CompTIA Cybersecurity Analyst (CySA+) - Module 2:
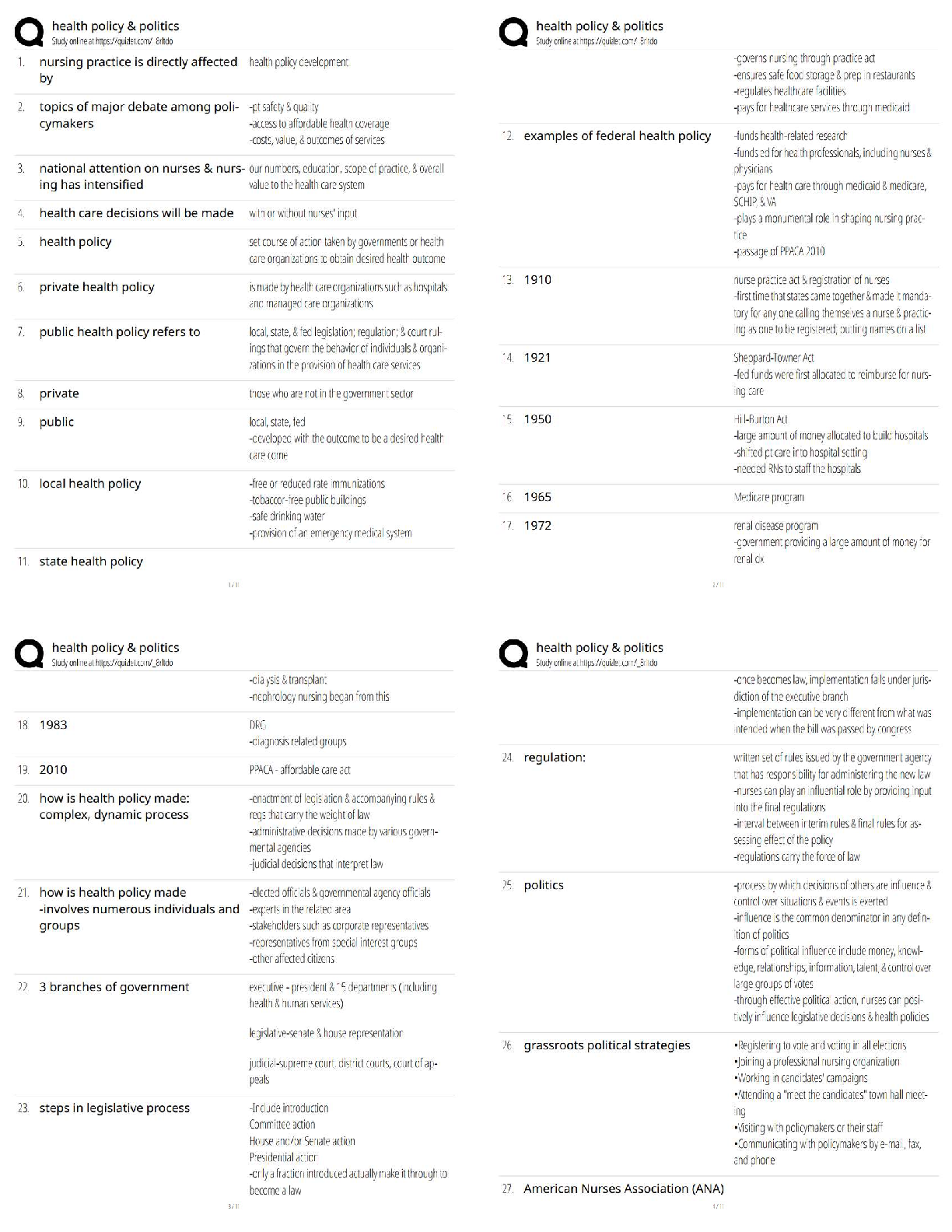
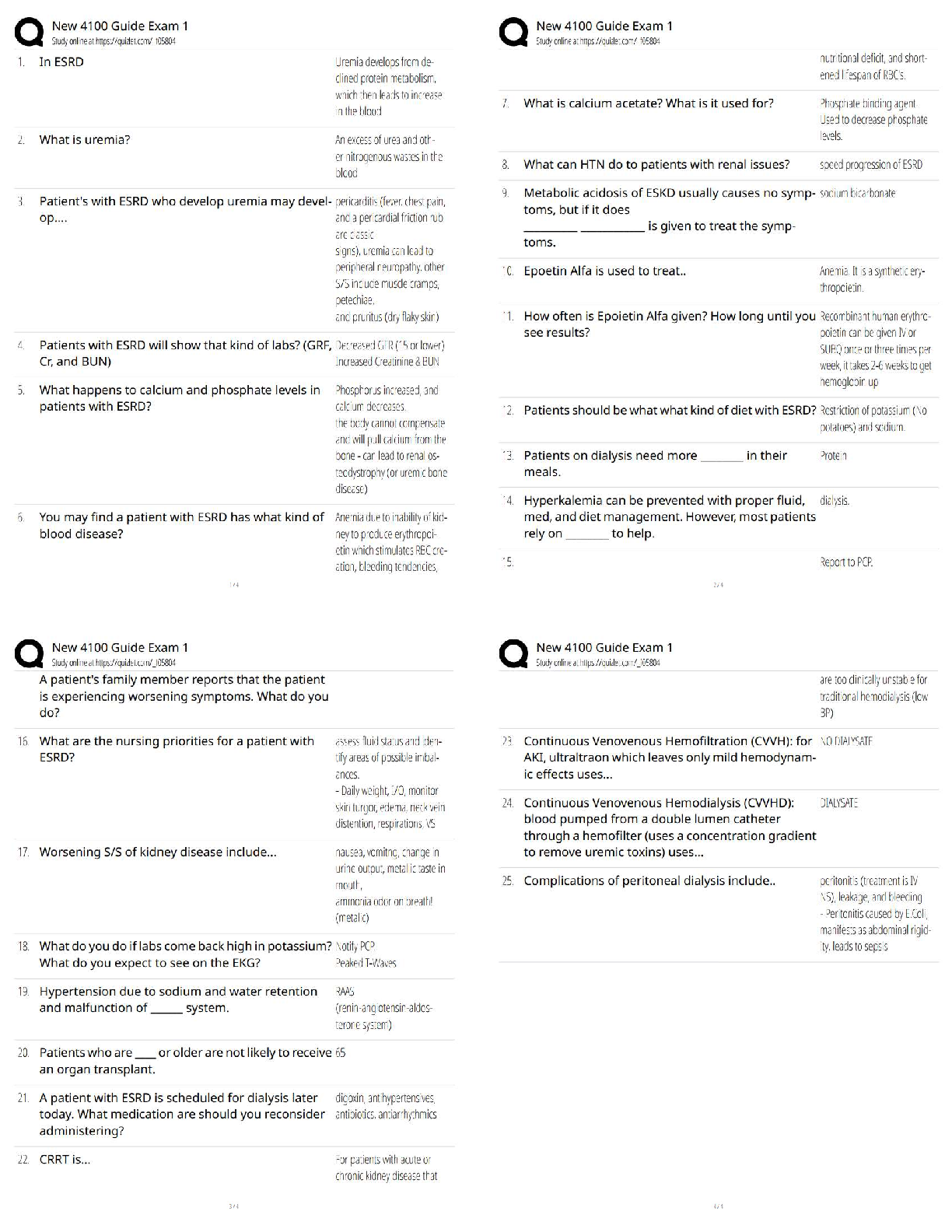
Vulnerability Management
All parts of a security policy should be public knowledge.
True
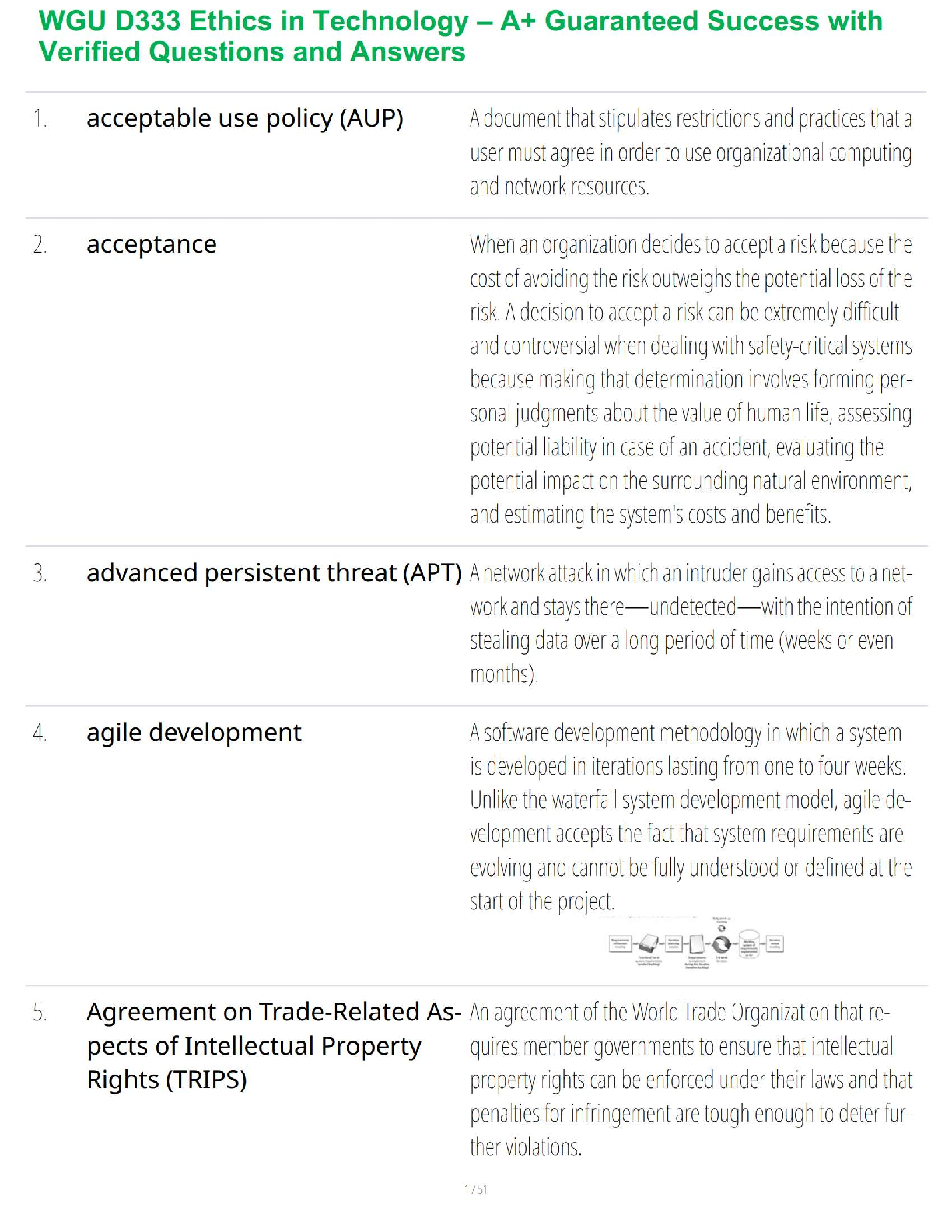
False -Answer- False
What reasons might a company forgo scanning a critical
...
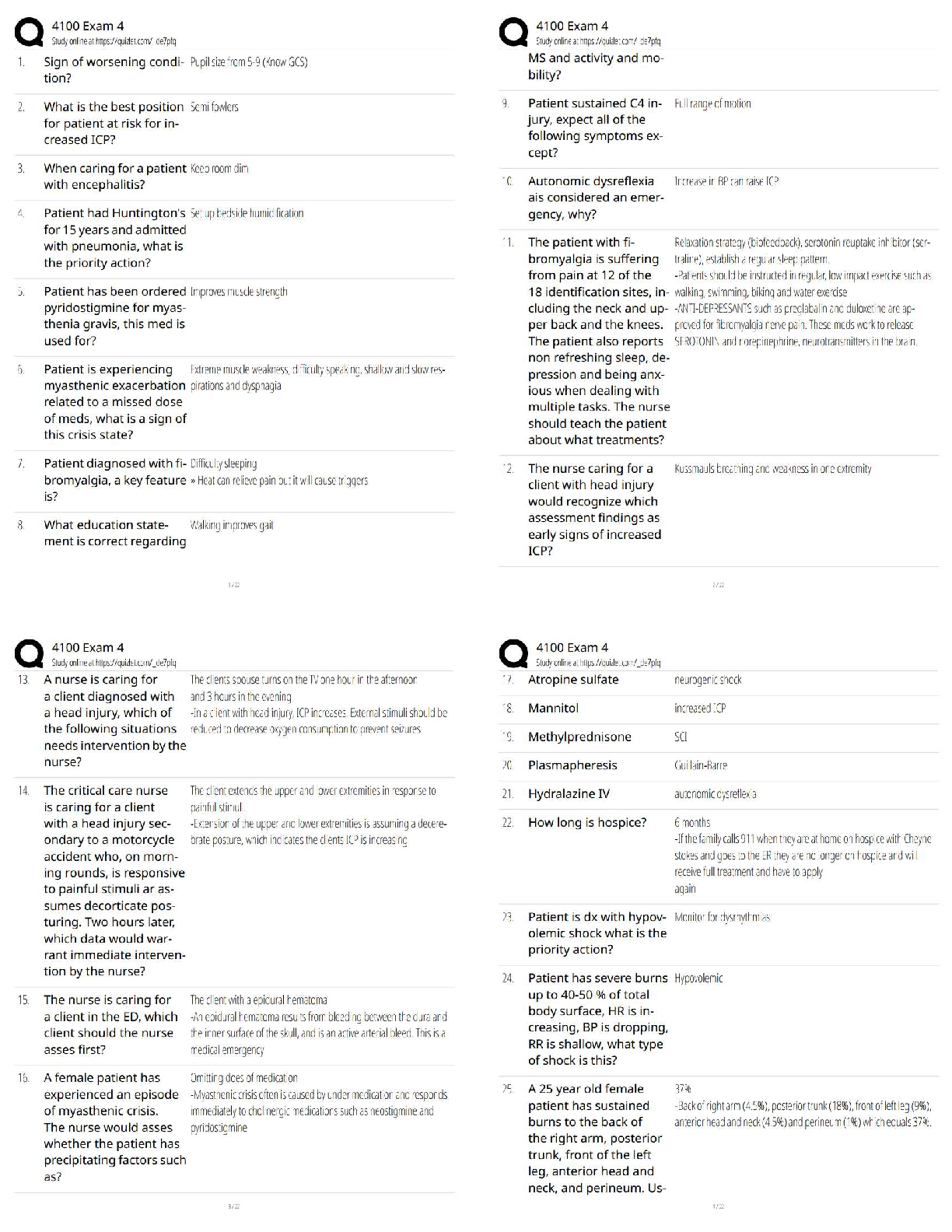
CompTIA Cybersecurity Analyst (CySA+) - Module 2:
Vulnerability Management
All parts of a security policy should be public knowledge.
True
False -Answer- False
What reasons might a company forgo scanning a critical system?
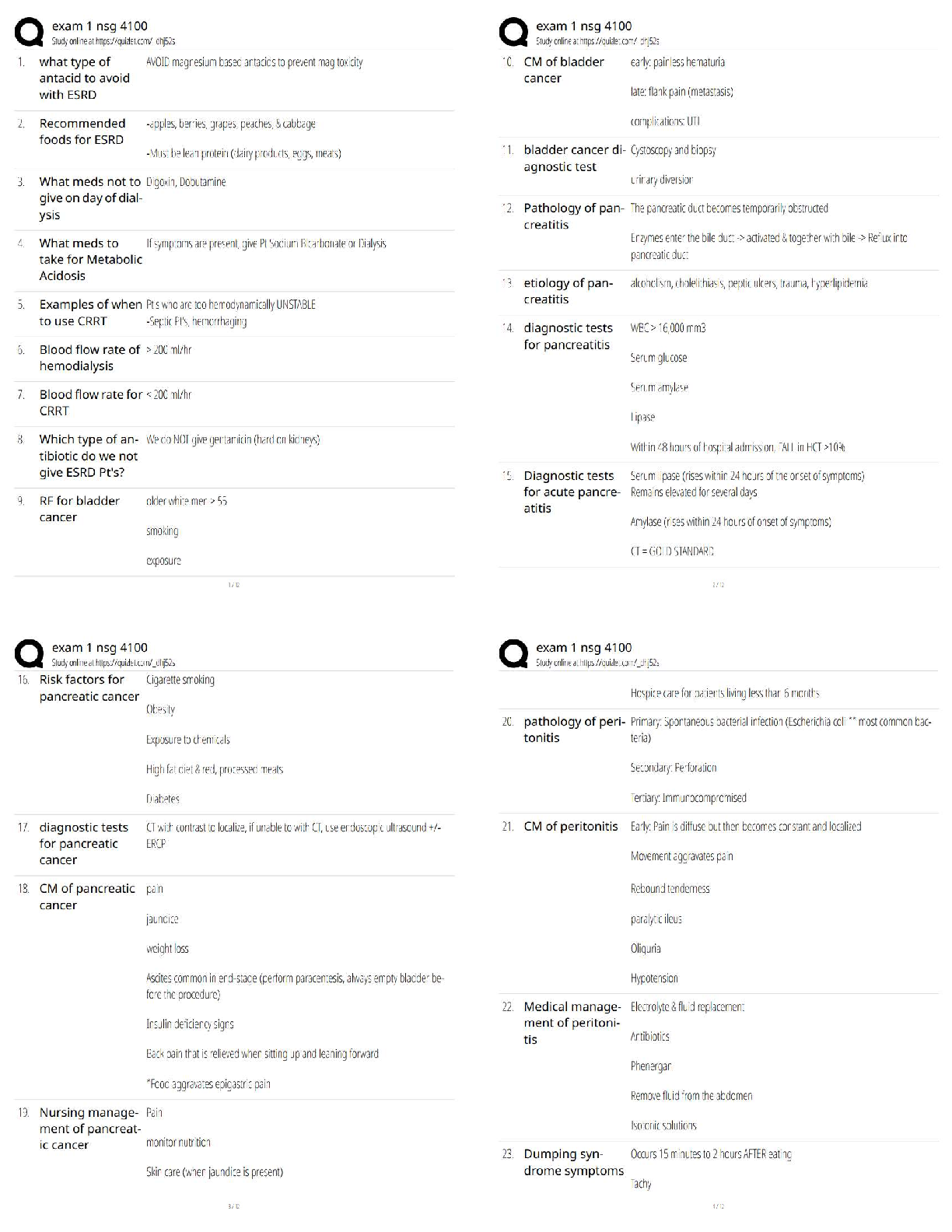
Too much time
Confidentiality
Backups already exist
Costs too much -Answer- Too much time & Costs too much
What is the factor that determines scanning frequency characterized by an accepted
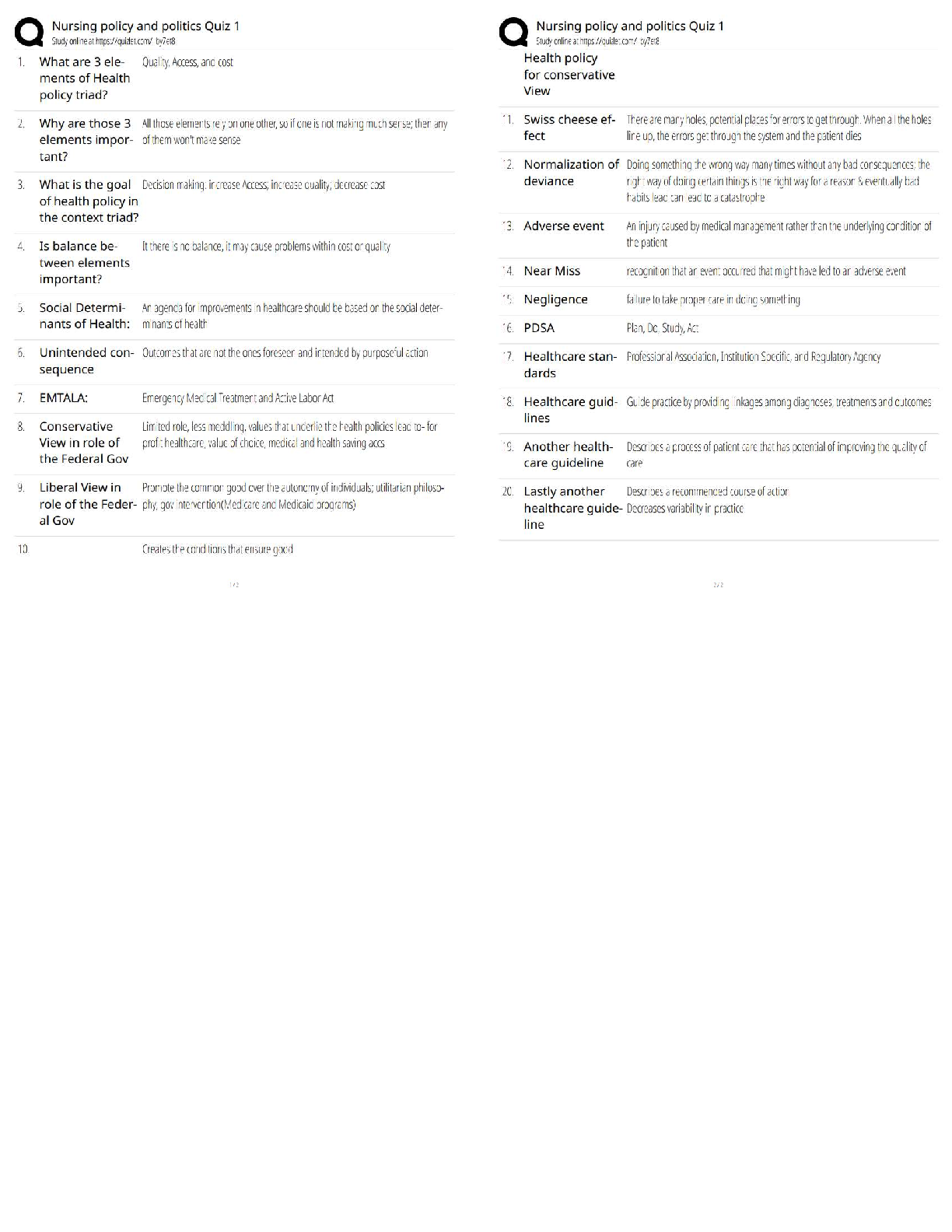
amount of risk?
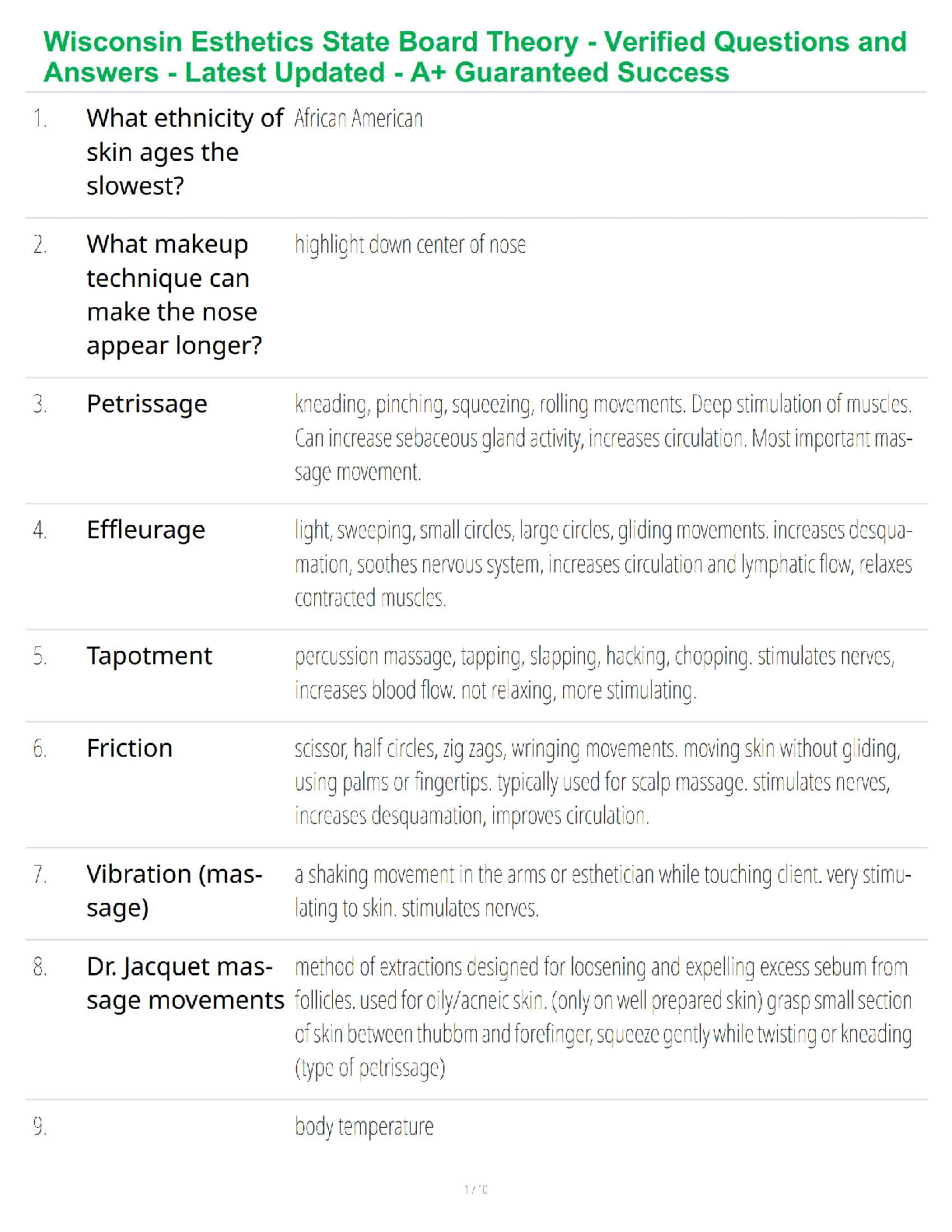
Technical Constraints
Risk Acceptance
Risk Appetite
Regulatory Requirements -Answer- Risk Appetite
An assessment scan is used to discover assets.
True
False -Answer- False
What type of test gives the best perspective of an outsider threat?
Non-Credentialed Scan
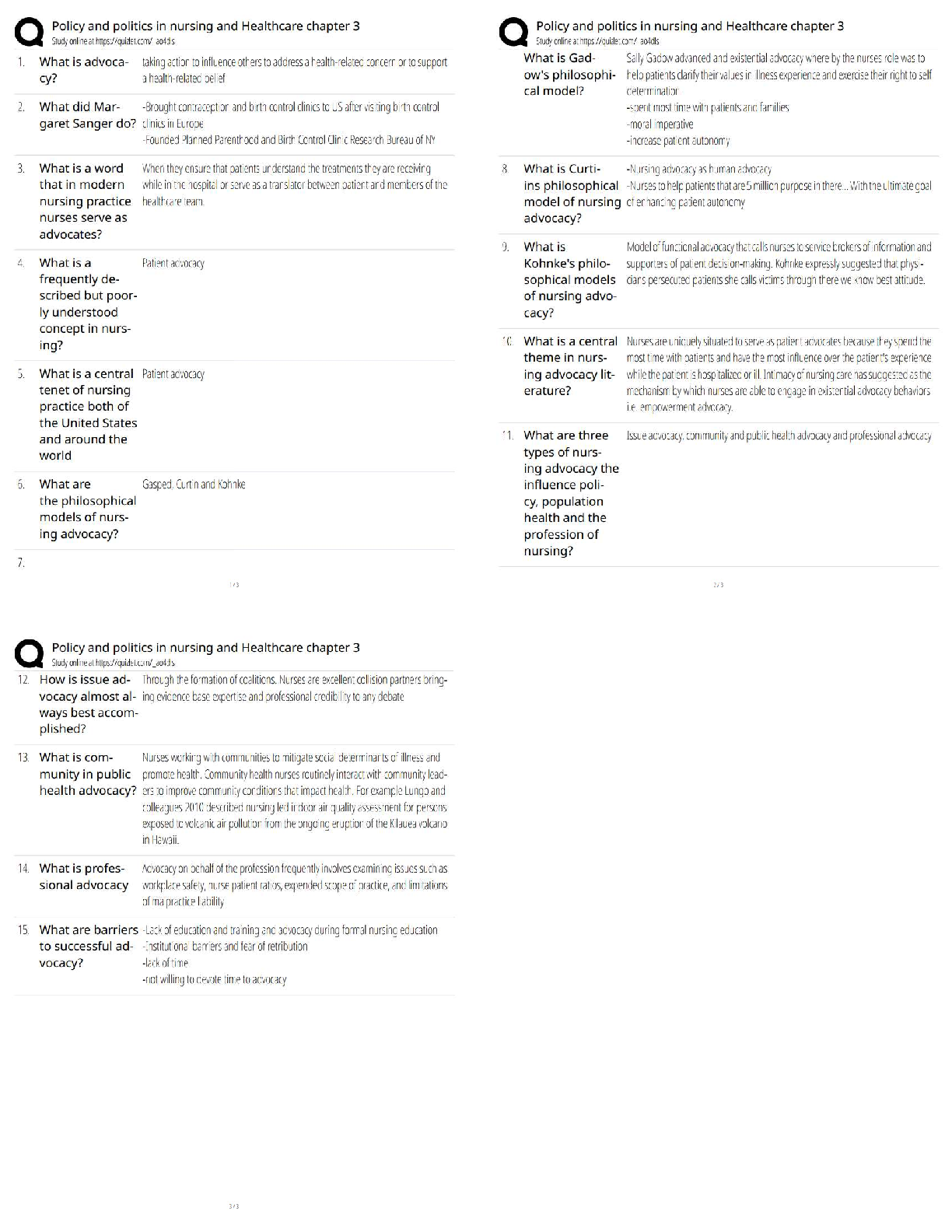
Passive Scan
Agent-Based Scan
Credentialed Scan -Answer- Non-Credentialed Scan
What should be considered when prioritizing vulnerabilities to be fixed?
Where it is
How critical it is
Time to fix
Which scanner was used -Answer- How critical it is & Time to fix
What is a factor considered when categorizing a change to a system?
ScopeSize
Sensitivity Level
Risk -Answer- Risk
What could inhibit a change from being implemented?
Cost
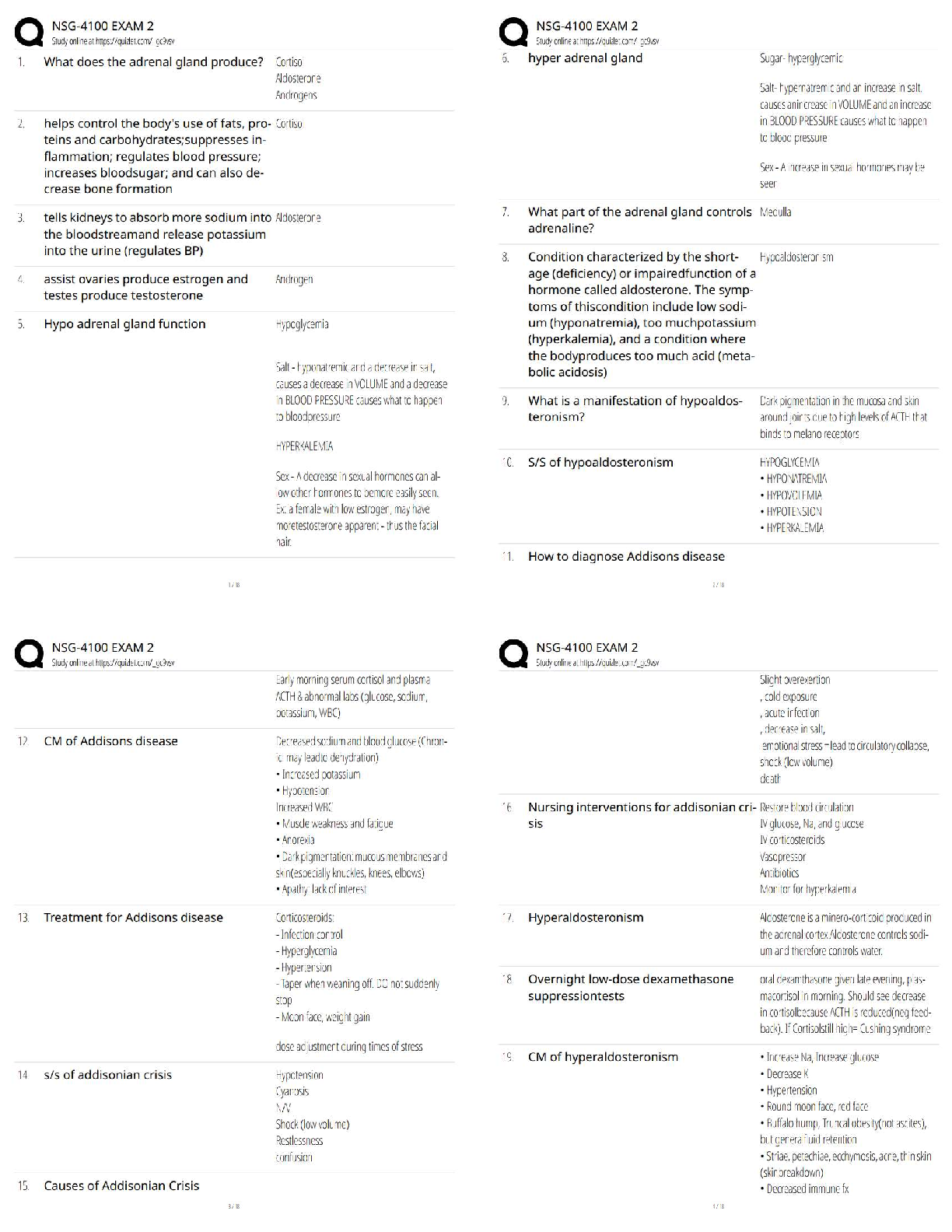
Complexity
Approval
All of the Above -Answer- All of the Above
An Agent-Based Scan has a lesser impact on a network vs Sever-based.
True
False -Answer- True
Which scan effects network traffic the least?
Non-Credentialed Scan
Agent-Based Scan
Passive Scan
Server-Based Scan -Answer- Passive Scan
Which one of these is legally binding?
MOU
SLA
ATWA
MTTR -Answer- SLA
What determines when a companies security capabilities should grow.
Workflow
Regulatory Requirements
Technical Constraints
Risk Appetite -Answer- Workflow
Which type of scan uses a copy of the network traffic to find vulnerabilities?
Agent-Based Scan
Non-Credentialed Scan
Passive Scan
Server-Based Scan -Answer- Passive Scan
The results of vulnerability scans should be shared with the entire company in order to
fix vulnerabilities.True
False -Answer- True
What is it called when a scan misses an existing vulnerability?
False Reporting
True Negative
False Negative
False Positive -Answer- False Negative
Which has a higher chance of being compromised?
Agent-Based Scan
SCAP
Passive Scan
Server-Based Scan -Answer- Agent-Based Scan
Which type of scan is most likely to cause major disruption in everyday operations?
Agent-Based Scan
Non-Credentialed Scan
Server-Based Scan
Credentialed Scan -Answer- Credentialed Scan
What factors help determine the potential frequency of scanning?
Technical Constraints
Vulnerability Feed
Workflow
Scope -Answer- Technical Constraints & Workflow
After a successful scan it is best to continue running them over time.
True
False -Answer- True
When running a vulnerability scan what determines the number of systems are part of
it?
Sensitivity Level
Technical Constraints
Scope
SCAP -Answer- Scope
What is making sure that a vulnerability scanner is kept up-to-date?Regulatory Requirements
Vulnerability Feed
SCAP
Change Control -Answer- Vulnerability Feed
A security policy stays relatively static throughout a companies history.
True
False -Answer- False
What is a projected acceptable amount of downtime that is allowed that can determine if
a change can be implemented?
Regulatory Requirements
MTTR
Risk Appetite
Availability -Answer- Availability
What allows scanners to determine if a system meets a configuration baseline if that
scanner is compatible?
SCAP
SLA
Sandboxing
CVSS -Answer- SCAP
What uses a list of known weaknesses to determine if a system meets certain baseline?
CVSS
CWE
SJW
CVE -Answer- CWE & CVE
Having multiple scanners does not decrease the likelihood of false negatives.
True
False -Answer- False
What determines how far a vulnerability scan will examine?
Vulnerability Feed
Sensitivity Level
Scope
Depth -Answer- Sensitivity LevelRegulatory requirements could prevent a company from increasing it's risk appetite.
True
False -Answer- True
Which scan gives the most information about a system?
Passive Scan
Non-Credentialed Scan
Credentialed Scan
Server-Based Scan -Answer- Credentialed Scan
What determines how frequently a certain type of scan will run?
Sensitivity Level
Time Management
Vulnerability Feed
Scope -Answer- Scope
A companies security policy doesn't need to change for different countries if it is
compliant within it's own.
True
False -Answer- False
What is the average amount of time that it takes to correct an issue?
Availability
MOU
MTTR
Downtime Management -Answer- MTTR
What type of scan gives the best perspective of a potential insider threat?
Credentialed Scan
[Show More]






.png)