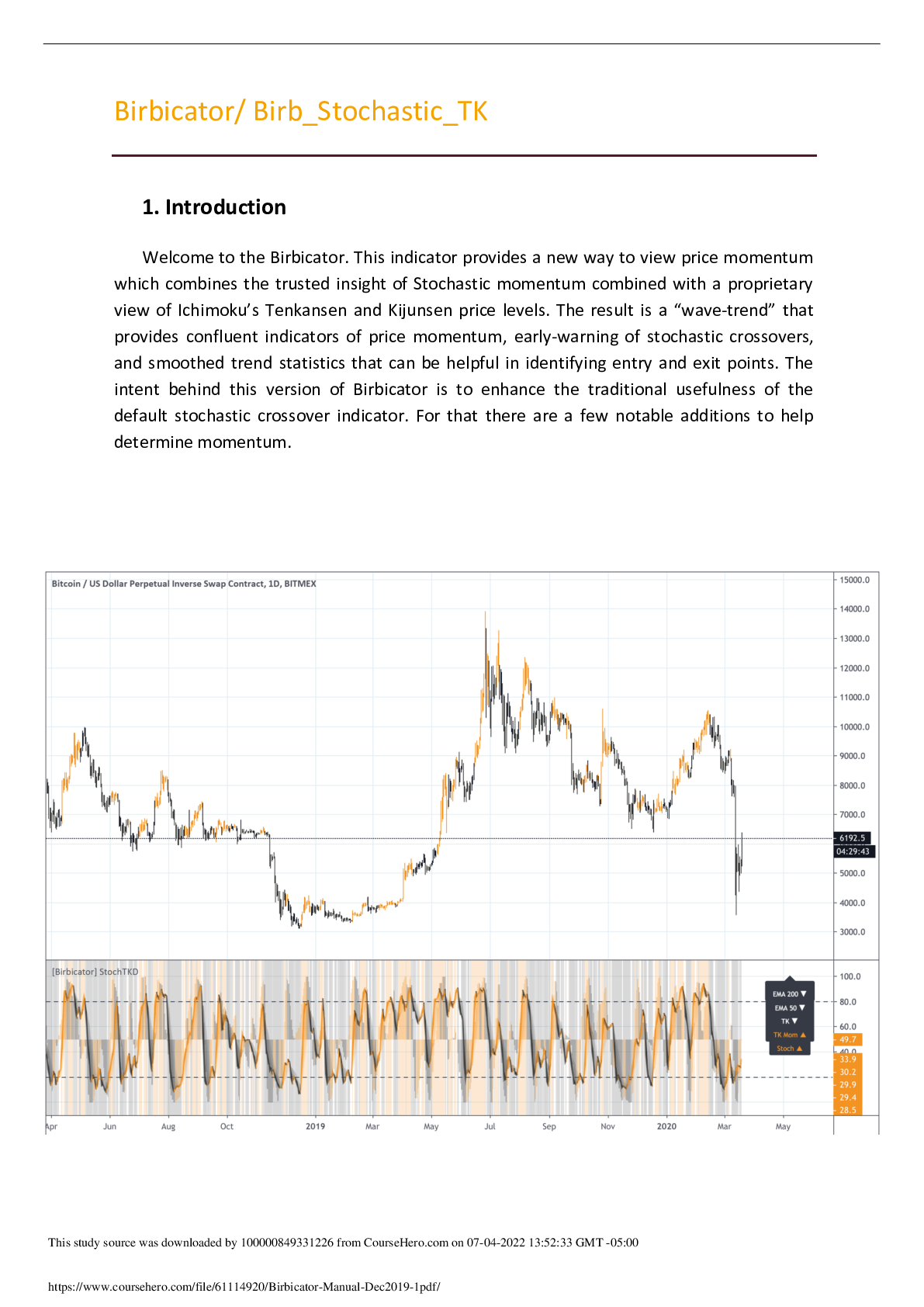
As a Network Security Team, we will be proving IDI with a network security plan to mitigate the vulnerabilities that have been discovered. A secure site will be set up with network intrusion detection and network protec
...
As a Network Security Team, we will be proving IDI with a network security plan to mitigate the vulnerabilities that have been discovered. A secure site will be set up with network intrusion detection and network protection systems and will be available to access via the internal network. Policies will be presented for remote access and the use of VPN. Also will be in this report will be strategies for hardening the network and mitigating risks. An updated network layout with increased network security to meet the current needs will be included. In the interest of business continuity, remote access will be utilized. User wishing access to internal network assets will only be able to access said assets with the use of a company issued laptop. We will make use of MAC address filtering to allow remote users access to the internal network via VPN. Each have the remote access laptops will have been loaded with VPN and have the MAC address added to the list on the MAC address filter.
ITT Tech - IS3220 Final Project Network Security Plan
As a Network Security Team, we will be proving IDI with a network security plan to mitigate the vulnerabilities that have been discovered. A secure site will be set up with network intrusion detection and network protection systems and will be available to access via the internal network. Policies will be presented for remote access and the use of VPN. Also will be in this report will be strategies for hardening the network and mitigating risks. An updated network layout with increased network security to meet the current needs will be included. In the interest of business continuity, remote access will be utilized. User wishing access to internal network assets will only be able to access said assets with the use of a company issued laptop. We will make use of MAC address filtering to allow remote users access to the internal network via VPN. Each have the remote access laptops will have been loaded with VPN and have the MAC address added to the list on the MAC address filter.
Multi Layered Security Plan Corporation Tech
1. User Domain
2. Workstation Domain
3. LAN Domain
4. LAN to WAN Domain
5. WAN Domain
6. Remote Access Domain
Policies and Procedures
Acceptable Use Policy
Remote Access Policy
Remote Access Password Policy
Remote Device Policy
Security Awareness Policy
Internet Use Policy
Access Control Policy
Data Classification Policy
VPN Policy
Compromise or Infection Policy
[Show More]