Computer Science > QUESTIONS & ANSWERS > SSCP practice questions and answers WGU C845; Latest 2022 (All)
SSCP practice questions and answers WGU C845; Latest 2022
Document Content and Description Below
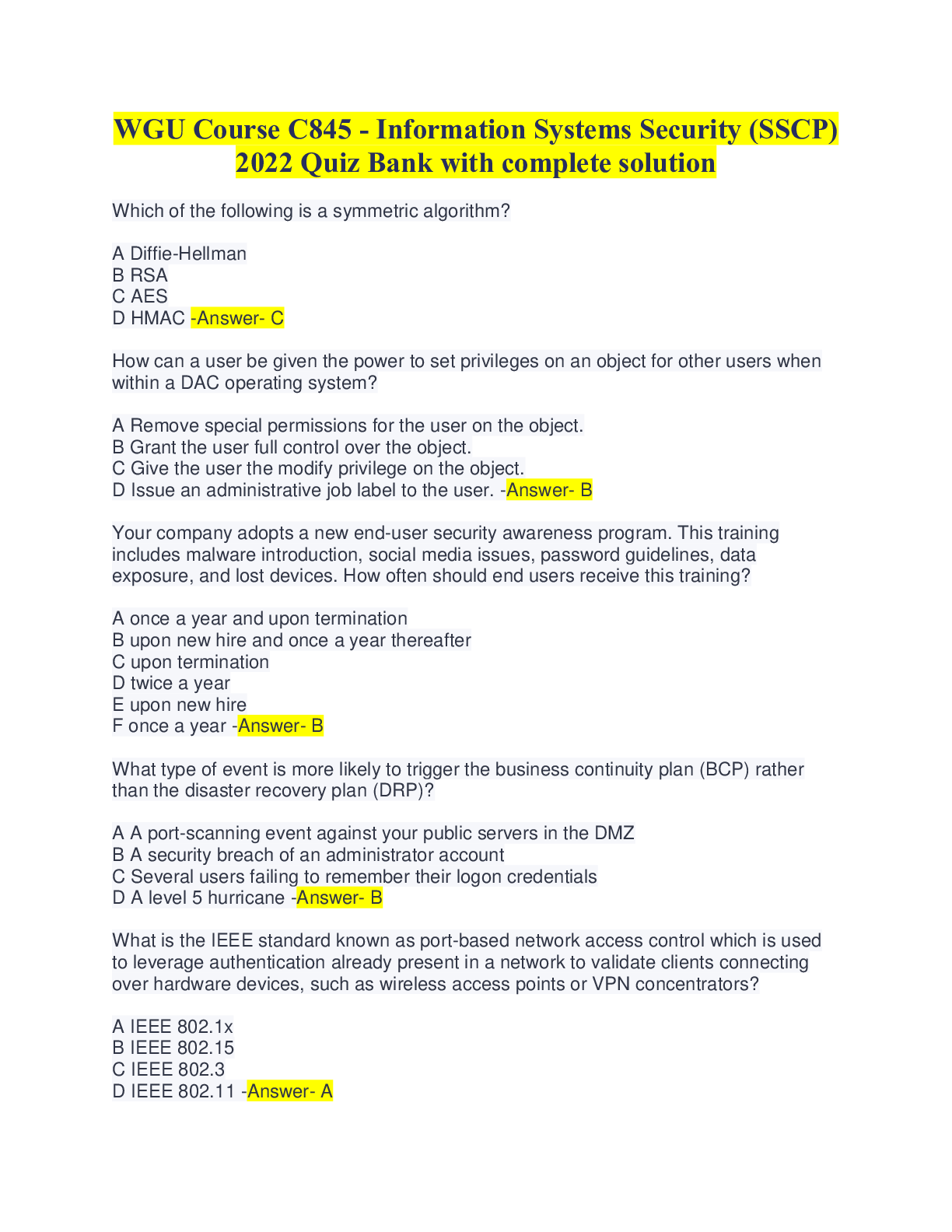
SSCP practice questions and answers WGU C845; Latest 2022 What can be defined as a table of subjects and objects indicating what actions individual subjects can take upon individual objects? A. A ... capacity table B. An access control list C. An access control matrix D. A capability table -Answer- C. An Access Control Matrix Which access control model is best suited in an environment where a high security level is required and where it is desired that only the administrator grants access control? A. DAC B. MAC C. Access control matrix D. TACACS -Answer- B. MAC Which access control model provides upper and lower bounds of access capabilities for a subject? A. Role-based access control B. Lattice-based access control C. Biba access control D. Content-dependent access control -Answer- B Lattice-based access control How are memory cards and smart cards different? A. Memory cards normally hold more memory than smart cards B. Smart cards provide a two-factor authentication whereas memory cards don't C. Memory cards have no processing power D. Only smart cards can be used for ATM cards -Answer- C. Memory Cards have no processing power Why do buffer overflows happen? What is the main cause? A. Because buffers can only hold so much data B. Because of improper parameter checking within the application C. Because they are an easy weakness to exploit D. Because of insufficient system memory -Answer- B. because of improper parameter checking within the application What is the main focus of the Bell-LaPadula security model? A. Accountability B. Integrity C. Confidentiality D. Availability -Answer- C. Confidentiality Which of the following statements pertaining to the Bell-LaPadula is TRUE if you are NOT making use of the strong star property? A. It allows "read up." B. It addresses covert channels. C. It addresses management of access controls. D. It allows "write up." -Answer- D. it allows "write up." Which security model introduces access to objects only through programs? A. The Biba model B. The Bell-LaPadula model C. The Clark-Wilson model D. The information flow model -Answer- C. The Clark-Wilson model Which security model ensures that actions that take place at a higher security level do not affect actions that take place at a lower level? A. The Bell-LaPadula model B. The information flow model C. The noninterference model D. The Clark-Wilson model -Answer- C. the noninterference model Which of the following security models does NOT concern itself with the flow of data? A. The information flow model B. The Biba model C. The Bell-LaPadula model D. The noninterference model -Answer- D. the noninterference model What Orange Book security rating is reserved for systems that have been evaluated but fail to meet the criteria and requirements of the higher divisions? A. A B. D C. E D. F -Answer- B. D Which division of the Orange Book deals with discretionary protection (need-to-know)? A. D B. C C. B D. A -Answer- B. C Which of the following are not Remote Access concerns? A. Justification for remote access B. Auditing of activities C. Regular review of access privileges D. Access badges -Answer- D. Access badges Smart cards are an example of which type of control? A. Detective control B. Administrative control C. Technical control D. Physical control -Answer- C. Technical Control What security model is dependent on security labels? A. Discretionary access control B. Label-based access control C. Mandatory access control D. Non-discretionary access control -Answer- C. Mandatory Access control What security model implies a central authority that define rules and sometimes global rules, dictating what subjects can have access to what objects? A. Flow Model B. Discretionary access control C. Mandatory access control D. Non-discretionary access control -Answer- D. Non-discretionary access control Which of the following access control models requires defining classification for objects? A. Role-based access control B. Discretionary access control C. Identity-based access control D. Mandatory access control -Answer- D. Mandatory access control In the context of access control, locks, gates, guards are examples of which of the following? A. Administrative controls B. Technical controls C. Physical controls D. Logical controls -Answer- C. Physical controls Which of the following statements pertaining to using Kerberos without any extension is false? A. A client can be impersonated by password-guessing. B. Kerberos is mostly a third-party authentication protocol. C. Kerberos uses public key cryptography. D. Kerberos provides robust authentication -Answer- C. Kerberos uses public key crytography Which of the following statements pertaining to Kerberos is false? A. The Key Distribution Center represents a single point of failure. B. Kerberos manages access permissions. C. Kerberos uses a database to keep a copy of all users' public keys. D. Kerberos uses symmetric key cryptography -Answer- C. Kerberos uses a database to keep a copy of all users' public keys. Which access control model would a lattice-based access control model be an example of? A. Mandatory access control. B. Discretionary access control. C. Non-discretionary access control. D. Rule-based access control -Answer- A. Mandatory access control Which of the following is an example of discretionary access control? A. Identity-based access control B. Task-based access control C. Role-based access control D. Rule-based access control -Answer- A. Identity-based access control Which of the following would be used to implement Mandatory Access Control (MAC)? A. Clark-Wilson Access Control B. Role-based access control C. Lattice-based access control D. User dictated access control -Answer- C. Lattice-based access control Which type of attack involves impersonating a user or a system? A. Smurfing attack B. Spoofing attack C. Spamming attack D. Sniffing attack -Answer- B. Spoofing attack Which of the following is NOT an advantage that TACACS+ has over TACACS? A. Event logging B. Use of two-factor password authentication C. User has the ability to change his password D. Ability for security tokens to be resynchronized -Answer- A. Event logging Which of the following remote access authentication systems is the most robust? A. TACACS+ B. RADIUS C. PAP D. TACACS -Answer- A. TACAS+ Which of the following is an example of a passive attack? A. Denying services to legitimate users B. Shoulder surfing C. Brute-force password cracking D. Smurfing -Answer- B. Shoulder surfing What does the Clark-Wilson security model focus on? A. Confidentiality B. Integrity C. Accountability D. Availability -Answer- B. Integrity [Show More]
Last updated: 3 years ago
Preview 1 out of 301 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$12.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 07, 2022
Number of pages
301
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 07, 2022
Downloads
0
Views
120