Management > QUESTIONS & ANSWERS > PMT 252 PMT 252 Mod 8 Test | Defense Acquisition University (All)
PMT 252 PMT 252 Mod 8 Test | Defense Acquisition University
Document Content and Description Below
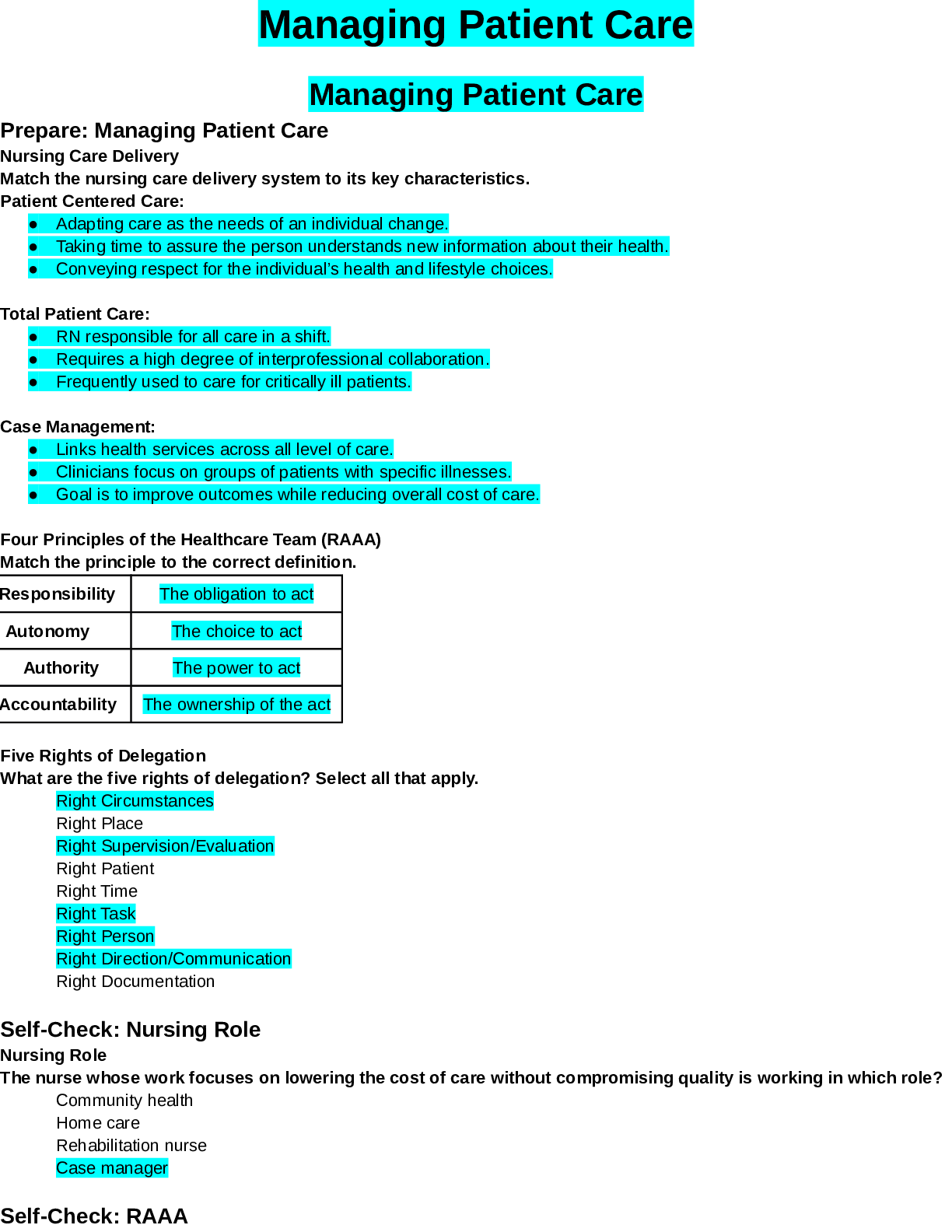
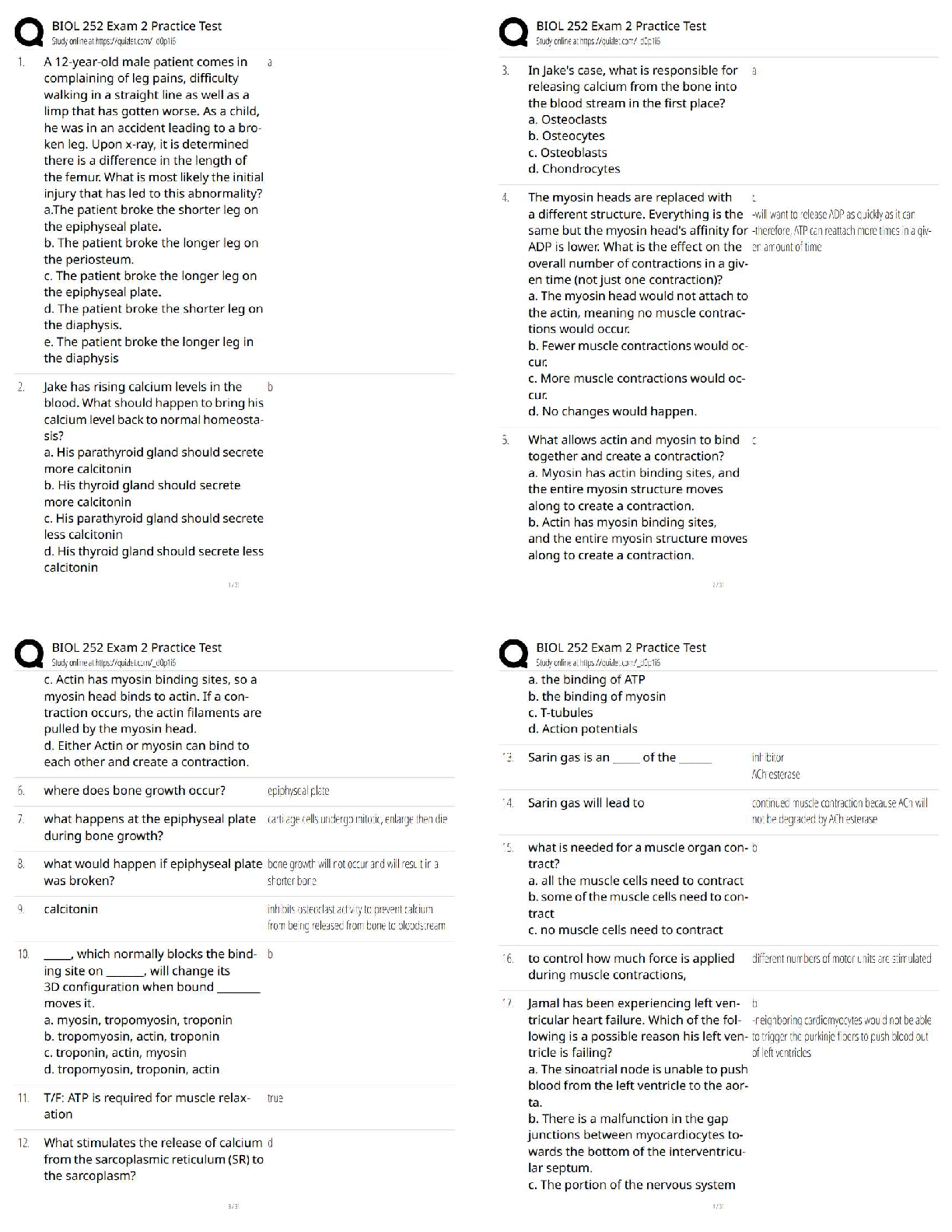
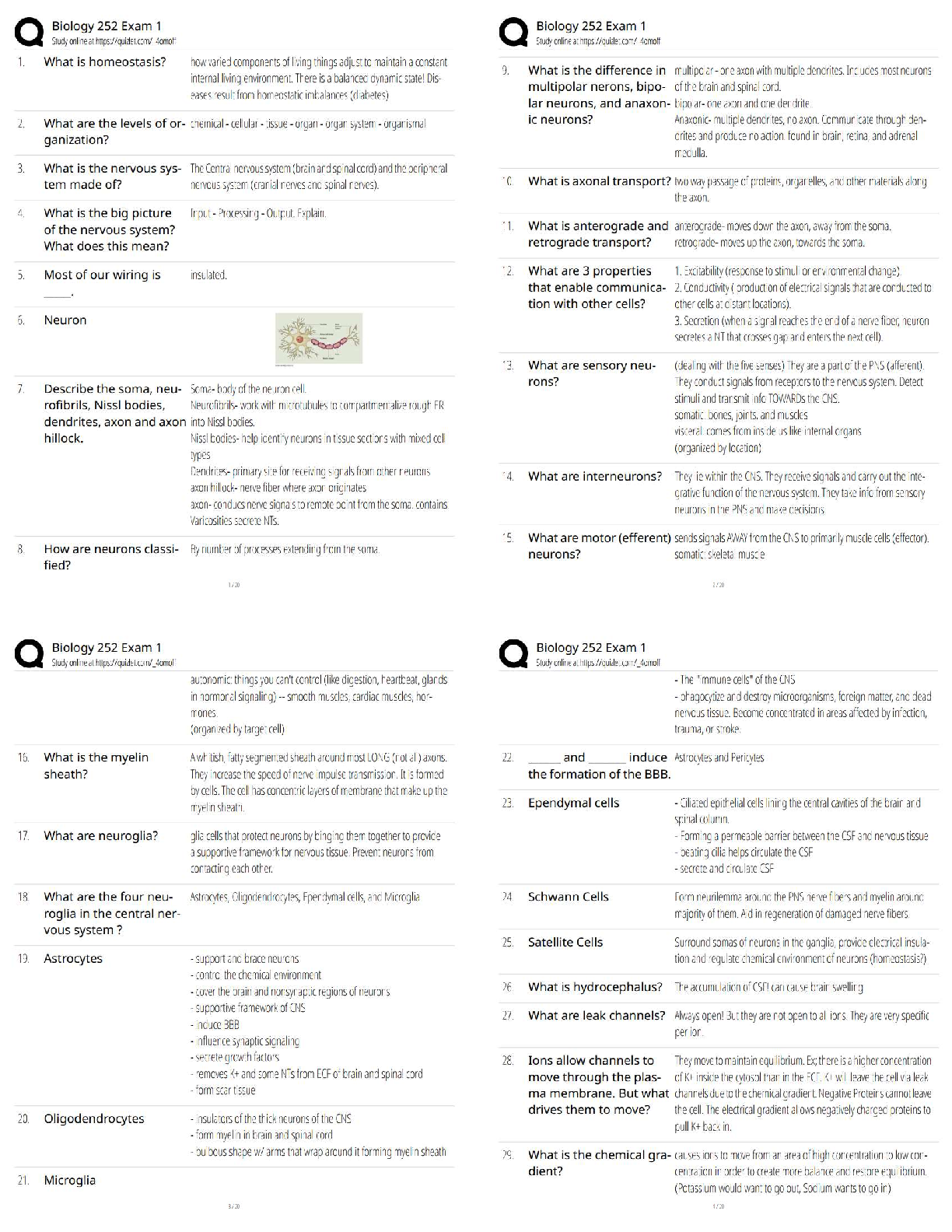
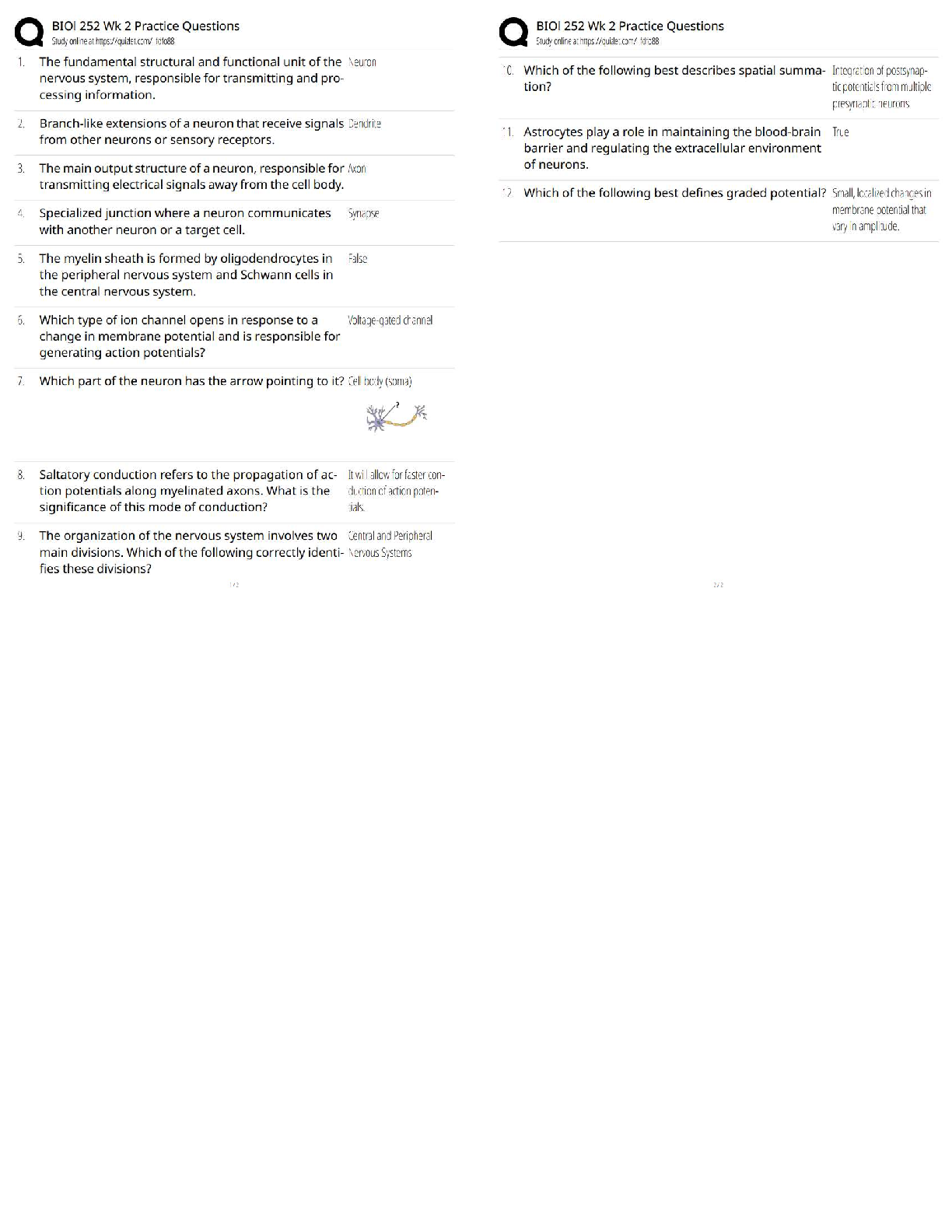
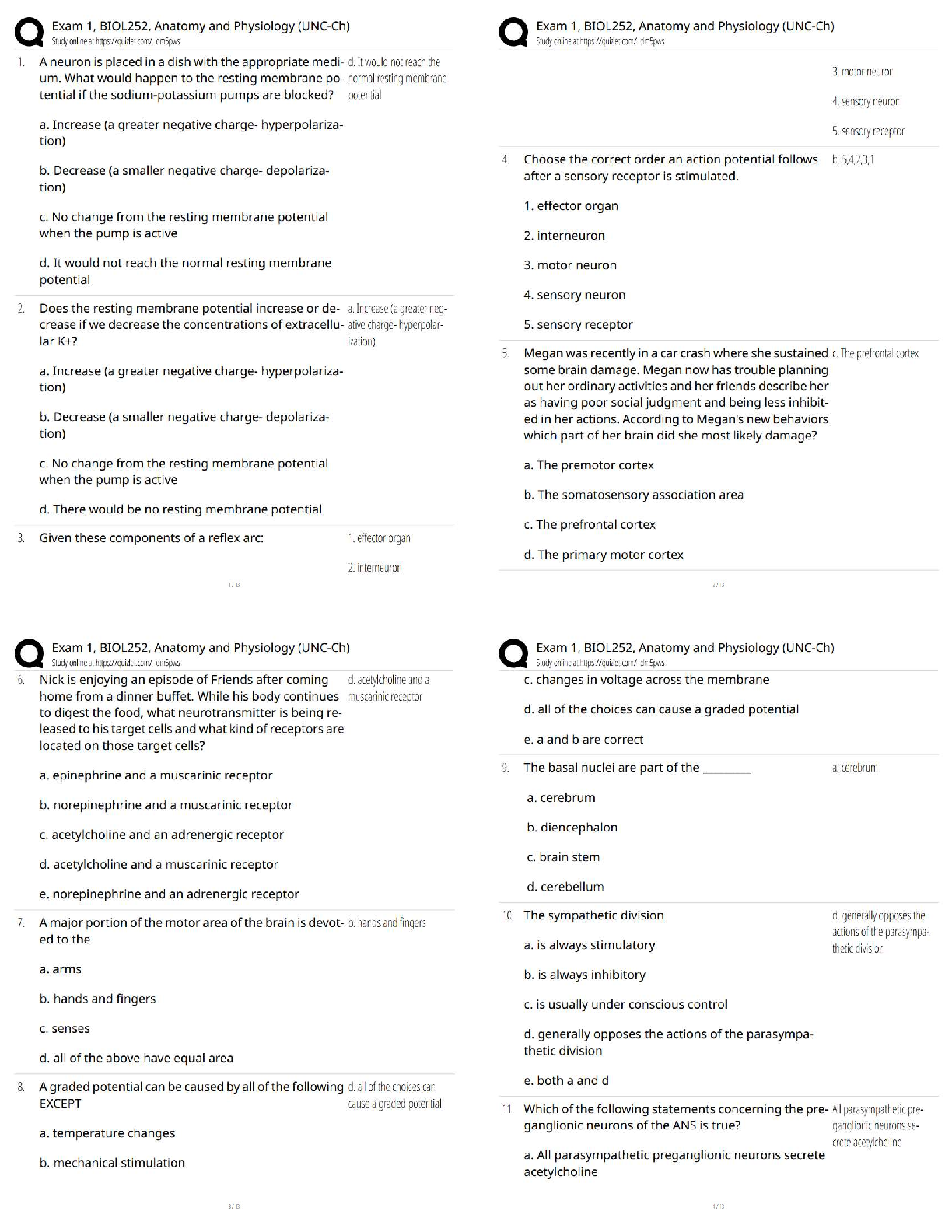
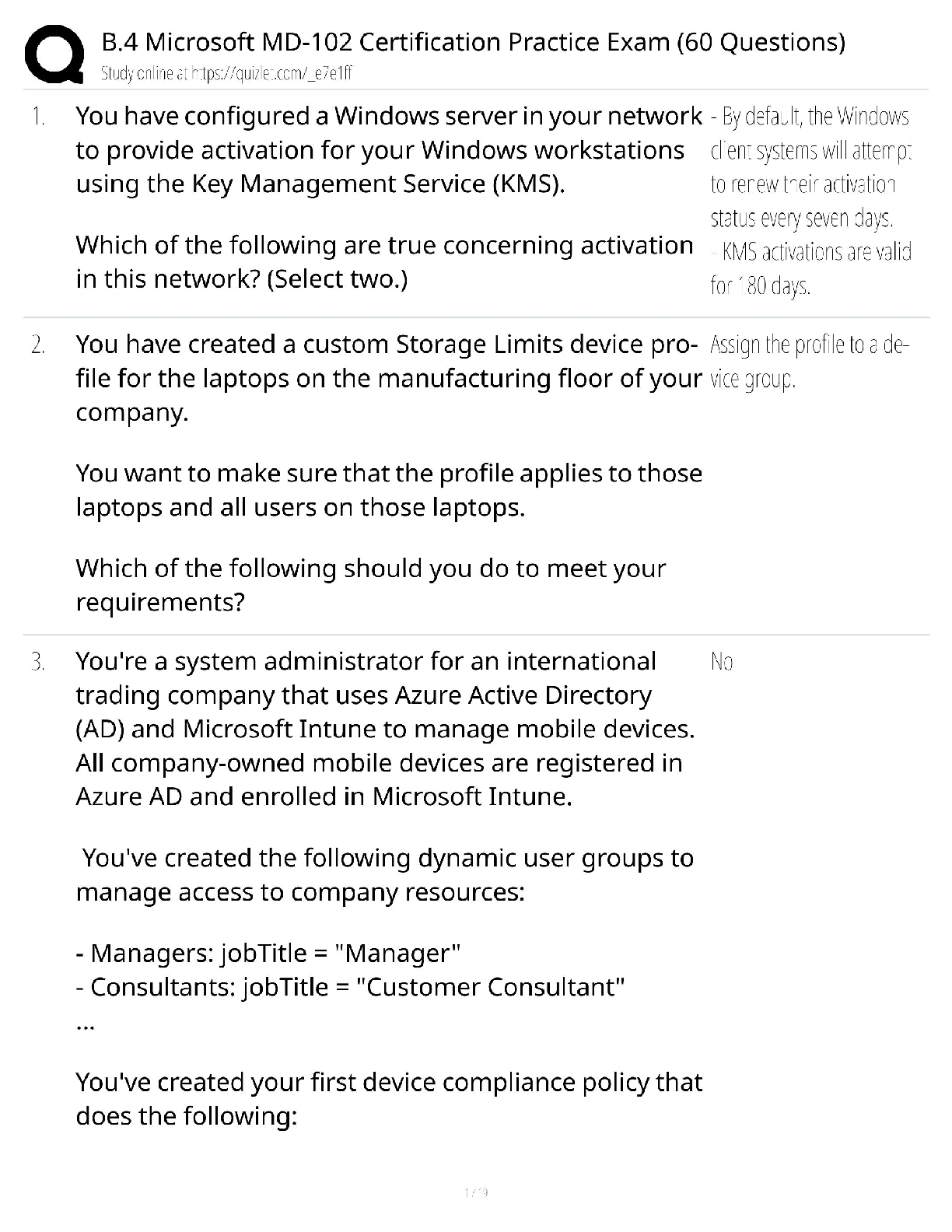
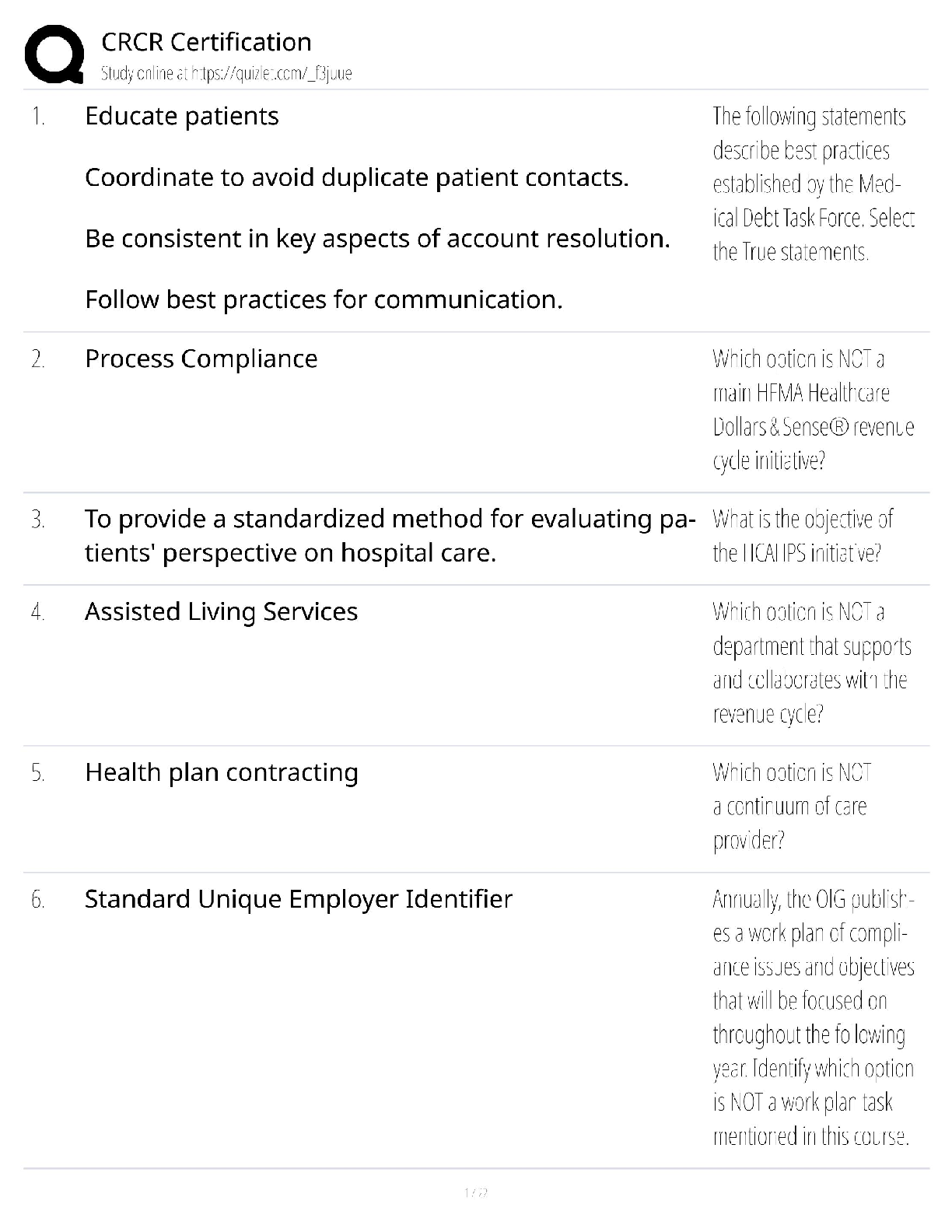
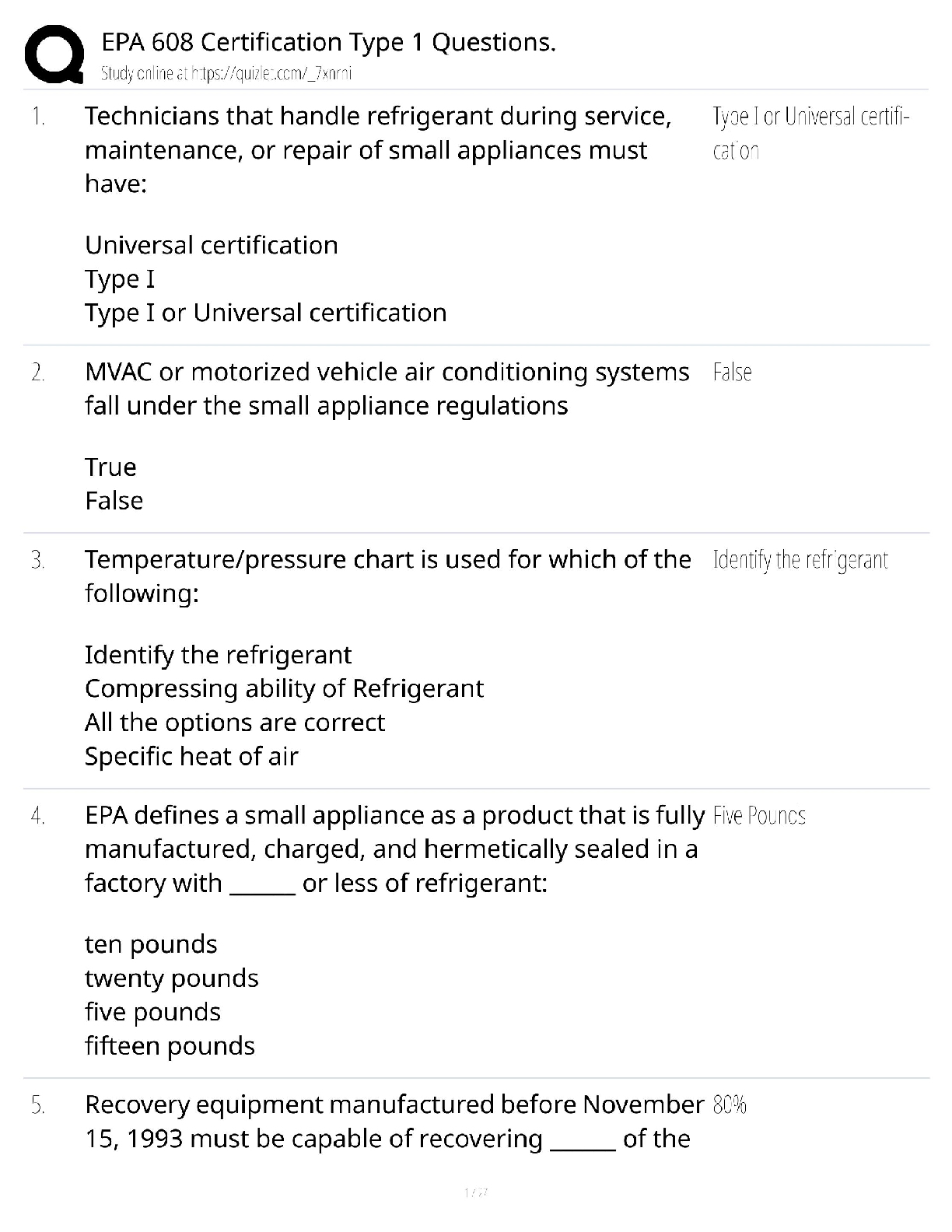
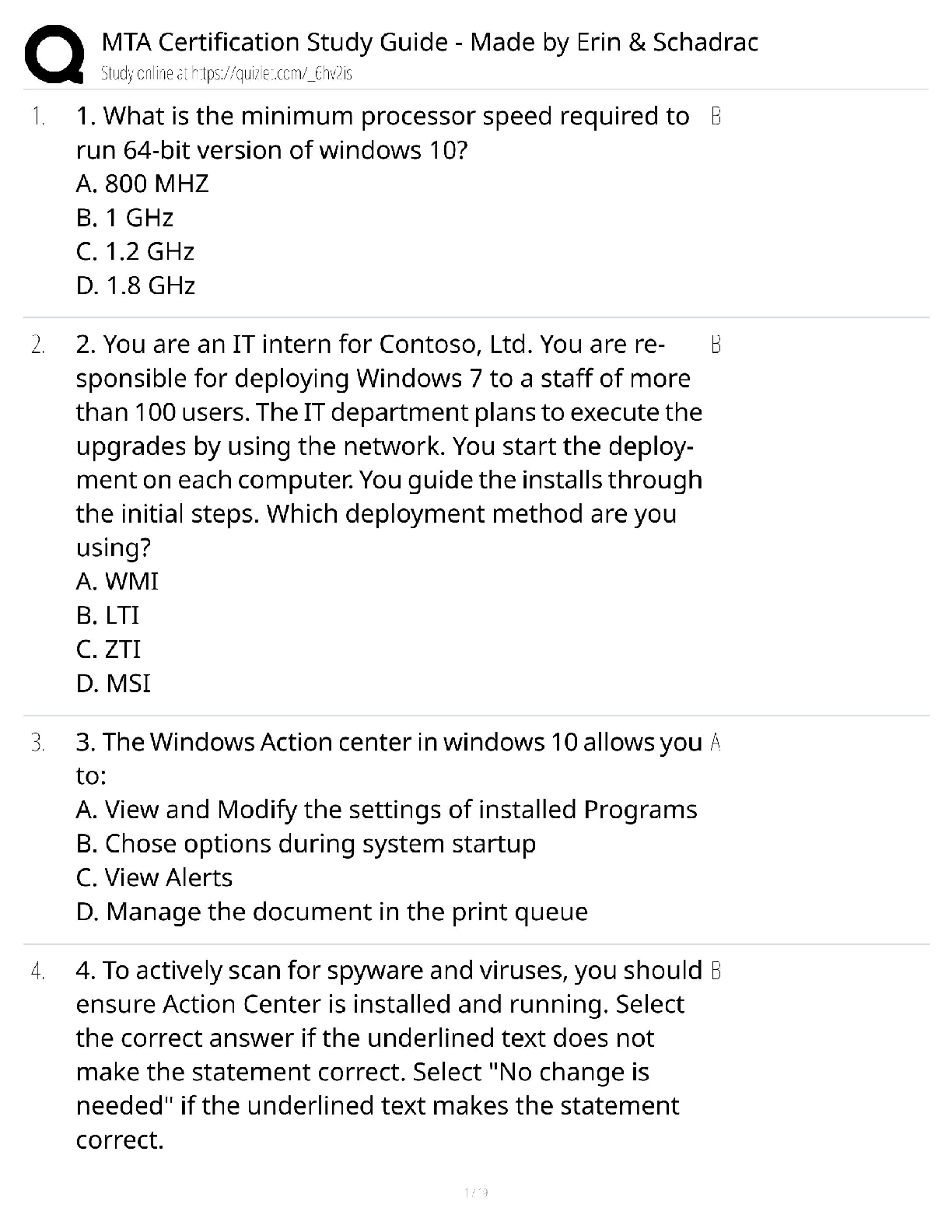
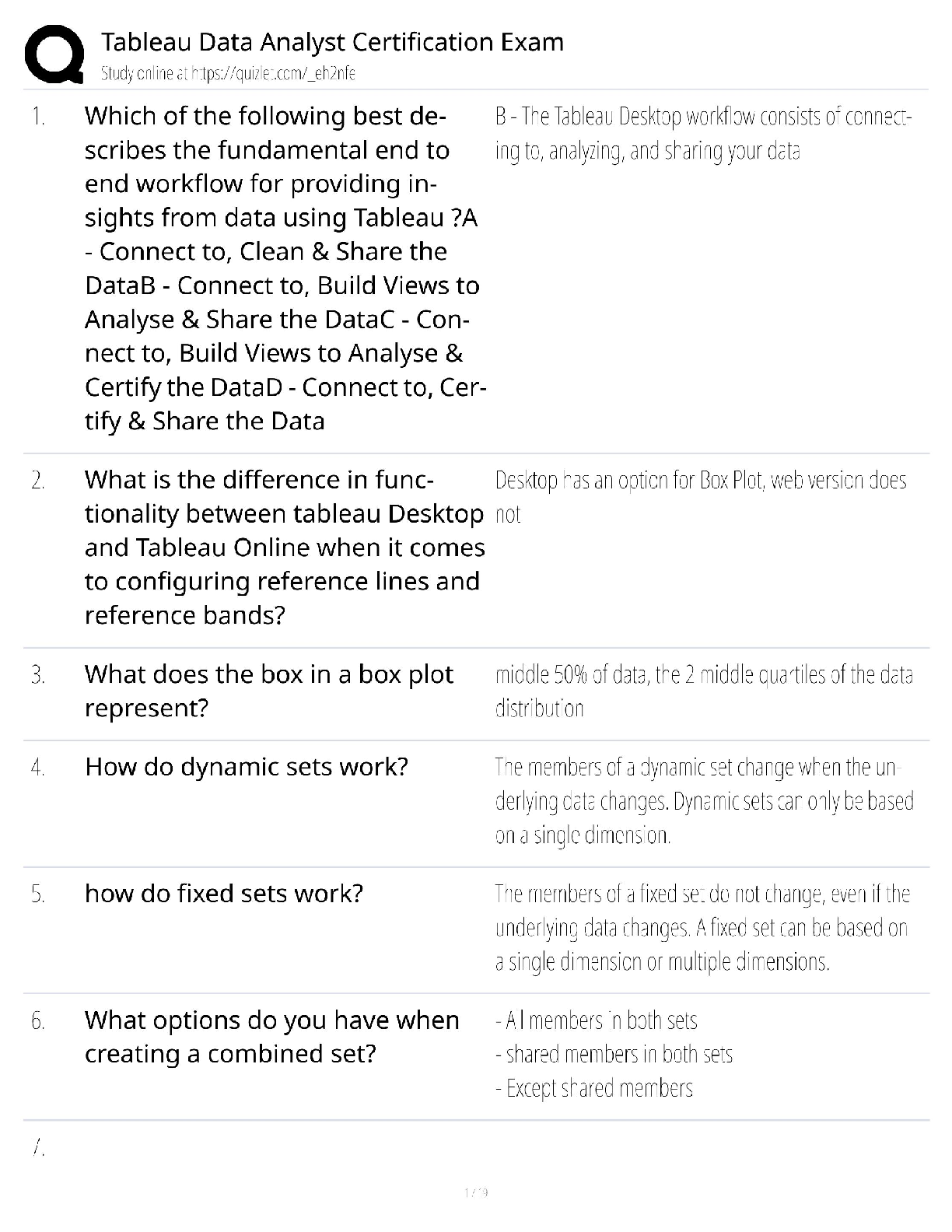
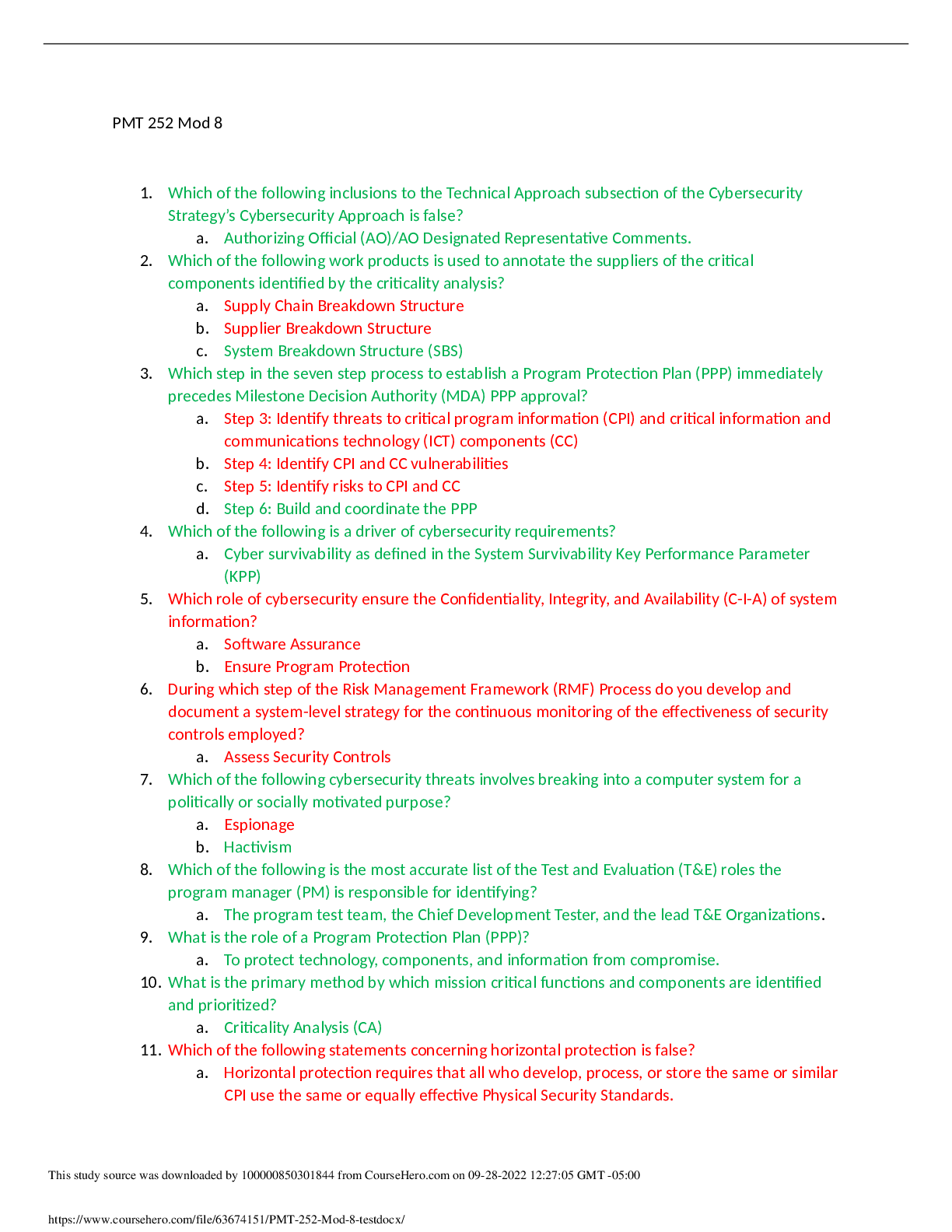
PMT 252 Mod 8 1. Which of the following inclusions to the Technical Approach subsection of the Cybersecurity Strategy’s Cybersecurity Approach is false? a. Authorizing Official (AO)/AO Designated ... Representative Comments. 2. Which of the following work products is used to annotate the suppliers of the critical components identified by the criticality analysis? a. Supply Chain Breakdown Structure b. Supplier Breakdown Structure c. System Breakdown Structure (SBS) 3. Which step in the seven step process to establish a Program Protection Plan (PPP) immediately precedes Milestone Decision Authority (MDA) PPP approval? a. Step 3: Identify threats to critical program information (CPI) and critical information and communications technology (ICT) components (CC) b. Step 4: Identify CPI and CC vulnerabilities c. Step 5: Identify risks to CPI and CC d. Step 6: Build and coordinate the PPP 4. Which of the following is a driver of cybersecurity requirements? a. Cyber survivability as defined in the System Survivability Key Performance Parameter (KPP) 5. Which role of cybersecurity ensure the Confidentiality, Integrity, and Availability (C-I-A) of system information? a. Software Assurance b. Ensure Program Protection 6. During which step of the Risk Management Framework (RMF) Process do you develop and document a system-level strategy for the continuous monitoring of the effectiveness of security controls employed? a. Assess Security Controls 7. Which of the following cybersecurity threats involves breaking into a computer system for a politically or socially motivated purpose? a. Espionage b. Hactivism 8. Which of the following is the most accurate list of the Test and Evaluation (T&E) roles the program manager (PM) is responsible for identifying? a. The program test team, the Chief Development Tester, and the lead T&E Organizations. 9. What is the role of a Program Protection Plan (PPP)? a. To protect technology, components, and information from compromise. 10. What is the primary method by which mission critical functions and components are identified and prioritized? a. Criticality Analysis (CA) 11. Which of the following statements concerning horizontal protection is false? a. Horizontal protection requires that all who develop, process, or store the same or similar CPI use the same or equally effective Physical Security Standards. Based on your understanding of the relationship between prevention countermeasures and detection-and-response countermeasures, which measures would you evaluate if your goal was to make an attack look more risky to a potential attacker? a. Measures to detect and respond to a risk. [Show More]
Last updated: 1 year ago
Preview 1 out of 3 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

Defense Acquisition University PMT 252 Lesson 1 test Module 1 Exam- Module 8 Exam TESTS and RESULTS.
Defense Acquisition University PMT 252 Lesson 1 test Module 1 Exam Defense Acquisition University PMT 252 252 Lesson 2 test . Module 2 Exam Defense Acquisition University PMT 252 252 Module 2...
By QuizMaster 3 years ago
$47
18
Reviews( 0 )
$5.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 28, 2022
Number of pages
3
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 28, 2022
Downloads
0
Views
122