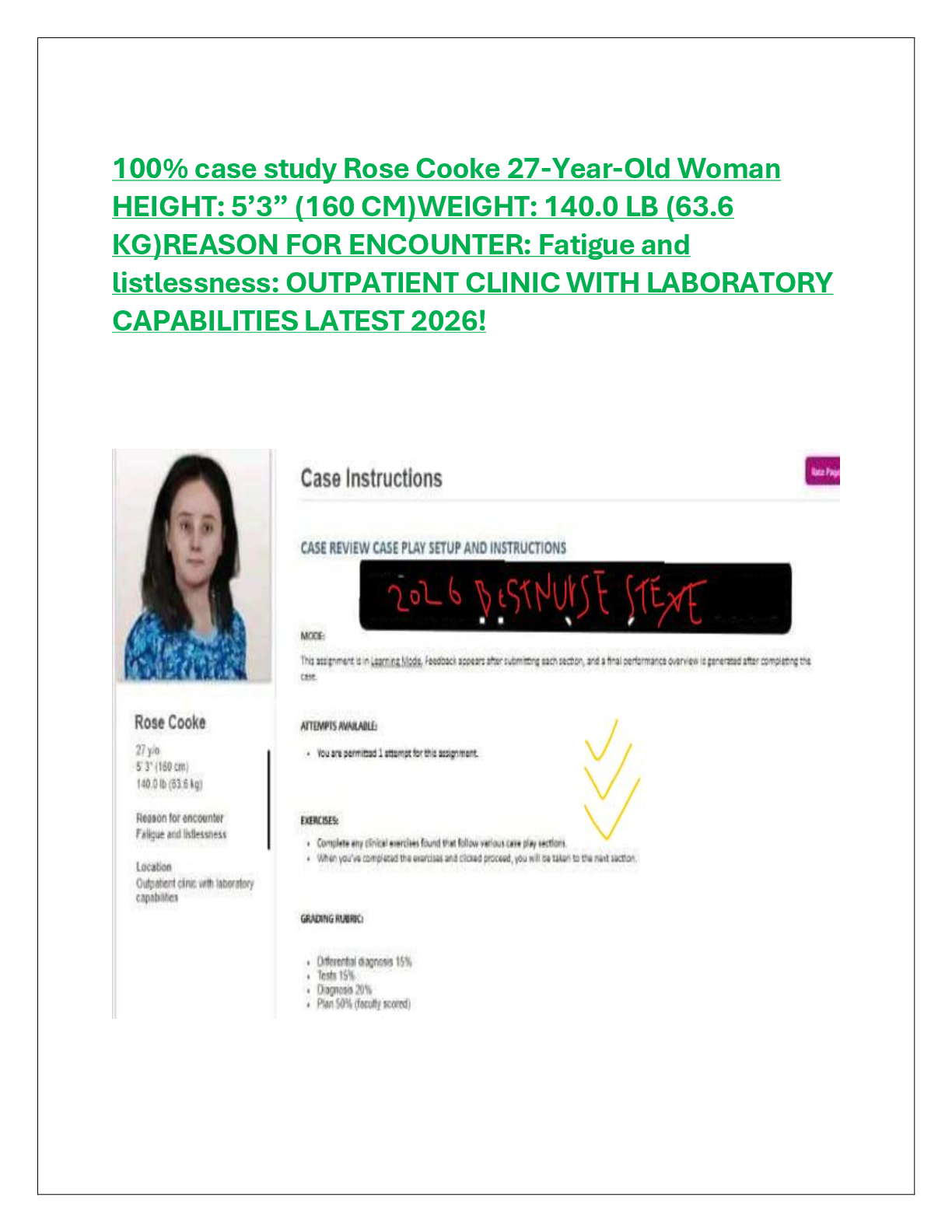
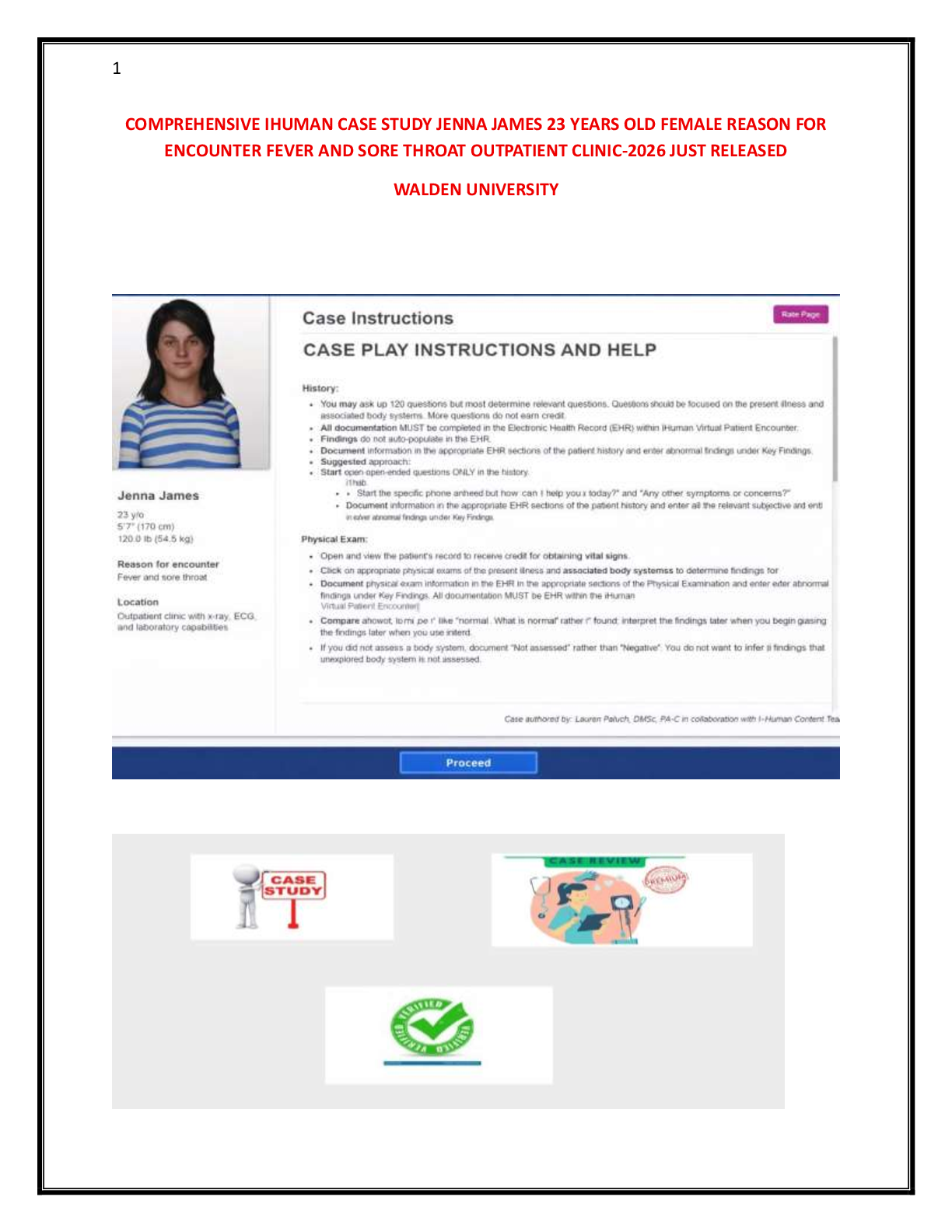
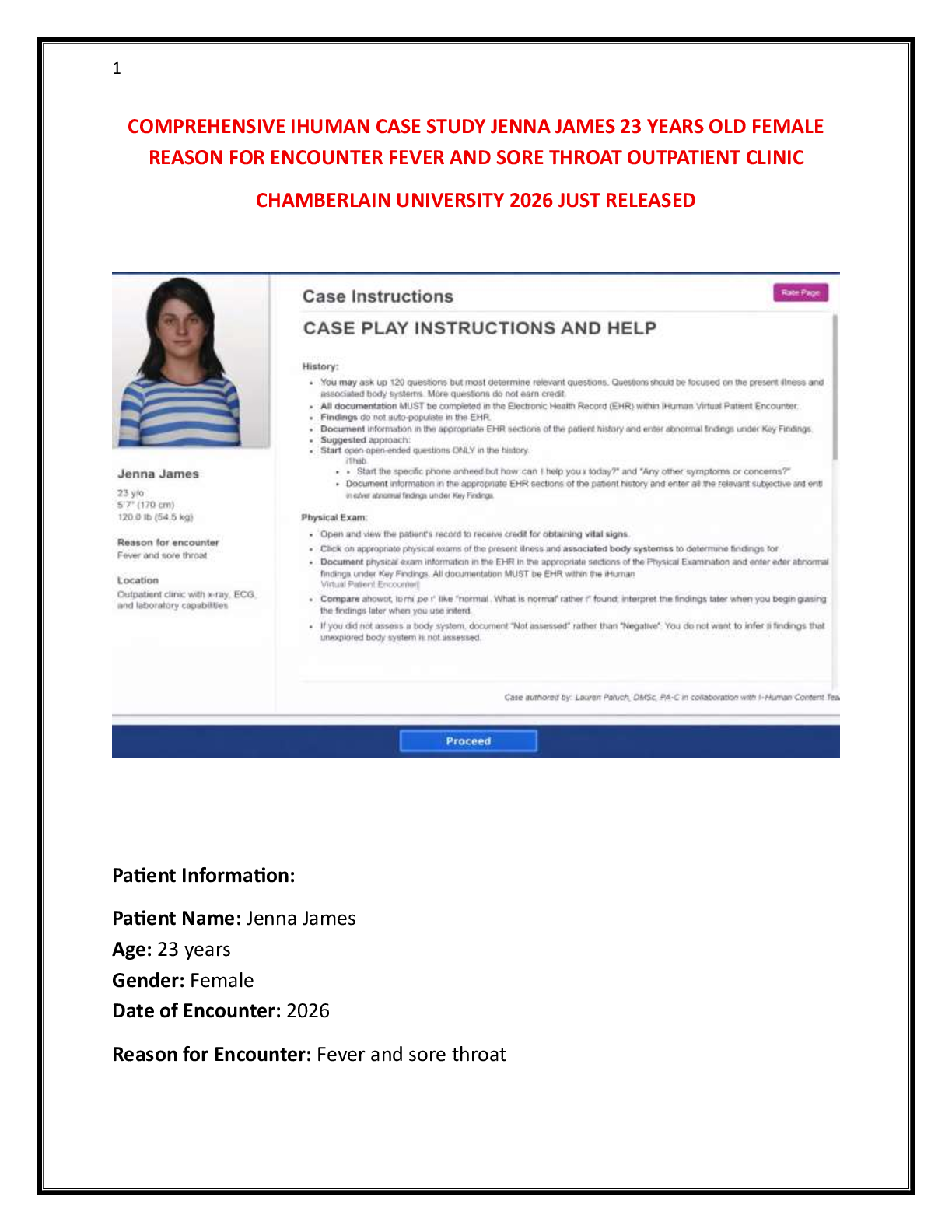
Assurance Assignment 2.docx ISSC366 ISSC366– Information Assurance Assignment #2 American Military University There are two forms of cryptography: symmetrical and asymmetrical. Symmetrical cryptography encrypts d
...
Assurance Assignment 2.docx ISSC366 ISSC366– Information Assurance Assignment #2 American Military University There are two forms of cryptography: symmetrical and asymmetrical. Symmetrical cryptography encrypts data using a secret key and decrypts it with the same key. Asymmetrical cryptography encrypts data using a public key and decrypts it with another public key. You will compare symmetrical and asymmetrical encryption in this article by utilizing typical methods from each encryption type. This analysis will concentrate on the following factors: speed, key length, and implementation. The fastest approach is symmetrical encryption since it is the one most people choose. Due to these different contributing variables, symmetric encryption can be faster. The technique yields the same or smaller-sized ciphertext as the original text. This is particularly useful when you quickly encrypt large volumes of data since it shortens the encryption time and avoids increasing the file size. An inherent problem with asymmetrical encryption is that the encryption method may not be as sophisticated as other methods. Another aspect of this kind of encryption is that it utilizes the same key to encrypt and decode a communication. The opposite is also true: communications will be harder to decode if one side is hacked. This technique is effective in intranets when keys can also be maintained safe from one machine to the next, but less effective in the public Internet since the risk of exposure is higher. For movi. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .. . . . . .. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .. . .. .. . . . . . . . . . . . . . . . . . .. . . . .
[Show More]