Computer Science > ESSAY > ESSAY : THE SPLUNK SOFTWARE ; Leverage of Splunk as a Fraud Detector (All)
ESSAY : THE SPLUNK SOFTWARE ; Leverage of Splunk as a Fraud Detector
Document Content and Description Below
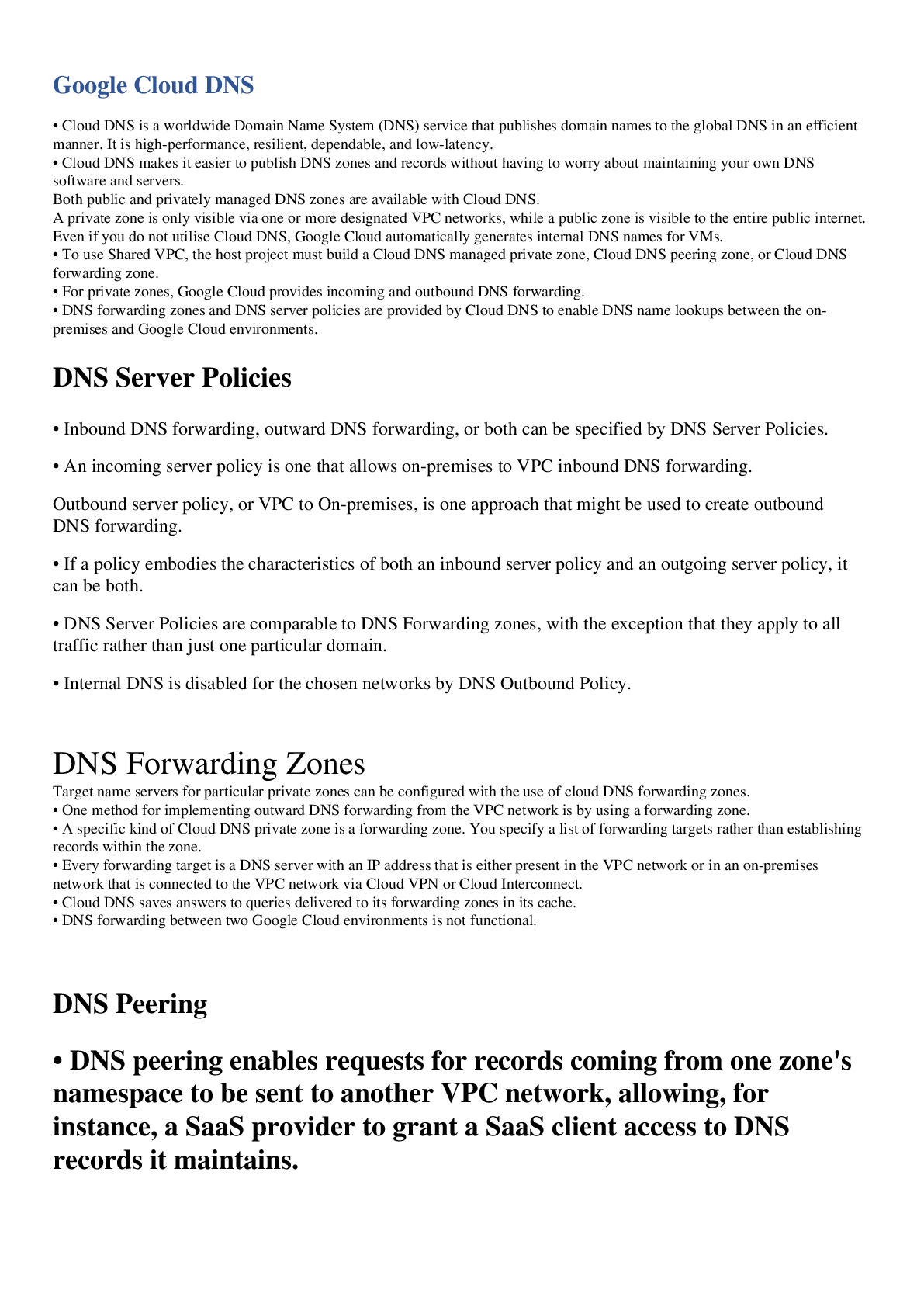
Splunk is a software application used for searching and monitoring big data systems. Splunk tool is a powerful tool for log collection. From its outlook or appearance, its operation and navigation are ... easier. Upon its application, one can add more information and adjustments as he wishes based on what is intended to be done. A lot of functionalities can be done or added through the use of the add-ons buttons and apps available on the software system. can range from a simple line to a more complex tool application that contains saved servers for searching and other executable elements among more. From the attacker’s point of view of the fraudulent activities, certain leverage adjustments can be done to aid in this risk detection. The general knowledge of the use of this tool is more important for both fraud detection and offensive/defensive positions in cyber security. Big losses have been reported by more industries and organizations as a result of fraudulent activities. Many frauds involve the use of users’ original login credentials and registered means of online payments totalling 50 per cent of the fraudulent activities reported every year from different parts of the world. The Splunk system can avail searching tools, creation of insights, availing alerts on tempted fraud, and lastly reporting and visualization of the fraud activity. By leveraging algorithms in machine learning as far as Splunk software is concerned, it helps to correlate the behaviour of the user and the machine data sources involved. The network baselines are also kept on standby and the recognition of their behaviour is to make the insecurity detection successful. Fraud activities from stolen identity to stealing personal and account information. This calls for an alarm as online customers and online organizations are at risk of fraudulent activities and thus need to be secured. The leveraging Individuals involved in fraud activities are becoming more sophisticated as they daily learn and adopt new techniques to carry out their practices. From the Forbes news, it is reported that fraudsters can leverage multiple cheaps from different platforms worldwide to hide their location and identities as they deceive fraud experts and the systems involved in fraud detection (Jha et al., 2020). This has rendered the monitoring of malicious activities become more complicated. [Show More]
Last updated: 1 year ago
Preview 1 out of 4 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$12.50
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jan 08, 2024
Number of pages
4
Written in
All
Additional information
This document has been written for:
Uploaded
Jan 08, 2024
Downloads
0
Views
111