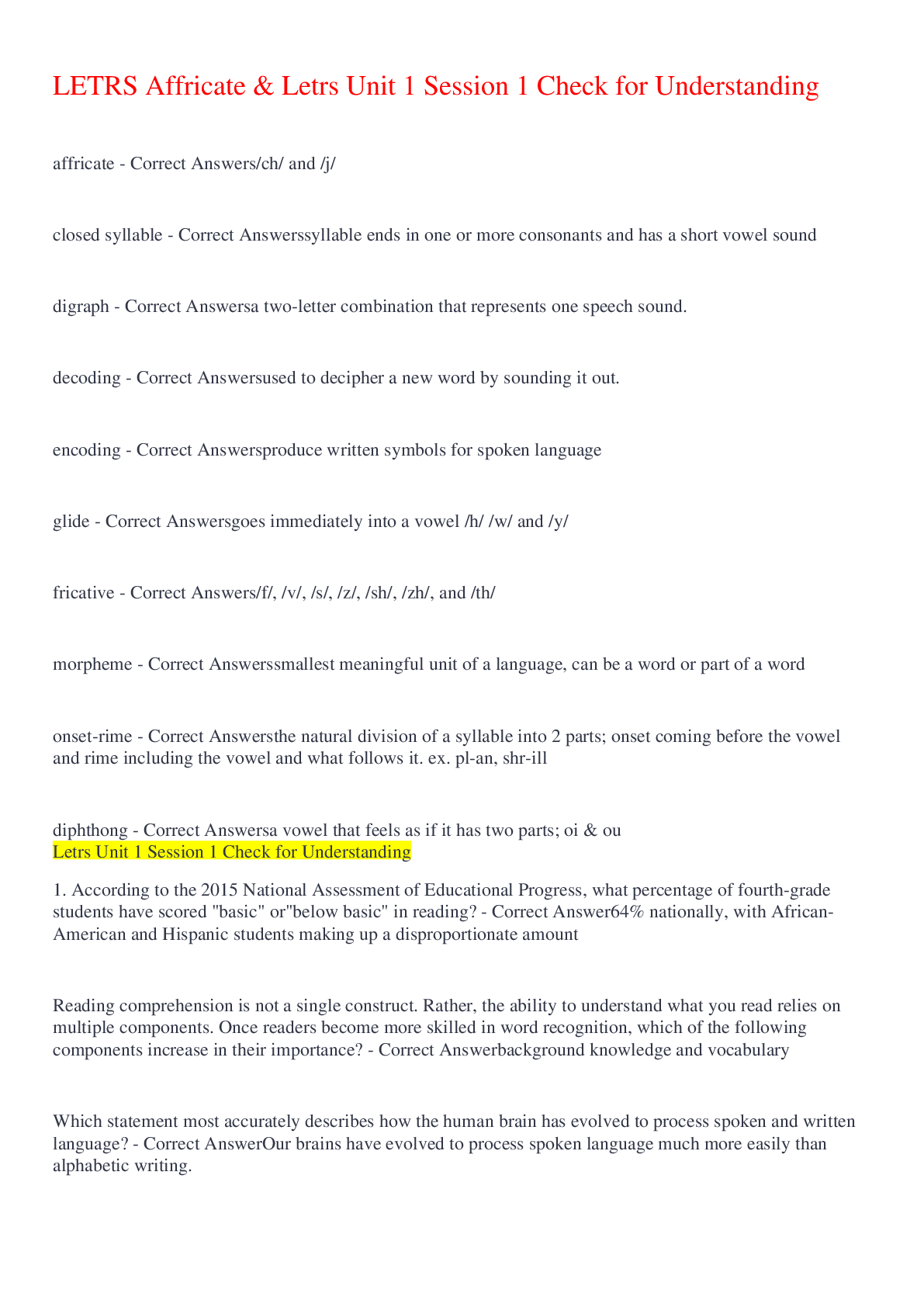
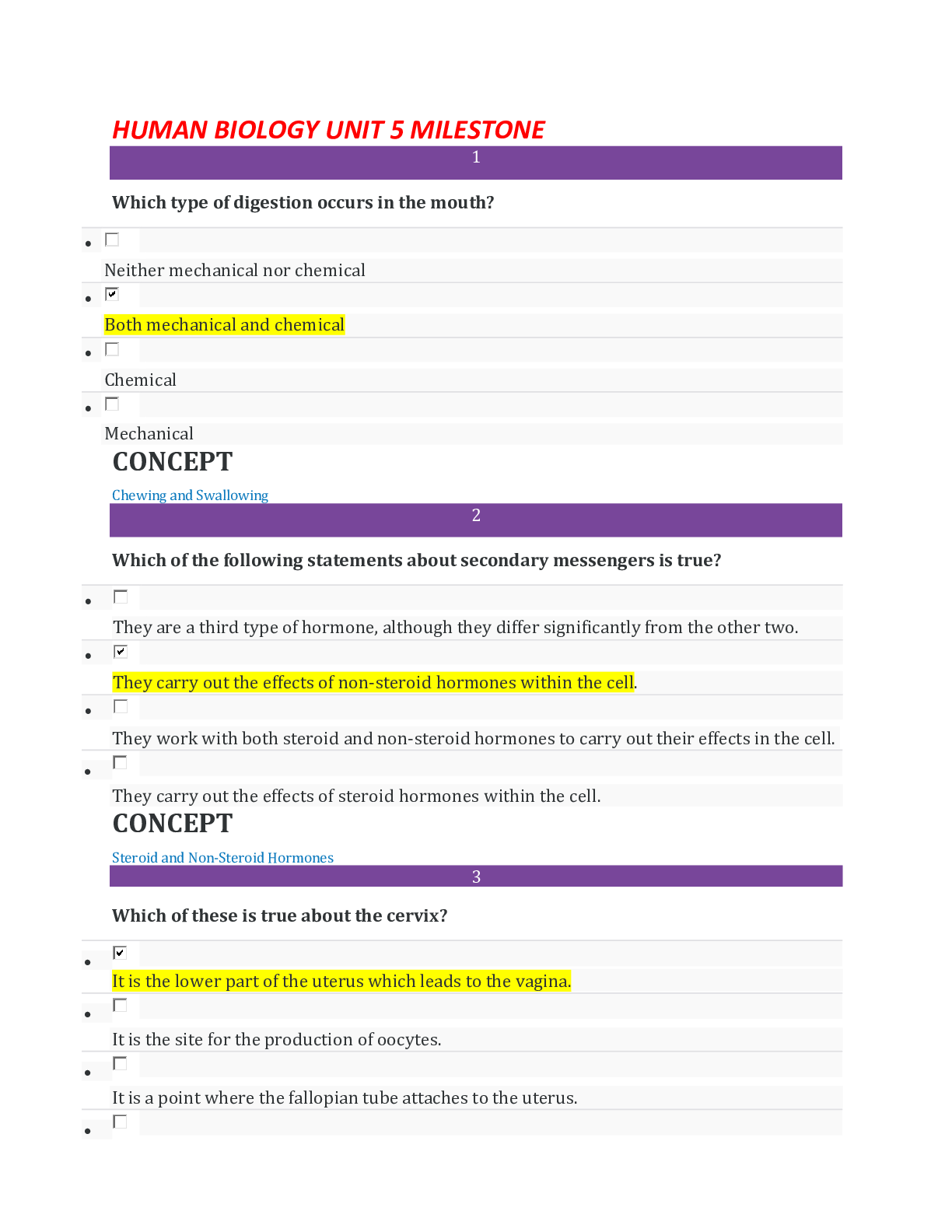
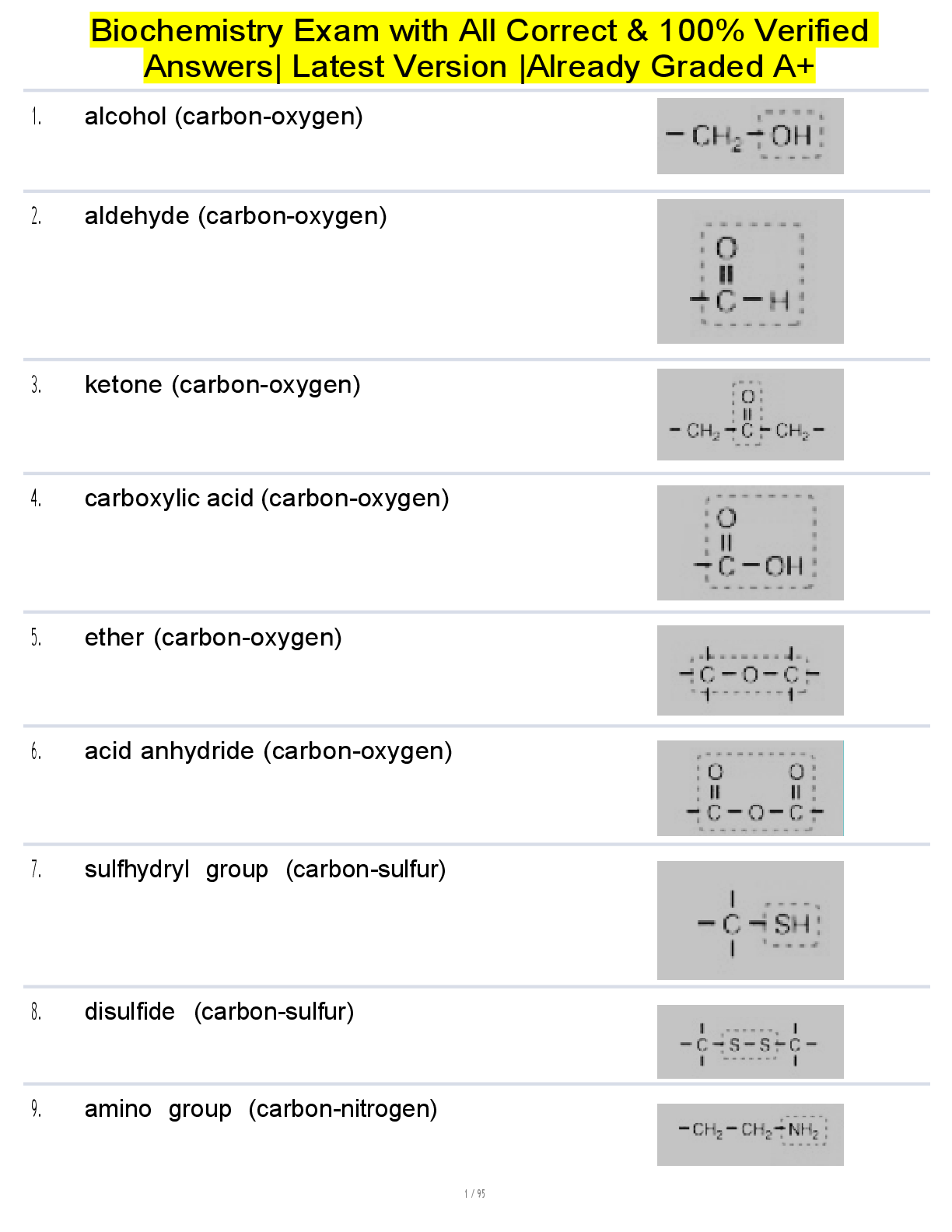
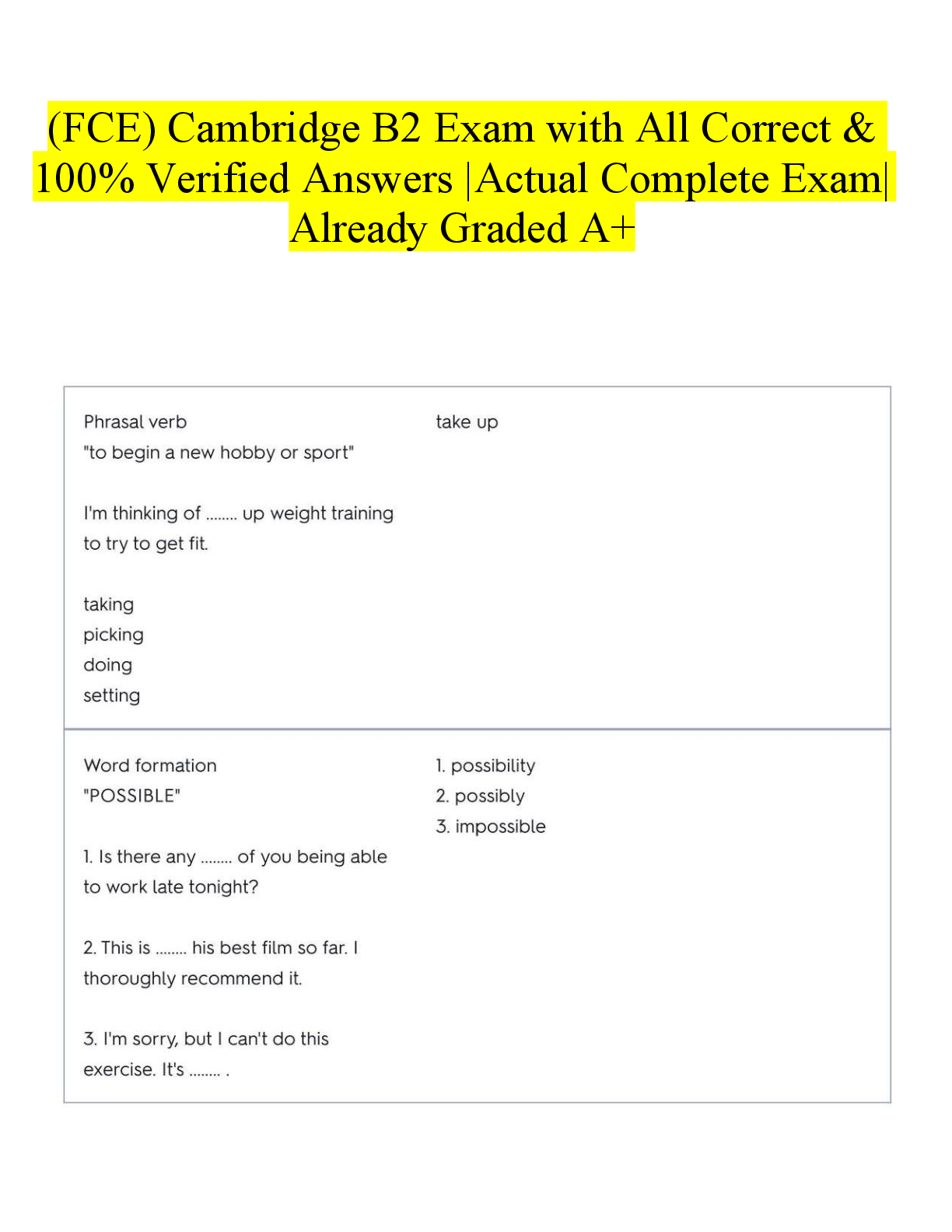
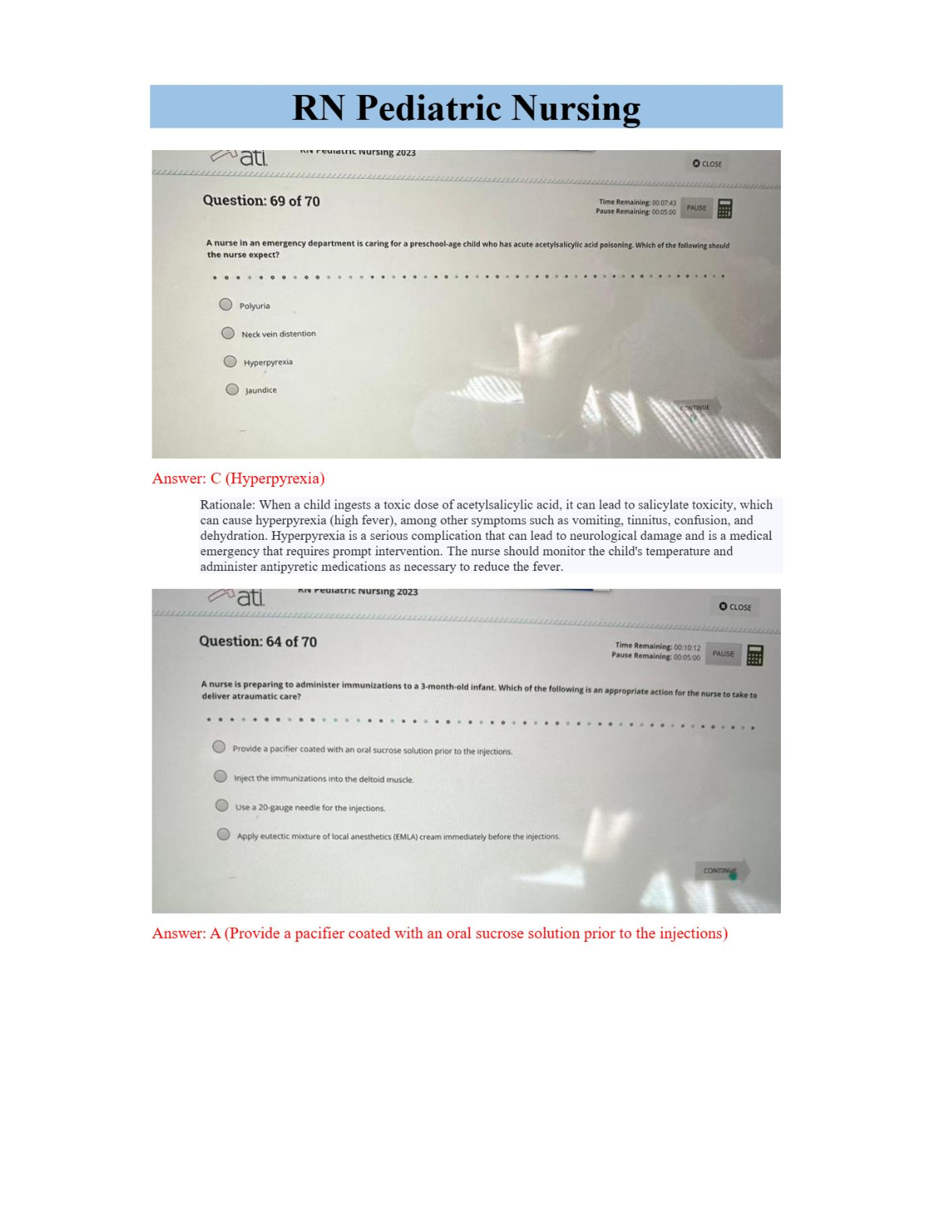
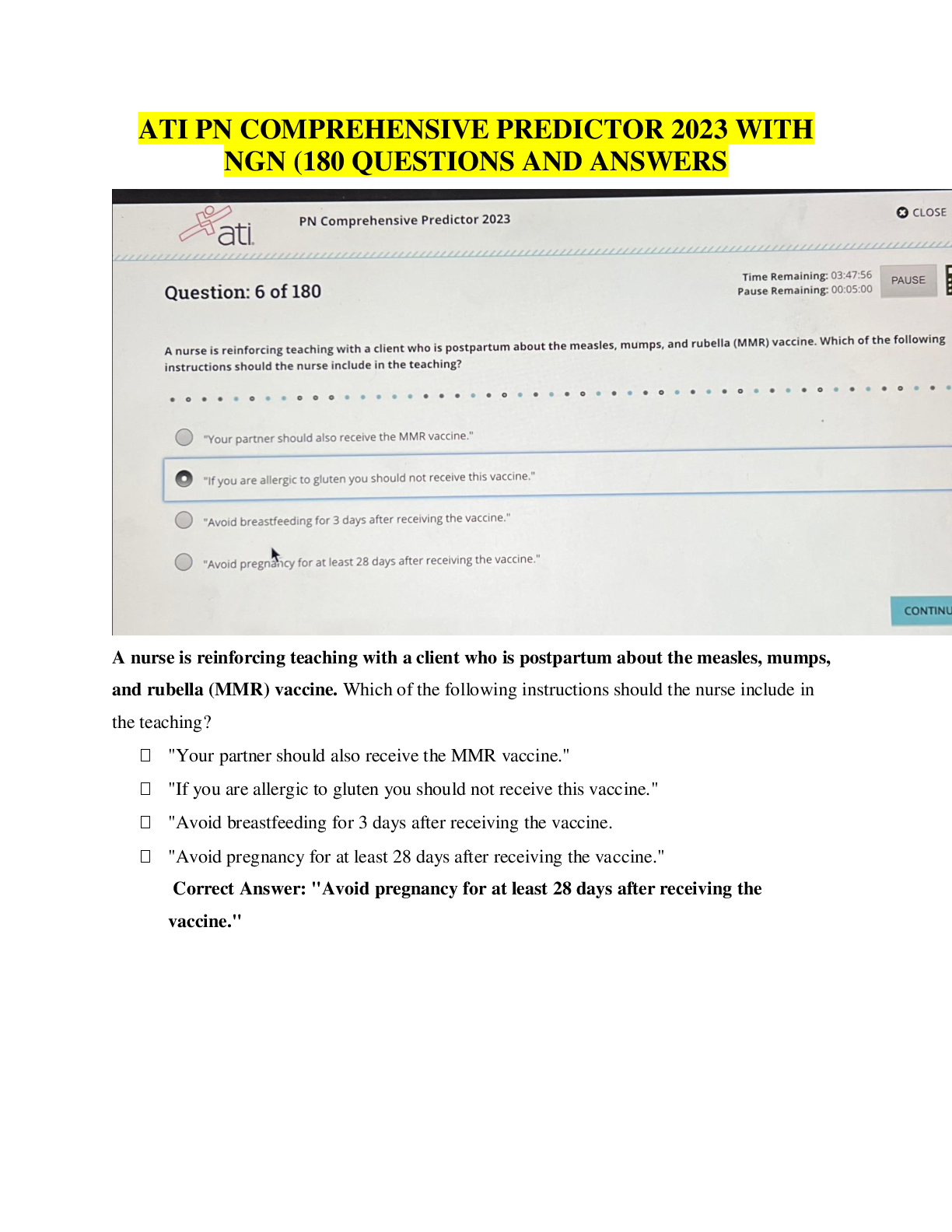
Vulnerability Response Exam 118 Questions with Verified Answers The Vulnerability Response tasks provides which roles by default? - CORRECT ANSWER a) sn_vul.admin b) sn_vul.vulnerability_read c ... ) sn_vul.vulnerability_write d) sn_vul.vr_import_admin Common Vulnerability and Exposure — a dictionary of publicly known information-security vulnerabilities and exposures. - CORRECT ANSWER CVE Common Vulnerability Scoring System — an open framework for communicating the characteristics and severity of software vulnerabilities. - CORRECT ANSWER CVSS Common Weakness Enumeration — a list of software vulnerabilities - CORRECT ANSWER CWE Calculators used to prioritize and categorize vulnerabilities based on user-defined criteria. - CORRECT ANSWER Vulnerability calculators and calculator groups Vulnerability groups and group rules - CORRECT ANSWER Used to group vulnerable items based on vulnerability, vulnerable item conditions, or filter group. Configure Vulnerability integrations - CORRECT ANSWER A process that pulls report data from a thirdparty system, generally to retrieve vulnerability data. Vulnerabilities - CORRECT ANSWER Records of potentially vulnerable software downloaded from the National Institute of Standards and Technology (NIST) NVD or third party integrations. Vulnerable items - CORRECT ANSWER Pairings of vulnerable entries, downloaded from the NIST NVD or third-party integrations, and potentially vulnerable configuration items and software in your company network. When the Qualys Cloud Platform integration is installed, which the following rules are available - CORRECT ANSWER sn_vul_qualys.admin — can read, write, and delete records sn_vul_qualys.user — can read and write records sn_vul_qualys.read — can read records What role is required to define a VR email template? - CORRECT ANSWER sn_vul.vulnerability_admin How can you manually create vulnerability groups? - CORRECT ANSWER Manually, using one of three options, to add vulnerable items to the group. 1) Add vulnerable items to the group by hand. 2) Use a Condition filter that automatically adds vulnerable items to the vulnerability group. 3) Use a Filter group that automatically adds vulnerable items to the vulnerability group. Note: Manually added vulnerable items are not automatically removed from vulnerability groups by vulnerability group rules or group conditions. T/F - vulnerable item refresh automation applies only to groups created using the Condition filter, Filter group, or vulnerability group rules. If the VIs are added manually, automation does not apply. - CORRECT ANSWER True T/F - If you want vulnerable items to continue being added to the group, regardless of state, disable the Set auto refresh vulnerable items business rule. - CORRECT ANSWER True T/F - Manually created Vulnerability Groups using Condition or Filter Group filter types are refreshed once an hour. - CORRECT ANSWER True T/F - Manually created Vulnerability Groups using Condition or Filter Group filter types are refreshed once an hour. - CORRECT ANSWER True Add users to the Vulnerability Response group - CORRECT ANSWER When the Request Review feature is used to ignore or close a vulnerable item without requiring a scan, the Vulnerability Response group is notified to approve or reject the request. You can assign the appropriate users. Create a Vulnerability Response group - CORRECT ANSWER Creating a vulnerability group manually is done when you want to group vulnerable items by something other than by the Vulnerability Group Rules criteria. For example, you can create groups for a particular single manager, or for active, new exploits, such as ransomware, that include different vulnerabilities. Create vulnerability group rules - CORRECT ANSWER You can create rules to automatically group vulnerable items based on filter conditions. How to Add users to the Vulnerability Response group ? - CORRECT ANSWER Before you begin - Role required: admin Procedure - Navigate to User Administration > Groups. Open the Vulnerability Response group. Click the Group Members related list and add the appropriate members to the group. How to Create a Vulnerability Response group - CORRECT ANSWER Before you begin Role required: sn_vuln.admin If the system property (sn_vul.autocreate_vul_centric_group) is set to true, each vulnerability entry with a vulnerable item creates a group associated with it. If it is set to false, you create groups manually as follows. Procedure Navigate to Vulnerability > Vulnerabilities > Vulnerability Groups. Click New. Fill in the fields on the form, as appropriate. Groups that come with VR plugin - CORRECT ANSWER Vulnerability Response Which Configuration Compliance administrator role is able to modify application property and configuration. - CORRECT ANSWER sn_vul.admin Security Incident Vulnerability Read role can see the vulnerable module section and vulnerable softwares - CORRECT ANSWER sn_vul.vulnerability_read Vulnerability administrator is able to modify application property and configuration - CORRECT ANSWER sn_vul.admin VR System import administrator is able to run scheduled job - CORRECT ANSWER sn_vul.vr_import_admin Security Incident Vulnerability Write role can see and edit the vulnerable module section and vulnerable softwares - CORRECT ANSWER sn_vul.vulnerability_write Which roles come with Qualys integration - CORRECT ANSWER - sn_vul_qualys.admin - sn_vul_qualys.read - sn_vul_qualys.user Which role comes with Configuration Compliance - CORRECT ANSWER - sn_vul.admin - sn_vul.read - sn_vul.write What is Security Operations? - CORRECT ANSWER • Collective processes, products and people that provide security to business data and its safe usage, including network enclaves, applications, websites, databases, data centers etc • Not just preventative can also be: - detective - signs that security outbreak has occurred - corrective - procedures to invoke post breach to limit damage ServiceNow Secops Process - CORRECT ANSWER 1. Integrate your security process 2. Auto prioritize Security incidents 3. Utilize threat intelligence 4. Determine response actions 5. Remediate threats fast 6. Review post incidents reports Average takes 200 days to identify and 70 days to contain ServiceNow Secops Suite - CORRECT ANSWER - Security Incident response - Vulnerability Response - Threat intelligence - Trusted Security Circles - Workflow - Automation & Orchestration - Deep IT Integration - Integrations with other tools provided like o Palo Alto Networks Wildfire and Autofocus o Tanium - Orchestration packs provided- Automate many of the daily manual processes that security teams perform What is Security Response? - CORRECT ANSWER - Integrates with organizations existing security tools like firewalls, endpoint security products or Security Information and Event Management tools to collect and prioritize security incidents - Allows fast analysis and quick decision making concerning the appropriate response What is Vulnerability Response? - CORRECT ANSWER - Represents the proactive approach by reducing attacks through understanding and addressing the most vulnerable components in the infrastructure What is Threat Intelligence? - CORRECT ANSWER - Relevant threat intelligence data can be imported into SIR and VR applications - Provides details and information security analyst can make decisions on, reduces their time and need to do manual task - STIX and TAXII feeds are supported but can work with open source feeds as well What are Trusted Security Circles? - CORRECT ANSWER - Identifies people with whom Threat Intelligence can be shared in a secure and scalable way. - Allows security analyst to tell if it is apart of a much bigger attack - Can serve as an early warning of attacks targeted at common groups - Shared threat intelligence with industry peers - Send anonymous query to other users and receive a sightings count Configuration Item - CORRECT ANSWER Things we use to deliver a service Vulnerability - CORRECT ANSWER Any weakness that allows exploitation or an attacker to further reduce security posture Vulnerability Response - CORRECT ANSWER The process of dealing identifying, classifying and prioritizing vulnerabilities. Then deciding on response VR Single system record - CORRECT ANSWER - Allows related info to be showed about that specific occurrence - Vulnerability Item extends task meaning record indicates work to be done - Baselines integration include Change, Problem, and security incident -ACLS include for only people with certain roles (sn_vul scope) Vulnerability Response Focus - CORRECT ANSWER -Proactive -Grown from more mature secops/it team -Primary focus is on current state of environment -Tools used : scanners. (qualys / Rapid7) Patch Management Focus - CORRECT ANSWER -Reactive -Primary focus is on patches being available or attempts to apply to existing environments -Tools used : patch deployment tools (Altiris / SCCM ) Vulnerability Response Scopes - CORRECT ANSWER Vulnerability Responses - sn_vul Security support Common - sn_sec Vulnerability Response Tables - CORRECT ANSWER 43 in VR and 27 in Security support Task Extending tables Vulnerable Item [sn_vul_vulnerable_item] Vulnerability Group [sn_vul_vulnerability] Vulnerability response Roles - CORRECT ANSWER sn_vul.vulnerability_read sn_vul.vulnerability_write sn_vul.vulnerability_admin permits visibility to the application menu and modules, vulnerable software and items - CORRECT ANSWER sn_vul.vulnerability_read needed to create and update vulnerable items, groups etc... - CORRECT ANSWER sn_vul.vulnerability_write Vulnerability administrator is able to modify application property and configuration - CORRECT ANSWER sn_vul.vulnerability_admin sn_vul.autocreate_vul_centric_group - CORRECT ANSWER Determines if to allow auto creation of groups sn_vul.popup - CORRECT ANSWER Allow customization when creating a Problem, Change or Security Incident in Vulnerability Item form. sn_vul.vulnerable_item.approval_required - CORRECT ANSWER Determines whether an approval process is required to move a vulnerable item into a terminal state. sn_vul.email_to - CORRECT ANSWER Specifies the inbox used by vulnerability tools Vulnerability Sources - CORRECT ANSWER NVD CWE CVE When is a vulnerable item created? - CORRECT ANSWER When CVE-ID matches a vulnerable software or CI VIT cannot exist without specific CI How are vulnerability groups created automatically - CORRECT ANSWER Using vulnerability groups Which of the following is NOT is the Vulnerability scope? Vulnerability groups Group rules Vulnerability Calculator Filtered groups Scanner rate limit Rate limits Assignment rules - CORRECT ANSWER Filtered groups Qualys plugin - CORRECT ANSWER Synchronizes Qualys IT Asset discovery and ServiceNow's CMDB system How does Qualys load data into instance - CORRECT ANSWER Uses scheduled jobs that query and load Qualys scans into the instance What is a QID - CORRECT ANSWER -is the unique ID number assigned to a vulnerability -Information imported is stored on its own table -Sn_vul_third_party_entry Extended from vulnerability table How are Scanners added ? - CORRECT ANSWER Vulnerability scanning > Scanners > New -Use integrations and processor scripts to handle the integration -Integration script handles interface with system -Processor script handles processing the received data What are Rate Limit Definitions? - CORRECT ANSWER You can define the rate that different types of scans are performed to balance the load in your scan queue. Conditions defined in the rate limit determine whether the rate limits are applied to queued entries. -You get a queue table -Then conditions on that table of what should be processed -Then script that returns true or false How do you link Rate limit scanners and scanners? - CORRECT ANSWER Using a Scanner Rate limit Lets you define scanner and rate limit to use Can set how many queues are processed What does Qualys Host Detection Integration do? - CORRECT ANSWER queries host from Qualys and runs a Qualys Host transform to insert or update corresponding Cis into the Servicenow CMDB What fields are populated when Qualys inserts a ci? - CORRECT ANSWER Class Name CI Name DNS Name Fully qualified domain name Ip address Which fields are added once the qualys Vulnerability management plugin is activated? - CORRECT ANSWER Qualys ID Qualys host ID Created by Qualys Which script includes are used by the Qualys plugin? - CORRECT ANSWER Search and population logic located in "QualysUtil" and "QualysSimpleTranform" How is Qualys host data handled? - CORRECT ANSWER creates new new ci with new type OR Log instead of updating CI What is asset tagging? - CORRECT ANSWER -Tagging information can be loaded into a separate custom related table to the CI for additional reporting information by setting the asset_tags parameter to 1 -Information may be truncated as result due to it adding to xml payloads -System property needs to be increased to prevent truncated data Glide.db.impex.XMLLoader.max.file.size.mb What is the Sn_vul.autocreate_vul_centric_group property used for? - CORRECT ANSWER -Default set to true -Any vulnerability that comes in and doesn't match an existing group will be placed in its own orphaned group Role required for grouping vulnerabilities manually? - CORRECT ANSWER Sn_vul.admin What are vulnerability calculators - CORRECT ANSWER -Built to prioritize and rate the impact of VIT's based on any criteria by using condition filters -Each calculator contains a list of calculator rules with a condition determining when to apply it -When conditions run they are evaluated in order and whichever matches first is used What are assignment rules? - CORRECT ANSWER used to get the new record to the correct group as soon as possible T/f vulnerable items can be closed manually? - CORRECT ANSWER True but consider using automation instead t/f There are preconfigured SLA's - CORRECT ANSWER false What are Remediation Target Rules? - CORRECT ANSWER Define the expected timeframe for remediating a VIT Has reminder email that sends out x days before due How do you close/defer a Vulnerability item? - CORRECT ANSWER Close/defer ui action When you select the close/defer ui action what happens? - CORRECT ANSWER opens the review_request ui page as a pop up Where are the choices stored for the close/defer pop up? - CORRECT ANSWER Vulnerability state change approval table sn_vul_change_approval When a VIT is closed or deferred where are the records created? - CORRECT ANSWER Vulnerability state change approval table sn_vul_change_approval If a VIT is to be closed/deferred which is permanent? - CORRECT ANSWER Closed is permanent Deferred has a choice that allows you to pick date that it is deferred until When determining data visualization what will the CIO/CISO want to see? - CORRECT ANSWER Need high level overviews Single, clear indicators of organizational health and function When determining data visualization what will the Managers want to see? - CORRECT ANSWER Aggregations for priority and workload Need drill down to granularity Need time period views When determining data visualization what will the Analyst want to see? - CORRECT ANSWER Need up to the minute views Need clear prioritizations Need granularity Who will ask "What is the status & quality of my requested service" regarding reports and dashboards - CORRECT ANSWER End users Who will ask "How can I impact trends that affect cost and quality" regarding reports and dashboards - CORRECT ANSWER Service Owner Who will ask "How can I work more efficiently to achieve targets" regarding reports and dashboards - CORRECT ANSWER Front line worker Who will ask "How are we tracking against organizational objectives?" regarding reports and dashboards - CORRECT ANSWER Executive What is the difference between Reporting and PA? - CORRECT ANSWER Reporting -Real time information - where are we now -Analysis of what has happened Performance Analytics Process trends - how did we get here - Insight into leading indicators that influence health of process The Vulnerability Management page does what? - CORRECT ANSWER -Provides an executive view into vulnerabilities and vit's -With PA - content pack - vulnerability response plugin [com.snc.vulnerability.analytics] users with certain roles can view data of interest to the Chief information security officer, vulnerability managers and analyst The Vulnerability Remediation page is used for? - CORRECT ANSWER Involves viewing trends, managing risk, and monitoring assignment groups Can review high risk issues, assignment group workloads, deferrals and reoccurring vulnerabilities The PA Vulnerability management dashboard is used for? - CORRECT ANSWER Management can easily track volume, performance and progress Can filter by assignment group, exploits, risk rating, and state etc... Quickly gain insight on what is affected or exposed Which tables are commonly used for reporting? - CORRECT ANSWER Vulnerability Item Task Vulnerability Group Vulnerability Item Vulnerability Software What are indicators used for? - CORRECT ANSWER Also known as known as metrics, business metrics or KPI's Are statistics that businesses track to measure current conditions and forecast trends What are the two type of Indicators? - CORRECT ANSWER Leading indicators Lagging indicators What is the difference between lagging and leading indicators? - CORRECT ANSWER Leading indicators - Focus on input that is required to achieve an objective - Harder to measure which is why most reports are lagging indicators - They are easier to influence than lagging indicators Lagging indicators - Measure the output of your activities Which property allows customization when creating a Problem, Change or Security Incident in Vulnerability Item form? - CORRECT ANSWER sn_vul.popup Which property when true, automatically creates a Vulnerability Group when a vulnerable item is created for a vulnerability entry that does not yet have a group ? - CORRECT ANSWER sn_vul.autocreate_vul_centric_group Where is the "filter group" module located? - CORRECT ANSWER Security Operations > Groups > Filter Groups What are the States of the Vulnerability Maturity Model? - CORRECT ANSWER 0 - Manual operations (spreadsheets) 1 - Automated Prioritization (auto priority/groups) 2 - Improved Remediation () 3 - Enterprise Risk Trending Which roles are delegate roles to the sn_vul.admin role? - CORRECT ANSWER sn_sec_cmn.admin sn_vul.vulnerability_write What state does the VIT go into once it is deferred? - CORRECT ANSWER In review If you were to create SLA's what would be the start, what would be the hold and what would be the end states? - CORRECT ANSWER Start - sys_created_on pause - in review (deferred) end - cancelled or closed What state does the VIT go to after it is closed for "result invalid" or "fixed"? - CORRECT ANSWER In review What state does the VIT go into after it is reopened/ deferred is denied? - CORRECT ANSWER Open What is the prefix for tables in the vulnerability response scope? - CORRECT ANSWER sn_vul_ Vulnerability Response works closely with which ITIL product? incident problem change - CORRECT ANSWER change When deferring a VIT what fields are mandatory? - CORRECT ANSWER State Reason Until When closing a VIT what fields are mandatory? - CORRECT ANSWER State Reason Additional information Who approves or rejects the deferred/closed VITS? - CORRECT ANSWER Vulnerability Response - group only group created with the app What are the sizing limits and amount for each groups? - CORRECT ANSWER Less than 1 million = XL size 1-2.5 million = XXL size 2.5 million or more = Ultra What are the SecOps Product Tiers? - CORRECT ANSWER Good - standard VR or SIR Better - SIR + VR + Threat Intelligence Best - SIR + VR + TI + Trusted Security Circles What is the Main goal of VR? - CORRECT ANSWER -Primary focus is on current state of environment -Process of identifying, classifying, remediation and mitigating vulnerabilities Which Role do you need in order to see the overview dashboard? - CORRECT ANSWER sn_vul.vulnerability_read Where does the community developed list of common security weaknesses come from? - CORRECT ANSWER CWE? What does Qualys use to query and load data into SN? - CORRECT ANSWER scheduled jobs which of the Vulnerable group options does not have the option to Automatically refresh vulnerable items? -manual -condition -filtered group - CORRECT ANSWER Manual How are vulnerabilities closed? - CORRECT ANSWER -report remediated vulnerabilities but ultimately the scanner confirms/denies the final result -compare subsequent scans to verify results what are the Recommended dashboard for VR? - CORRECT ANSWER Vulnerability Management (PA) Vulnerability Remediation Vulnerability Management [Show More]
Last updated: 2 years ago
Preview 1 out of 17 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$11.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 30, 2023
Number of pages
17
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 30, 2023
Downloads
0
Views
38